Li was asked to create a Splunk configuration to monitor syslog files stored on Linux servers at their organization. This configuration will be pushed out to multiple systems via a Splunk app using the on-prem deployment server.
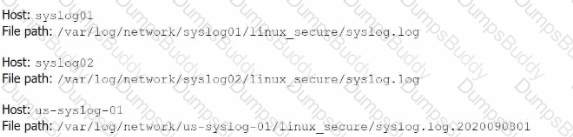
The system administrators have provided Li with a directory listing for the logging locations on three syslog hosts, which are representative of the file structure for all systems collecting this data. An example from each system is shown below:
A)
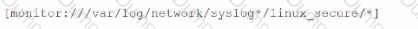
B)
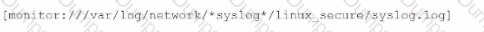
C)

D)
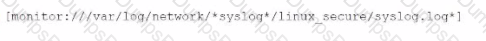
A customer has worked with their LDAP administrator to configure an LDAP strategy in Splunk. The configuration works, and user Mia can log into Splunk using her LDAP Account. After some time, the Splunk Cloud administrator needs to move Mia from the user role to the power role. How should they accomplish this?
By default, which of the following capabilities are granted to the sc_admin role?
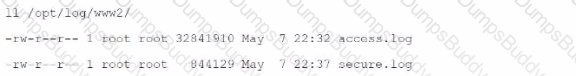
Which monitor statement will retrieve only files that start with "access" in the directory /opt/log/ww2/?
When a forwarder phones home to a Deployment Server it compares the check-sum value of the forwarder's app to the Deployment Server's app. What happens to the app If the check-sum values do not match?
Which of the following stanzas would enable a TCP input on port 1025, allowing traffic from all IP addresses except 10.5.5.1?
A)
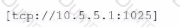
B)
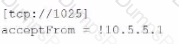
C)

D)

When monitoring network inputs, there will be times when the forwarder is unable to send data to the indexers. Splunk uses a memory queue and a disk queue. Which setting is used for the disk queue?
When creating a new index, which of the following is true about archiving expired events?
Which of the following files is used for both search-time and index-time configuration?
A customer wants to mask unstructured data before sending it to Splunk Cloud. Where should SEBCMD be configured for this?
Files from multiple systems are being stored on a centralized log server. The files are organized into directories based on the original server they came from. Which of the following is a recommended approach for correctly setting the host values based on their origin?
Given the following set of files, which of the monitor stanzas below will result in Splunk monitoring all of the files ending with .log?
Files:
/var/log/www1/secure.log
/var/log/www1/access.log
/var/log/www2/logs/secure.log
/var/log/www2/access.log
/var/log/www2/access.log.1