Your network is a mixed environment of Windows, Linux, and UNIX, computers. The routers are primarily
Cisco and the network uses a T-1 to connect to the Internet. You are experimenting with setting up a mail server in a production environment for internal use only. You do not want this mail server to receive any requests from anywhere but the internal network. Therefore you have decided to block incoming SMTP traffic at the Firewall. Which port will you block at the Firewall?
The main reason you have been hired at a company is to bring the network security of the organization up to current standards. A high priority is to have a full security audit of the network as soon as possible. You have chosen an Independent Audit and are describing it to your coworkers. Which of the following best describes an Independent Audit?
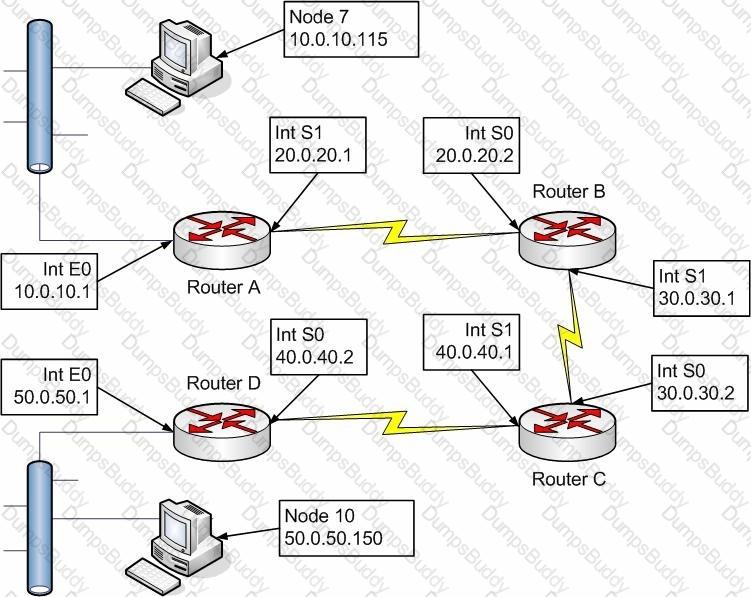
The exhibit represents a simple routed network. Node 7 is a Windows 2000 Professional machine that establishes a TCP communication with Node 10, a Windows 2003 Server. The routers are Cisco 2500 series running IOS 11.2.
While working at Node 10, you run a packet capture. Packets received by Node 10, and sent from Node 7 will reveal which of the following combination of source IP and source Physical addresses:
You were recently hired as the security administrator of a small business. You are reviewing the current state of security in the network and find that the current logging system must be immediately modified. As the system is currently configured, auditing has no practical value. Which of the following are the reasons that the current auditing has little value?
In your current organization, you have been given the task of implementing the IPSec solution. All your servers are running Windows Server 2003, so you wish to use the built in policies. What are the three default IPSec policies in Windows Server 2003?
During a network capture in Network Monitor, you capture some UDP traffic. In a UDP Header, what is the function of the first sixteen bits?
You wish to configure a new Cisco router, which will take advantage of the AutoSecure feature. The AutoSecure security features are divided into which two planes?
If you wish to implement IPSec between two branch offices of your organization, and wish for this to include the encryption of the full packet, which implementation would meet your needs?
Your network is going to implement a new network security solution, and as part of this you are configuring IPSec on a Windows Server 2003 machine. Which of the following is the description of the Client (Respond Only) default IPSec Policy?
During your review of the logs of your Cisco router, you see the following line. What is the meaning of this line?
%SYS-5-CONFIG_I: Configured from console by vty1 (172.16.10.1)
As you increase the layers of security in your organization you watch the network behavior closely. What kind of problems can be introduced by adding file encryption to the computers in your network?
You are configuring a new IDS, running Snort, in your network. To better configure Snort, you are studying the configuration file. Which four of the following are the primary parts of the Snort configuration file?
As per the specifications of RFC 1191: Path MTU Discovery, MTUs have been defined so that transmitted datagram will not unnecessarily become fragmented when traveling across different types of physical media. You are going to run several packet captures to be sure there are no out of spec packets on
your network. According to these specifications what are the absolute minimum and maximum MTUs?
During a network analysis session, you capture several TCP/IP sessions. You focus your analysis on the
IP Headers. In an IP Header, what is the function of the first four bits?
You are configuring your new IDS machine, and are creating new rules. You enter the following rule:
Alert tcp any any -> any 23 (msg: "Telnet Connection Attempt";)
What is the effect of this rule?
You are in the process of configuring your network firewall policy. As you begin building the content of the policy you start to organize the document into sections. Which of the following are sections found in the firewall policy?
You have successfully implemented a new Intrusion Detection System in your network. You have verified that the system is active and did detect the tests you have run against it thus far. You are now in the stage of identifying the type of analysis you wish to use with the system. You meet with the rest of the IT staff and are asked to describe the different options for analysis. Which of the following best describes Interval Analysis?
The main reason you have been hired at a company is to bring the network security of the organization up to current standards. A high priority is to have a full security audit of the network as soon as possible. You have chosen an Independent Audit and are describing it to your coworkers. Which of the following best describes an Independent audit?
After installing Snort on your windows machine that is destined to be your IDS, you need to edit the configuration files entry of "HOME_NET" to define which of the following?
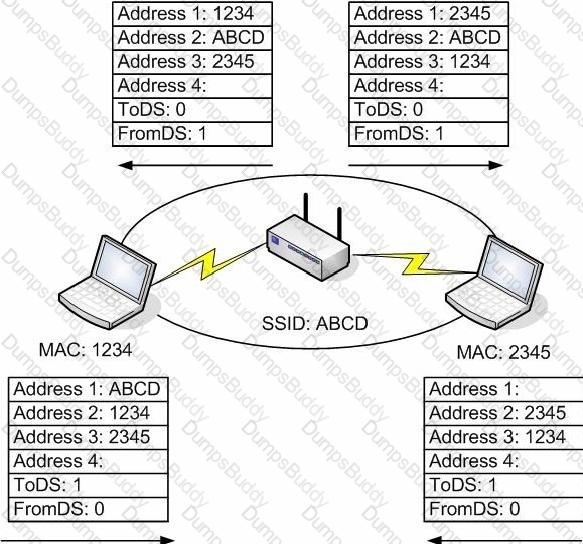
You need to diagram wireless security options for your team during a planning meeting. What wireless security process is shown in this image?
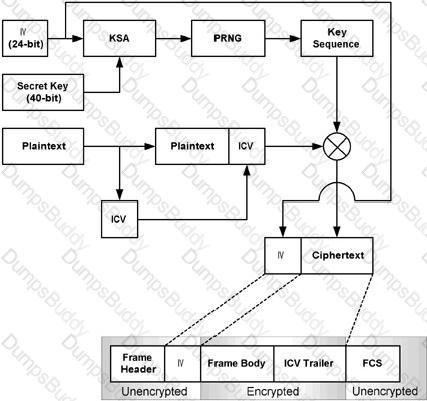
You have made some changes to the configuration of your ISA Server 2006 firewall. While analyzing the network traffic, you see that these changes have not yet taken affect. What must you do to get these new rules to take function?
You are reviewing your companys IPTables Firewall and see the command (minus the quotes) " ! 10.10.216" as part of a rule, what does this mean?
As Intrusion Detection Systems become more sophisticated, the software manufacturers develop different methods of detection. If an IDS uses the process of finding a deviation from a well know pattern of user behavior, what is this known as?
You are going to add another computer to the pool that you use for detecting intrusions. This time you are making a customized Snort machine running on Windows 2000 Professional. Prior to running Snort you must install which of the following programs?
For the new Snort rules you are building, it will be required to have Snort examine inside the content of the packet. Which keyword is used to tell Snort how far inside the packet it should look for the pattern, or defined content match?
You are reconfiguring your networks firewall to create a DMZ using three network interfaces. After configuring the addresses on the interfaces, you are making the required changes in ISA Server 2006. You are going to use Network Template during this configuration change. What Network Template is designed for this firewall topology?
In order to properly manage the network traffic in your organization, you need a complete understanding of protocols and networking models. In regards to the 7-layer OSI model, what is the function of the Network Layer?
Your company has many different services that go through your ISA Server 2006, and you need to prioritize the network traffic. What does ISA Server 2006 use to prioritize packets?
You are using Network Monitor to capture some traffic for later analysis. When you do begin to look at your captured data, you examine the TCP traffic you captured. In a TCP Header, what is the function of the first sixteen bits?
In the image, there are two nodes communicating via an access point. In the packet on the right side of the image, the Address 1 field is blank. If this packet is destined for the other computer, what is the value that must be filled in this blank address field?