You are concerned that email messages sent to your Outlook clients could contain customized and dangerous scripting. What can you do to minimize the threat that this specific type of email presents?
You have a series of new Windows Server 2003 systems, including 3 new web servers running IIS 6.0.
You are concerned about the overall security of your servers, and are checking with Microsoft for any patches or updates that you might need to apply to your systems. Which of the following would you apply if you need to implement an update to fix a specific problem that addresses a critical, non-security-related bug?
Often times attackers will run scans against the network to identify different network and operating systems, and resources that are available. If an attacker runs scans on the network, and you are logging the connections, which of the following represent the legitimate combination of packets that will be sent between the attacker and target?
You are creating the Remote Access section of your organizational security policy. From the following options, select the questions to use for the formation of this section?
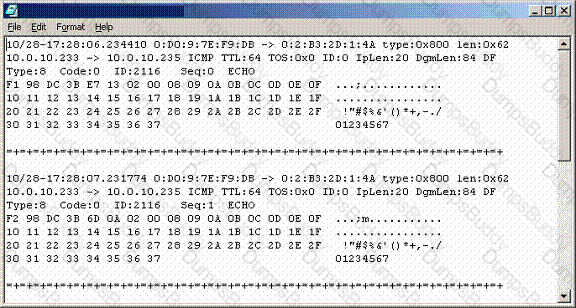
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
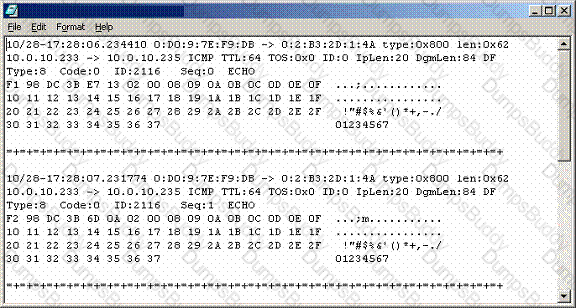
It has come to your attention that some machine has tried to send a packet to your DNS server containing both a DNS query and an answer that is false. What type of attack was used against your network?
Recently you found out that there has been a flood of bogus network traffic hitting your Email server.
Because of this flood, authorized users have not been able to consistently send or receive email. What is happening to your Email server?
In your organization, the majority of employees use Microsoft Outlook Express as their email client. You are configuring these systems so that applications on the employee systems cannot send email, posing as the user of the system. Under the Security tab, which option will you select to achieve this goal?
After a security meeting, IT leaders decided that the organization will perform a completely new risk analysis, as the previous one was done over five years ago. The methods that will be used is FRAP. Which of the following best describes the FRAP method of risk analysis?
Which of the following has the stages of Risk Analysis in order, from a to e?
a) Management
b) Threat Assessment
c) Control Evaluation
d) Inventory
e) Monitoring
Microsoft has developed several security tools to help you with the security and configuration of the systems in your network. One of these tools is the Microsoft Security Baseline Analyzer (MBSA). In the command line options of the MBSA is the HFNetChk tool. What is the function of the HFNetChk tool, available with MBSA?
You work for a medium sized ISP and there have been several attacks of the DNS configuration recently.
You are particularly concerned with DNS Spoofing attacks. If an attacker is able to send out false data to a
DNS client before the response from the DNS server arrives, this is which type of DNS Spoofing?
You are running some tests in your network, to see if you can remotely identify the operating system of nodes in the network. Using the nmap tool, which of the following commands will identify the operating system of the computer using IP address 192.168.10.1?
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
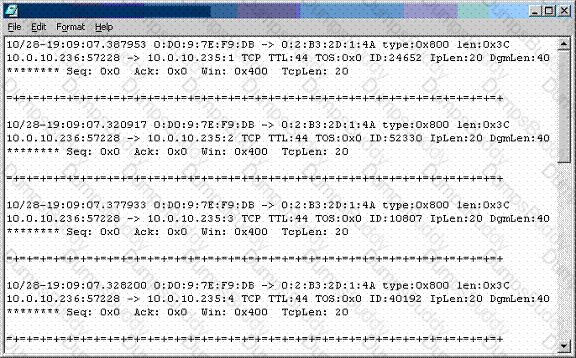
In order for your newly written security policy to have any weight, it must be implemented. Which of the following are the three components of a successful Security Policy Implementation in an organization?
During a one week investigation into the security of your network you work on identifying the information that is leaked to the Internet, either directly or indirectly. One thing you decide to evaluate is the information stored in the Whois lookup of your organizational website. Of the following, what pieces of information can be identified via this method?
You are discussing the design and infrastructure of the Internet with several colleagues when a disagreement begins over the actual function of the NAP in the Internets design. What is the function of a
NAP in the physical structure of the Internet?
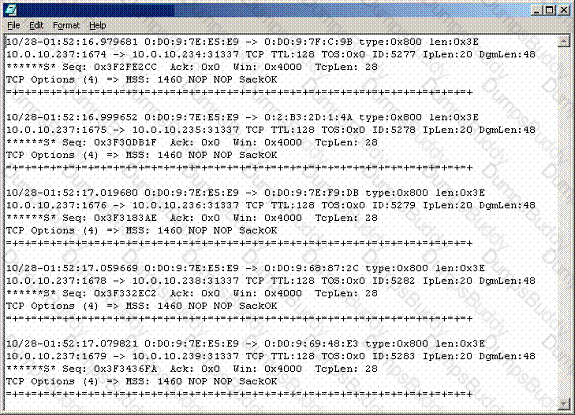
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use
Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
You are reviewing the lines used in the configuration of TCP Wrappers on your Linux system. When placed in the denial file, what is the function of the following line?
in.telnetd: 192.168.23.: spawn (/bin/echo %c >> /var/log/telnet.log)
At the root@linuxbox$ prompt on a Linux machine you type ls -l b.doc and the output reads:
-rw-rw-r--1 simonusers31337Oct 5 11:21 b.doc
According to this output, which of the following is true?
On your Linux computer you are examining the contents of various files to ensure they are secured and contain the designated information. Entries in the /etc/hosts file consist of which of the following?
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use
Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
In Windows 2003, there are four methods of implementing IPSec. They are:
1 - Require Security
2 - Request Security
3 - Respond Only
4 - No IPSec Policy
Your network hosts many servers, and different security policies are in place in different locations in the network. The Clients and Servers in your network are configured as follows:
-You have servers numbered 1-9, which have a policy stating they require no network traffic security.
-You have servers numbered 10-19, which have a policy stating they are not required to be secure, but will encrypt network traffic if the client is able to receive it.
-You have servers numbered 20-29, which have a policy stating they are required to be secure and all network traffic they deliver must be secured.
-You have clients numbered 60-79 that are required to access secure servers 20-29.
-You have clients numbered 80-99 that are not required to access secure servers 20-29, but are required to access servers 1-9 and 10-19.
Based on the Client and Server configuration provided above, which of the following computers must implement IPSec method 3?
When a new user account is created in Linux, what values are assigned to the user account?
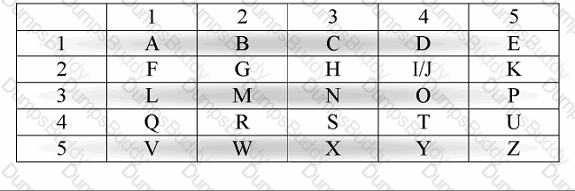
Which of the following answers is the word SECURITY after having been encrypted using the following Polybius Cipher shown in the figure?
You are configuring a complex set of policies in your Windows 2003 Active Directory network. You have parent and child GPOs. If you do not want the child GPO to inherit policy from the parent GPO, you would do which of the following?
You fear an unauthorized program has taken control of your CPU in your Linux system. What command will you run to see the CPU percentage per application in real-time?
One of your assistants has configured a Windows 2003 Server to use EFS. This server is only accessed from internal network clients over a 100BaseT infrastructure. You tell your assistant that the security offered by EFS in this situation will not increase the security of the data transferred. Why is your statement correct?