PSP Planning & Scheduling Professional (PSP) Exam Questions and Answers
The Scope of Work divides the major deliverables into smaller more manageable components for all of the following EXCEPT to:
If all other work proceeds according to the Baseline plan, how many times will the critical path change?
Which of the following are NOT normally included in the project scope statement, either directly or by reference?
Which of the following phases does NOT describe the commonly accepted construction life cycle?
Who will receive the most benefit from a master schedule of the Spring Highway project?
During the Bid Phase, do the planning and scheduling project documents impact the Bid pricing?
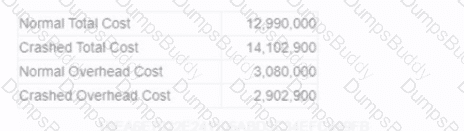
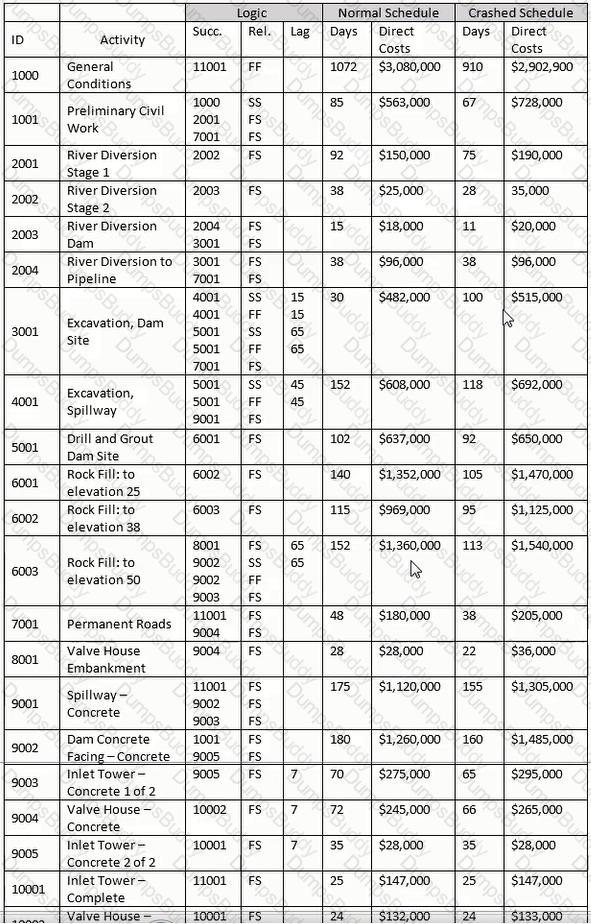
Before the work begins, the contractor considers crashing the schedule. How much would the crashed general conditions have to be reduced to break even with the normal cost budget?
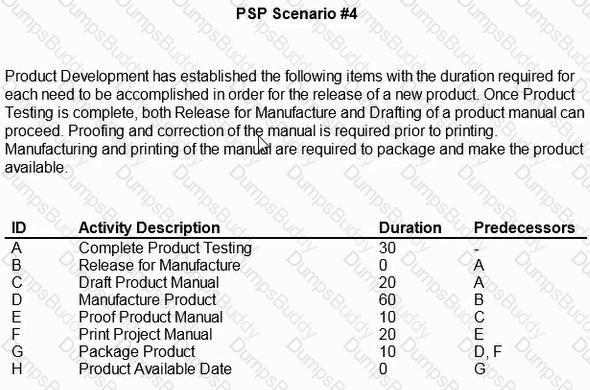
During proofing of the product manual, a problem was discovered requiring 15 days additional time to affect a correction. How can the date of availability be maintained?
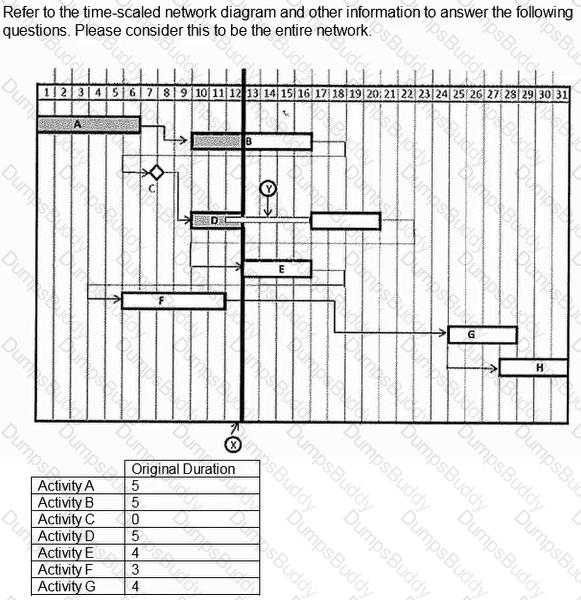
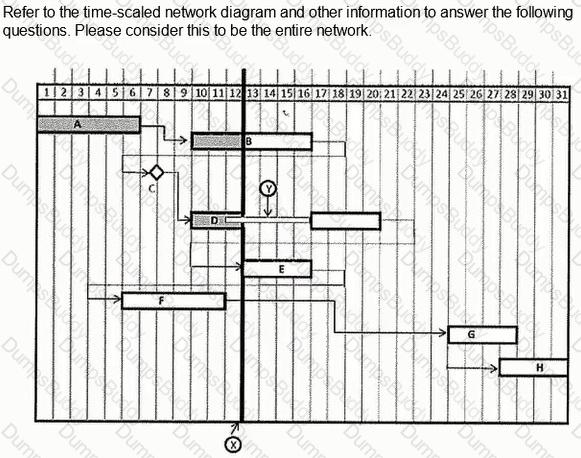
What day would Activity C complete if the duration of Activity A was reduced by five days?
Due to a testing delay, release of the product for manufacture is delayed by 5 workdays and the product manual misses its print window at the printer. If the printer is delayed by 10 workdays, what is the delay to produce release?
Scenario: You are providing construction management services for a small office building project. Your duties include reviewing and approving the contractor's baseline schedule. The contractor has submitted the first baseline schedule for the project.
The contractor's baseline schedule submittal includes a bar chart, but no CPM diagram. Which of the following is the most significant shortcoming to using a bar chart to review the baseline?
In an earned value-based system, a schedule performance index of less than one for the project indicates the project is:
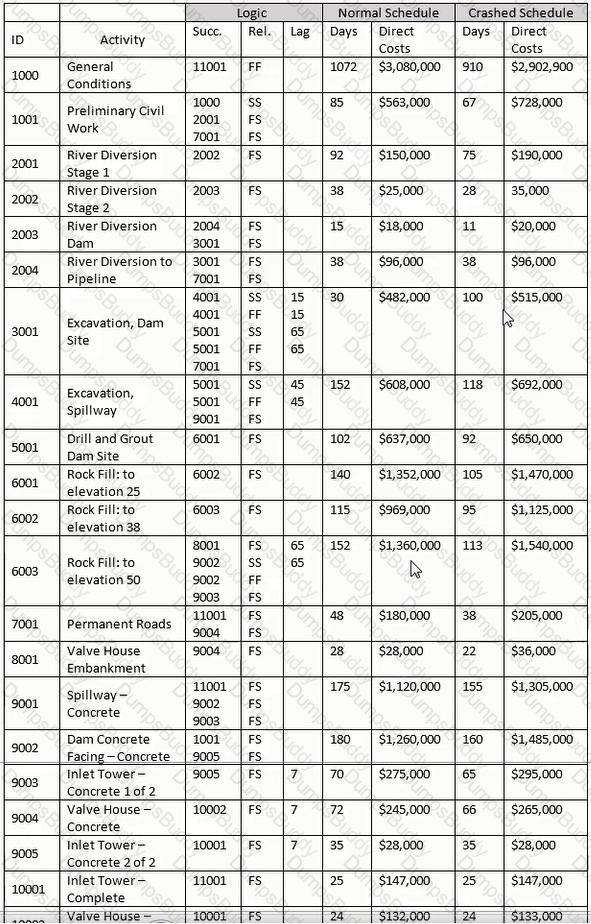
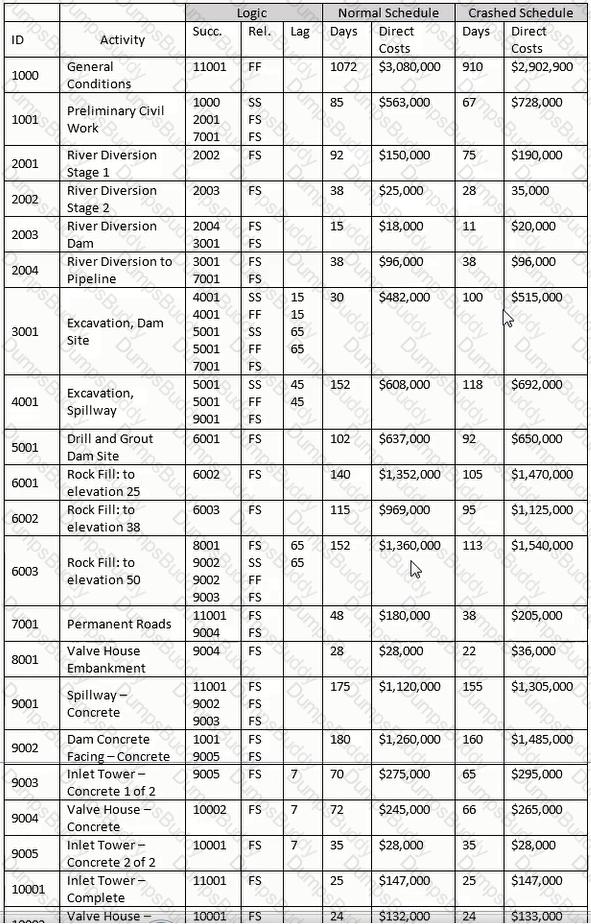
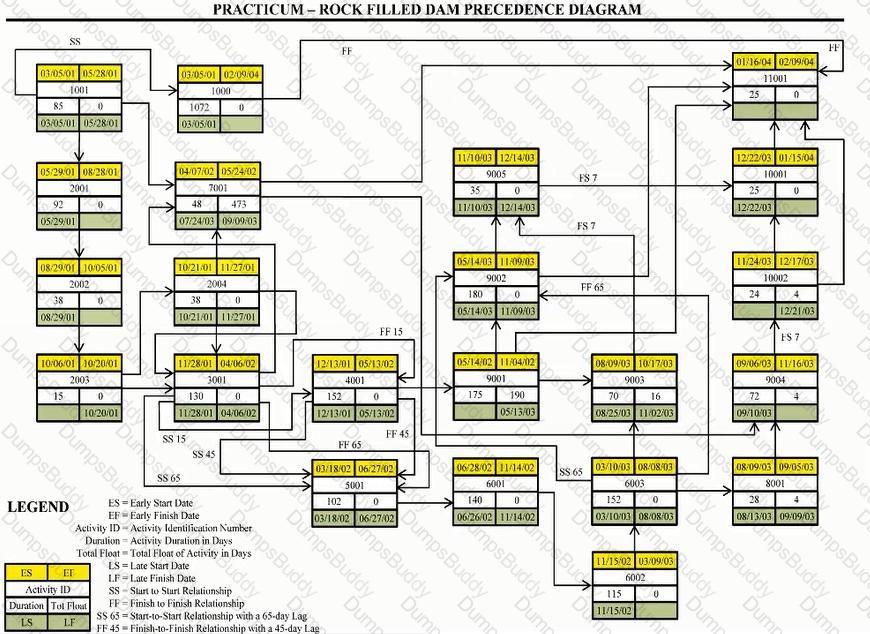
For the late finish for Activity 11001, select the most appropriate response for transitioning from the forward pass.
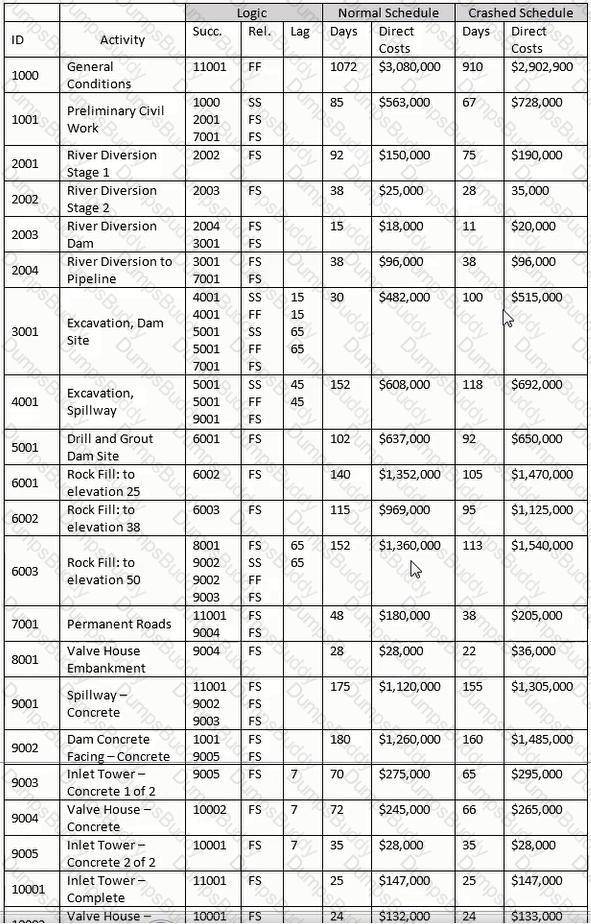
In the "normal" schedule, excluding Activity 1000, what activity(s) are concurrent with Activity 3001?
Management has determined the need to release the product 20 days earlier than planned. What tasks need to be expedited?
The sum of all budgets for work scheduled to be accomplished within a given time period is the ____________.
The amount of time that an activity can be delayed from its early start date without delaying project completion is called:
Which of the following project planning situations is the most frequent contributor to cost overruns?
You are retained by a contractor who asks you to perform a simple as-planned versus as-built analysis (APAB) of a large hydro-electric dam project that took more than five years to complete. Your analysis will form the basis of a change order that requests a time extension. You suggest using a different methodology for quantifying the delay. Which of the following reasons for recommending a different analysis does NOT apply to a simple APAB analysis?
Which of the following risks CANNOT be estimated by BILCO with only a resource-loaded schedule?
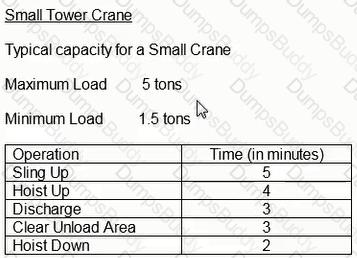
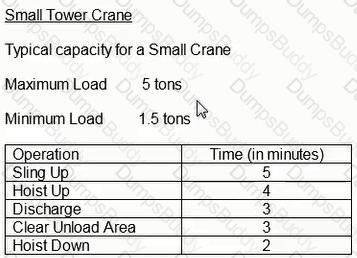
Assuming a total of 30 lifts per crane per day, what is the maximum number of lifts that could be accomplished using 3 small tower cranes over a 5-day period?
Using the normal schedule, what is the early finish date and total float of Activity 10002?
Using the "normal" schedule, given Activity 3001 and the relationship with Activity 4001, what is indicated?
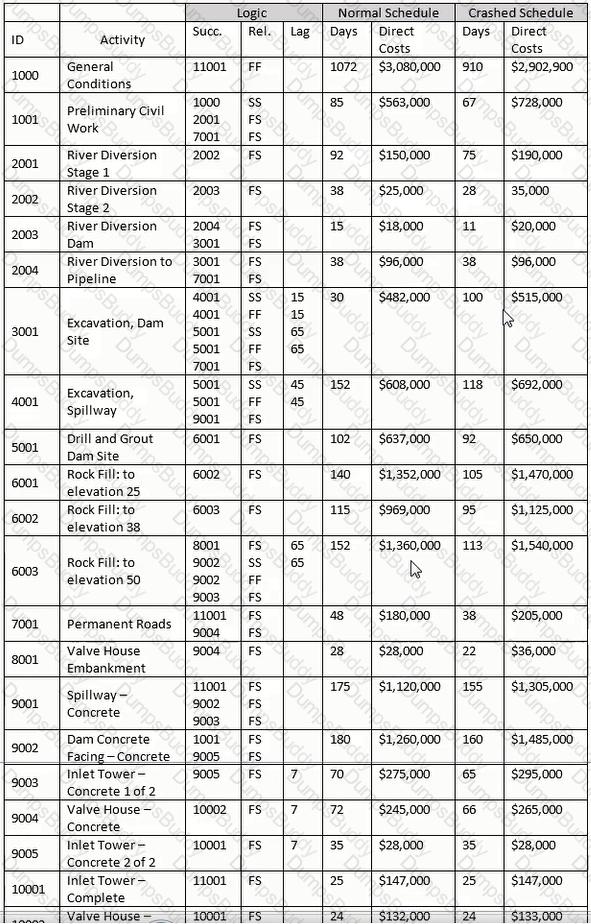
Scenario:
The entire network consists of the following activities and relationships. Activity A is twenty days long and is tied to Activity B, a ten-day activity, with a finish-to-finish tie with a lag value of five Activity B is tied to Activity C, a twenty-day activity, with a start-to-start relationship with a lag value of five.
PSP Activities Table
Scope Known about Rock-Filled Dam Project:
The dam requires river diversion and work over two or more rainy seasons. The contract is lump sum, competitively bid, and will be self-performed. The owner has attempted to shift all risk to the contractor by employing "no differing sit conditions" and "no damage for delay" clauses. There is a bonus/penalty provision of $2,500 per calendar day for early or late delivery. The early completion bonus is capped at $500,000, with no cap for late delivery penalty.
Liquidated damages end at the finish of demobilization. Indirect costs per calendar day are $2,800 for the "normal" schedule and $3,200 for the "crashed" schedule. The winter/wet weather season is 151 days between October 15 and March 25 of each year, reduces the efficiency of the contractor's operations by 20% and costs the contractor $10,000 per day. Assume a start date of March 5, 2001 and use a 7-day work week.
The following table lists work activities as planned by the contractor.
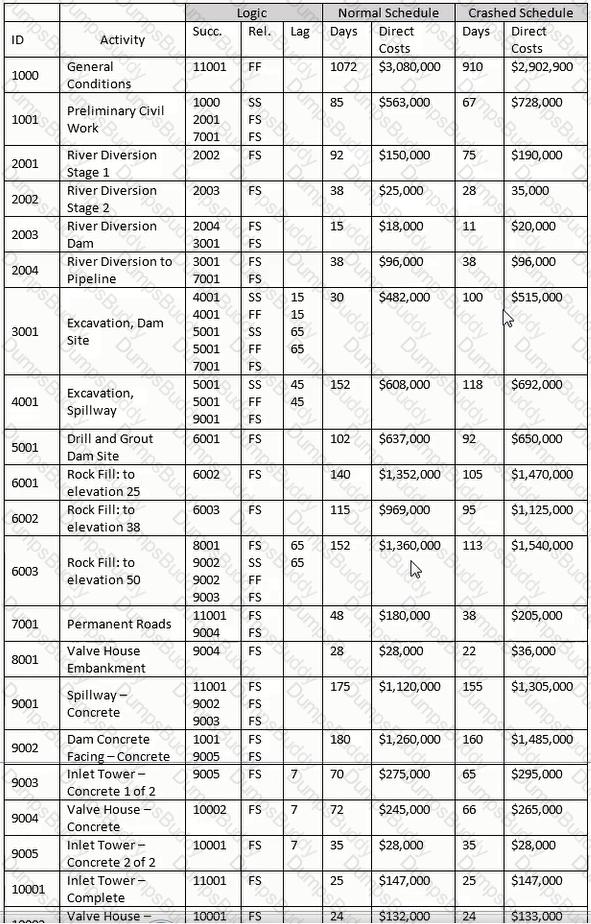
Theoretically construct a summary activity for only those activities with a finish-to-start relationship for Activities 8001 through 10001. Using the "normal" schedule, what is the cost of this hammock?
If after calculating a schedule an activity exhibits negative total float, which of the following is certain? The activity
Which of the following are NOT considerations or constraints of the planning process for construction scheduling?
By subtracting a measured unit productivity rate during an impacted period from the unit productivity rate during an unimpacted period, the resulting value represents:
Assuming activities 2001 through 2004 comprise the same WBS element, construct a WBS summary activity for activities 2001 through 2004. Use the normal schedule, what is the cost of the activity?
Which of the following types of delay will NOT result in a time extension and additional compensation for a contractor?
For activity 11001. why would the crashed direct cost be greater than the direct cost of the normal schedule?
In a graphical earned value analysis, what time-scaled value determines the reporting intervals for both schedule and cost performance?
Which of the following parties is NOT a stakeholder of the Spring Highway project?
If Activity A was delayed 5 days from starting, which of the following adjustments will NOT maintain the completion date of Activity C at Day 40?
When project risk is reflected in scheduled activities, what is the most significant characteristic of those activities?
At the end of month one, did the delay to the parking structure foundation delay the project?
You are the project manager of the AHQ project. This project is scheduled to last for six months and will require S345.000 to complete. If the project completes earlier than scheduled your organization will receive a bonus of S5 000 per day of early completion Management has asked you to develop an aggressive schedule to realize as much of the bonus as possible but management does not want you to increase the costs of the project beyond $1,000 per day of the bonus realization. Which of the following approaches will likely add costs to the project?
SUBCO is a potential concrete bridge contractor based in a metropolitan area 300 miles away from your project. They have offered to supply manpower and equipment t BILCO at a per diem rate of $3,000 above their direct labor and equipment rates. In doing a cost benefit analysis, which of the following is NOT a consideration?
Using a 1.75 cubic yard [1.34 cubic meter] bucket, how many lifts does it take to pour each 2.000-cubic foot [56.64 cubic meter] column?
You are developing a detailed critical path schedule for a proposed petrochemical plant. The schedule will become a part of the project baseline document, which will be sent to the company's board of directors for its consideration. What document or resource is likely to be MOST valuable in determining the schedule's work activity durations?