What are two core values of the Palo Alto Network Security Operating Platform? (Choose two.}
Which statement applies to Palo Alto Networks Single Pass Parallel Processing (SP3)?
Which built-in feature of PAN-OS allows the NGFW administrator to create a policy that provides autoremediation for anomalous user behavior and malicious activity while maintaining user visibility?
The need for a file proxy solution, virus and spyware scanner, a vulnerability scanner, and HTTP decoder for URL filtering is handled by which component in the NGFW?
Which three signature-based Threat Prevention features of the firewall are informed by intelligence from the Threat Intelligence Cloud? (Choose three.)
In Panorama, which three reports or logs will help identify the inclusion of a host source in a command-and-control (C2) incident? (Choose three.)
Which two email links, contained in SMTP and POP3, can be submitted from WildFire analysis with a WildFire subscription? (Choose two.)
WildFire can discover zero-day malware in which three types of traffic? (Choose three)
A customer is starting to understand their Zero Trust protect surface using the Palo Alto Networks Zero Trust reference architecture.
What are two steps in this process? (Choose two.)
Which two types of security chains are supported by the Decryption Broker? (Choose two.)
Which solution informs a customer concerned about zero-day targeted attacks whether an attack is specifically targeted at its property?
A customer has business-critical applications that rely on the general web-browsing application. Which security profile can help prevent drive-by-downloads while still allowing web-browsing traffic?
A customer is concerned about zero-day targeted attacks against its intellectual property.
Which solution informs a customer whether an attack is specifically targeted at them?
A customer is looking for an analytics tool that uses the logs on the firewall to detect actionable events on the network. They require something to automatically process a series of related threat events that, when combined, indicate a likely compromised host on their network or some other higher level conclusion. They need to pinpoint the area of risk, such as compromised hosts on the network, allows you to assess the risk and take action to prevent exploitation of network resources.
Which feature of PAN-OS can you talk about to address their requirement to optimize their business outcomes?
When HTTP header logging is enabled on a URL Filtering profile, which attribute-value can be logged?
Which CLI command will allow you to view latency, jitter and packet loss on a virtual SD-WAN interface?
A)
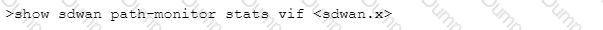
B)
C)

D)

Which Security profile on the Next-Generation Firewall (NGFW) includes Signatures to protect against brute force attacks?
A customer with a fully licensed Palo Alto Networks firewall is concerned about threats based on domain generation algorithms (DGAS).
Which Security profile is used to configure Domain Name Security (DNS) to Identity and block
previously unknown DGA-based threats in real time?
What are three sources of malware sample data for the Threat Intelligence Cloud? (Choose three)
A customer requires an analytics tool with the following attributes:
- Uses the logs on the firewall to detect actionable events on the network
- Automatically processes a series of related threat events that, when combines, indicate a likely comprised host on the network
- Pinpoints the area of risk and allows for assessment of the risk to action can be taken to prevent exploitation of network resources
Which feature of PAN-OS will address these requirements?
An administrator wants to justify the expense of a second Panorama appliance for HA of the management layer.
The customer already has multiple M-100s set up as a log collector group. What are two valid reasons for deploying Panorama in High Availability? (Choose two.)
XYZ Corporation has a legacy environment with asymmetric routing. The customer understands that Palo Alto Networks firewalls can support asymmetric routing with redundancy.
Which two features must be enabled to meet the customer’s requirements? (Choose two.)
Palo Alto Networks publishes updated Command-and-Control signatures. How frequently should the related signatures schedule be set?
What are three purposes for the Eval Systems, Security Lifecycle Reviews and Prevention Posture Assessment tools? (Choose three.)
Which selection must be configured on PAN-OS External Dynamic Lists to support MineMeld indicators?
Which three components are specific to the Query Builder found in the Custom Report creation dialog of the firewall? (Choose three.)
Which functionality is available to firewall users with an active Threat Prevention subscription, but no WildFire license?
Which component is needed for a large-scale deployment of NGFWs with multiple Panorama Management Servers?
Which filtering criterion is used to determine users to be included as members of a dynamic user group (DUG)?
Which domain permissions are required by the User-ID Agent for WMI Authentication on a Windows Server? (Choose three.)
Which three platform components can identify and protect against malicious email links? (Choose three.)
Which three of the following actions must be taken to enable Credential Phishing Prevention? (Choose three.)
Which two network events are highlighted through correlation objects as potential security risks? (Choose two.)
What are the three possible verdicts in WildFire Submissions log entries for a submitted sample? (Choose four.)
When the Cortex Data Lake is sized for Traps Management Service, which two factors should be considered? (Choose two.)