A security engineer wants to upgrade the company's deployed firewalls from PAN-OS 10.1 to 11.0.x to take advantage of the new TLSvl.3 support for management access.
What is the recommended upgrade path procedure from PAN-OS 10.1 to 11.0.x?
An administrator notices that an interface configuration has been overridden locally on a firewall. They require all configuration to be managed from Panorama and overrides are not allowed. What is one way the administrator can meet this requirement?
Which two components are required to configure certificate-based authentication to the web Ul when an administrator needs firewall access on a trusted interface'? (Choose two.)
An engineer is troubleshooting a traffic-routing issue.
What is the correct packet-flow sequence?
When a new firewall joins a high availability (HA) cluster, the cluster members will synchronize all existing sessions over which HA port?
An administrator plans to install the Windows User-ID agent on a domain member system.
What is a best practice for choosing where to install the User-ID agent?
An engineer needs to configure a standardized template for all Panorama-managed firewalls. These settings will be configured on a template named "Global" and will be included in all template stacks.
Which three settings can be configured in this template? (Choose three.)
Which log type would provide information about traffic blocked by a Zone Protection profile?
A network security engineer needs to enable Zone Protection in an environment that makes use of Cisco TrustSec Layer 2 protections
What should the engineer configure within a Zone Protection profile to ensure that the TrustSec packets are identified and actions are taken upon them?
An administrator configures a site-to-site IPsec VPN tunnel between a PA-850 and an external customer on their policy-based VPN devices.
What should an administrator configure to route interesting traffic through the VPN tunnel?
An administrator troubleshoots an issue that causes packet drops.
Which log type will help the engineer verify whether packet buffer protection was activated?
A security team has enabled real-time WildFire signature lookup on all its firewalls. Which additional action will further reduce the likelihood of newly discovered malware being allowed through the firewalls?
When an engineer configures an active/active high availability pair, which two links can they use? (Choose two)
An internal audit team has requested additional information to be included inside traffic logs forwarded from Palo Alto Networks firewalls to an interal syslog server. Where can the firewall engineer define the data to be added into each forwarded log?
A security engineer needs firewall management access on a trusted interface.
Which three settings are required on an SSL/TLS Service Profile to provide secure Web UI authentication? (Choose three.)
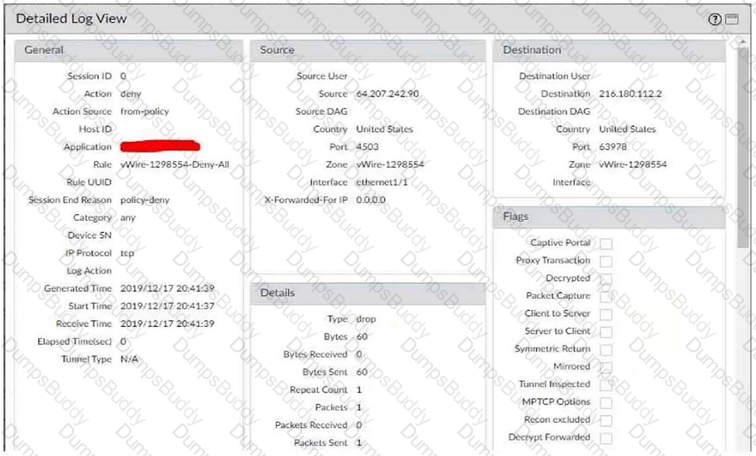
Refer to the exhibit.
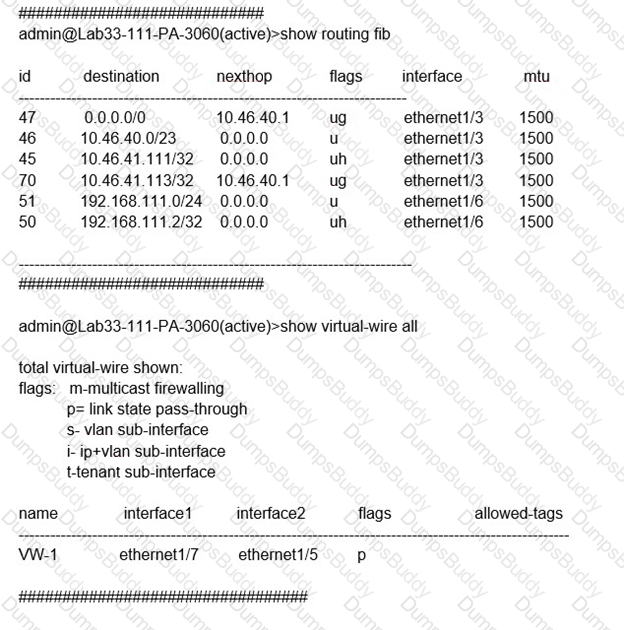
Which will be the egress interface if the traffic's ingress interface is ethernet1/7 sourcing from 192.168.111.3 and to the destination 10.46.41.113?
How is Perfect Forward Secrecy (PFS) enabled when troubleshooting a VPN Phase 2 mismatch?
A firewall engineer has determined that, in an application developed by the company's internal team, sessions often remain idle for hours before the client and server exchange any data. The application is also currently identified as unknown-tcp by the firewalls. It is determined that because of a high level of trust, the application does not require to be scanned for threats, but it needs to be properly identified in Traffic logs for reporting purposes.
Which solution will take the least time to implement and will ensure the App-ID engine is used to identify the application?
A company is expanding its existing log storage and alerting solutions All company Palo Alto Networks firewalls currently forward logs to Panorama. Which two additional log forwarding methods will PAN-OS support? (Choose two)
A firewall administrator has configured User-ID and deployed GlobalProtect, but there is no User-ID showing in the traffic logs.
How can the administrator ensure that User-IDs are populated in the traffic logs?
Which tool will allow review of the policy creation logic to verify that unwanted traffic is not allowed?
Which configuration change will improve network reliability and ensure minimal disruption during tunnel failures?
Which two actions must an engineer take to configure SSL Forward Proxy decryption? (Choose two.)
Which three items must be configured to implement application override? (Choose three )
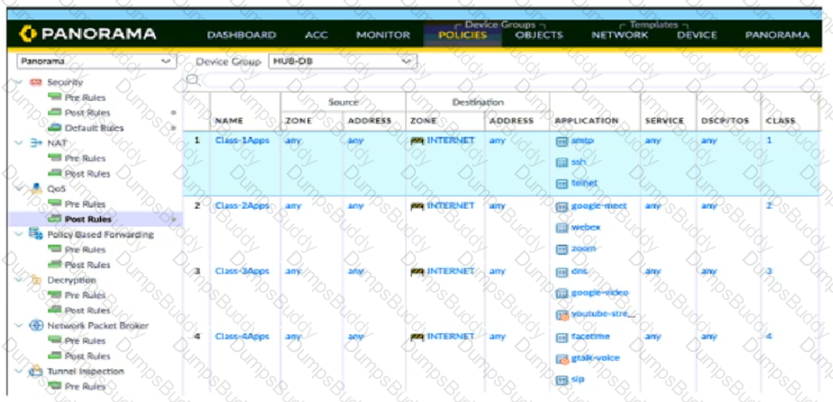
Refer to the exhibit.
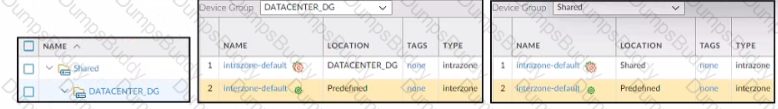
Based on the screenshots above what is the correct order in which the various rules are deployed to firewalls inside the DATACENTER_DG device group?
Which function does the HA4 interface provide when implementing a firewall cluster which contains firewalls configured as active-passive pairs?
An administrator is attempting to create policies tor deployment of a device group and template stack. When creating the policies, the zone drop down list does not include the required zone.
What must the administrator do to correct this issue?
Which statement accurately describes how web proxy is run on a firewall with multiple virtual systems?
An administrator connects a new fiber cable and transceiver Ethernet1/1 on a Palo Alto Networks firewall. However, the link does not come up. How can the administrator troubleshoot to confirm the transceiver type, tx-power, rxpower, vendor name, and part number by using the CLI?
A firewall architect is attempting to install a new Palo Alto Networks NGFW. The company has previously had issues moving all administrative functions onto a data plane interface to meet the design limitations of the environment. The architect is able to access the device for HTTPS and SSH; however, the NGFW can neither validate licensing nor get updates. Which action taken by the architect will resolve this issue?
Which GlobalProtect gateway selling is required to enable split-tunneling by access route, destination domain, and application?
If an administrator wants to apply QoS to traffic based on source, what must be specified in a QoS policy rule?
When you import the configuration of an HA pair into Panorama, how do you prevent the import from affecting ongoing traffic?
A company wants to add threat prevention to the network without redesigning the network routing.
What are two best practice deployment modes for the firewall? (Choose two.)
An engineer troubleshooting a VPN issue needs to manually initiate a VPN tunnel from the CLI Which CLI command can the engineer use?
A firewall administrator is configuring an IPSec tunnel between a company's HQ and a remote location. On the HQ firewall, the interface used to terminate the IPSec tunnel has a static IP. At the remote location, the interface used to terminate the IPSec tunnel has a DHCP assigned IP address.
Which two actions are required for this scenario to work? (Choose two.)
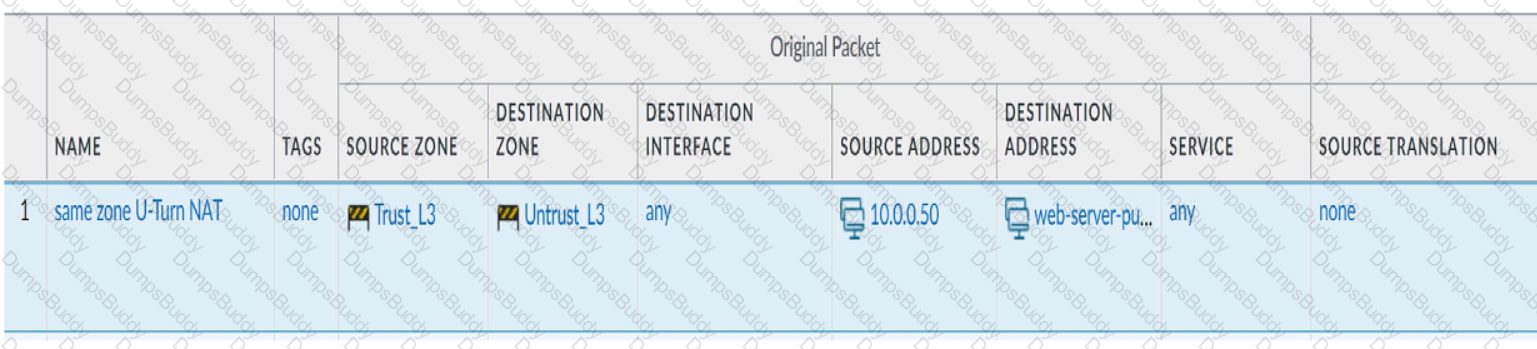
Review the information below. A firewall engineer creates a U-NAT rule to allow users in the trust zone access to a server in the same zone by using an external,
public NAT IP for that server.
Given the rule below, what change should be made to make sure the NAT works as expected?
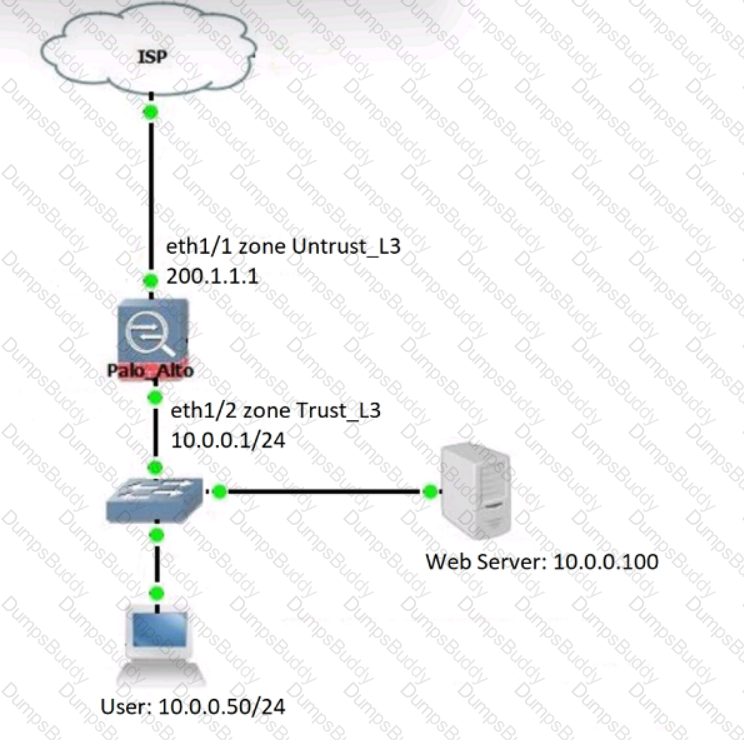
An engineer is deploying multiple firewalls with common configuration in Panorama.
What are two benefits of using nested device groups? (Choose two.)
A company is deploying User-ID in their network. The firewall team needs to have the ability to see and choose from a list of usernames and user groups directly inside the Panorama policies when creating new security rules.
How can this be achieved?
A company has configured a URL Filtering profile with override action on their firewall. Which two profiles are needed to complete the configuration? (Choose two)
A network engineer troubleshoots a VPN Phase 2 mismatch and decides that PFS (Perfect Forward Secrecy) needs to be enabled. What action should the engineer take?
A security engineer needs to mitigate packet floods that occur on a RSF servers behind the internet facing interface of the firewall. Which Security Profile should be applied to a policy to prevent these packet floods?
A firewall administrator configures the HIP profiles on the edge firewall where GlobalProtect is enabled, and adds the profiles to security rules. The administrator wants to redistribute the HIP reports to the data center firewalls to apply the same access restrictions using HIP profiles. However, the administrator can only see the HIP match logs on the edge firewall but not on the data center firewall
What are two reasons why the administrator is not seeing HIP match logs on the data center firewall? (Choose two.)
An engineer configures a destination NAT policy to allow inbound access to an internal server in the DMZ. The NAT policy is configured with the following values:
- Source zone: Outside and source IP address 1.2.2.2
- Destination zone: Outside and destination IP address 2.2.2.1
The destination NAT policy translates IP address 2.2.2.1 to the real IP address 10.10.10.1 in the DMZ zone.
Which destination IP address and zone should the engineer use to configure the security policy?
Which two key exchange algorithms consume the most resources when decrypting SSL traffic? (Choose two)
Users have reported an issue when they are trying to access a server on your network. The requests aren’t taking the expected route. You discover that there are two different static routes on the firewall for the server. What is used to determine which route has priority?
With the default TCP and UDP settings on the firewall, what will be the identified application in the following session?
An engineer is configuring a Protection profile to defend specific endpoints and resources against malicious activity.
The profile is configured to provide granular defense against targeted flood attacks for specific critical systems that are accessed by users from the internet.
Which profile is the engineer configuring?
Exhibit.
An organization has Palo Alto Networks NGFWs that send logs to remote monitoring and security management platforms The network team has reported excessive traffic on the corporate WAN How could the Palo Alto Networks NGFW administrator reduce WAN traffic while maintaining support for all the existing monitoring/security platforms?
A customer would like to support Apple Bonjour in their environment for ease of configuration.
Which type of interface in needed on their PA-3200 Series firewall to enable Bonjour Reflector in a segmented network?
Which feature of Panorama allows an administrator to create a single network configuration that can be reused repeatedly for large-scale deployments even if values of configured objects, such as routes and interface addresses, change?
An engineer needs to permit XML API access to a firewall for automation on a network segment that is routed through a Layer 3 sub-interface on a Palo Alto Networks firewall. However, this network segment cannot access the dedicated management interface due to the Security policy.
Without changing the existing access to the management interface, how can the engineer fulfill this request?
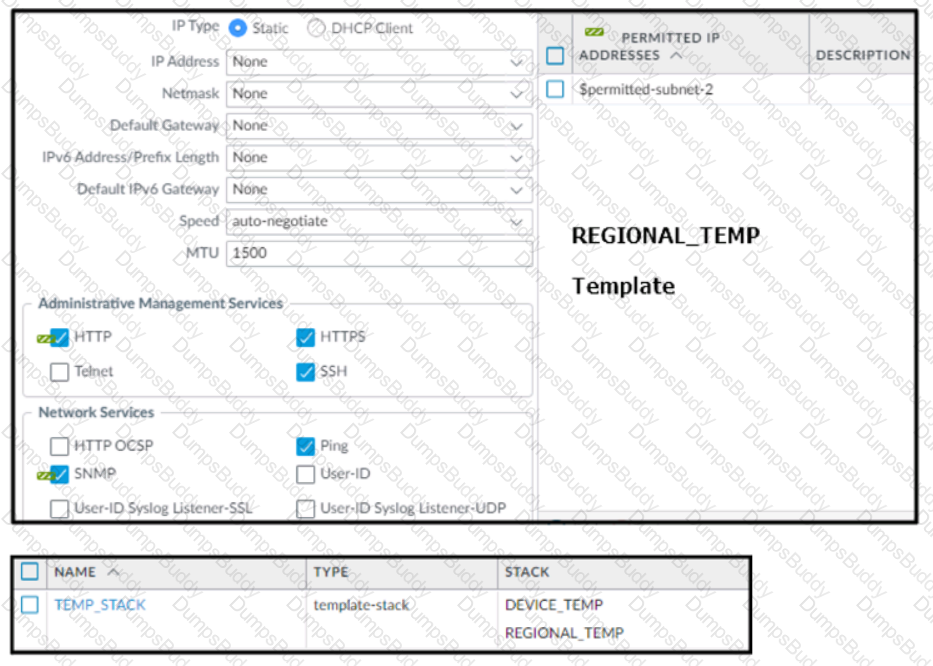
Based on the screenshots above, and with no configuration inside the Template Stack itself, what access will the device permit on its Management port?
View the screenshots
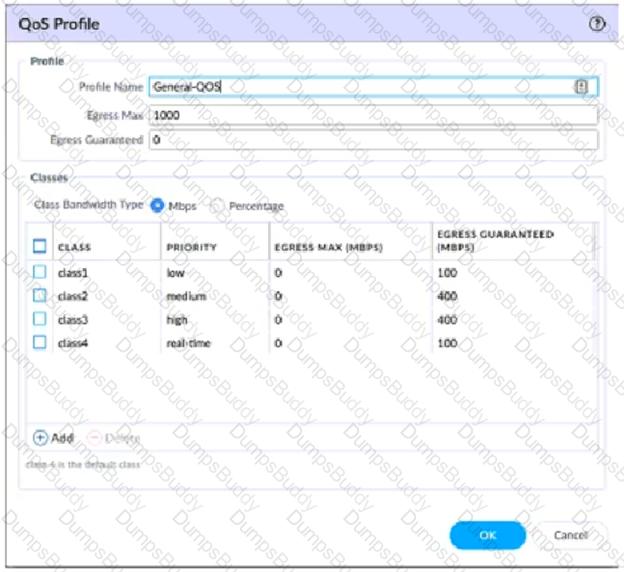
A QoS profile and policy rules are configured as shown. Based on this information which two statements are correct?
An administrator is building Security rules within a device group to block traffic to and from malicious locations.
How should those rules be configured to ensure that they are evaluated with a high priority?
A new firewall has the Threat Prevention subscription, but the Antivirus does not appear in Dynamic Updates.
What must occur to have Antivirus signatures update?
Which statement explains the difference between using the PAN-OS integrated User-ID agent and the standalone User-ID agent when using Active Directory for user-to-IP mapping?
An administrator wants to enable WildFire inline machine learning. Which three file types does WildFire inline ML analyze? (Choose three.)
Which three methods are supported for split tunneling in the GlobalProtect Gateway? (Choose three.)
What are three tasks that cannot be configured from Panorama by using a template stack? (Choose three.)
An administrator configures HA on a customer's Palo Alto Networks firewalls with path monitoring by using the default configuration values.
What are the default values for ping interval and ping count before a failover is triggered?
An administrator notices interface ethernet1/2 failed on the active firewall in an active / passive firewall high availability (HA) pair Based on the image below what - if any - action was taken by the active firewall when the link failed?
A customer requires that virtual systems with separate virtual routers can communicate with one another within a Palo Alto Networks firewall. In addition to confirming Security policies, which three configurations will accomplish this goal? (Choose three)
Review the screenshots.
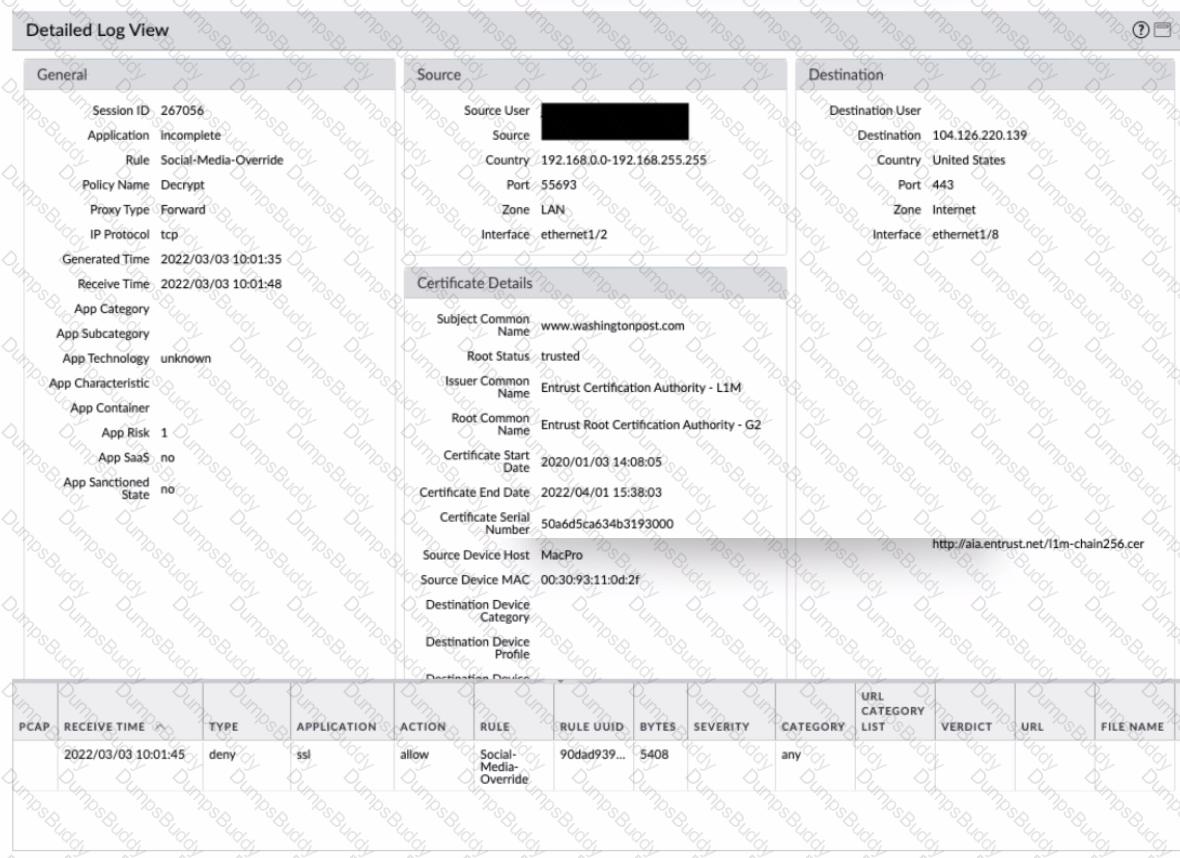
What is the most likely reason for this decryption error log?
An administrator is assisting a security engineering team with a decryption rollout for inbound and forward proxy traffic. Incorrect firewall sizing is preventing the team from decrypting all of the traffic they want to decrypt. Which three items should be prioritized for decryption? (Choose three.)
When you troubleshoot an SSL Decryption issue, which PAN-OS CL1 command do you use to check the details of the Forward Trust certificate. Forward Untrust certificate, and SSL Inbound Inspection certificate?
A firewall engineer is investigating high dataplane CPU utilization. To decrease the load on this CPU, what should be reduced?
A decryption policy has been created with an action of "No Decryption." The decryption profile is configured in alignment to best practices.
What protections does this policy provide to the enterprise?
Users are intermittently being cut off from local resources whenever they connect to GlobalProtect. After researching, it is determined that this is caused by an incorrect setting on one of the NGFWs. Which action will resolve this issue?
Which Panorama mode should be used so that all logs are sent to. and only stored in. Cortex Data Lake?
Panorama is being used to upgrade the PAN-OS version on a pair of firewalls in an active/passive high availability (HA) configuration. The Palo Alto Networks best practice upgrade steps have been completed in Panorama (Panorama upgraded, backups made, content updates, and disabling "Preemptive" pushed), and the firewalls are ready for upgrade. What is the next best step to minimize downtime and ensure a smooth transition?
A network administrator wants to deploy SSL Forward Proxy decryption. What two attributes should a forward trust certificate have? (Choose two.)
An engineer configures a new template stack for a firewall that needs to be deployed. The template stack should consist of four templates arranged according to the diagram

Which template values will be configured on the firewall If each template has an SSL/TLS Service profile configured named Management?
An engineer is designing a deployment of multi-vsys firewalls.
What must be taken into consideration when designing the device group structure?
An engineer is monitoring an active/active high availability (HA) firewall pair.
Which HA firewall state describes the firewall that is experiencing a failure of a monitored path?
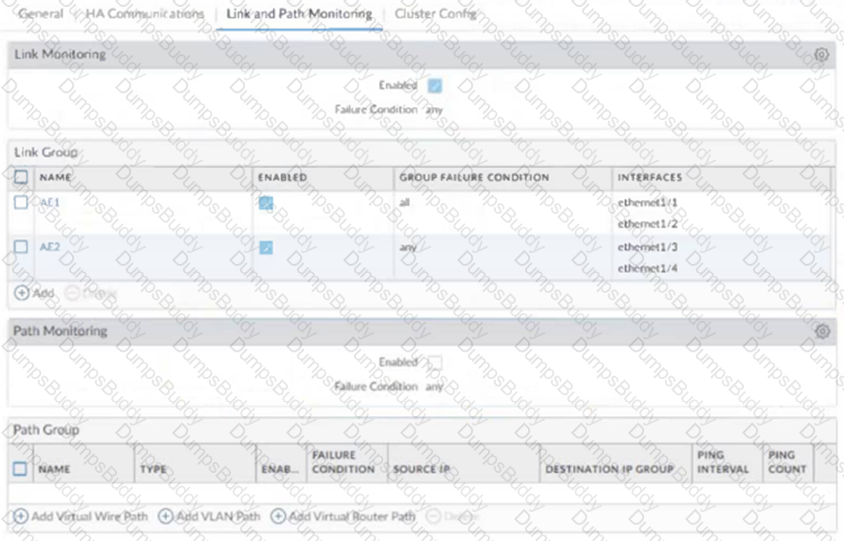
An administrator has configured a pair of firewalls using high availability in Active/Passive mode. Link and Path Monitoring is enabled with the Failure Condition set to "any." There is one link group configured containing member interfaces ethernet1/1 and ethernet1/2 with a Group Failure Condition set to "all."
Which HA state will the Active firewall go into if ethernet1/1 link goes down due to a failure?'
A company wants to use GlobalProtect as its remote access VPN solution.
Which GlobalProtect features require a Gateway license?
A firewall administrator has confirm reports of a website is not displaying as expected, and wants to ensure that decryption is not causing the issue. Which three methods can the administrator use to determine if decryption is causing the website to fail? (Choose three.)
A system administrator runs a port scan using the company tool as part of vulnerability check. The administrator finds that the scan is identified as a threat and is dropped by the firewall. After further investigating the logs, the administrator finds that the scan is dropped in the Threat Logs.
An organization is interested in migrating from their existing web proxy architecture to the Web Proxy feature of their PAN-OS 11.0 firewalls. Currently. HTTP and SSL requests contain the c IP address of the web server and the client browser is redirected to the proxy
Which PAN-OS proxy method should be configured to maintain this type of traffic flow?
An engineer manages a high availability network and requires fast failover of the routing protocols. The engineer decides to implement BFD.
Which three dynamic routing protocols support BFD? (Choose three.)
An engineer creates a set of rules in a Device Group (Panorama) to permit traffic to various services for a specific LDAP user group.
What needs to be configured to ensure Panorama can retrieve user and group information for use in these rules?
An organization conducts research on the benefits of leveraging the Web Proxy feature of PAN-OS 11.0.
What are two benefits of using an explicit proxy method versus a transparent proxy method? (Choose two.)
An administrator plans to install the Windows-Based User-ID Agent to prevent credential phishing.
Which installer package file should the administrator download from the support site?
An administrator plans to install the Windows-Based User-ID Agent.
What type of Active Directory (AD) service account should the administrator use?
An administrator is creating a new Dynamic User Group to quarantine users for suspicious activity.
Which two objects can Dynamic User Groups use as match conditions for group membership? (Choose two.)
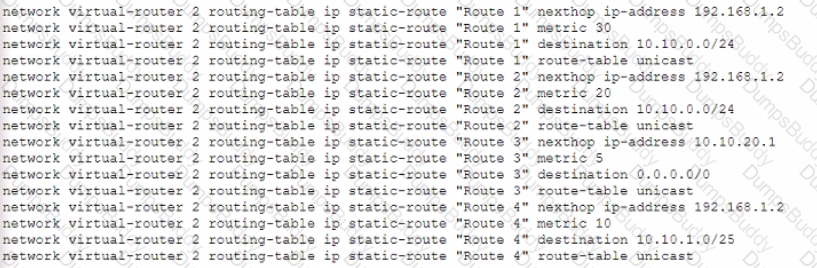
Given the following configuration, which route is used for destination 10 10 0 4?
A company wants to implement threat prevention to take action without redesigning the network routing.
What are two best practice deployment modes for the firewall? (Choose two.)
An engineer configures a specific service route in an environment with multiple virtual systems instead of using the inherited global service route configuration.
What type of service route can be used for this configuration?
An existing log forwarding profile is currently configured to forward all threat logs to Panorama. The firewall engineer wants to add syslog as an additional log forwarding method. The requirement is to forward only medium or higher severity threat logs to syslog. Forwarding to Panorama must not be changed.
Which set of actions should the engineer take to achieve this goal?
An engineer troubleshoots a Panorama-managed firewall that is unable to reach the DNS servers configured via a global template. As a troubleshooting step, the engineer needs to configure a local DNS server in place of the template value.
Which two actions can be taken to ensure that only the specific firewall is affected during this process? (Choose two )
A network administrator notices a false-positive state after enabling Security profiles. When the administrator checks the threat prevention logs, the related signature displays the following:
threat type: spyware category: dns-c2 threat ID: 1000011111
Which set of steps should the administrator take to configure an exception for this signature?