Which two elements are included in the audit trail section of the asset detail view? (Choose two).
Which two CI/CD plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.).
Which two proper agentless scanning modes are supported with Prisma Cloud? (Choose two).
An administrator has a requirement to ingest all Console and Defender logs to Splunk.
Which option will satisfy this requirement in Prisma Cloud Compute?
In WAAS Access control file upload controls, which three file types are supported out of the box? (Choose three.)
Which API calls can scan an image named myimage: latest with twistcli and then retrieve the results from Console?
What must be created in order to receive notifications about alerts generated when the operator is away from the Prisma Cloud Console?
A security team has a requirement to ensure the environment is scanned for vulnerabilities. What are three options for configuring vulnerability policies? (Choose three.)
Which role must be assigned to DevOps users who need access to deploy Container and Host Defenders in Compute?
Which two processes ensure that builds can function after a Console upgrade? (Choose two.)
A security team is deploying Cloud Native Application Firewall (CNAF) on a containerized web application. The application is running an NGINX container. The container is listening on port 8080 and is mapped to host port 80.
Which port should the team specify in the CNAF rule to protect the application?
A customer does not want alerts to be generated from network traffic that originates from trusted internal networks.
Which setting should you use to meet this customer’s request?
You have onboarded a public cloud account into Prisma Cloud Enterprise. Configuration Resource ingestion is visible in the Asset Inventory for the onboarded account, but no alerts are being generated for the configuration assets in the account.
Config policies are enabled in the Prisma Cloud Enterprise tenant, with those policies associated to existing alert rules. ROL statements on the investigate matching those policies return config resource results successfully.
Why are no alerts being generated?
A business unit has acquired a company that has a very large AWS account footprint. The plan is to immediately start onboarding the new company’s AWS accounts into Prisma Cloud Enterprise tenant immediately. The current company is currently not using AWS Organizations and will require each account to be onboarded individually.
The business unit has decided to cover the scope of this action and determined that a script should be written to onboard each of these accounts with general settings to gain immediate posture visibility across the accounts.
Which API endpoint will specifically add these accounts into the Prisma Cloud Enterprise tenant?
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
Which two options may be used to upgrade the Defenders with a Console v20.04 and Kubernetes deployment? (Choose two.)
A customer has a large environment that needs to upgrade Console without upgrading all Defenders at one time.
What are two prerequisites prior to performing a rolling upgrade of Defenders? (Choose two.)
During the Learning phase of the Container Runtime Model, Prisma Cloud enters a “dry run” period for how many hours?
A customer has a requirement to scan serverless functions for vulnerabilities.
What is the correct option to configure scanning?
Which serverless cloud provider is covered by the "overly permissive service access" compliance check?
An administrator has been tasked with creating a custom service that will download any existing compliance report from a Prisma Cloud Enterprise tenant.
In which order will the APIs be executed for this service?
(Drag the steps into the correct order of occurrence, from the first step to the last.)

Per security requirements, an administrator needs to provide a list of people who are receiving e-mails for Prisma Cloud alerts.
Where can the administrator locate this list of e-mail recipients?
Which three Orchestrator types are supported when deploying Defender? (Choose three.)
The compliance team needs to associate Prisma Cloud policies with compliance frameworks. Which option should the team select to perform this task?
The security team wants to protect a web application container from an SQLi attack. Which type of policy should the administrator create to protect the container?
Which Prisma Cloud policy type detects port scanning activities in a customer environment?
Which action would be applicable after enabling anomalous compute provisioning?
Prisma Cloud supports which three external systems that allow the import of vulnerabilities and provide additional context on risks in the cloud? (Choose three.)
Given the following RQL:
Which audit event snippet is identified by the RQL?
A)
B)
C)
D)
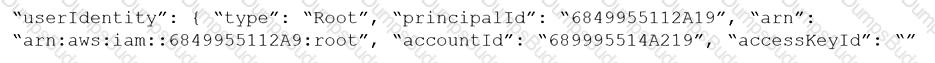
An administrator sees that a runtime audit has been generated for a container.
The audit message is:
“/bin/ls launched and is explicitly blocked in the runtime rule. Full command: ls -latr”
Which protection in the runtime rule would cause this audit?
A customer wants to harden its environment from misconfiguration.
Prisma Cloud Compute Compliance enforcement for hosts covers which three options? (Choose three.)
During an initial deployment of Prisma Cloud Compute, the customer sees vulnerabilities in their environment.
Which statement correctly describes the default vulnerability policy?
In Azure, what permissions need to be added to Management Groups to allow Prisma Cloud to calculate net effective permissions?
Which of the following are correct statements regarding the use of access keys? (Choose two.)
Which categories does the Adoption Advisor use to measure adoption progress for Cloud Security Posture Management?
A customer's Security Operations Center (SOC) team wants to receive alerts from Prisma Cloud via email once a day about all policies that have a violation, rather than receiving an alert every time a new violation occurs.
Which alert rule configuration meets this requirement?
A customer has a requirement to terminate any Container from image topSecret:latest when a process named ransomWare is executed.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
A customer has a development environment with 50 connected Defenders. A maintenance window is set for Monday to upgrade 30 stand-alone Defenders in the development environment, but there is no maintenance window available until Sunday to upgrade the remaining 20 stand-alone Defenders.
Which recommended action manages this situation?
Which set of steps is the correct process for obtaining Console images for Prisma Cloud Compute Edition?
A customer wants to monitor the company’s AWS accounts via Prisma Cloud, but only needs the resource configuration to be monitored for now.
Which two pieces of information do you need to onboard this account? (Choose two.)
Given the following RQL:
event from cloud.audit_logs where operation IN (‘CreateCryptoKey’, ‘DestroyCryptoKeyVersion’, ‘v1.compute.disks.createSnapshot’)
Which audit event snippet is identified?
A)
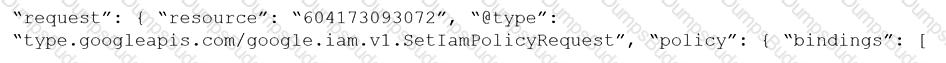
B)
C)
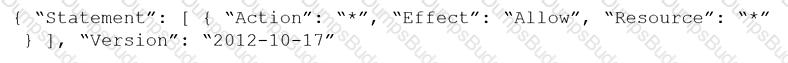
D)

Which action must be taken to enable a user to interact programmatically with the Prisma Cloud APIs and for a nonhuman entity to be enabled for the access keys?
A customer wants to scan a serverless function as part of a build process. Which twistcli command can be used to scan serverless functions?
Given an existing ECS Cluster, which option shows the steps required to install the Console in Amazon ECS?
When configuring SSO how many IdP providers can be enabled for all the cloud accounts monitored by Prisma Cloud?
Which ban for DoS protection will enforce a rate limit for users who are unable to post five (5) “. tar.gz" files within five (5) seconds?
Match the correct scanning mode for each given operation.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
A customer has a requirement to scan serverless functions for vulnerabilities.
Which three settings are required to configure serverless scanning? (Choose three.)
How are the following categorized?
Backdoor account access Hijacked processes Lateral movement
Port scanning
Which ROL query is used to detect certain high-risk activities executed by a root user in AWS?
A Prisma Cloud Administrator needs to enable a Registry Scanning for a registry that stores Windows images. Which of the following statement is correct regarding this process?
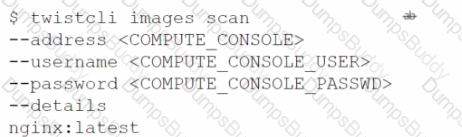
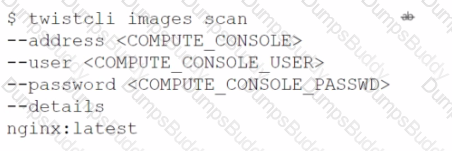
Which command should be used in the Prisma Cloud twistcli tool to scan the nginx:latest image for vulnerabilities and compliance issues?
A)
B)
C)
D)
Which two services require external notifications to be enabled for policy violations in the Prisma Cloud environment? (Choose two.)
Which two statements explain differences between build and run config policies? (Choose two.)
Which three steps are involved in onboarding an account for Data Security? (Choose three.)
An administrator sees that a runtime audit has been generated for a Container. The audit message is “DNS resolution of suspicious name wikipedia.com. type A”.
Why would this message appear as an audit?
Which three options are selectable in a CI policy for image scanning with Jenkins or twistcli? (Choose three.)
You are tasked with configuring a Prisma Cloud build policy for Terraform. What type of query is necessary to complete this policy?
Which two bot types are part of Web Application and API Security (WAAS) bot protection? (Choose two.)
A customer has multiple violations in the environment including:
User namespace is enabled
An LDAP server is enabled
SSH root is enabled
Which section of Console should the administrator use to review these findings?