A Vault Administrator team member can log in to CyberArk, but for some reason, is not given Vault Admin rights.
Where can you check to verify that the Vault Admins directory mapping points to the correct AD group?
It is possible to restrict the time of day, or day of week that a [b]verify[/b] process can occur
In addition to add accounts and update account contents, which additional permission on the safe is required to add a single account?
Which authorizations are required in a recording safe to allow a group to view recordings?

You notice an authentication failure entry for the DR user in the ITALog.
What is the correct process to fix this error? (Choose two.)
Which command configures email alerts within PTA if settings need to be changed post install?
If PTA is integrated with a supported SIEM solution, which detection becomes available?
Target account platforms can be restricted to accounts that are stored m specific Safes using the Allowed Safes property.
Where can a user with the appropriate permissions generate a report? (Choose two.)
A user needs to view recorded sessions through the PVWA.
Without giving auditor access, which safes does a user need access to view PSM recordings? (Choose two.)
Which keys are required to be present in order to start the PrivateArk Server service?
Users are unable to launch Web Type Connection components from the PSM server. Your manager asked you to open the case with CyberArk Support.
Which logs will help the CyberArk Support Team debug the issue? (Choose three.)
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password.
What is the least intrusive way to accomplish this?

What are the mandatory fields when onboarding from Pending Accounts? (Choose two.)
To change the safe where recordings are kept for a specific platform, which setting must you update in the platform configuration?
In a rule using “Privileged Session Analysis and Response” in PTA, which session options are available to configure as responses to activities?
Via Password Vault Web Access (PVWA), a user initiates a PSM connection to the target Linux machine using RemoteApp. When the client’s machine makes an RDP connection to the PSM server, which user will be utilized?
Before failing back to the production infrastructure after a DR exercise, what must you do to maintain audit history during the DR event?
A new domain controller has been added to your domain. You need to ensure the CyberArk infrastructure can use the new domain controller for authentication.
Which locations must you update?
CyberArk implements license limits by controlling the number and types of users that can be provisioned in the vault.
Your organization has a requirement to allow users to “check out passwords” and connect to targets with the same account through the PSM.
What needs to be configured in the Master policy to ensure this will happen?
Which of the following files must be created or configured m order to run Password Upload Utility? Select all that apply.
Which of the following Privileged Session Management solutions provide a detailed audit log of session activities?
Which service should NOT be running on the DR Vault when the primary Production Vault is up?
If a user is a member of more than one group that has authorizations on a safe, by default that user is granted________.
Match the Status of Service on a DR Vault to what is displayed when it is operating normally in Replication mode.

When a DR Vault Server becomes an active vault, it will automatically revert back to DR mode once the Primary Vault comes back online.
A new colleague created a directory mapping between the Active Directory groups and the Vault.
Where can the newly Configured directory mapping be tested?
Time of day or day of week restrictions on when password verifications can occur configured in ____________________.
You want to build a connector that connects to a website through the Web applications for PSM framework.
Which default connector do you duplicate and modify?
Assuming a safe has been configured to be accessible during certain hours of the day, a Vault Admin may still access that safe outside of those hours.
You created a new safe and need to ensure the user group cannot see the password, but can connect through the PSM.
Which safe permissions must you grant to the group? (Choose two.)
Due to corporate storage constraints, you have been asked to disable session monitoring and recording for 500 testing accounts used for your lab environment.
How do you accomplish this?
When a DR Vault Server becomes an active vault, it will automatically fail back to the original state once the Primary Vault comes back online.
What is the maximum number of levels of authorization you can set up in Dual Control?
ADR Vault became active due to a failure of the primary Vault. Service on the primary Vault has now been restored. Arrange the steps to return the DR vault to its normal standby mode in the correct sequence.
A Simple Mail Transfer Protocol (SMTP) integration is critical for monitoring Vault activity and facilitating workflow processes, such as Dual Control.
Which of the Following can be configured in the Master Poky? Choose all that apply.
A new HTML5 Gateway has been deployed in your organization.
From the PVWA, arrange the steps to configure a PSM host to use the HTML5 Gateway in the correct sequence.

Which Cyber Are components or products can be used to discover Windows Services or Scheduled Tasks that use privileged accounts? Select all that apply.
What is required to enable access over SSH to a Unix account through both PSM and PSMP?
Which methods can you use to add a user directly to the Vault Admin Group? (Choose three.)
Which of the following properties are mandatory when adding accounts from a file? (Choose three.)
Which built-in report from the reports page in PVWA displays the number of days until a password is due to expire?
According to the DEFAULT Web Options settings, which group grants access to the REPORTS page?
Which type of automatic remediation can be performed by the PTA in case of a suspected credential theft security event?
Which statement is correct concerning accounts that are discovered, but cannot be added to the Vault by an automated onboarding rule?
When an account is unable to change its own password, how can you ensure that password reset with the reconcile account is performed each time instead of a change?
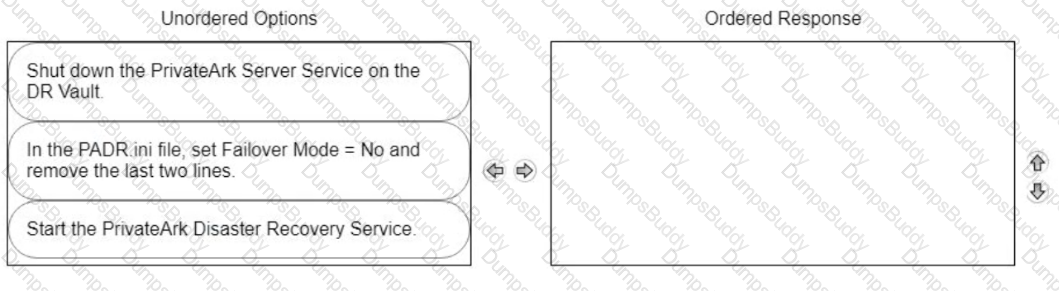
Due to network activity, ACME Corp’s PrivateArk Server became active on the OR Vault while the Primary Vault was also running normally. All the components continued to point to the Primary Vault.
Which steps should you perform to restore DR replication to normal?
You created a new platform by duplicating the out-of-box Linux through the SSH platform.
Without any change, which Text Recorder Type(s) will the new platform support? (Choose two.)