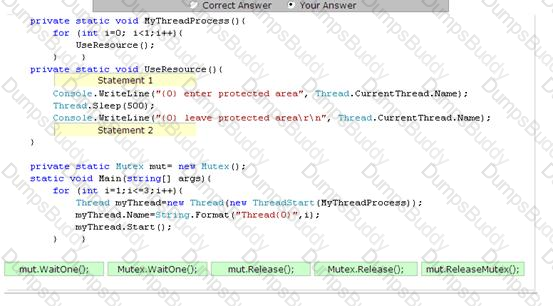
You work as a Software Developer for ManSoft Inc. The company uses Visual Studio .NET 2005 as its application development platform. You create an application named MyApplication using Visual C# .NET. You use the Mutex class for synchronization among threads. You create three threads to enter the protected area one by one. This means that if one thread is already in the protected area, no other thread is allowed to enter in the protected area. When you execute the application, it gives the following output:
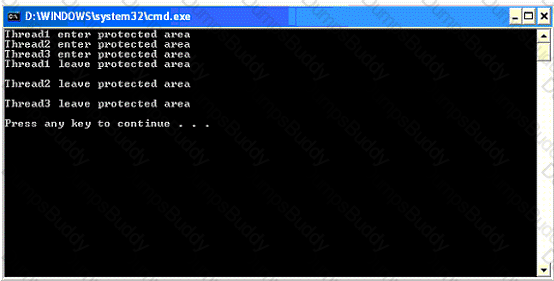
As you can see in the above code window, all the three threads enter the protected area at the same time. Drag and drop the appropriate statements that will allow the threads to enter the protected area one by one.
You work as a Software Developer for Mansoft Inc. You create an application and use it to create code access security policies. Which of the following tools will you use to examine and modify code access security policies from a batch file?
You work as a Software Developer for ABC Inc. You use C# .NET to develop a windows application. The application will implement a role-based authorization scheme that is based on a Microsoft SQL Server database of user names. Users will enter their names in a text box named UserName. You must ensure that users are assigned the supervisor role and the PG role by default. Which of the following code segments will you use to accomplish this task?
You work as a Software Developer for Hi-Tech Inc. You develop an application using Visual Studio .NET 2005. You create an unregistered COM DLL file named Com1.dll. You want to use this Com1.dll file in your application code. However, Com1.dll needs to be registered in the Windows Registry before it is used by the application. Which of the following tools will you use to accomplish the task?
You work as a Web Application Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a Web application using .NET Framework 2.0. You configure the application at the following levels:
l Root Web
l Web application root directory
l Web site
l Web application subdirectory
In which of the following files will these levels be stored?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You are creating an application using .NET Framework 2.0. The application will perform security related operations. You want to manage the role-based security in the application. What will you do to accomplish the task?
Peter works as a Software Developer for PatSoluTech Inc. He creates a .NET assembly using Visual Studio .NET. He wants to use this assembly in multiple .NET applications on a local computer. He decides to deploy the assembly into the global assembly cache (GAC). What will he do to accomplish the task?
Each correct answer represents a complete solution. Choose two.
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a Windows application using the .NET Framework. You create a Semaphore class instance in the application by using the following code snippet:
Semaphore tSema = new Semaphore(0, 5);
...
tSema.Release(6);
What will the above code segment do?
You work as an ADO.NET Application Developer for ABC Inc. The company uses Microsoft Visual Studio .NET 2008 as its application development platform. You create an ADO.NET application by using .NET Framework 3.5. You are using the System.Linq.Expressions namespace to represent the code expression as objects in the form of expression trees. You want to initialize the members of a newly created object. What will you do to accomplish the task?
You work as a Software Developer for ABC Inc. You use C# .NET to develop a windows application. The application will implement a role-based authorization scheme that is based on a Microsoft SQL Server database of user names. Users will enter their names in a text box named UserName. You must ensure that users are assigned the supervisor role and the PG role by default. Which of the following code segments will you use to accomplish this task?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. You want to implement state management in your application. In which of the following stages of the application life cycle will your application actually start?
Allen works as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. Allen creates an application that will be used to handle security information related to the company. He wants to secure the application by using the most secure authentication method. The method should have a strong key for encryption and send the encrypted password across the network. Which of the following authentication methods will Allen use to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You are developing an application that manages sports teams. When a user queries details about a particular team, the id and name of each member of the team must be stored as a single collection. You must create the collection of team members in the most efficient manner, in a manner that guarantees type safety, and in a manner that will require the least amount of code to retrieve and work with the data in the collection. Which code segment should you choose?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. Your application has a form that accepts a user name and email address. You want to validate the input text for the email address by matching against a pattern defined in the regular expression.
Which of the following validation controls will you use to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating an ASP.NET Web application using .NET Framework 3.5. The application will be accessed by Internet users. You need to enable users to authenticate from the client-side script. You add the following code fragment in the Web.config file of the application:
You must configure the application to ensure that user credentials are validated against Active Directory by using the client-side script. What will you do to accomplish this?
Each correct answer represents a part of the solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You are creating an application that will perform statistics calculations using .NET Framework. You want to ensure that the application is capable of performing multiple calculations concurrently. What will you do to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You need to write a code segment that transfers the contents of a byte array named ToSend by using a NetworkStream object named NetStr. You want to use a cache of size only 8,192 bytes. Which of the following code segments will you use to accomplish the task?
Martin works as a Software Developer for BlueWell Inc. He creates an ASP.NET application, named App1. During beta testing of App1, he ensures that the actual ASP.NET error messages are displayed whenever errors are encountered. He also ensures that both developers and beta testers see the actual text of the error messages.
During beta testing of App1, Martin performs beta testing of other applications also on the same test server. All the other applications display the ASP.NET error messages. After completing beta testing, Martin promotes the beta test server to a production server. He wants all the applications to display a single, user-friendly error message. Martin also wants to configure App1 and the production server to meet these goals. He removes the customErrors element from the Web.config file for App1. What else will he do to accomplish the required task with minimum administrative effort?
You work as a Software Developer for ManSoft Inc. The company uses Visual Studio.NET 2005 as its application development platform. The company wants you to develop an application that manages the account information of the company. The requirement of the application is to use only value types. Which of the following types will you use to accomplish the task?
Each correct answer represents a complete solution. Choose three.
Sam works as a Software Developer for BlueWell Inc. He develops two applications: MyApp1 and MyApp2 using Visual Studio .NET 2005. He wants to ensure that both these applications use the same assembly named Assembly1. Therefore, he signs Assembly1 with a strong name for each application. What is significant about the strong name that consists of the assembly's identity?
Each correct answer represents a part of the solution. Choose all that apply.
You work as a Software Developer for Blue Well Inc. You create a mobile Web application for
mobile users. You want to ensure that a cookieless session is implemented on it. Which of the
following statements are the main reasons of implementing a cookieless session on a mobile Web application?
Each correct answer represents a part of the solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished the development of a class named TestCase and you have used only reference types in the class. The class will be used in an application that will use pointers. Therefore, you are required to convert the reference types to pointers in the class. Which of the following keywords will you use to accomplish the task?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. You want to redirect users to a default error page if an unhandled error occurs within your site. Which of the following actions will you perform to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You create an application using .NET Framework. The application is used to place an assembly on the intranet. Which of the following classes will you use to test whether or not an assembly was located on the intranet?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows application using .NET Framework 3.5. The application will process one million records in a production environment. Therefore, you need to test the application by using 7,500 records in a limited test environment to identify potential problems that might arise when the application is moved to the production environment. What will you do?
Each correct answer represents a part of the solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You create an application using .NET Framework. You use the application to create an assembly. Now you need to encrypt assembly data. The company has not provided encryption requirements to you. Which of the following symmetric cryptography classes will you use to accomplish this task?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a Windows application using .NET Framework 2.0. The application allows computer engineers to design circuit boards for different types of hardware. You create a custom control that represents the design surface. You are required to highlight the vacant areas on the design surface where a component can be dropped. Which of the following events will you use to accomplish this task?
You work as a Software Developer for ManSoft Inc. You create an assembly. You place the assembly in a specific folder. Which of the following classes can you use to determine whether the assembly was located in a specific folder?
Each correct answer represents a complete solution. Choose two.
Hannah works as a Programmer in a college of Information Technology. The company uses Visual Studio .NET as its application development platform. The Dean of the college wants to obtain the performance report of each student. Hannah develops an application named StudentPerformanceReport by using Visual C# .NET. This application uses a SQL Server database named Database1 and a stored procedure named PROC1. PROC1 executes a query that returns the internal assessment result of each student. Hannah uses a TextBox control named AssessmentText in the application form named MyForm. She wants to display the total test result of each student in the AssessmentText text box control. StudentPerformanceReport uses a SqlCommand object to run PROC1. Hannah wants to write code to call PROC1. PROC1 contains an output parameter and displays its value as "@AssessmentResult" in text format. Which of the following code segments can Hannah use to accomplish this task?
Each correct answer represents a complete solution. Choose two.
You work as a Software Developer for ManSoft Inc. The company uses Visual Studio.NET as its application development platform. You create an application using the .NET Framework. You use ManSoft's intranet to deploy the application to client computers. You use the security configuration of the .NET Framework to configure security for the application at the enterprise policy level. Virus attacks caused the IT manager at ManSoft Inc. to tighten the security at the machine level. Users reported that they could no longer execute the application. Which of the following options will you use to resolve this issue?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create an ASP.NET Web application using .NET Framework 3.5. You utilize the built-in ASP.NET Web server controls in all the Web forms of the application. You access and modify the properties of all Web server controls in the code behind code of the Web forms. You are required to include custom client-side and AJAX behavior to the ASP.NET Web server controls. You are also required to ensure nominal effect on the current application code. What will you do?
Each correct answer represents a part of the solution. Choose two.
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows Forms application using .NET Framework 3.5. You need to execute a method named ProcAmount in the background of the application. The method requires that an integer value 101 is passed to it. You are required to pass an integer value 101 to start a background thread. Which of the following code segments should you use?
Each correct answer represents a part of the solution. Choose two.
You work as a Software Developer for WebTech Inc. You create a Web service named Utils. You want a new object of Utils to be created whenever a customer makes a call to the service. Which of the following will accomplish this task?
Julia works as a Software Developer for Mansoft Inc. She develops an application using Visual Studio .NET. The application uses a method named MyMethod, which is located in an unmanaged DLL. Julia wants MyMethod to require the application to allocate unmanaged memory, fill the data, and pass the memory address to the application. She also wants to ensure that on returning from MyMethod, the application de-allocates the unmanaged memory. What will Julia do to accomplish the task?
Which of the following providers is a block cipher that encrypts and decrypts data in blocks of 8 bytes?
Allen works as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. He creates an application using .NET Framework. He wants to encrypt all his e-mails that he sends to anyone. Which of the following will he use to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create an ASP.NET Web application using .NET Framework 3.5. You need to represent a strongly typed lambda expression as a data structure in the form of an expression tree. Which of the following classes will you use to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create an ASP.NET Web application using .NET Framework 3.5. You are not using an exception handling framework in the application. However, the application must automatically log all unhandled exceptions to an event log. You are required to configure the Web.config file accordingly. Which of the following configurations will you use to accomplish the task?
David works as a Software Developer for GenTech Inc. He creates an XML Web service, named MyWebService, using Visual Studio .NET. MyWebService uses Microsoft Windows authentication. Users of MyWebService are in the GenTech domain. David wants to configure MyWebService to use the following URL-based authorization rules:
l Anonymous users must not be allowed to access MyWebService.
l All the users except User1 and User2 must be allowed to access MyWebService.
David configures Internet Information Services (IIS) to meet these requirements. Which of the following code will David use to configure the authorization section of the Web.config file for MyWebService?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You are creating an application using .NET Framework 2.0. The application will be used by school children to read a sequential chain of characters. What will you do to accomplish this task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You need to write a code segment that transfers the contents of a byte array named ToSend by using a NetworkStream object named NetStr. You want to use a cache of size only 8,192 bytes. Which of the following code segments will you use to accomplish the task?
Which of the following algorithms supports key lengths from 128 bits to 192 bits in increments of 64 bits?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. You want to redirect users to a default error page if an unhandled error occurs within your site. Which of the following actions will you perform to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You create an ASP.NET Web application using the .NET Framework 3.5. The application contains two HTML pages named Error.htm and
PageNotFound.htm. You want to make sure that the following requirements are met:
l When any user requests a page that does not exist, the PageNotFound.htm page is
displayed.
l When any other error occurs, the Error.htm page is displayed. Which of the following code segments will you add to the Web.config file to accomplish this task?
Which of the following data structures is used for storing reference data types?
Tony works as a Software Developer for TechNet Inc. He creates a satellite assembly named
SatAssembly1. He wants to install SatAssembly1 in the global assembly cache. Therefore, he compiles the assembly by using the Al.exe tool and signs SatAssembly1. Which of the following possible tools will Tony use to sign SatAssembly1?
Each correct answer represents a complete solution. Choose two.
Smith works as a Software Developer for BlueWell Inc. He develops a Web application named WebApp by using Visual Studio .NET. He wants to deploy WebApp on a target computer. He wants to take precautionary measures in the application so that no issues may arise while deploying it. Which of the following measures will Smith take to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for ABC Inc. You create a Console application to create multiple satellite assemblies. Which of the following statements about satellite assemblies are true?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating a Windows Forms application using .NET Framework 3.5. You need to develop a new control for the application. You must ensure that the control inherits the TreeView control by adding a custom node tag and a highlight color. What will you do?
You work as a Web Administrator for BlueWell Inc. The company's sales employees access the Web server from remote locations via the Internet using Netscape Navigator or Internet Explorer. You want to secure the Web server. To secure the Web server, you want to use cookieless forms authentication. Which of the following properties will you use to accomplish the task?
Maria works as a Software Developer for BlueWell Inc. She develops an application, named App1, using Visual C# .NET. The application displays employee details from a SQL Server database. Maria wants to use a string array, named MyArray, in the application code to store employee names. Which of the following statements will she use to declare MyArray?
You work as a Software Developer for ABC Inc. You are defining a component for an application. In some deployments, the component will be deployed on the same computer as the application. In other deployments the component will be deployed on a separate computer. The component has implicit dependencies and needs to access and use server-side resources that cannot cross system boundaries.
You must ensure that your component design supports both deployment scenarios. What will you do to accomplish the task?
You work as a Software Developer for ManSoft Inc. You use Microsoft Visual Studio to create a Web service named MyWebService. You create a SOAP message that is not secure in the Web service. You want to use the ReceiveSecurityFilter class in the Web service to handle the receiving and securing of SOAP messages. Which of the following code segments will you use to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a Windows application using the .NET Framework.
You create a database to maintain the record of the students. You create a table named Student. You want to retrieve names and roll number of those students whose age is less than ten years. An instance of the SqlCommand class named StudentCommand is already created. Which of the following code segments should you use to execute the query?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You create an application named MyApplication. MyApplication uses the System.IO namespace. You want to ensure that you are able to use a class that specifies read and write operations either in synchronous or asynchronous manner. Which of the following classes will you use to accomplish the task?
You work as a software developer for ManSoft Inc. The company uses Visual Studio .NET 2005 as its application development platform. You use C#. NET to create an assembly that will be consumed by other Visual Studio .NET applications. No Permissions should be granted to this assembly unless the assembly makes a minimum permission request. You need to write a code for the assembly that makes a minimum permission request. Which of the following code segments will you use to accomplish this task?
Samantha works as a Software Developer for InfoWorld Inc. She develops a Web page named SalesReport.aspx for the employees of the company. However, she wants to ensure that all the requests for a particular employee are not stored on the server's memory. She also wants to ensure that no data is lost even after each user session has expired. Which of the following actions will Samantha take to accomplish the task?
You work as a Software Developer for InfoTech Inc. You develop an application named MyApp that works as a scientific calculator. A user inputs data and retrieves the calculated results based on the input values. The application uses a SQL database that contains two tables. One table contains data related to standard calculation specifications and the other table stores input values entered by the user. You want to ensure that the user is able to retrieve appropriate data fast. Which of the following actions will you take to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
You work as a Software Developer for ManSoft Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You are creating a global application that will be used by all the branches of the company. You want to perform the encoding of Unicode characters with error detection capability. Which of the following classes will you use to accomplish the task?
Each correct answer represents a complete solution. Choose three.
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You create an application using .NET Framework. The application is using an assembly. You want to ensure that the application provides the best performance. Security is not a consideration. Which of the following permission sets will you use to accomplish the task?
John works as a Web Developer for ProLabs Inc. He develops an ASP.NET application, named
MyWebApp1, using Visual Studio .NET. One of the pages in the application is named as Page1.aspx, which does not need to maintain session state. To improve the performance of the application, John wants to disable session state for Page1. Which of the following actions will he take to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You create an ASP.NET Web application using the .NET Framework 3.5. The application contains two HTML pages named Error.htm and
PageNotFound.htm. You want to make sure that the following requirements are met:
l When any user requests a page that does not exist, the PageNotFound.htm page is displayed.
l When any other error occurs, the Error.htm page is displayed.
Which of the following code segments will you add to the Web.config file to accomplish this task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You have recently finished development of an application using .NET Framework. The application used two threads named threadOne and threadTwo. You are required to modify the code of the application to prevent the execution of threadOne until threadTwo completes execution. What will you do to accomplish this task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You are creating an application using the .NET Framework. The application contains a class named globalInfo. You need to serialize all public and nonpublic data of the globalInfo class to ensure that the class generates the minimum byte stream so that the minimum load is placed upon network resources. What will you do?
Mark works as a Software Developer for BlueWell Inc. The company uses Visual Studio .NET as its application development platform. He develops four applications using the .NET Framework.. All the four applications use an assembly named MyAssembly. He deploys the applications on the company's intranet. Later, Mark modifies MyAssembly and wants to ensure that all applications use the latest version of MyAssembly. What will he do to accomplish this?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You create a message queue named SecureQ using .NET Framework. The message queue requires each incoming message to be encrypted. You want to ensure that a message can be sent to SecureQ without an exception being thrown. What will you do to accomplish this task?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Windows Forms application using .NET Framework 3.5. You add a button control to a form named form1. You want to retrieve more information about the mouse event. You use the MouseClick event in your application. Which of the following parameters will you pass to the event handler of the MouseClick event?