John works as a Web Developer for ProMetaworks Inc. He creates an ASP.NET application, named MyApp1, using Visual Studio .NET. MyApp1 contains a page, named Page1. Page1 contains several TextBox controls that accept users' input. John uses several validation controls on the page to validate input controls. He wants to display all the validation error messages on the page in a message box. However, he does not want the validation summary to be displayed inline on the Web page. What will he do to accomplish the task?
You work as an Application Developer for ABC. The company uses Visual Studio .NET Framework 3.5 as its application development platform. You are working on enhancements to an existing WPF application. One problem you have been encountering is that users of the current version routinely enter invalid data, and since the controls use data binding, that data either gets put in the database incorrectly, or in some cases generates a database error. You want to incorporate validation with your data bound controls. Which of the following choices is the best way to accomplish this goal?
Ricky works as a Software Developer for SoftTech Inc. He creates an XML Web service, named XmlWeb, by using Visual Studio .NET. He wants to publish XmlWeb within the company's intranet. Which of the following actions will Ricky take to publish XmlWeb?
Each correct answer represents a part of the solution. Choose all that apply.
Henry works as a Software Developer for InfoTech Inc. He develops a Web application for registered employees of the company. The application requires accessing several XML data stored in a database named Database1. However, Henry wants to ensure that the XML data is validated before being accessed. Which of the following classes will Henry use to validate the XML data?
Sandra works as a Software Developer for ABC Inc. She develops a Web site on a client computer. She creates a custom control named CustControl1 on a Web page named
MicrosoftCert1. She wants to retain the custom control property information during several round trips to a server. She wants to ensure that the control property is retained even if the view state of the Web page is disabled at the page level. Which of the following client-based techniques for storing state management information will Sandra use to accomplish the task?
George works as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. George creates an application using the .NET Framework. He writes the following code snippet in the application:
public class FirstClass
{
public static int test=500;
}
public class SecondClass : FirstClass
{
public static void Main(String[] args)
{
SecondClass mb=new SecondClass();
mb.MyMethod();
}
public void MyMethod()
{
//Appropriate statement
}
}
George wants to modify the value of the test variable in MyMethod to 1000. Which of the following code segments will he place in MyMethod to accomplish this task?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You are creating a Windows service application using the .NET Framework. The service is used to execute several tasks that require background processing. You do not want to actively manage threads in the service application, but you must make sure that security checks are performed during the execution of the task. What will you do to accomplish the task?
Allen works as a Software Developer for Mansoft Inc. He develops a Web application using Visual Studio .NET. He adds a Web reference to an XML Web service named MyWebService in the application. MyWebService includes a method named MyMethod, which takes user identification number as a parameter and returns a DataSet object containing user information. The System.ArgumentException is thrown if the user identification number does not lie between 1 and 500. Allen writes a try and catch block to capture the exception thrown by the Web service. Which of the following exceptions will the try and catch block catch if a user calls MyMethod passing 501 as a parameter?
Sophia works as a Software Developer for BlueWell Inc. She creates a component, named MyComp, using Visual Studio .NET. MyComp includes a method named MyMethod1, which is used to process user requests. MyMethod1 calls a private method, named MyMethod2. Sophia wants to ensure that if an error occurs during the execution, the exceptions encountered by MyMethod2 are caught and passed on to MyMethod1 for exception handling. Which of the following combinations of the exception handler should she use to accomplish the task?
Kathy works as a Software Developer for BlueWell Inc. She creates a serviced component named
Com1. She wants to ensure that all the employees of the company are able to use Com1. Therefore, she wants to install Com1 in the Global Assembly Cache (GAC). Before the installation, she wants to register the serviced component manually with COM+. Which of the following tools will Kathy use to register Com1?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You have recently finished development of an ASP.NET Web application using the .NET Framework 3.5. You host the application on a Web farm that consists of three Web servers. You should configure the ASP.NET application for session state to meet the following requirements:
l Session state data should not be lost if a server fails.
l Session state must be maintained across browser requests by the same user.
You are required to configure the Web.config file to meet these requirements. Which of the following configurations will you use?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows Forms application using .NET Framework 3.5. The application needs a thread that accepts an integer parameter. You write the following code segment in the application:
Thread myThread = new Thread(new ParameterizedThreadStart(doWork));
myThread.Start(125);
You are required to declare the signature of the doWork method. Which of the following method signatures will you use?
You work as a Software Developer for ManSoft Inc. You create an application using Visual Studio .NET
2005. You write the following code snippet in the application:
int amt = 50;
String s = "John gave me " + amt + " dollars";
Console.WriteLine(s);
What will be the output of the above code?
Mark works as a Web Developer for ABC Inc. He develops an ASP.NET application, named MyApp1, using Visual Studio .NET. MyApp1 allows users to view and purchase company products.
It includes several pages. The start-up page of the application is Page1.aspx. He configures the application's Web.config file to use form-based authentication.
Mark wants users to log on to Page1.aspx by providing their user names and passwords. To accomplish this, he creates an ASP.NET page named UsersLogIn.aspx that allows each user to specify a user name and password. He then writes the following syntax in the Web.config filE.
loginUrl="/UsersLogIn.aspx" protection="All" timeout="60" slidingExpiration="true">
What will be the result?
Each correct answer represents a part of the solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You are creating an application using .NET Framework 2.0. You are using regular expression in the application to validate email, phone number, etc. You are required to match the preceding character or sub expression zero or more times. Which of the following wildcard characters will you use to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You are creating an application using .NET Framework 2.0.
The application is used to exchange structured and type information on the Web using Soap. You want to use the BinaryFormatter and SoapFormatter classes to support RPCs and serialization of a graph of objects. Which of the following interfaces will the BinaryFormatter and SoapFormatter classes implement to accomplish the task?
Each correct answer represents a part of the solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You create an application named StringRW using .NET Framework. You store some characters into an array of Unicode characters. You need to write all or some of these characters into a String object. Which of the following code segments will you choose to accomplish this task?
Each correct answer represents a complete solution. Choose all that apply.
You work as an Enterprise Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create an ASP.NET application using .NET Framework 3.5. You have already created a data contract for a WCF service and the ASP.NET Web application, which consumes the WCF service. The application has the following requirements:
l On low network bandwidth the serialized format of the data contract type should be minimum.
l The application uses AJAX to retrieve the data from the WCF service.
l Use the least amount of development effort.
What will you do?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows application using .NET Framework 3.5. The application uses a SQL Server 2008 database on the network.
You use ADO.NET Data Services that exposes data as resources that are addressable by URIs. You need to access and change data, specifically the standard HTTP verbs of GET, PUT, POST, and DELETE. What will you do to accomplish this?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5.
You want to ensure that the data input by a user falls within a predetermined range. Which of the following validation controls will you use to accomplish the task?
John works as a Web Developer for ProLabs Inc. He develops an ASP.NET application, named
MyWebApp1, using Visual Studio .NET. One of the pages in the application is named as Page1.aspx, which does not need to maintain session state. To improve the performance of the application, John wants to disable session state for Page1. Which of the following actions will he take to accomplish the task?
You work as a Software Developer for ABC Inc. The Company uses .NET Framework 2.0 as its application development platform. You are creating an application that will perform different types of comparison operations. Therefore, you decide to use only those methods that are available in all the classes of .NET Framework 2.0. Which of the following methods will you use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Allen works as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. He creates an application using the .NET Framework.. He writes the following code segment in the application:
01 class gClass
02 {
03 public gClass(int k)
04 {
05 //Write code here
06 }
07 }
08 public class gSub : gClass
09 {
10 public static void Main(String[] argv)
11 {
12 gSub gs=new gSub(20);
13 }
14 gSub(int j):base(j)
15 {
16 //Write Code here
17 }
18 gSub(string st, int j):this(j)
19 {
20 gClass ss=new gClass();
21 }
22 }
When you execute the above code segment, you get an error at line 20. Which of the following code segments will he place at line 20 to execute the code successfully?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create an ASP.NET Web application using .NET Framework 3.5. You utilize the built-in ASP.NET Web server controls in all the Web forms of the application. You access and modify the properties of all Web server controls in the code behind code of the Web forms. You are required to include custom client-side and AJAX behavior to the ASP.NET Web server controls. You are also required to ensure nominal effect on the current application code. What will you do?
Each correct answer represents a part of the solution. Choose two.
You work as a Software Developer for ManSoft Inc. The company uses Visual Studio.NET 2005 as its application development platform. The company wants you to develop an application that manages the account information of the company. The requirement of the application is to use only value types. Which of the following types will you use to accomplish the task?
Each correct answer represents a complete solution. Choose three.
Allen works as a Software Developer for ManSoft Inc. He uses Microsoft Visual Studio 2005 to create a Web service named MyWebService. He wants to create a policy file with the help of WSE 3.0, which makes creating policy assertions files fairly straightforward. A policy assertion is a combination of the capabilities and requirements of the Web service. Allen initially writes the following steps to create and implement a policy file:
l He creates a stud to hold the policy elements. This task is accomplished by creating a config file known as a policy file or a policy cache file.
l He creates a set of policy assertions. There exists a set of assertions that can be used.
l He references the policy file from the application configuration file.
After completing these steps, the structure of the policy file is created. Now, he wants to use the structure of the policy file to inject input filters, output filters, or both, into the processing pipeline.
Which of the following policy file structures will Allen use to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You create an ASP.NET Web application using the .NET Framework 3.5. You create a HTTP module that is called on each and every request made by the application. It is called as part of the ASP.NET request pipeline. Other then this, under which of the following operations will you use the HTTP module?
Each correct answer represents a complete solution. Choose three.
Allen works as a Software Developer for ManSoft Inc. He develops a Web application using Visual Studio .NET. He adds a Web reference to an XML Web service named MyWebService in the application. MyWebService includes a method named MyMethod, which takes user identification number as a parameter and returns a DataSet object containing user information. The System.ArgumentException is thrown if the user identification number is not positioned between 1 and 500. Allen writes a try/catch block to capture the exceptions thrown by the Web service. Which of the following exceptions will the try/catch block catch if a user calls MyMethod passing 501 as a parameter?
You work as a Software Developer for ABC Inc. You have created a console application that uses two threads, named thread1 and thread2. You need to modify the code to prevent the execution of thread1 until thread2 completes its execution. Which of the following steps will you take to accomplish this task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating an ASP.NET Web application using .NET Framework 3.5. The application will be used to share any type of photos on Internet. All the photos should be accessible in various sizes and formats. You need to add a download feature that can be easily maintained. You also need to make sure that only a single version of all photos is stored on a SQL server database. What will you do?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You are creating an assembly. The assembly contains a public method. The Global Assembly Cache contains a second assembly. You require that the public method is only called from the second assembly. Which of the following permission classes will you use to accomplish this task?
You work as a .NET Trainer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You are required to identify the building blocks of .NET Framework. Which of the following building blocks will you choose to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
John works as a Web Developer for TechCom Inc. He creates an ASP.NET application, named MyApp1, using Visual Studio .NET. Only registered users of the company will be able to use the application. The application contains a page, named NewAccount.aspx that allows new users to register themselves to the registered user list of the company. The NewAccount page contains several TextBox controls that accept users' personal details such as username, password, confirm password, first name, last name, home address, zip code, phone number, etc. One of the TextBox controls on the page is named txtZipCode in which a user enters a Zip code. John wants to ensure that when a user submits the NewAccount page, txtZipCode must contain five numeric digits. He wants least development effort. Which of the following validation controls will he use to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
You work as a Software Developer for ManSoft Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You are creating an application that will be used by all the branches of the company. You use the Code Access Security to manage the security of the application. The application requires to obtain minimum permissions to execute properly. Which of the permissions will you grant to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Maria works as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. She creates a Web service and uses a Session object in it. She declares a variable in the Session object. What will be the scope of the variable?
Ross works as a Software Developer for GenTech Inc. He develops a Windows-based application using Visual Studio .NET. He uses the Write method of the Debug and Trace classes to record information about the execution of the application in Windows 2000 event log. Ross performs integration testing on the application. He wants to ensure that only one entry is made to the event log, each time a call is made to the Write method of either class. Which of the following code will he use to accomplish this?
Each correct answer represents a complete solution. Choose two.
George works as a Software Developer for GenTech Inc. He creates an application named App1 using Visual Studio .NET. App1 uses the version 2.0.0.0 of an assembly named Assembly1. However, he wants App1 to use a new version i.e. 2.1.0.0 of Assembly1. Therefore, he needs to specify Assembly1's location so that App1 can use version 2.1.0.0 of Assembly1. What will George use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You create an application using .NET Framework. You use the application to create an assembly. Now you need to encrypt assembly data. The company has not provided encryption requirements to you. Which of the following symmetric cryptography classes will you use to accomplish this task?
Mark works as a Software Developer for BlueWell Inc. He develops four Windows-based applications using Visual Studio .NET. All the applications use an assembly, named Assembly1. Mark deploys the applications on the company's intranet. Later, he modifies Assembly1 and wants to ensure that all the applications use the latest version of Assembly1. Which of the following files will Mark use to accomplish this?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating an ASP.NET Web application using .NET Framework 3.5. The application will be accessed by users from remote locations over the Internet. You need to use ASP.NET role management. You must ensure that any authorization information cached on remote client computers is as secure as possible. What will you do?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. You create an application using .NET Framework. The application is used to place an assembly on the intranet. Which of the following classes will you use to test whether or not an assembly was located on the intranet?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You are developing an application that manages sports teams. When a user queries details about a particular team, the id and name of each member of the team must be stored as a single collection. You must create the collection of team members in the most efficient manner, in a manner that guarantees type safety, and in a manner that will require the least amount of code to retrieve and work with the data in the collection. Which code segment should you choose?
You work as a Software Developer for ManSoft Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You create an application that will be used by all the branches of the company. You use the Regex class in the application to validate some strings. You want to search an input string for an occurrence of a regular expression. Which of the following methods of the Regex class will you use to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You are creating an application using .NET Framework 2.0. The application will perform security related operations. You want to manage the role-based security in the application. What will you do to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You create an ASP.NET Web application using the .NET Framework 3.5. The application uses Session objects. You are changing the application to run on a Web farm. You want to make sure that the application can access the Session objects from all the servers in the Web farm. You also make sure that when any server in the Web farm restarts or stops responding, the Session objects are not lost. What will you do?
Adam works as a Software Developer for ABC Inc. He creates an ASP.NET application, named MyApp. During beta testing of MyApp, he ensures that both developers and beta testers see the actual text of error messages. Adam performs beta testing of other applications on the same test server. All the other applications display ASP.NET error messages. After completing beta testing, Adam promotes the beta test server to a production server. He wants all the applications to display a single, userfriendly error message. Adam also wants to configure MyApp and the production server to meet these goals. What will he do to accomplish the required task with minimum administrative effort?
Peter works as a Software Developer for PatSoluTech Inc. He develops a Web application using Visual Studio .NET. The application contains an online ordering Web form named WebForm1. WebForm1 contains several Web server controls that include a TextBox control named TextBox1 and an ImageButton control named ImageButton1. He wants data entered in TextBox1 to be validated whenever ImageButton1 is clicked. Which of the following will Peter use to accomplish the task?
Dilton works as a Software Developer for GREC Research Center (Central). This research center has its subsidiaries in several different cities. Dilton wants to retrieve a Soil Test Report for the Geological Survey Department. He wants the test report to be available to all the members of the department over the Internet. He creates an XML Web service named SampleReport. SampleReport contains a Web method named SoilTestDetails that requires additional security.
Dilton decides to use generic role-based security to secure the SoilTestDetails method from unauthorized users. Dilton writes code to ensure that once a user is authenticated, a user identity named Generic is created. The Generic user identity has a group membership named GeoSurvey to allow the authenticated users access to the SoilTestDetails Web method. Which of the following code segments should Dilton use to accomplish the task?
You work as a Software Developer for Mansoft Inc. The company uses Visual Studio .NET as its application development platform. You create an application named ExceptionHandling using .NET Framework. You write code and execute it, but it causes an error. Now, you want to find out where the exception has occurred.
Which of the following properties of the exception class will you use to accomplish the task?
John works as a Web Developer for ABC Inc. He develops an ASP.NET application, named MyApp1, using Visual Studio .NET. The application will be used in the Sales department to generate monthly reports. The company uses Microsoft Windows authentication. All users are in the TESTPRO1 domain. John wants to ensure that all users except Mark, Roger, and David are allowed to access the application. Which of the following code will he use in the application's Web.config file to accomplish the task?
You work as a Database Developer for a Web based music company named Music2Music. You are designing a database for online order management application. The customers use the company's Web site to place orders for the music CDs. Orders details are first inserted into an online database named OrdersData. The Orders database includes a table named Orders and a table named OrderDetails. The Orders table contains basic information about the orders. The OrderDetails table contains information about the individual items in the orders. Fragments of the Orders database is given below:
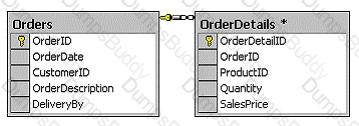
Requirements of the database design are given below:
l Customers must be able to use the company's Web site to view orders stored in the OrdersData database.
l Customers should be able to see only their own orders.
l Customers should not be able to modify the orders.
l The primary key values of the orders are not relevant to the customers and should not be
visible. What will you do?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You are creating an application using the .NET Framework. You need to save a graphical object from the application. The graphical object is a collection of x and y points, each represented by using a single precision floating point number. You want to use the least amount of disk space by the saved object. Which the following classes will you use to accomplish this task?
You work as a Software Developer for ABC Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You are creating an application using .NET Framework 2.0. The application will be used by all the branches of the company. You sometimes require a variable number of arguments to be passed to a method. For example, you may require a sum method, which calculates the total of the numbers passed to it no matter how many numbers are passed. What will you do to accomplish the task?
Maria works as a Software Developer for ManSoft Inc. She develops an application using Visual Studio .NET 2005. Maria wants to ensure that only employees of the Accounts department can view the application. Therefore, she decides to change the configuration settings in the Web.config file.
What will Maria do to accomplish the task?
John works as a Software Developer for DawnStar Inc. He creates a class, named MyClass1. He wants to generate a key pair that he will use to give the compiled assembly a strong name. Which of the following tools will he use to accomplish the task?
John works as a Software Developer for InfoTech Inc. He develops an application named
SerializeObj. He creates a custom class and wants to serialize its object. He also wants the object to be stored into an XML file named File1.xml. He writes the following code: public class Employees
{
public string EmpID;
public string EmpName;
public decimal Salary;
}
Which of the following code statements will John add in the application?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a method to call a COM component using the .NET Framework. You want to use declarative security to request the runtime to run a complete stack walk. You need to ensure that all callers be obliged to level of trust for COM interop before the callers execute the method. Which of the following attributes will you place on the method to accomplish the task?
Maria works as a Software Developer for BlueWell Inc. She develops an application, named App1, using Visual C# .NET. The application displays employee details from a SQL Server database. Maria wants to use a string array, named MyArray, in the application code to store employee names. Which of the following statements will she use to declare MyArray?
You work as a Software Developer for ManSoft Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You create an application that will be used by all the branches of the company. You use the Regex class in the application to validate some strings. You want to search an input string for an occurrence of a regular expression. Which of the following methods of the Regex class will you use to accomplish the task?
Mark works as a Software Developer for Mansoft Inc. He develops an application using Visual
Studio .NET 2005. He writes the following code snippet in the application:
public class MyClass
{
public static void Main(String[] args)
{
try
{
return;
}
finally
{
Console.WriteLine("Finally");
}
}
}
What will happen when Mark attempts to compile and execute the code snippet?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished development of Web services using the .NET Framework. The access control to Web services is part of your accountability. You are currently revealing an existing class as a XML Web service. You are required to ensure that the XML Web service is exclusively accessible to Web service clients within the ABC Inc. domain. To fulfill this requirement you want to change the access modifiers on methods that must be represented as Web methods. What will you do to accomplish this task?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating a Windows Forms application using .NET Framework 3.5. You need to develop a new control for the application. You must ensure that the control inherits the TreeView control by adding a custom node tag and a highlight color. What will you do?
You work as a .NET Trainer for ABC Inc. The Company uses .NET Framework as its application development platform. You are creating an application to demonstrate the use of datatypes. You create an unsigned Short datatype in the application. Which of the following values can be assigned to the unsigned Short datatype?
Each correct answer represents a complete solution. Choose three.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a class library using the .NET Framework. The library will be used to open the NSCs of computers. Later, you will set up the class library to the GAC and provide it Full Trust permission. You write down the following code segments for the socket connections:
SocketPermission permission = new SocketPermission(PermissionState.Unrestricted);
permission.Assert();
A number of the applications that use the class library may not have the necessary permissions to open the network socket connections. Therefore, you are required to withdraw the assertion. Which of the following code segments will you use to accomplish the task?
You work as a software developer for ManSoft Inc. The company uses Visual Studio .NET 2005 as its application development platform. You use C#. NET to create an assembly that will be consumed by other Visual Studio .NET applications. No Permissions should be granted to this assembly unless the assembly makes a minimum permission request. You need to write a code for the assembly that makes a minimum permission request. Which of the following code segments will you use to accomplish this task?
Which of the following is an exception of background threads as compared to foreground threads?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create an ASP.NET Web application using .NET Framework 3.5. You create a Web form in the application that permits users to provide personal information. You add a DropDownList control to the Web form to retrieve the residential status of users. The default item that the DropDownList control displays is the "Select Country" option. You have to ensure that users select a country other than the default option. Which of the following validation controls should you use to accomplish this task?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows Forms application using .NET Framework 3.5. The application contains a data-bound control. You use the LinqDataSource control to use LINQ in the ASP.NET application by setting properties in markup text. The LinqDataSource control uses LINQ to SQL to automatically generate the data commands. You are required to perform data operations by using the LinqDataSource control. What is the correct order in which data operations are applied?
Bill works as a Software Developer for SunInfo Inc. He develops an application named SunApplication using C# .NET. The employees of the company use SunApplication for viewing and editing inventory data. SunApplication receives data from a file named MyFile.xml, which currently does not provide any information. Bill decides to write code to get information from the MyFile.xml file. Which of the following code segments will he use to resolve the issue?
Each correct answer represents a complete solution. Choose all that apply.