Which of the following organizations is dedicated to computer security research and information sharing?
You are concerned about outside attackers penetrating your network via your company Web server. You wish to place your Web server between two firewalls. One firewall between the Web server and the outside world. The other between the Web server and your network. What is this called?
Which of the following files in LILO booting process of Linux operating system stores the location of Kernel on the hard drive?
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domain-based network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. According to the company's security policy, you apply Windows firewall setting to the computers on the network. Now, you are troubleshooting a connectivity problem that might be caused by Windows firewall. What will you do to identify connections that Windows firewall allows or blocks?
Mark works as the Network Administrator of a Windows 2000 based network. The network has a DNS server installed. He experiences host name resolution problems on the network. In order to rectify the situation, he wants to troubleshoot DNS name resolution problems on the network.
Which of the following tools will he use to do this?
Sasha wants to add an entry to your DNS database for your mail server. Which of the following types of resource records will she use to accomplish this?
You work as a Network Administrator for McRobert Inc. You want to know the NetBIOS name of your computer. Which of the following commands will you use?
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases. The email header of the suspicious email is given below:
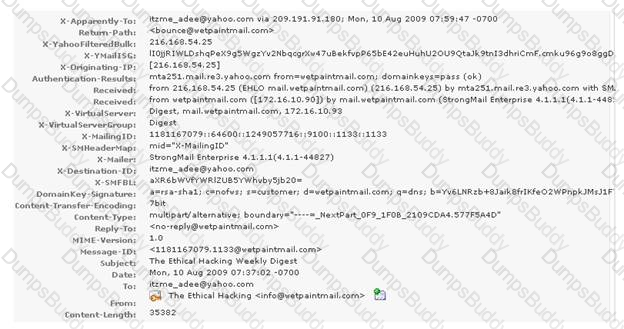
What is the IP address of the sender of this email?
A firewall is a combination of hardware and software, used to provide security to a network. It is used to protect an internal network or intranet against unauthorized access from the Internet or other outside networks. It restricts inbound and outbound access and can analyze all traffic between an internal network and the Internet. Users can configure a firewall to pass or block packets from specific IP addresses and ports. Which of the following tools works as a firewall for the Linux 2.4 kernel?
Adam works as a Computer Hacking Forensic Investigator in a law firm. He has been assigned with his first project. Adam collected all required evidences and clues. He is now required to write an investigative report to present before court for further prosecution of the case. He needs guidelines to write an investigative report for expressing an opinion. Which of the following are the guidelines to write an investigative report in an efficient way?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following IDs is used to reassemble the fragments of a datagram at the destination point?
Which of the following tools is used to detect spam email without checking the content?
You work as a Desktop Support Technician for umbrella Inc. The company uses a Windows-based network. An employee of the production department is facing the problem in the IP configuration of the network connection.
He called you to resolve the issue. You suspect that the IP configuration is not configured properly. You want to use the ping command to ensure that IPv4 protocol is working on a computer. While running the ping command from the command prompt, you find that Windows Firewall is blocking the ping command. You enter the following command in the elevated command prompt on the computer:
netsh advfirewall firewall add rule name="ICMPv4" protocol=icmpv4:any,any dir=in action=allow
Which of the following actions will this command perform?
Adam works as a professional Computer Hacking Forensic Investigator. He has been called by the FBI to examine data of the hard disk, which is seized from the house of a suspected terrorist.
Adam decided to acquire an image of the suspected hard drive. He uses a forensic hardware tool, which is capable of capturing data from IDE, Serial ATA, SCSI devices, and flash cards. This tool can also produce MD5 and CRC32 hash while capturing the data. Which of the following tools is Adam using?
Which of the following is allowed by a company to be addressed directly from the public network and is hardened to screen the rest of its network from security exposure?
Victor wants to send an encrypted message to his friend. He is using certain steganography technique to accomplish this task. He takes a cover object and changes it accordingly to hide information. This secret information is recovered only when the algorithm compares the changed cover with the original cover. Which of the following Steganography methods is Victor using to accomplish the task?
Which of the following is a form of cheating or copying someone else's work or idea without acknowledging the source?
Web applications are accessed by communicating over TCP ports via an IP address. Choose the two most common Web Application TCP ports and their respective protocol names.
Each correct answer represents a complete solution. Choose two.
Which of the following is the default port used by Simple Mail Transfer Protocol (SMTP)?
Which of the following intrusion detection systems (IDS) monitors network traffic and compares it against an established baseline?
Which of the following is a reason to implement security logging on a DNS server?
The National Shoes Inc. has an SNMP enabled router installed on its network. IT Manager wants to monitor all SNMP traffic generated by the router. So, he installs a Network Monitor on a Windows2000 Server computer on the network. The router is configured to send traps to an SNMP manager installed on another server. He wants to get a notification whenever the network router raises an SNMP trap. What will he do to achieve this?
(Click the Exhibit button on the toolbar to see the case study.)
Each correct answer represents a part of the solution. Choose two.
Which of the following is a hardware/software platform that is designed to analyze, detect, and report on security related events. NIPS is designed to inspect traffic and based on its configuration or security policy, it can drop the malicious traffic?
Which of the following tools works by using standard set of MS-DOS commands and can create an MD5 hash of an entire drive, partition, or selected files?
Peter works as a professional Computer Hacking Forensic Investigator for eLaw-Suit law firm. He is working on a case of a cyber crime. Peter knows that the good investigative report should not only communicate the relevant facts, but also present expert opinion. This report should not include the cases in which the expert acted as a lay witness. Which of the following type of witnesses is a lay witness?
Which of the following utilities is used to display the current TCP/IP configuration of a Windows NT computer?
You work as a Network Security Administrator for NetPerfect Inc. The company has a Windowsbased network. You are incharge of the data and network security of the company. While performing a threat log analysis, you observe that one of the database administrators is pilfering confidential data. What type of threat is this?
Which of the following is the correct order of loading system files into the main memory of the system, when the computer is running on Microsoft's Windows XP operating system?
Which of the following are not functions of the SNORT application?
Each correct answer represents a complete solution. Choose two.
Fill in the blank with the appropriate term.
___________ is a technique used to make sure that incoming packets are actually from the networks that they claim to be from.
In which of the following IDS evasion attacks does an attacker send a data packet such that IDS accepts the data packet but the host computer rejects it?
You work as a Network Administrator for McNeil Inc. The company's Windows 2000-based network is configured with Internet Security and Acceleration (ISA) Server 2000. You want to configure intrusion detection on the server. You find that the different types of attacks on the Intrusion Detection tab page of the IP Packet Filters Properties dialog box are disabled. What is the most likely cause?
What is the name of the group of blocks which contains information used by the operating system in Linux system?
Which of the following is the process of categorizing attack alerts produced from IDS?
Which of the following partitions contains the system files that are used to start the operating system?
Which of the following Windows XP system files handles memory management, I/O operations, and interrupts?
You work as a Network Administrator for Tech Perfect Inc. The office network is configured as an IPv6 network. You have to configure a computer with the IPv6 address, which is equivalent to an IPv4 publicly routable address. Which of the following types of addresses will you choose?
Which of the following attacks is designed to deduce the brand and/or version of an operating system or application?
Sandra, a novice computer user, works on Windows environment. She experiences some problem regarding bad sectors formed in a hard disk of her computer. She wants to run CHKDSK command to check the hard disk for bad sectors and to fix the errors, if any, occurred. Which of the following switches will she use with CHKDSK command to accomplish the task?
Which of the following types of attacks uses ICMP to consume bandwidth and crash sites?
Which of the following forensic tool suite is developed for Linux operating system?
Which of the following statements are true about an IPv6 network?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following can be applied as countermeasures against DDoS attacks?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following utilities allows to view all files including invisible files and folders on a Macintosh OS X?
Which of the following is an expression of interference that triggers a false positive signal during an intrusion detection process performed by IDS?
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple small-sized packets to the target computer. Hence, it becomes very difficult for an IDS to detect the attack signatures of such attacks. Which of the following tools can be used to perform session splicing attacks?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following statements is NOT true about the file slack spaces in Windows operating system?
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network.
You want to know the statistics of each protocol installed on your computer. Which of the following commands will you use?
Which of the following image file formats uses a lossy data compression technique?
A firewall is a combination of hardware and software, used to provide security to a network. It is used to protect an internal network or intranet against unauthorized access from the Internet or other outside networks. It restricts inbound and outbound access and can analyze all traffic between an internal network and the Internet. Users can configure a firewall to pass or block packets from specific IP addresses and ports. Which of the following tools works as a firewall for the Linux 2.4 kernel?
Which of the following can be monitored by using the host-based intrusion detection system (HIDS)?
You work as a Network Administrator for Net Perfect Inc. The company has a TCP/IP-based network. You are configuring an Internet connection on a server. Which of the following servers filters outbound Web traffic on the network?
John works as a Network Security Administrator for NetPerfect Inc. The manager of the company has told John that the company's phone bill has increased drastically. John suspects that the company's phone system has been cracked by a malicious hacker. Which attack is used by malicious hackers to crack the phone system?
Which of the following tools is used to locate lost files and partitions to restore data from a formatted, damaged, or lost partition in Windows and Apple Macintosh computers?
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domain-based network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. The network contains a Windows Server 2008 Core computer.
You want to install the DNS server role on the Windows Server 2008 Core computer. Which of the following commands will you use to accomplish the task?
Which of the following is a hardware/software platform that is designed to analyze, detect, and report on security related events. NIPS is designed to inspect traffic and based on its configuration or security policy, it can drop the malicious traffic?
Which of the following information must the fragments carry for the destination host to reassemble them back to the original unfragmented state?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following IP packet elements is responsible for authentication while using IPSec?
You work as a Network Administrator for Net Perfect Inc. The company has a TCP/IP-based network. The network is connected to the Internet through a firewall. A user complains that he is unable to access the abc.com site. However, he can access all other sites. Which of the following tools will help you diagnose the problem?