Exhibit

You have configured the SRX Series device to switch packets for multiple directly connected hosts that are within the same broadcast domain However, the traffic between two hosts in the same broadcast domain are not matching any security policies
Referring to the exhibit, what should you do to solve this problem?
You are asked to deploy filter-based forwarding on your SRX Series device for incoming traffic sourced from the 10.10 100 0/24 network in this scenario, which three statements are correct? (Choose three.)
Exhibit:
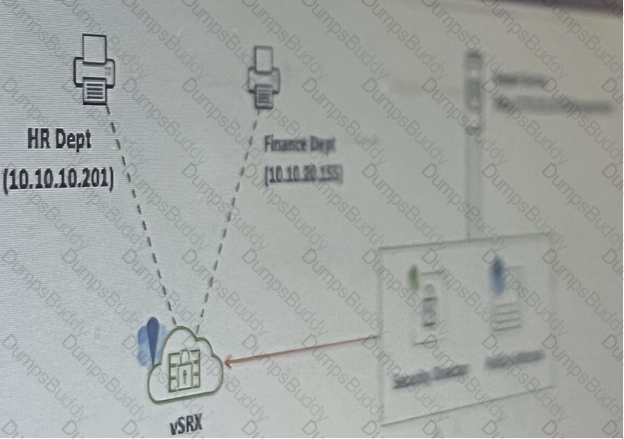
Referring to the exhibit, your company’s infrastructure team implemented new printers
To make sure that the policy enforcer pushes the updated Ip address list to the SRX.
Which three actions are required to complete the requirement? (Choose three )
Exhibit
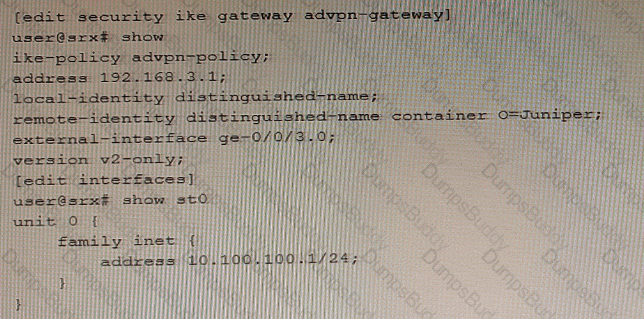
Referring to the exhibit, a spoke member of an ADVPN is not functioning correctly.
Which two commands will solve this problem? (Choose two.)
A)

B)
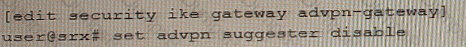
C)

D)

You must implement an IPsec VPN on an SRX Series device using PKI certificates for authentication. As part of the implementation, you are required to ensure that the certificate submission, renewal, and retrieval processes are handled
automatically from the certificate authority.
In this scenario, which statement is correct.
You are asked to control access to network resources based on the identity of an authenticated device
Which three steps will accomplish this goal on the SRX Series firewalls? (Choose three )
You want to configure a threat prevention policy.
Which three profiles are configurable in this scenario? (Choose three.)
you are connecting two remote sites to your corporate headquarters site. You must ensure that traffic
passes corporate headquarter.
In this scenario, which VPN should be used?
You are asked to deploy Juniper atp appliance in your network. You must ensure that incidents and
alerts are sent to your SIEM.
In this scenario, which logging output format is supported?
Exhibit
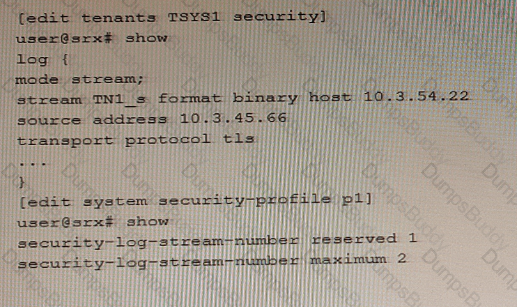
An administrator wants to configure an SRX Series device to log binary security events for tenant systems.
Referring to the exhibit, which statement would complete the configuration?
Exhibit
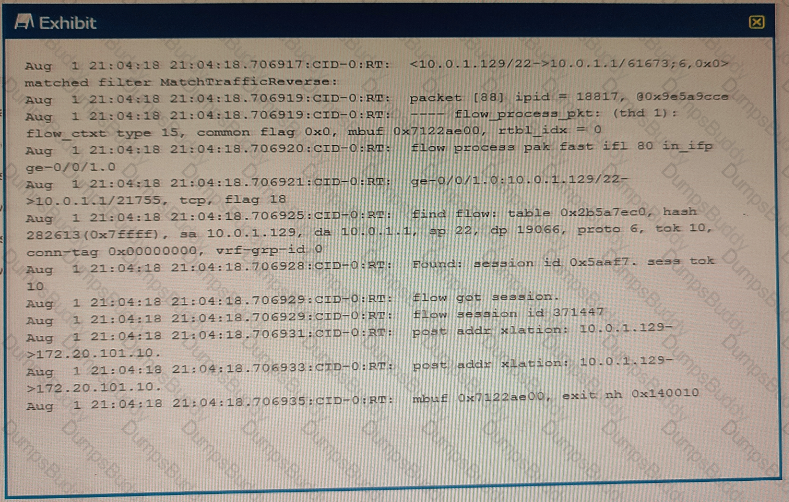
You are using trace options to verity NAT session information on your SRX Series device
Referring to the exhibit, which two statements are correct? (Choose two.)
Exhibit
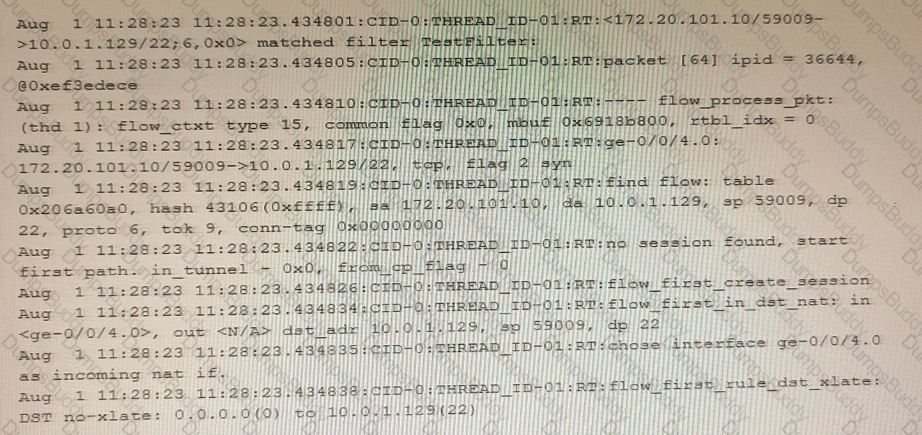
The exhibit shows a snippet of a security flow trace.
In this scenario, which two statements are correct? (Choose two.)
Refer to the exhibit,
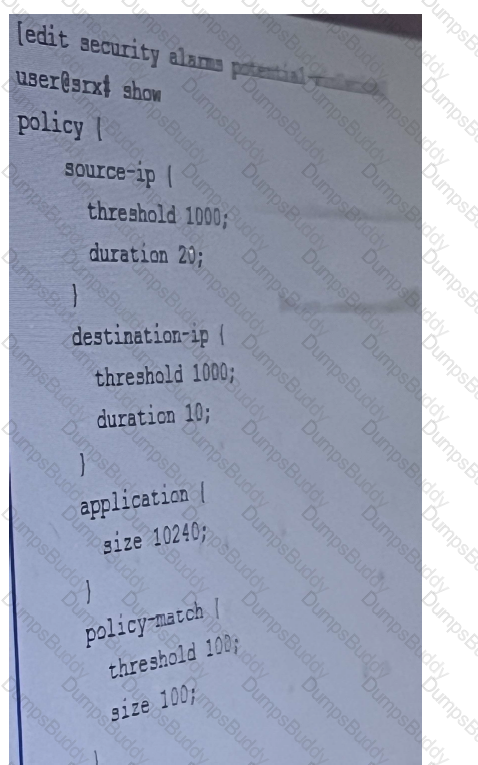
which two potential violations will generate alarm ? (Choose Two)
Your IPsec VPN configuration uses two CoS forwarding classes to separate voice and data traffic. How many IKE security associations are required between the IPsec peers in this scenario?
You configured a chassis cluster for high availability on an SRX Series device and enrolled this HA cluster with the Juniper ATP Cloud. Which two statements are correct in this scenario? (Choose two.)
Exhibit

The show network-access aaa radius-servers command has been issued to solve authentication issues.
Referring to the exhibit, to which two authentication servers will the SRX Series device continue to send requests? (Choose TWO)
You are asked to look at a configuration that is designed to take all traffic with a specific source ip address and forward the
traffic to a traffic analysis server for further evaluation. The configuration is no longer working as intended.
Referring to the exhibit which change must be made to correct the configuration?
You are asked to configure a security policy on the SRX Series device. After committing the policy, you receive the “Policy is out of sync between RE and PFE
Which command would be used to solve the problem?
Exhibit
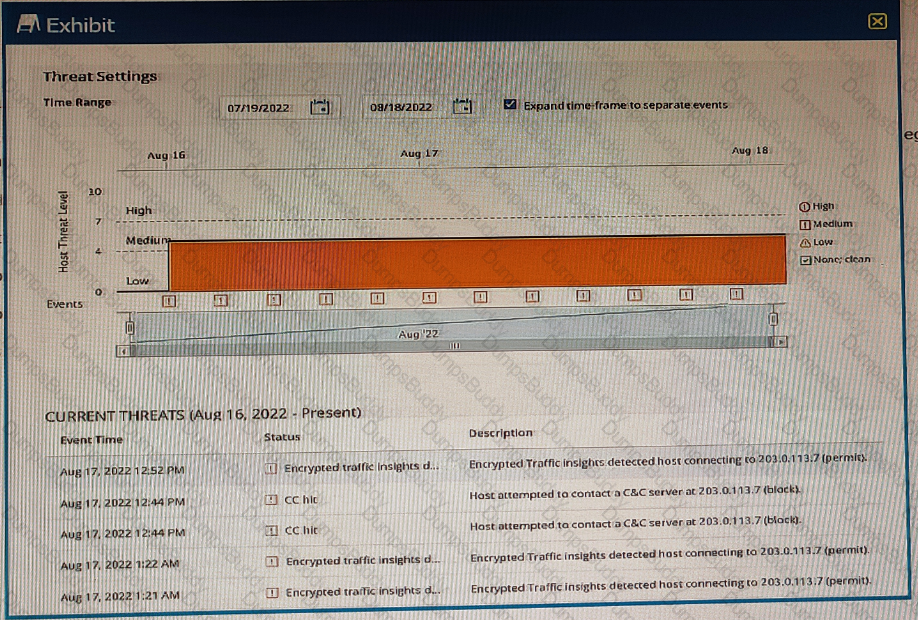
You are using ATP Cloud and notice that there is a host with a high number of ETI and C&C hits sourced from the same investigation and notice that some of the events have not been automatically mitigated.
Referring to the exhibit, what is a reason for this behavior?
You have a webserver and a DNS server residing in the same internal DMZ subnet. The public Static NAT addresses for
the servers are in the same subnet as the SRX Series devices internet-facing interface. You implement DNS doctoring to
ensure remote users can access the webserver.Which two statements are true in this scenario? (Choose two.)
You want to use selective stateless packet-based forwarding based on the source address.
In this scenario, which command will allow traffic to bypass the SRX Series device flow daemon?
In Juniper ATP Cloud, what are two different actions available in a threat prevention policy to deal with an infected host? (Choose two.)
According to the log shown in the exhibit, you notice the IPsec session is not establishing.
What is the reason for this behavior?
You are configuring transparent mode on an SRX Series device. You must permit IP-based traffic only, and BPDUs must be restricted to the VLANs from which they originate.
Which configuration accomplishes these objectives?
A)
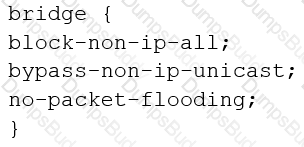
B)

C)
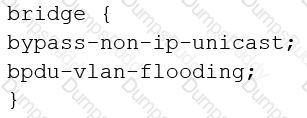
D)
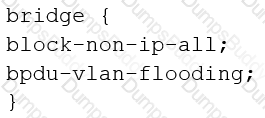
You want to identify potential threats within SSL-encrypted sessions without requiring SSL proxy to decrypt the session contents. Which security feature achieves this objective?