Which two functions does Juniper ATP Cloud perform to reduce delays in the inspection of files? (Choose two.)
Click the Exhibit button.

You are validating the configuration template for device access. The commands in the exhibit have been entered to secure IP access to an SRX Series device.
Referring to the exhibit, which two statements are true? (Choose two.)
You want to manually failover the primary Routing Engine in an SRX Series high availability cluster pair.
Which step is necessary to accomplish this task?
Which statement regarding Juniper Identity Management Service (JIMS) domain PC probes is true?
You are asked to implement IPS on your SRX Series device.
In this scenario, which two tasks must be completed before a configuration will work? (Choose two.)
You are asked to block malicious applications regardless of the port number being used.
In this scenario, which two application security features should be used? (Choose two.)
Exhibit

When trying to set up a server protection SSL proxy, you receive the error shown. What are two reasons for this error? (Choose two.)
You want to control when cluster failovers occur.
In this scenario, which two specific parameters would you configure on an SRX Series device? (Choose two.)
Which two statements are correct about SSL proxy server protection? (Choose two.)
You want to permit access to an application but block application sub-Which two security policy features provide this capability? (Choose two.)
Exhibit

You are asked to track BitTorrent traffic on your network. You need to automatically add the workstations to the High_Risk_Workstations feed and the servers to the BitTorrent_Servers feed automatically to help mitigate future threats.
Which two commands would add this functionality to the FindThreat policy? (Choose two.)
A)

B)

C)

D)

Click the Exhibit button.
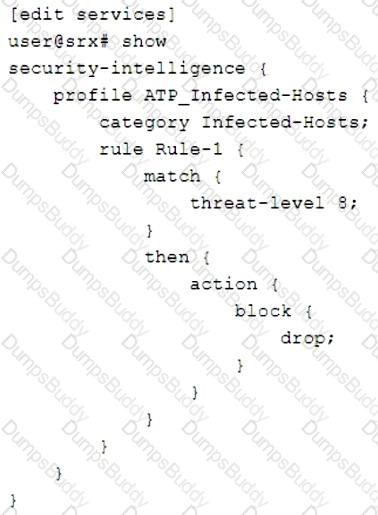
Referring to the exhibit, what will the SRX Series device do in this configuration?
Which two statements are correct about the fab interface in a chassis cluster? (Choose two.)
Exhibit

You are trying to create a security policy on your SRX Series device that permits HTTP traffic from your private 172 25.11.0/24 subnet to the Internet You create a policy named permit-http between the trust and untrust zones that permits HTTP traffic. When you issue a commit command to apply the configuration changes, the commit fails with the error shown in the exhibit.
Which two actions would correct the error? (Choose two.)
You want to be alerted if the wrong password is used more than three times on a single device within five minutes.
Which Juniper Networks solution will accomplish this task?
Click the Exhibit button.

You are asked to create a security policy that will automatically add infected hosts to the infected hosts feed and block further communication through the SRX Series device.
What needs to be added to this configuration to complete this task?
Which two devices would you use for DDoS protection with Policy Enforcer? (Choose two.)
Your manager asks you to provide firewall and NAT services in a private cloud.
Which two solutions will fulfill the minimum requirements for this deployment? (Choose two.)