An administrator has created several virtual machines on the same host server and requires them to each be on separate VLANs. Which of the following should the administrator configure to meet this goal?
An administrator would like to get more speed out of a wireless network. The administrator decides to configure the AP with a frequency width of 40MHz. Which of the following features is the administrator MOST likely using?
Which of the following wireless router security measures provides access to a network by allowing only devices on an approved physical address list?
Which of the following network protocols is used for a secure command line interface for management of network devices?
Which of the following can determine the last time an address lease was renewed on a network device?
An administrator edits the network firewall configuration. After editing the configuration, the administrator logs the date and time of the edit and why it was performed in the firewall documentation. Which of the following BEST describes these actions?
Which of the following commands would be used to identify how many hops a data packet makes before reaching its final destination?
When troubleshooting a connectivity issue, which of the following commands will give the technician a list of the host names connected to the network?
A network administrator suspects that recent traffic problems could be caused by a high CPU load on company routers. Which of the following would BEST be used to monitor CPU cycles on the routers?
A user reports that one of their critical programs no longer functions after a recent router upgrade in the office. A network technician is called in to troubleshoot the issue and documentation shows that the software needs full open connections over ports 558, 981, and 382 in order to function. Which of the following tools could the technician BEST use to troubleshoot this issue?
A network administrator is looking to implement a solution allowing users to utilize a common password to access most network resources for an organization. Which of the following would BEST provide this functionality?
Which of the following protocols would the network administrator use to protect login credentials when accessing a router terminal session?
Which of the following should be installed to prevent inappropriate websites from being viewed?
A network administrator opens up the RDP port to access network resources from home. Several months later, the administrator’s account is getting locked out constantly. After closing the port, which of the following should be used to identify the source of the attack?
Which of the following is needed when using WPA2-Enterprise wireless encryption?
A new technician has moved the wireless access point from the middle of the office to an area near a corner office. Wireless users are MOST likely to experience issues with which of the following?
An organization finds that most of the outgoing traffic on the network is directed at several Internet sites viewed by multiple computers simultaneously. Which of the following performance optimization methods would BEST alleviate network traffic?
A company has just installed a new network switch for an expanding department. The company is also piloting the use of a VoIP phone system for this department. Which of the following should be enabled on the new network switch?
Joe, a network technician, is troubleshooting in a wiring closet in 2011. The cabling to all the equipment does not match the documentation from 2007. Which of the following configuration management methods has been overlooked?
A technician grabs a network cable and connects two switches together. However, the ports fail to come up as indicated by the link lights. Which of the following is MOST likely the issue?
A technician needs multiple networks, high speeds, and redundancy on a system. Which of the following configurations should be considered for these requirements? (Select TWO).
A technician is attempting to set up a new laptop for a user. The user’s old laptop connects to the corporate wireless network “CompanyWiFi” automatically. However, when the technician looks for the “CompanyWiFi” network on the new laptop, he does not find it in the list of available networks. Both laptops have 802.11g wireless network adapters and are sitting next to each other on the user’s desk. Which of the following would MOST likely be the reason that the new laptop cannot see the “CompanyWiFi” network?
Which of the following transmission methods do DHCP enabled devices use to request an IP address?
A company is looking for the simplest solution to help prioritize VoIP traffic on its congested network. Which of the following would BEST accomplish this?
A technician is troubleshooting a wireless network that was setup previously. The network is a hybrid of 802.11g and 802.11n WAPs. Users are not able to view or connect to the 802.11n WAPs. Which of the following is MOST likely the cause?
A Linux-based workstation is unable to connect to an IP printer on the same network segment. The printer IP address settings have been verified. How would a network technician verify IP address settings on the Linux-based workstation?
A technician has traced a POTS line to a 110 block. Which of the following devices would the technician MOST likely use to see if the line carries a dial tone?
Which of the following routing protocols utilizes the DUAL algorithm for determining best path?
Which of the following would the telecommunications carrier use to segregate customer traffic over long fiber links?
Standards such as JPEG and ASCII operate at which of the following OSI model layers?
A technician needs to ensure that traffic from a specific department is separated within several switches. Which of the following needs to be configured on the switch to separate the traffic?
A user reports intermittent network connectivity from their desktop PC. A technician determines the cause to be a bad wall jack and fixes the jack. Which of the following should the technician do NEXT?
In order to limit the number of dynamic addresses of hosts on a network, which of the following can be implemented?
Which of the following port numbers needs to be open on a firewall to allow FTP traffic?
A user wants to connect seven PCs together for a game night. Which of the following should the user install to help with this task?
The application layer in the TCP/IP model is comparable to which of the following layers in the OSI model?
A technician finds that the network card is no longer functioning. At which of the following OSI layers is the problem occurring?
A SOHO client has tasked Joe, a technician, with setting up a basic SOHO network to support four laptops and one desktop PC. The client would also like to have a basic wireless network to use for internal devices only that is secure. Given the list of requirements, which of the following devices would Joe need to purchase for his client? (Select TWO).
While working on a PC, a technician notices 0.0.0.0 in the routing table. Which of the following does this indicate?
After the technician has established a theory of probable cause of a user reported problem, which of the following should the technician do NEXT in the troubleshooting process?
A customer has requested that a new piece of network equipment be installed so that the customer can have multiple subnets for each department, but allow network traffic from each department to reach one another without the use of a router. Which of the following network devices would satisfy this customer’s requirements?
Which of the following is the unit used to transfer information at Layer 2 of the OSI model?
Which of the following network protocols is used to transport email across the Internet?
Which of the following commands displays the routing table on a server or workstation?
The components of a NIC function at which of the following layers of the OSI model? (Select TWO).
A technician is installing 802.11a wireless access points in an open warehouse 300 feet (91.44 meters) long and 200 feet (60.96 meters) wide. Which of the following would be the LEAST number of devices needed to provide coverage to the entire building?
A user does not have network connectivity. While testing the cable the technician receives the below reading on the cable tester:
1-----------1
2-----------2
3-----------3
4-----------4
5-----------5
6-----------6
7-----------7
8-----------8
Which of the following should the technician do NEXT?
A large corporate office is looking to place smaller network closets around campus to handle switching for remote workstations. To which of the following is this referring?
The unit responsible for the successful shaping and transmission of a digital signal is called:
A user’s network connection is slow. After testing the cabling, the cable tester shows that only pins 1, 2, 3 and 6 are being used. After accurately terminating both ends, the tester displays the same results. Which of the following is the MOST likely cause?
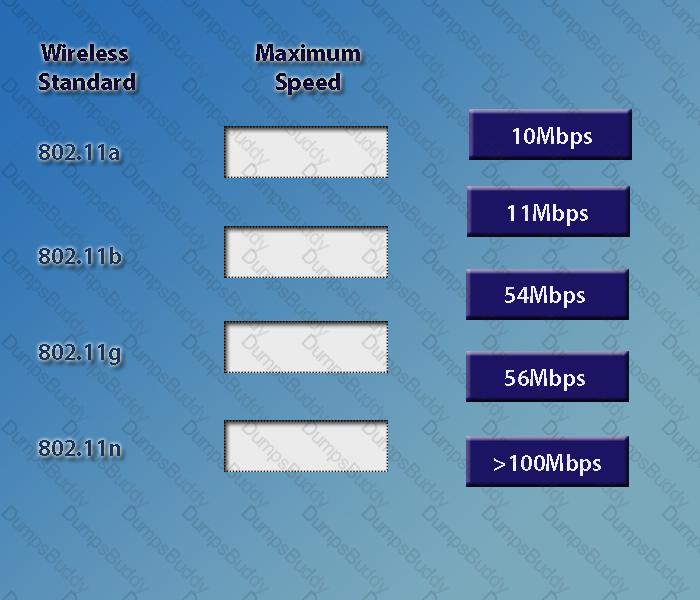
Drag and drop the following maximum speeds to their corresponding wireless standards. Tokens can be used more than once.
Which of the following network topologies is MOST likely used in remote access VPN?
A technician is not getting a link light on two switches connected by a fiber cable. After the cable tests good, which of the following should the technician check NEXT?
A technician has been called about intermittent connectivity near IDF 2. Multiple cables were recently pulled through a common conduit. Which of the following is MOST likely the cause of the problem?
Which of the following cable types use pins 1 and 2 to transmit and 3 and 6 to receive?
Users are reporting wired connectivity drops in a new office with brand new CAT6 infrastructure. Which of the following tools should a technician use to BEST troubleshoot this issue?
A technician is troubleshooting a problem where data packets are being corrupted. Which of the following connectivity problems should the technician check?
Multiple networked devices running on the same physical hardware that provide central access to applications and files, where each device runs as a piece of software are known as:
A network administrator needs to ensure there is no same channel interference for an 802.11n deployment with four WAPs. Which of the following channel setting configurations meets this criteria when using 40 MHz channels?
A technician testing an Ethernet card uses a cable wired with pins 1,2 to pins 3,6 on the same RJ-45 plug. Which of the following describes what the technician is using?
A technician notices a newly installed CAT5 cable is longer than the standard maximum length. Which of the following problems would this MOST likely cause?
Which of the following cable types is employed to protect against interference in the physical environment or when security is a concern?
Which of the following is used to allow multiple sources on a single optical cable?
The security measure used to reduce vulnerabilities for MOST network devices that require regular application and monitoring is:
Which of the following wireless standards uses a block encryption cipher rather than a stream cipher?
A user wants to send information and ensure that it was not modified during transmission. Which of the following should be implemented?
A technician enters a username and password once and can access multiple databases without being prompted to reenter their password. This is an example of which of the following?
Which of the following provides the STRONGEST security for a tunneled connection over the Internet?
Which of the following protocols can be implemented to provide encryption during transmission between email gateways?
Which of the following is being described when symbols are displayed on the side of the building and/or walking path, to identify open hot-spots?
Which of the following is the wireless encryption standard associated with WPA2?
The company requires all users to authenticate to the network with a smart card, a pin number, and a fingerprint scan. Which of the following BEST describes the user authentication being used?
A strong network firewall would likely support which of the following security features for controlling access? (Select TWO).
A network technician has configured a new firewall with a rule to deny UDP traffic. Users have reported that they are unable to access Internet websites. The technician verifies this using the IP address of a popular website. Which of the following is the MOST likely cause of the error?
A home user wishes to secure the wireless network using strong encryption, so they decide to use AES. Which of the following would be used as the encryption method?
Which of the following are authentication methods that can use AAA authentication? (Select TWO).
Which of the following protocols is used to provide secure authentication and encryption over non-secure networks?
Which of the following would a network administrator use to scan a network for vulnerabilities?
Which of the following would allow a network administrator to implement a user authentication method that uses X.509 certificates?
Which of the following remote access types requires a certificate for connectivity?
An organization only has a single public IP address and needs to host a website for its customers. Which of the following services is required on the network firewall to ensure connectivity?
Which of the following attacks would allow an intruder to do port mapping on a company’s internal server from a separate company server on the Internet?
Encryption provides which of the following to data being transferred across the network?
A small business owner is setting up a SOHO office. The business owner needs one device that will allow for Internet access, trunk VLANs, translate multiple private IP addresses into public IP addresses, and filter packets. Which of the following network devices will allow for all functions?
A technician needs to install network device in a SOHO network. The office requires 9 wired workstations to share and print data. Which of the following can the technician use?
Joe, a network technician, is asked to install a couple new WAP’s inside a back warehouse that was added to a main warehouse facility that already has complete wireless coverage on both the 2.4GHz and 5GHz frequencies. Joe already has a complete wireless heat map of the main warehouse. Which of the following is the first step that Joe should do before choosing which WAP’s to use?
Which of the following wireless standards has a MAXIMUM transfer rate of 11Mbps?
During a disaster recovery test, several billing representatives need to be temporarily setup to take payments from customers. It has been determined that this will need to occur over a wireless network, with security being enforced where possible. Which of the following configurations should be used in this scenario?
Which of the following is the BEST way to prevent new users from connecting to a wireless access point, but still allow already connected users to continue to connect?
If a technician does not assign an IP address to a device, the DHCP server will assign the device a:
A technician is troubleshooting a printing issue where some users in an office are unable to print. Which of the following should be the FIRST step in troubleshooting this issue?
A technician is reviewing the following company diagram to determine proper connectivity settings:
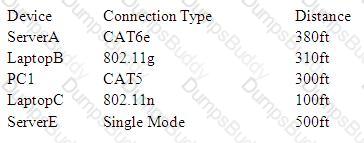
Which of the following device configurations is out of specifications?
A user is unable to communicate with any local network resources, but is connected to the wireless network and can access the Internet. The network technician notices that the laptop has an incorrect IP address, even though it shows it is connected. Which of the following is the MOST likely cause?
Which of the following is a terminal emulator used to manage a network device?
A company has multiple WAPs within close proximity to each other to allow users to move about seamlessly through the building with their laptops, without losing any connection. However, this has had the opposite effect, causing any user that is close to two of the access points to constantly reconnect to the wireless network. Which of the following should be changed on all the WAPs to allow this to work as the customer intended?
Which of the following tools would a technician use to determine if a CAT6 patch cable has an open or short?
Which of the following can a technician use when installing a wireless network in a lounge to prevent inappropriate website images?
A technician is upgrading the wiring in an older office building. The building currently contains some CAT3, CAT5, and CAT6 cables. The technician cannot visually distinguish between the cables because they are all the same color. Which of the following tools would help the technician determine which wires are the CAT3 and CAT5 cables needing to be replaced with CAT6 ones?
A network technician is trying to run a protocol analyzer and is instructed to record the chimney offload state of TCP. Which of the following utilities did the technician use to check this parameter with the output listed below?
Querying active state...
TCP Global Parameters
----------------------------------------------
Receive-Side Scaling State : enabled
Chimney Offload State : disabled
Receive Window Auto-Tuning Level : normal
Add-On Congestion Control Provider : ctcp
ECN Capability : disabled
RFC 1323 Timestamps : disabled
An administrator is trying to retrieve management information from the network devices on their LAN. Which of the following monitoring resources provides the ability to collect this information encrypted over the network?
A customer with a SOHO requires fast, secure, cost-effective access to the Internet. Which of the following would be the MOST appropriate solution? (Select TWO).
Various desktop computers are not getting a link light even though the patch cables were replaced. Cables on a 110-block patch panel are suspected to be causing the issues. Which of the following hardware tools would MOST likely be used to troubleshoot and resolve the issue? (Select TWO).
A technician has to terminate a CAT3 cable to a 110 block. Which of the following tools should the technician use?
A server that filters traffic between a WAN and a LAN is which of the following?