Scenario 9: UpNet, a networking company, has been certified against ISO/IEC 27001. It provides network security, virtualization, cloud computing, network hardware, network management software, and networking technologies.
The company's recognition has increased drastically since gaining ISO/IEC 27001 certification. The certification confirmed the maturity of UpNefs operations and its compliance with a widely recognized and accepted standard.
But not everything ended after the certification. UpNet continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. The top management was not willing to employ a full-time team of internal auditors, so they decided to outsource the internal audit function. This form of internal audits ensured independence, objectivity, and that they had an advisory role about the continual improvement of the ISMS.
Not long after the initial certification audit, the company created a new department specialized in data and storage products. They offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. This caused changes to the operations of the other departments already covered in the ISMS certification scope.
Therefore. UpNet initiated a risk assessment process and an internal audit. Following the internal audit result, the company confirmed the effectiveness and efficiency of the existing and new processes and controls.
The top management decided to include the new department in the certification scope since it complies with ISO/IEC 27001 requirements. UpNet announced that it is ISO/IEC 27001 certified and the certification scope encompasses the whole company.
One year after the initial certification audit, the certification body conducted another audit of UpNefs ISMS. This audit aimed to determine the UpNefs ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure that the ISMS is being continually improved. The audit team confirmed that the certified ISMS continues to fulfill
the requirements of the standard. Nonetheless, the new department caused a significant impact on governing the management system. Moreover, the certification body was not informed about any changes. Thus, the UpNefs certification was suspended.
Based on the scenario above, answer the following question:
UpNet ensured independence, objectivity, and advisory activities from the internal audit. Is this action acceptable?
A telecommunications company uses the AES method for ensuring that confidential information is protected. This means that they use a single key to encrypt and
decrypt the information. What kind of control does the company use?
Audit methods can be either with or without interaction with individuals representing the auditee. Which two of the following methods are with interaction?
AppFolk, a software development company, is seeking certification against ISO/IEC 27001. In the initial phases of the external audit, the certification body in discussion with the company excluded the marketing division from the audit scope, although they stated in their ISMS scope that the whole company is included. Is this acceptable?
Scenario 9: UpNet, a networking company, has been certified against ISO/IEC 27001. It provides network security, virtualization, cloud computing, network hardware, network management software, and networking technologies.
The company's recognition has increased drastically since gaining ISO/IEC 27001 certification. The certification confirmed the maturity of UpNefs operations and its compliance with a widely recognized and accepted standard.
But not everything ended after the certification. UpNet continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. The top management was not willing to employ a full-time team of internal auditors, so they decided to outsource the internal audit function. This form of internal audits ensured independence, objectivity, and that they had an advisory role about the continual improvement of the ISMS.
Not long after the initial certification audit, the company created a new department specialized in data and storage products. They offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. This caused changes to the operations of the other departments already covered in the ISMS certification scope.
Therefore. UpNet initiated a risk assessment process and an internal audit. Following the internal audit result, the company confirmed the effectiveness and efficiency of the existing and new processes and controls.
The top management decided to include the new department in the certification scope since it complies with ISO/IEC 27001 requirements. UpNet announced that it is ISO/IEC 27001 certified and the certification scope encompasses the whole company.
One year after the initial certification audit, the certification body conducted another audit of UpNefs ISMS. This audit aimed to determine the UpNefs ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure that the ISMS is being continually improved. The audit team confirmed that the certified ISMS continues to fulfill
the requirements of the standard. Nonetheless, the new department caused a significant impact on governing the management system. Moreover, the certification body was not informed about any changes. Thus, the UpNefs certification was suspended.
Based on the scenario above, answer the following question:
What type of audit is illustrated in the last paragraph of scenario 9?
You are an experience ISMS audit team leader carrying out a third-party certification audit of an organization specialising in the secure disposal of confidential documents and removable media. Both documents and media are shredded in military grade devices which make it impossible to reconstruct the original.
The audit has gone well and you are just about to start to write the audit report, 30 minutes before the closing meeting. At
this point one of the organization's employees knocks on your door and asks if they can speak to you. They tell you that when things get busy her manager tells her to use a lower grade industrial shredder instead as the organisation has more of these and they operate faster. You were not informed about the existence or use of these machines by the auditee.
Select three options for how you should respond to this information.
Which three of the following options are an advantage of using a sampling plan for the audit?
To verify conformity to control 8.15 Logging of ISO/IEC 27001 Annex A, the audit team verified a sample of server logs to determine if they can be edited or deleted. Which audit procedure was used?
Scenario 7: Lawsy is a leading law firm with offices in New Jersey and New York City. It has over 50 attorneys offering sophisticated legal services to clients in business and commercial law, intellectual property, banking, and financial services. They believe they have a comfortable position in the market thanks to their commitment to implement information security best practices and remain up to date with technological developments.
Lawsy has implemented, evaluated, and conducted internal audits for an ISMS rigorously for two years now. Now, they have applied for ISO/IEC 27001 certification to ISMA, a well-known and trusted certification body.
During stage 1 audit, the audit team reviewed all the ISMS documents created during the implementation. They also reviewed and evaluated the records from management reviews and internal audits.
Lawsy submitted records of evidence that corrective actions on nonconformities were performed when necessary, so the audit team interviewed the internal auditor. The interview validated the adequacy and frequency of the internal audits by providing detailed insight into the internal audit plan and procedures.
The audit team continued with the verification of strategic documents, including the information security policy and risk evaluation criteria. During the information security policy review, the team noticed inconsistencies between the documented information describing governance framework (i.e., the information security policy) and the procedures.
Although the employees were allowed to take the laptops outside the workplace, Lawsy did not have procedures in place regarding the use of laptops in such cases. The policy only provided general information about the use of laptops. The company relied on employees' common knowledge to protect the confidentiality and integrity of information stored in the laptops. This issue was documented in the stage 1 audit report.
Upon completing stage 1 audit, the audit team leader prepared the audit plan, which addressed the audit objectives, scope, criteria, and procedures.
During stage 2 audit, the audit team interviewed the information security manager, who drafted the information security policy. He justified the Issue identified in stage 1 by stating that Lawsy conducts mandatory information security training and awareness sessions every three months.
Following the interview, the audit team examined 15 employee training records (out of 50) and concluded that Lawsy meets requirements of ISO/IEC 27001 related to training and awareness. To support this conclusion, they photocopied the examined employee training records.
Based on the scenario above, answer the following question:
Should the auditor archive the copies of employee training records after the completion of the audit? Refer to scenario 7.
You are performing an ISMS initial certification audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to conduct the closing meeting. During the final audit team meeting, as an audit team leader, you agree to report 2 minor nonconformities and 1 opportunity for improvement as below:
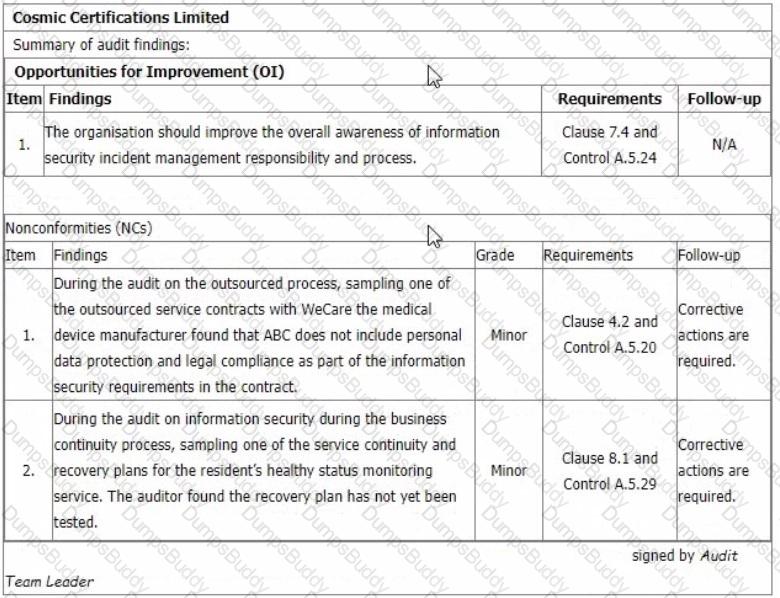
Select one option of the recommendation to the audit programme manager you are going to advise to the auditee at the closing meeting.
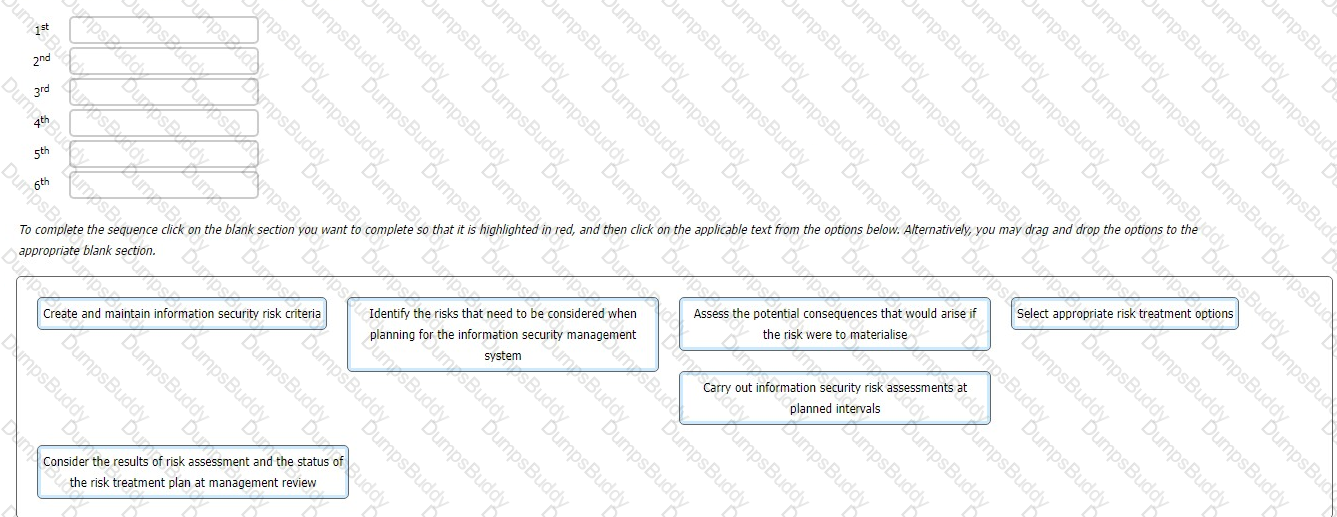
You are an experienced ISMS audit team leader providing instruction to a class of auditors in training. The subject of today's lesson is the management of information security risk in accordance with the requirements of ISO/IEC 27001:2022.
You provide the class with a series of activities. You then ask the class to sort these activities into the order in which they appear in the standard.
What is the correct sequence they should report back to you?
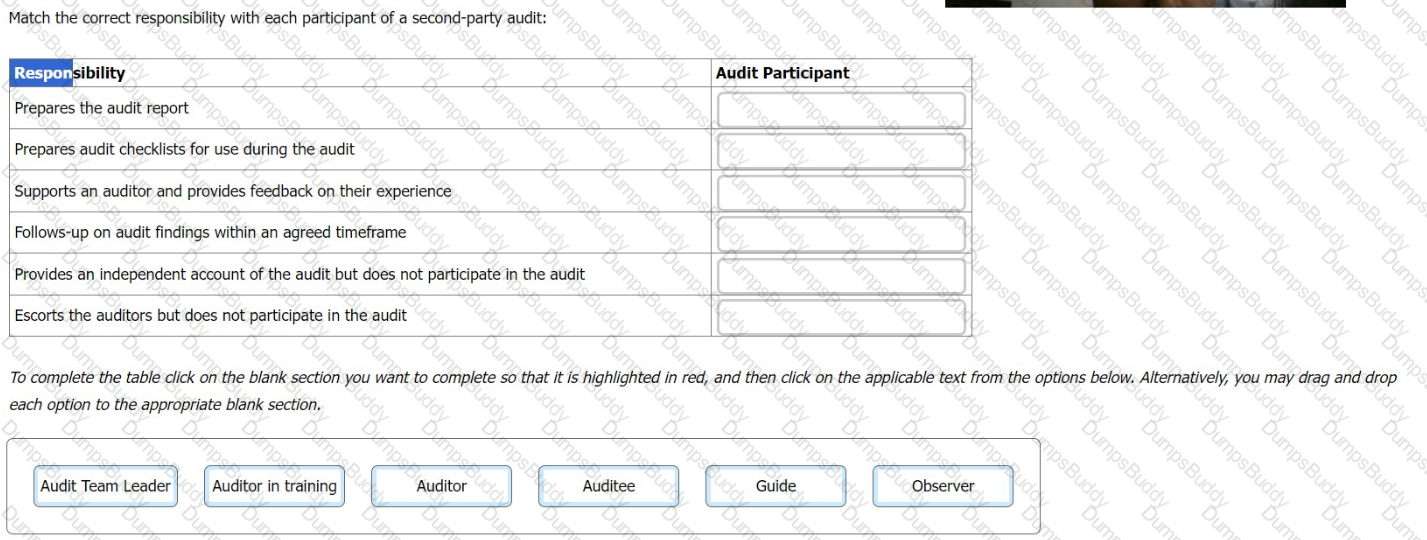
Match the correct responsibility with each participant of a second-party audit:
Scenario 1: Fintive is a distinguished security provider for online payments and protection solutions. Founded in 1999 by Thomas Fin in San Jose, California, Fintive
offers services to companies that operate online and want to improve their information security, prevent fraud, and protect user information such as PII. Fintive centers
its decision-making and operating process based on previous cases. They gather customer data, classify them depending on the case, and analyze them. The company
needed a large number of employees to be able to conduct such complex analyses. After some years, however, the technology that assists in conducting such analyses
advanced as well. Now, Fintive is planning on using a modern tool, a chatbot, to achieve pattern analyses toward preventing fraud in real-time. This tool would also be
used to assist in improving customer service.
This initial idea was communicated to the software development team, who supported it and were assigned to work on this project. They began integrating the chatbot
on their existing system. In addition, the team set an objective regarding the chatbot which was to answer 85% of all chat queries.
After the successful integration of the chatbot, the company immediately released it to their customers for use. The chatbot, however, appeared to have some issues.
Due to insufficient testing and lack of samples provided to the chatbot during the training phase, in which it was supposed "to learn" the queries pattern, the chatbot
failed to address user queries and provide the right answers. Furthermore, the chatbot sent random files to users when it received invalid inputs such as odd patterns
of dots and special characters. Therefore, the chatbot was unable to properly answer customer queries and the traditional customer support was overwhelmed with
chat queries and thus was unable to help customers with their requests.
Consequently, Fintive established a software development policy. This policy specified that whether the software is developed in-house or outsourced, it will undergo a
black box testing prior to its implementation on operational systems.
Based on this scenario, answer the following question:
The chatbot was supposed "to learn" the queries pattern to address user queries and provide the right answers. What type of technology enables
this?
You are conducting an ISMS audit in the despatch department of an international logistics organisation that provides shipping services to large organisations including local hospitals and government offices. Parcels typically contain pharmaceutical products, biological samples, and documents such as passports and driving licences. You note that the company records show a very large number of returned items with causes including misaddressed labels and, in 15% of cases, two or more labels for different addresses for the one package. You are interviewing the Shipping Manager (SM).
You: Are items checked before being dispatched?
SM: Any obviously damaged items are removed by the duty staff before being dispatched, but the small profit margin makes it uneconomic to implement a formal checking process.
You: What action is taken when items are returned?
SM: Most of these contracts are relatively low value, therefore it has been decided that it is easier and more convenient to simply reprint the label and re-send individual parcels than it is to implement an investigation.
You raise a nonconformity against ISO 27001:2022 based on the lack of control of the labelling process.
At the closing meeting, the Shipping Manager issues an apology to you that his comments may have been misunderstood. He says that he did not realise that there is a background IT process that automatically checks that the right label goes onto the right parcel otherwise the parcel is ejected at labelling. He asks that you withdraw your nonconformity.
Select three options of the correct responses that you as the audit team leader would make to the request of the Shipping Manager.
You are the audit team leader conducting a third-party audit of an online insurance organisation. During Stage 1, you found that the organisation took a very cautious risk approach and included all the information security controls in ISO/IEC 27001:2022 Appendix A in their Statement of Applicability.
During the Stage 2 audit, your audit team found that there was no evidence of the implementation of the three controls (5.3 Segregation of duties, 6.1 Screening, 7.12 Cabling security) shown in the extract from the Statement of Applicability. No risk treatment plan was found.

Select three options for the actions you would expect the auditee to take in response to a
nonconformity against clause 6.1.3.e of ISO/IEC 27001:2022.
The data centre at which you work is currently seeking ISO/IEC27001:2022 certification. In preparation for your initial certification visit, several internal audits have been carried out by a colleague working at another data centre within your Group. They secured their own ISO/IEC 27001:2022 certificate earlier in the year.
You have just qualified as an Internal ISMS auditor and your manager has asked you to review the audit process and audit findings as a final check before the external Certification Body arrives.
Which four of the following would cause you concern in respect of conformity to ISO/IEC 27001:2022 requirements?
Scenario 8: EsBank provides banking and financial solutions to the Estonian banking sector since September 2010. The company has a network of 30 branches with over 100 ATMs across the country.
Operating in a highly regulated industry, EsBank must comply with many laws and regulations regarding the security and privacy of data. They need to manage information security across their operations by implementing technical and nontechnical controls. EsBank decided to implement an ISMS based on ISO/IEC 27001 because it provided better security, more risk control, and compliance with key requirements of laws and regulations.
Nine months after the successful implementation of the ISMS, EsBank decided to pursue certification of their ISMS by an independent certification body against ISO/IEC 27001 .The certification audit included all of EsBank’s systems, processes, and technologies.
The stage 1 and stage 2 audits were conducted jointly and several nonconformities were detected. The first nonconformity was related to EsBank’s labeling of information. The company had an information classification scheme but there was no information labeling procedure. As a result, documents requiring the same level of protection would be labeled differently (sometimes as confidential, other times sensitive).
Considering that all the documents were also stored electronically, the nonconformity also impacted media handling. The audit team used sampling and concluded that 50 of 200 removable media stored sensitive information mistakenly classified as confidential. According to the information classification scheme, confidential information is allowed to be stored in removable media, whereas storing sensitive information is strictly prohibited. This marked the other nonconformity.
They drafted the nonconformity report and discussed the audit conclusions with EsBank’s representatives, who agreed to submit an action plan for the detected nonconformities within two months.
EsBank accepted the audit team leader's proposed solution. They resolved the nonconformities by drafting a procedure for information labeling based on the classification scheme for both physical and electronic formats. The removable media procedure was also updated based on this procedure.
Two weeks after the audit completion, EsBank submitted a general action plan. There, they addressed the detected nonconformities and the corrective actions taken, but did not include any details on systems, controls, or operations impacted. The audit team evaluated the action plan and concluded that it would resolve the nonconformities. Yet, EsBank received an unfavorable recommendation for certification.
Based on the scenario above, answer the following question:
By drafting a procedure for information labeling, EsBank has:
In the context of a management system audit, please identify the sequence of a typical process of collecting and verifying information. The first one has been done for you.
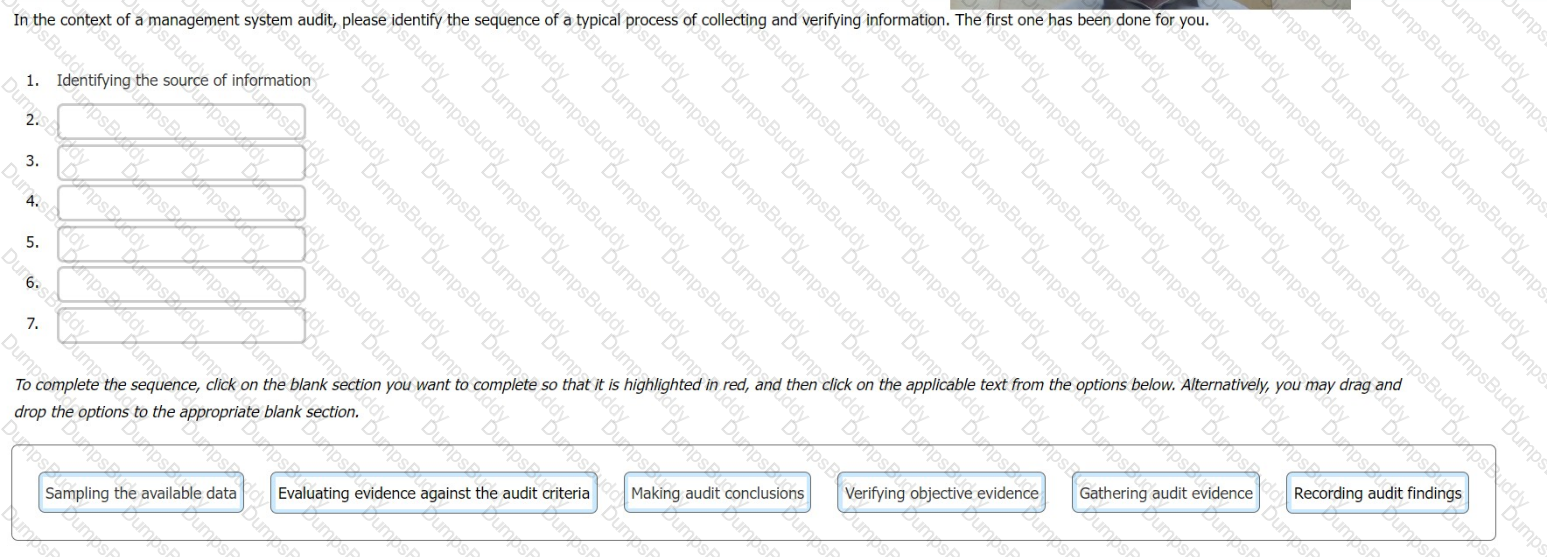
Which six of the following actions are the individual(s) managing the audit programme responsible for?
Which three of the following work documents are not required for audit planning by an auditor conducting a certification audit?
Which two of the following phrases would apply to "plan" in relation to the Plan-Do-Check-Act cycle for a business process?
During a follow-up audit, you notice that a nonconformity identified for completion before the follow-up audit is still outstanding.
Which four of the following actions should you take?
Which one of the following options best describes the main purpose of a Stage 2 third-party audit?
After drafting the audit conclusions, the work documents of the audit team leader were reviewed by another auditor selected by the certification body. Is this acceptable?
Scenario 8: EsBank provides banking and financial solutions to the Estonian banking sector since September 2010. The company has a network of 30 branches with over 100 ATMs across the country.
Operating in a highly regulated industry, EsBank must comply with many laws and regulations regarding the security and privacy of data. They need to manage information security across their operations by implementing technical and nontechnical controls. EsBank decided to implement an ISMS based on ISO/IEC 27001 because it provided better security, more risk control, and compliance with key requirements of laws and regulations.
Nine months after the successful implementation of the ISMS, EsBank decided to pursue certification of their ISMS by an independent certification body against ISO/IEC 27001 .The certification audit included all of EsBank’s systems, processes, and technologies.
The stage 1 and stage 2 audits were conducted jointly and several nonconformities were detected. The first nonconformity was related to EsBank’s labeling of information. The company had an information classification scheme but there was no information labeling procedure. As a result, documents requiring the same level of protection would be labeled differently (sometimes as confidential, other times sensitive).
Considering that all the documents were also stored electronically, the nonconformity also impacted media handling. The audit team used sampling and concluded that 50 of 200 removable media stored sensitive information mistakenly classified as confidential. According to the information classification scheme, confidential information is allowed to be stored in removable media, whereas storing sensitive information is strictly prohibited. This marked the other nonconformity.
They drafted the nonconformity report and discussed the audit conclusions with EsBank’s representatives, who agreed to submit an action plan for the detected nonconformities within two months.
EsBank accepted the audit team leader's proposed solution. They resolved the nonconformities by drafting a procedure for information labeling based on the classification scheme for both physical and electronic formats. The removable media procedure was also updated based on this procedure.
Two weeks after the audit completion, EsBank submitted a general action plan. There, they addressed the detected nonconformities and the corrective actions taken, but did not include any details on systems, controls, or operations impacted. The audit team evaluated the action plan and concluded that it would resolve the nonconformities. Yet, EsBank received an unfavorable recommendation for certification.
Based on the scenario above, answer the following question:
According to scenario 8, the audit team evaluated the action plan and concluded that it would resolve the detected nonconformities. Is this acceptable?
You are performing an ISMS audit at a residential nursing home (ABC) that provides healthcare services. The next step in your audit plan is to verify the information security of ABC's healthcare mobile app development, support, and lifecycle process. During the audit, you learned the organization outsourced the mobile app development to a professional software development company with CMMI Level 5, ITSM (ISO/IEC 20000-1), BCMS (ISO 22301) and ISMS (ISO/IEC 27001) certified.
The IT Manager presented the software security management procedure and summarised the process as following:
The mobile app development shall adopt "security-by-design" and "security-by-default" principles, as a minimum. The following security
functions for personal data protection shall be available:
Access control.
Personal data encryption, i.e., Advanced Encryption Standard (AES) algorithm, key lengths: 256 bits; and
Personal data pseudonymization.
Vulnerability checked and no security backdoor
You sample the latest Mobile App Test report, details as follows:
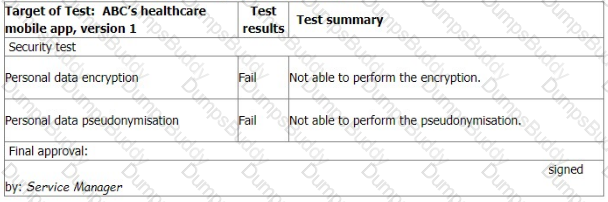
You ask the IT Manager why the organisation still uses the mobile app while personal data encryption and pseudonymization tests failed. Also, whether the Service Manager is authorised to approve the test.
The IT Manager explains the test results should be approved by him according to the software security management procedure.
The reason why the encryption and pseudonymisation functions failed is that these functions heavily slowed down the system and service performance. An extra 150% of resources are needed to cover this. The Service Manager agreed that access control is good enough and acceptable. That's why the Service Manager signed the approval.
You are preparing the audit findings. Select the correct option.
Auditors should have certain knowledge and skills; while audit team leaders should have some additional knowledge and skills. From the following list, select two that only apply to audit team leaders.
You are an experienced audit team leader guiding an auditor in training.
Your team is currently conducting a third-party surveillance audit of an organisation that stores data on behalf of external clients. The auditor in training has been tasked with reviewing the PEOPLE controls listed in the Statement of Applicability (SoA) and mplemented at the site.
Select four controls from the following that would you expect the auditor in training to review.
An external auditor received an offer to conduct an ISMS audit at a research development company. Before accepting it, they discussed with the internal auditor of the auditee, who was their friend, about previous audit reports. Is this acceptable?
A property of Information that has the ability to prove occurrence of a claimed event.
You are performing an ISMS audit at a residential nursing home that provides healthcare services and are reviewing the Software Code Management (SCM) system. You found a total of 10 user accounts on the SCM. You confirm that one of the users, Scott, resigned 9-months
ago. The SCM System Administrator confirmed Scott's last check-out of the source code was found 1 month ago. He was using one of the uthorized desktops from the local network in a secure area.
You check with the user de-registration procedure which states "Managers have to make sure of deregistration of the user account and authorisation immediately from the relevant ICT system and/or equipment after resignation approval." There was no deregistration record for user Scott.
The IT Security Manager explains that Scott still comes back to the office every month after he resigned to provide support on source code maintenance. That's why his account on SCM still exists.
You would like to investigate other areas further to collect more audit evidence. Select three options that would not be valid audit trails.
In the event of an Information security incident, system users' roles and responsibilities are to be observed, except:
Which two of the following options for information are not required for audit planning of a certification audit?
Which two activities align with the “Check’’ stage of the Plan-Do-Check-Act cycle when applied to the process of managing an internal audit program as described in ISO 19011?
Scenario 4: SendPay is a financial company that provides its services through a network of agents and financial institutions. One of their main services is transferring money worldwide. SendPay, as a new company, seeks to offer top quality services to its clients. Since the company offers international transactions, it requires from their clients to provide personal information, such as their identity, the reason for the transactions, and other details that might be needed to complete the transaction. Therefore, SendPay has implemented security measures to protect their clients' information, including detecting, investigating, and responding to any information security threats that may emerge. Their commitment to offering secure services was also reflected during the ISMS implementation where the company invested a lot of time and resources.
Last year, SendPay unveiled their digital platform that allows money transactions through electronic devices, such as smartphones or laptops, without requiring an additional fee. Through this platform, SendPay's clients can send and receive money from anywhere and at any time. The digital platform helped SendPay to simplify the company's operations and further expand its business. At the time, SendPay was outsourcing its software operations, hence the project was completed by the software development team of the outsourced company. The same team was also responsible for maintaining the technology infrastructure of SendPay.
Recently, the company applied for ISO/IEC 27001 certification after having an ISMS in place for almost a year. They contracted a certification body that fit their criteria. Soon after, the certification body appointed a team of four auditors to audit SendPay's ISMS.
During the audit, among others, the following situations were observed:
1.The outsourced software company had terminated the contract with SendPay without prior notice. As a result, SendPay was unable to immediately bring the services back in-house and its operations were disrupted for five days. The auditors requested from SendPay's representatives to provide evidence that they have a plan to follow in cases of contract terminations. The representatives did not provide any documentary evidence but during an interview, they told the auditors that the top management of SendPay had identified two other software development companies that could provide services immediately if similar situations happen again.
2.There was no evidence available regarding the monitoring of the activities that were outsourced to the software development company. Once again, the representatives of SendPay told the auditors that they regularly communicate with the software development company and that they are appropriately informed for any possible change that might occur.
3.There was no nonconformity found during the firewall testing. The auditors tested the firewall configuration in order to determine the level of security provided by
these services. They used a packet analyzer to test the firewall policies which enabled them to check the packets sent or received in real-time.
Based on this scenario, answer the following question:
Based on scenario 4, the auditors requested documentary evidence regarding the monitoring process of outsourced operations. What does this indicate?
Scenario 3: NightCore is a multinational technology company based in the United States that focuses on e-commerce, cloud computing, digital streaming, and artificial intelligence. After having an information security management system (ISMS) implemented for over 8 months, they contracted a certification body to conduct a third party audit in order to get certified against ISO/IEC 27001.
The certification body set up a team of seven auditors. Jack, the most experienced auditor, was assigned as the audit team leader. Over the years, he received many well known certifications, such as the ISO/IEC 27001 Lead Auditor, CISA, CISSP, and CISM.
Jack conducted thorough analyses on each phase of the ISMS audit, by studying and evaluating every information security requirement and control that was implemented by NightCore. During stage 2 audit. Jack detected several nonconformities. After comparing the number of purchased invoices for software licenses with the software inventory, Jack found out that the company has been using the illegal versions of a software for many computers. He decided to ask for an explanation from the top management about this nonconformity and see whether they were aware about this. His next step was to audit NightCore's IT Department. The top management assigned Tom, NightCore's system administrator, to act as a guide and accompany Jack and the audit team toward the inner workings of their system and their digital assets infrastructure.
While interviewing a member of the Department of Finance, the auditors discovered that the company had recently made some unusual large transactions to one of their consultants. After gathering all the necessary details regarding the transactions. Jack decided to directly interview the top management.
When discussing about the first nonconformity, the top management told Jack that they willingly decided to use a copied software over the original one since it was cheaper. Jack explained to the top management of NightCore that using illegal versions of software is against the requirements of ISO/IEC 27001 and the national laws and regulations. However, they seemed to be fine with it.
Several months after the audit, Jack sold some of NightCore's information that he collected during the audit for a huge amount of money to competitors of NightCore.
Based on this scenario, answer the following question:
Based on audit principles, should Jack contact the certification body regarding the second nonconformity? Refer to scenario 3.
A decent visitor is roaming around without visitor's ID. As an employee you should do the following, except:
You see a blue color sticker on certain physical assets. What does this signify?
Which of the options below is a control related to the management of personnel that aims to avoid the occurrence of incidents?
You are the person responsible for managing the audit programme and deciding the size and composition of the audit team for a specific audit. Select the two factors that should be considered.
An audit team leader is planning a follow-up audit after the completion of a third-party surveillance audit earlier in the year. They have decided they will verify the nonconformities that require corrections before they move on to consider corrective actions.
Based on the descriptions below, which four of the following are corrections for nonconformities identified at the surveillance?
Scenario 9: UpNet, a networking company, has been certified against ISO/IEC 27001. It provides network security, virtualization, cloud computing, network hardware, network management software, and networking technologies.
The company's recognition has increased drastically since gaining ISO/IEC 27001 certification. The certification confirmed the maturity of UpNefs operations and its compliance with a widely recognized and accepted standard.
But not everything ended after the certification. UpNet continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. The top management was not willing to employ a full-time team of internal auditors, so they decided to outsource the internal audit function. This form of internal audits ensured independence, objectivity, and that they had an advisory role about the continual improvement of the ISMS.
Not long after the initial certification audit, the company created a new department specialized in data and storage products. They offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. This caused changes to the operations of the other departments already covered in the ISMS certification scope.
Therefore. UpNet initiated a risk assessment process and an internal audit. Following the internal audit result, the company confirmed the effectiveness and efficiency of the existing and new processes and controls.
The top management decided to include the new department in the certification scope since it complies with ISO/IEC 27001 requirements. UpNet announced that it is ISO/IEC 27001 certified and the certification scope encompasses the whole company.
One year after the initial certification audit, the certification body conducted another audit of UpNefs ISMS. This audit aimed to determine the UpNefs ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure that the ISMS is being continually improved. The audit team confirmed that the certified ISMS continues to fulfill
the requirements of the standard. Nonetheless, the new department caused a significant impact on governing the management system. Moreover, the certification body was not informed about any changes. Thus, the UpNefs certification was suspended.
Based on the scenario above, answer the following question:
UpNet outsourced the internal audit function, as provided in scenario 9. Does it impact the internal audit process?
You are performing an ISO 27001 ISMS surveillance audit at a residential nursing home, ABC Healthcare Services. ABC uses a healthcare mobile app designed and maintained by a supplier, WeCare, to monitor residents' well-being. During the audit, you learn that 90% erf the residents' family members regularly receive medical device advertisements from WeCare, by email and SMS once a week. The service agreement between ABC and WeCare prohibits the supplier from using residents' personal data. ABC has received many complaints from residents and their family members.
The Service Manager says that the complaints were investigated as an information security incident which found that they were justified. Corrective actions have been planned and implemented according to the nonconformity and corrective action management procedure.
You write a nonconformity "ABC failed to comply with information security control A.5.34 (Privacy and protection of PII) relating to the personal data of residents' and their family members. A supplier, WeCare, used residents' personal information to send advertisements to family members"
Select three options of the corrections and corrective actions listed that you would expect ABC to make in response to the nonconformity
Which one of the following statements best describes the purpose of conducting a document review?
You are an experienced ISMS audit team leader. During the conducting of a third-party surveillance audit, you decide to test your auditee's knowledge of ISO/IEC 27001's risk management requirements.
You ask her a series of questions to which the answer is either 'that is true' or 'that is false'. Which four of the following should she answer 'that is true'?
Select the words that best complete the sentence:
To complete the sentence with the word(s) click on the blank section you want to complete so that it is highlighted in red, and then click on the application text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.

Scenario 5: Data Grid Inc. is a well-known company that delivers security services across the entire information technology infrastructure. It provides cybersecurity software, including endpoint security, firewalls, and antivirus software. For two decades, Data Grid Inc. has helped various companies secure their networks through advanced products and services. Having achieved reputation in the information and network security field, Data Grid Inc. decided to obtain the ISO/IEC 27001 certification to better secure its internal and customer assets and gain competitive advantage.
Data Grid Inc. appointed the audit team, who agreed on the terms of the audit mandate. In addition, Data Grid Inc. defined the audit scope, specified the audit criteria, and proposed to close the audit within five days. The audit team rejected Data Grid Inc.'s proposal to conduct the audit within five days, since the company has a large number of employees and complex processes. Data Grid Inc. insisted that they have planned to complete the audit within five days, so both parties agreed upon conducting the audit within the defined duration. The audit team followed a risk-based auditing approach.
To gain an overview of the main business processes and controls, the audit team accessed process descriptions and organizational charts. They were unable to perform a deeper analysis of the IT risks and controls because their access to the IT infrastructure and applications was restricted. However, the audit team stated that the risk that a significant defect could occur to Data Grid Inc.'s ISMS was low since most of the company's processes were automated. They therefore evaluated that the ISMS, as a whole, conforms to the standard requirements by asking the representatives of Data Grid Inc. the following questions:
•How are responsibilities for IT and IT controls defined and assigned?
•How does Data Grid Inc. assess whether the controls have achieved the desired results?
•What controls does Data Grid Inc. have in place to protect the operating environment and data from malicious software?
•Are firewall-related controls implemented?
Data Grid Inc.'s representatives provided sufficient and appropriate evidence to address all these questions.
The audit team leader drafted the audit conclusions and reported them to Data Grid Inc.'s top management. Though Data Grid Inc. was recommended for certification by the auditors, misunderstandings were raised between Data Grid Inc. and the certification body in regards to audit objectives. Data Grid Inc. stated that even though the audit objectives included the identification of areas for potential improvement, the audit team did not provide such information.
Based on this scenario, answer the following question:
Which type of audit risk was defined as “low* by the audit team? Refer to scenario 5.
The audit team leader prepares the audit plan for an initial certification stage 2 audit to ISO/IEC 27001:2022.
Which one of the following statements is true?
Scenario 5: Data Grid Inc. is a well-known company that delivers security services across the entire information technology infrastructure. It provides cybersecurity software, including endpoint security, firewalls, and antivirus software. For two decades, Data Grid Inc. has helped various companies secure their networks through advanced products and services. Having achieved reputation in the information and network security field, Data Grid Inc. decided to obtain the ISO/IEC 27001 certification to better secure its internal and customer assets and gain competitive advantage.
Data Grid Inc. appointed the audit team, who agreed on the terms of the audit mandate. In addition, Data Grid Inc. defined the audit scope, specified the audit criteria, and proposed to close the audit within five days. The audit team rejected Data Grid Inc.'s proposal to conduct the audit within five days, since the company has a large number of employees and complex processes. Data Grid Inc. insisted that they have planned to complete the audit within five days, so both parties agreed upon conducting the audit within the defined duration. The audit team followed a risk-based auditing approach.
To gain an overview of the main business processes and controls, the audit team accessed process descriptions and organizational charts. They were unable to perform a deeper analysis of the IT risks and controls because their access to the IT infrastructure and applications was restricted. However, the audit team stated that the risk that a significant defect could occur to Data Grid Inc.'s ISMS was low since most of the company's processes were automated. They therefore evaluated that the ISMS, as a whole, conforms to the standard requirements by asking the representatives of Data Grid Inc. the following questions:
•How are responsibilities for IT and IT controls defined and assigned?
•How does Data Grid Inc. assess whether the controls have achieved the desired results?
•What controls does Data Grid Inc. have in place to protect the operating environment and data from malicious software?
•Are firewall-related controls implemented?
Data Grid Inc.'s representatives provided sufficient and appropriate evidence to address all these questions.
The audit team leader drafted the audit conclusions and reported them to Data Grid Inc.'s top management. Though Data Grid Inc. was recommended for certification by the auditors, misunderstandings were raised between Data Grid Inc. and the certification body in regards to audit objectives. Data Grid Inc. stated that even though the audit objectives included the identification of areas for potential improvement, the audit team did not provide such information.
Based on this scenario, answer the following question:
Based on scenario 5, the audit team assessed the ISMS as a whole, rather than assessing the effectiveness and conformity of each process. Is this acceptable?
OrgXY is an ISO/IEC 27001-certified software development company. A year after being certified, OrgXY's top management informed the certification body that the company was not ready for conducting the surveillance audit. What happens in this case?
You are carrying out your first third-party ISMS surveillance audit as an Audit Team Leader. You are presently in the auditee's data centre with another member of your audit team.
You are currently in a large room that is subdivided into several smaller rooms, each of which has a numeric combination lock and swipe card reader on the door. You notice two external contractors using a swipe card and combination number provided by the centre's reception desk to gain access to a client's suite to carry out authorised electrical repairs.
You go to reception and ask to see the door access record for the client's suite. This indicates only one card was swiped. You ask the receptionist and they reply, "yes it's a common problem. We ask everyone to swipe their cards but with contractors especially, one tends to swipe and the rest simply 'tailgate' their way in" but we know who they are from the reception sign-in.
Based on the scenario above which one of the following actions would you now take?
After completing Stage 1 and in preparation for a Stage 2 initial certification audit, the auditee informs the audit team leader that they wish to extend the audit scope to include two additional sites that have recently been acquired by the organisation.
Considering this information, what action would you expect the audit team leader to take?
Scenario 2: Knight is an electronics company from Northern California, US that develops video game consoles. Knight has more than 300 employees worldwide. On the
fifth anniversary of their establishment, they have decided to deliver the G-Console, a new generation video game console aimed for worldwide markets. G-Console is
considered to be the ultimate media machine of 2021 which will give the best gaming experience to players. The console pack will include a pair of VR headset, two
games, and other gifts.
Over the years, the company has developed a good reputation by showing integrity, honesty, and respect toward their customers. This good reputation is one of the
reasons why most passionate gamers aim to have Knight's G-console as soon as it is released in the market. Besides being a very customer-oriented company, Knight
also gained wide recognition within the gaming industry because of the developing quality. Their prices are a bit higher than the reasonable standards allow.
Nonetheless, that is not considered an issue for most loyal customers of Knight, as their quality is top-notch.
Being one of the top video game console developers in the world, Knight is also often the center of attention for malicious activities. The company has had an
operational ISMS for over a year. The ISMS scope includes all departments of Knight, except Finance and HR departments.
Recently, a number of Knight's files containing proprietary information were leaked by hackers. Knight's incident response team (IRT) immediately started to analyze
every part of the system and the details of the incident.
The IRT's first suspicion was that Knight's employees used weak passwords and consequently were easily cracked by hackers who gained unauthorized access to their
accounts. However, after carefully investigating the incident, the IRT determined that hackers accessed accounts by capturing the file transfer protocol (FTP) traffic.
FTP is a network protocol for transferring files between accounts. It uses clear text passwords for authentication.
Following the impact of this information security incident and with IRT's suggestion, Knight decided to replace the FTP with Secure Shell (SSH) protocol, so anyone
capturing the traffic can only see encrypted data.
Following these changes, Knight conducted a risk assessment to verify that the implementation of controls had minimized the risk of similar incidents. The results of
the process were approved by the ISMS project manager who claimed that the level of risk after the implementation of new controls was in accordance with the
company's risk acceptance levels.
Based on this scenario, answer the following question:
Based on scenario 2, Knight decided to replace the FTP with Secure Shell (SSH) protocol. Should the Statement of Applicability (SoA) be updated in this case?
You are performing an ISMS audit at a residential nursing home called ABC that provides healthcare services. You find all nursing home residents wear an electronic wristband for monitoring their location, heartbeat, and blood pressure always. You learned that the electronic wristband automatically uploads all data to the artificial intelligence (AI) cloud server for healthcare monitoring and analysis by healthcare staff.
To verify the scope of ISMS, you interview the management system representative (MSR) who explains that the ISMS scope covers an outsourced data center.
Select three options for the audit evidence you need to find to verify the scope of the ISMS.
You are performing an ISMS audit at a residential nursing home railed ABC that provides healthcare services. The next step in your audit plan is to verify the effectiveness of the continual improvement process. During the audit, you learned most of the residents' family members (90%) receive WeCare medical device promotional advertisements through email and SMS once a week via ABC's healthcare mobile app. All of them do not agree on the use of the collected personal data (or marketing or any other purposes than nursing and medical care on the signed service agreement with ABC. They have very strong reason to believe that ABC is leaking residents' and family members' personal information to a non-relevant third party and they have filed complaints.
The Service Manager says that all these complaints have been treated as nonconformities, and the corrective actions have been planned and implemented according to the Nonconformity and Corrective management procedure. The corrective action involved stopping working with WeCare the medical device manufacturer immediately and asking them to delete all personal data received as well as sending an apology email to all residents and their family members.
You are preparing the audit findings. Select one option of the correct finding.
Scenario 2: Knight is an electronics company from Northern California, US that develops video game consoles. Knight has more than 300 employees worldwide. On the
fifth anniversary of their establishment, they have decided to deliver the G-Console, a new generation video game console aimed for worldwide markets. G-Console is
considered to be the ultimate media machine of 2021 which will give the best gaming experience to players. The console pack will include a pair of VR headset, two
games, and other gifts.
Over the years, the company has developed a good reputation by showing integrity, honesty, and respect toward their customers. This good reputation is one of the
reasons why most passionate gamers aim to have Knight's G-console as soon as it is released in the market. Besides being a very customer-oriented company, Knight
also gained wide recognition within the gaming industry because of the developing quality. Their prices are a bit higher than the reasonable standards allow.
Nonetheless, that is not considered an issue for most loyal customers of Knight, as their quality is top-notch.
Being one of the top video game console developers in the world, Knight is also often the center of attention for malicious activities. The company has had an
operational ISMS for over a year. The ISMS scope includes all departments of Knight, except Finance and HR departments.
Recently, a number of Knight's files containing proprietary information were leaked by hackers. Knight's incident response team (IRT) immediately started to analyze
every part of the system and the details of the incident.
The IRT's first suspicion was that Knight's employees used weak passwords and consequently were easily cracked by hackers who gained unauthorized access to their
accounts. However, after carefully investigating the incident, the IRT determined that hackers accessed accounts by capturing the file transfer protocol (FTP) traffic.
FTP is a network protocol for transferring files between accounts. It uses clear text passwords for authentication.
Following the impact of this information security incident and with IRT's suggestion, Knight decided to replace the FTP with Secure Shell (SSH) protocol, so anyone
capturing the traffic can only see encrypted data.
Following these changes, Knight conducted a risk assessment to verify that the implementation of controls had minimized the risk of similar incidents. The results of
the process were approved by the ISMS project manager who claimed that the level of risk after the implementation of new controls was in accordance with the
company's risk acceptance levels.
Based on this scenario, answer the following question:
Which risk treatment option has Knight used in replacing FTP with SSH? Refer to scenario 2.
You are an experienced ISMS audit team leader, talking to an Auditor in training who has been assigned to your audit team. You want to ensure that they understand the importance of the Check stage of the Plan-Do-Check-Act cycle in respect of the operation of the information security management system.
You do this by asking him to select the words that best complete the sentence:
To complete the sentence with the best word(s), click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.
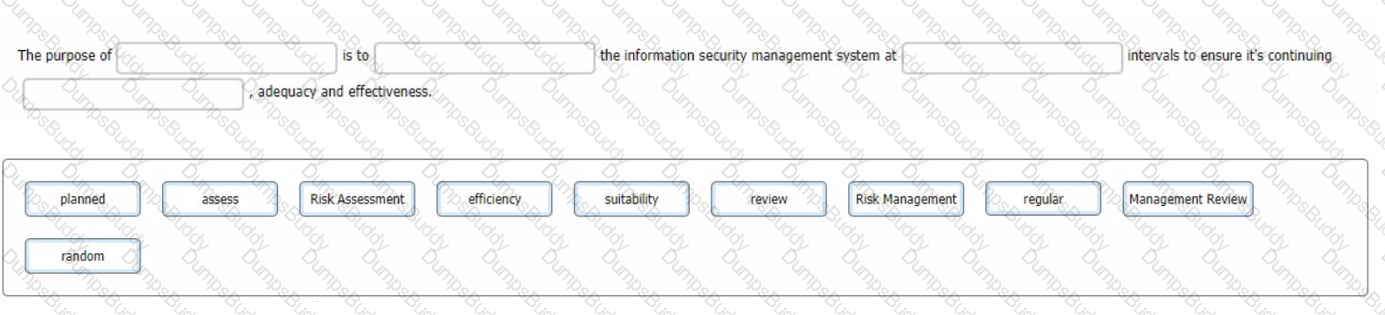
Which one of the following options best describes the purpose of a Stage 2 audit?