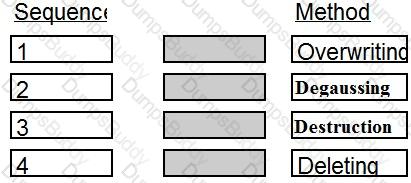
Place in order, from BEST (1) to WORST (4), the following methods to reduce the risk of data remanence on magnetic media.
Confidential information must not be shared with another unless the recipient has:
The threat modeling identifies a man-in-the-middle (MITM) exposure. Which countermeasure should the information system security officer (ISSO) select to mitigate the risk of a protected Health information (PHI) data leak?
Surgeons usually receive a single payment for the surgery and postoperative care. This bundling, or payment per episode, gives surgeons an economic incentive to.
Which one of these risk factors would be the LEAST important consideration in choosing a building site for a new computer facility?
___________ includes highly qualified pracitioners availble as consultants when needed.
Which central agency manages the health care delivery system in the United States?
Part of Administrative Safeguards under HIPAA is Workforce Security measures. Which is NOT a key element of a Workforce Security Element?
When responding to a client's request for information about the disclosure of his/her protected health information, which is NOT required?
The Baylor Hospital plan, started in 1929, laid the foundation for modern health insurance in the U.S. This was a _____ plan.
The adequacy of the health profession workforce (ie. supply and demand) can be determined by.
Assigning numeric and alphanumeric codes to diagnoses, procedures and services.
You work in the billing department of your agency and while processing claims, you notice the name of someone you know. Since you are curious, you decide to investigate and you pull their medical record and read it. Is this appropriate?
Initially, what was the primary purpose of private health insurance in the U.S.?
The CQI approach of producing health care "report cards," specifically HEDIS is a tool to encourage health care consumers to choose high-quality caregivers, but often.
Who was the first company to give their employees health insurance? What was the health insurance?
Is an interpretation of a law that is written by the responsible regulatory agency.
This type of hospital makes up 25% of hospitals in the United States and his a not for profit hospital.
Confidentiality protections cover not just a patient's health-related information, such as his or her diagnosis, but also other identifying information such as social security number and telephone numbers.
Under HIPAA Administrative Simplification, what must covered entities do in relation to submission of claims?
A health care provider is considering Internet access for their employees and patients. Which of the following is the organization's MOST secure solution for protection of data?
Under Title II of The Health Insurance Portability and Accountability Act, the administrative simplification provision:
The HIPPA task force must inventory the organization's systems, processes, policies, procedures and data to determine which elements are critical to patient care and central to the organizations business. All must be inventoried and listed by
Which of the following is a PRIMARY benefit of using a formalized security testing report format and structure?
Intellectual property rights are PRIMARY concerned with which of the following?
A continuous information security monitoring program can BEST reduce risk through which of the following?