You are the Network Administrator for a bank. In addition to the usual security issues, you are concerned that your customers could be the victim of phishing attacks that use fake bank Web sites.
Which of the following would protect against this?
Against which of the following does SSH provide protection?
Each correct answer represents a complete solution. Choose two.
Maria works as a Risk Analysis Manager for Gentech Inc. She starts a new IT project. Which of the following phases of her project development process is most suitable for including risk analysis?
You are configuring IPS (Intrusion Prevention System) on a Cisco IOS router. The IPS Policy Wizard window opens when you confirm the SDEE messages. Which of the following tasks can you perform using the IPS Policy Wizard window?
Each correct answer represents a complete solution. Choose all that apply.
A war dialer is a tool that is used to scan thousands of telephone numbers to detect vulnerable modems. It provides an attacker unauthorized access to a computer. Which of the following tools can an attacker use to perform war dialing?
Each correct answer represents a complete solution. Choose all that apply.
You are responsible for network security at a defense contractor. You are very concerned about sensitive data not getting out of your network. You have specific concerns about employees or contractors sending out files via FTP, or even spyware sending out data. You have blocked and monitored ports (as many as you can) on your firewall, and of course, run an anti spyware package.
Which of the following is another step you should take in preventing sensitive data from being sent out of your network without authorization?
A project team member has just identified a new project risk. The risk event is determined to have significant impact but a low probability in the project. Should the risk event happen it'll cause the project to be delayed by three weeks, which will cause new risk in the project. What should the project manager do with the risk event?
You work as a technician for Tech Perfect Inc. A user named Rick calls you. He wants to configure a wireless network for his small office. He wants to adopt a wireless technology that supports high data transfer speed. Which of the following technologies will you suggest?
In which of the following social engineering attacks does an attacker first damage any part of the target's equipment and then advertise himself as an authorized person who can help fix the problem.
Rick is the project manager for TTM project. He is in the process of procuring services from vendors. He makes a contract with a vendor in which he precisely specify the services to be procured, and any changes to the procurement specification will increase the costs to the buyer. Which type of contract is this?
Which of the following types of cryptography algorithms uses the MD series of encryption algorithms?
Which of the following RAID standards distributes data across multiple disks in a way that gives improved speed at any given instant?
You are the project manager of a large project that will span several time zones. You'll be utilizing project team members from across several departments. Project team members won't be working on the project full-time and will join and leave the project based on assignments in the project schedule.
What project management plan can you create to help you manage when project times will be brought onto and released from the project team?
This type of virus infects programs that can execute and load into memory to perform predefined steps for infecting systems. It infects files with the extensions .EXE, .COM, .BIN, and .SYS. As it can replicate or destroy these types of files, the operating system becomes corrupted and needs reinstallation. This type of virus is known as __________.
Which of the following terms describes the statement given below?
"It is a cryptographic protocol that provides security and data integrity for communications over networks such as the Internet."
Which of the following is a computer worm that caused a denial of service on some Internet hosts and dramatically slowed down general Internet traffic?
You work as a professional Ethical Hacker. You are assigned a project to test the security of www.weare-secure.com. You are working on the Windows Server 2003 operating system. You suspect that your friend has installed the keyghost keylogger onto your computer. Which of the following countermeasures would you employ in such a situation?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following terms describes the statement given below?
"It refers to a range of skills, tools, and techniques used to manage time when accomplishing specific tasks, projects, and goals. This set encompasses a wide scope of activities, and these include planning, allocating, setting goals, delegation, analysis of time spent, monitoring, organizing, scheduling, and prioritizing."
John used to work as a Network Administrator for We-are-secure Inc. Now he has resigned from the company for personal reasons. He wants to send out some secret information of the company. To do so, he takes an image file and simply uses a tool image hide and embeds the secret file within an image file of the famous actress, Jennifer Lopez, and sends it to his Yahoo mail id. Since he is using the image file to send the data, the mail server of his company is unable to filter this mail. Which of the following techniques is he performing to accomplish his task?
Which of the following is used to communicate with an authentication server commonly used in UNIX networks?
Nancy is the project manager for a new construction project. There are several occupational safety codes, which must be included in the project requirements. These requirements are nonnegotiable and the customer must pay for the safety measures, inspections, and training for the project team. What term best describes the cost associated with these safety requirements?
A honey pot is a computer trap that is used to attract potential intruders or attackers. Which of the following are some advantages of honey pots?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is NOT a principle and practice of the 'Minimize the number of highconsequence targets' principle?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He writes the following snort rule:
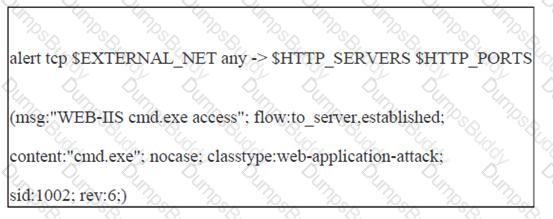
This rule can help him protect the We-are-secure server from the __________.
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He successfully performs a brute force attack on the We-are-secure server. Now, he suggests some countermeasures to avoid such brute force attacks on the We-are-secure server. Which of the following are countermeasures against a brute force attack?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following contains information that is read by a Web application whenever a user visits a site?
Which of the following uses a variable-length Initialization Vector (IV), where the encrypted data begins?
Which of the following is an authentication protocol used by clients to dial-in to computers running Windows 2000 Server?
Which of the following are used as a cost estimating technique during the project planning stage?
Each correct answer represents a complete solution. Choose three.
Which of the following generates MD5 hashes to check the MD5 value for each file processed and compares it with other MD5 strings?
Fill in the blank with the appropriate type of router.
A _________ router performs packet-filtering and is used as a firewall.
Which of the following is a computer file used in an operating system to map hostnames to IP addresses?
In which of the following does a project manager assign certain points towards various categories to judge the vendors?
Which type of repudiation states that the creator of the message denies ever creating the message even after creating it?
Which of the following is the best encryption algorithm to encrypt and decrypt messages?
Which of the following malware spread through the Internet and caused a large DoS attack in
1988?
Which of the following viruses masks itself from applications or utilities to hide itself by detection of anti-virus software?
You have been hired as a project manager for a project. The initial project planning predicts a benefitcost ratio (BCR) of the project as 3.5. What does this figure mean?
You work as a Consumer Support Technician for ABC Inc. The company provides troubleshooting support to users. You are troubleshooting a computer of a user who is working on Windows Vista.
He reports that his sensitive data is being accessed by someone because of security vulnerability in the component of Windows Vista. Which of the following features of Windows Security Center will you configure to save the user's data?
Complete the following sentence: Quality control is a(n)_______________ process while quality assurance is a(n)________________ process.
Roberta is the project manager of the KJL Project for her company. She is creating a chart that will help categorize the problems discovered during the quality control inspection process. She wants to create a chart where she can categorize the number of instances of problems and rank the problems based on frequency. Which chart should Roberta create?
You are concerned about rogue wireless access points being connected to your network. What is the best way to detect and prevent these?
Which of the following are the countermeasures against a man-in-the-middle attack?
Each correct answer represents a complete solution. Choose all that apply.
IP blocking is a technique that prevents the connection between a server/website and certain IP addresses or ranges of addresses. Which of the following tools use this technique?
Each correct answer represents a complete solution. Choose all that apply.
You are working on your computer system with Linux Operating system. After working for a few hours, the hard disk goes to the inactive state (sleep). You try to restart the system and check the power circuits. You later discover that the hard disk has crashed. Which of the following precaution methods should you apply to keep your computer safe from such issues?
You configure a wireless router at your home. To secure your home Wireless LAN (WLAN), you implement WEP. Now you want to connect your client computer to the WLAN. Which of the following is the required information that you will need to configure the client computer?
Each correct answer represents a part of the solution. Choose two.
You work as a Network Administrator for Marioxnet Inc. You have the responsibility of handling two routers with BGP protocol for the enterprise's network. One of the two routers gets flooded with an unexpected number of data packets, while the other router starves with no packets reaching it. Which of the following attacks can be a potential cause of this?
You have just set up a wireless network for customers at a coffee shop. Which of the following are good security measures to implement?
Each correct answer represents a complete solution. Choose two.
Which of the following security policies will you implement to keep safe your data when you connect your Laptop to the office network over IEEE 802.11 WLANs?
Each correct answer represents a complete solution. Choose two.
The MBR of a hard disk is a collection of boot records that contain disk information such as disk architecture, cluster size, and so on. The main work of the MBR is to locate and run necessary operating system files that are required to run a hard disk. In the context of the operating system, MBR is also known as the boot loader. Which of the following viruses can infect the MBR of a hard disk?
Each correct answer represents a complete solution. Choose two.
You and your project team have identified the project risks and now are analyzing the probability and impact of the risks. What type of analysis of the risks provides a quick and high-level review of each identified risk event?
Which type of virus is able to alter its own code to avoid being detected by anti-virus software?
Which of the following are the benefits of information classification for an organization?
Each correct answer represents a complete solution. Choose two.
Which of the following types of security will be the cause of concern if the server has been stolen from the organization's premises?
Which of the following statements are true about TCP/IP model?
Each correct answer represents a complete solution. Choose all that apply.
You work as a technician for Secure Net Inc. You receive an e-mail from your software vendor.
The e-mail contains information about a critical fix that needs to be installed on your computer. It further states that if this patch is not installed right away, your system will crash and you will lose all your data. Now they require your maintenance account password.
Which of the following types of security attacks do you think it is?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows:
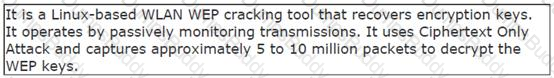
Which of the following tools is John using to crack the wireless encryption keys?
You are the project manager of a Web development project. You want to get information about your competitors by hacking into their computers. You and the project team determine should the hacking attack not be performed anonymously, you will be traced. Hence, you hire a professional hacker to work on the project. This is an example of what type of risk response?
You are an Administrator for a network at an investment bank. You are concerned about individuals breeching your network and being able to steal data before you can detect their presence and shut down their access. Which of the following is the best way to address this issue?
Mark works as a Network Administrator for Infonet Inc. The company has a Windows 2000 Active Directory domain-based network. The domain contains one hundred Windows XP Professional client computers. Mark is deploying an 802.11 wireless LAN on the network. The wireless LAN will use Wired Equivalent Privacy (WEP) for all the connections. According to the company's security policy, the client computers must be able to automatically connect to the wireless LAN. However, the unauthorized computers must not be allowed to connect to the wireless LAN and view the wireless network. Mark wants to configure all the wireless access points and client computers to act in accordance with the company's security policy. What will he do to accomplish this?
Each correct answer represents a part of the solution. Choose three.
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He copies the whole structure of the We-are-secure Web site to the local disk and obtains all the files on the Web site. Which of the following techniques is he using to accomplish his task?
Which interface does an IPS sensor use to communicate with a security appliance for management purposes?
You work as a Network Administrator for Tech Perfect Inc. The company has a Linux-based network. You have configured a VPN server for remote users to connect to the company's network. Which of the following encryption types will Linux use?
Which of the following processes is described in the statement below?
"It is a process of developing an approximation of the costs of the resources needed to complete project activities."
Which of the following cryptographic system services ensures that information will not be disclosed to any unauthorized person on a local network?
Maria works as a professional Ethical Hacker. She has been assigned the project of testing the security of www.gentech.com. She is using dumpster diving to gather information about Gentech Inc. In which of the following steps of malicious hacking does dumpster diving come under?
Which of the following are types of social engineering attacks?
Each correct answer represents a complete solution. Choose two.
Which of the following tools is based on Linux and used to carry out the Penetration Testing?
Which of the following layers of TCP/IP model is used to move packets between the Internet Layer interfaces of two different hosts on the same link?
Which of the following encryption algorithms is applied in the PGP encryption system?
The Project Procurement Management knowledge area focuses on which of the following processes?
Each correct answer represents a complete solution. Choose two.
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He wants to test the effect of a virus on the We-are-secure server. He injects the virus on the server and, as a result, the server becomes infected with the virus even though an established antivirus program is installed on the server. Which of the following do you think are the reasons why the antivirus installed on the server did not detect the virus injected by John?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following are the goals of risk management?
Each correct answer represents a complete solution. Choose three.
You are responsible for security on your network. One particular concern is the theft of sensitive data. You want to make sure that end users do not (purposefully or accidentally) take data off the premises. Which of the following should you be concerned about?
Each correct answer represents a complete solution. Choose all that apply.