In PKI, when someone wants to verify that the certificate is valid, what do they use to decrypt the signature?
What advantage would an attacker have in attacking a web server using the SSL protocol?
A web application requires multifactor authentication when a user accesses the application from a home office but does not require this when the user is in the office. What access control model is this describing?
Users at the Marketing department are receiving their new Windows XP Professional workstations. They will need to maintain local work files in the first logical volume, and will use a second volume for the information shared between the area group. Which is the best file system design for these workstations?
You have set up a local area network for your company. Your firewall separates your network into several sections: a DMZ with semi-public servers (web, dns, email) and an intranet with private servers. A penetration tester gains access to both sections and installs sniffers in each. He is able to capture network traffic for all the devices in the private section but only for one device (the device with the sniffer) in the DMZ. What can be inferred about the design of the system?
Which of the following are the types of access controls?
Each correct answer represents a complete solution. Choose three.
An organization keeps its intellectual property in a database. Protection of the data is assigned to one system administrator who marks the data, and monitors for this intellectual property leaving the network. Which defense-In-depth principle does this describe?
What type of attack can be performed against a wireless network using the tool Kismet?
A system administrator sees the following URL in the webserver logs:
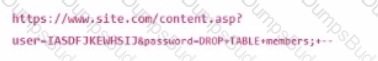
Which action will mitigate against this attack?
Use PowerShell ISE to
examineC:\Windows\security\templates\WorkstationSecureTemplate.inf. Which setting is configured in the template?


Which of the following applications would be BEST implemented with UDP instead of TCP?
Which of the following BEST describes the two job functions of Microsoft Baseline Security Analyzer (MBSA)?
What is the discipline of establishing a known baseline and managing that condition known as?
Which of the following statements about Hypertext Transfer Protocol Secure (HTTPS) are true? Each correct answer represents a complete solution. Choose two.
Which of the following monitors program activities and modifies malicious activities on a system?
What are the two actions the receiver of a PGP email message can perform that allows establishment of trust between sender and receiver?
You are doing some analysis of malware on a Unix computer in a closed test network. The IP address of the computer is 192.168.1.120. From a packet capture, you see the malware is attempting to do a DNS query for a server called iamabadserver.com so that it can connect to it. There is no DNS server on the test network to do name resolution. You have another computer, whose IP is 192.168.1.115, available on the test network that you would like for the malware connect to it instead. How do you get the malware to connect to that computer on the test network?
You work as an Administrator for McRoberts Inc. The company has a Linux-based network. You are logged in as a non-root user on your client computer. You want to delete all files from the /garbage directory. You want that the command you will use should prompt for the root user password. Which of the following commands will you use to accomplish the task?
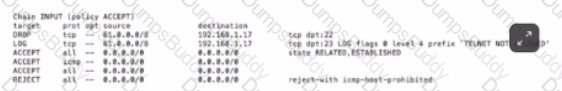
Based on the iptables output below, which type of endpoint security protection has host 192.168.1.17 implemented for incoming traffic on TCP port 22 (SSH) and TCP port 23 (telnet)?
What does PowerShell remoting use to authenticate to another host in a domain environment?
Which of the following proxy servers provides administrative controls over the content?
Your software developer comes to you with an application that controls a user device. The application monitors its own behavior and that of the device and creates log files. The log files are expected to grow steadily and rapidly. Your developer currently has the log files stored in the /bin folder with the application binary. Where would you suggest that the developer store the log files?
What is the command-line tool for Windows XP and later that allows administrators the ability to get or set configuration data for a very wide variety of computer and user account settings?
What is the function of the TTL (Time to Live) field in IPv4 and the Hop Limit field in IPv6 In an IP Packet header?
What is the first thing that should be done during the containment step of incident handling?
Which of the following would be used to explicitly deny the traffic from a foreign IP address scanning the EC2 Instances in a VPC?
You work as a Network Administrator for Secure World Inc. The company has a Linux-based network. You want to run a command with the changed root directory. Which of the following commands will you use?
In an Active Directory domain, which is the preferred method of keeping host computers patched?
Which of the following statements about Network Address Translation (NAT) are true? Each correct answer represents a complete solution. Choose two.
Which of the following are examples of Issue-Specific policies all organizations should address?
Which of the following is a valid password for a system with the default "Password must meet complexity requirements" setting enabled as part of the GPO Password policy requirements?
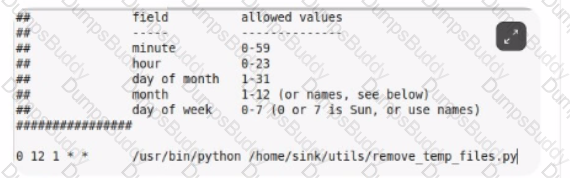
Analyze the file below. When will the program /home/sink/utils/remove temp hies.py run?
To update from a Windows Server Update Services (WSUS) server, users of the machine must have what rights, If any?
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we- are-secure.com. He installs a rootkit on the Linux server of the We-are-secure network. Which of the following statements are true about rootkits?
Each correct answer represents a complete solution. Choose all that apply.
If Linux server software is a requirement in your production environment which of the following should you NOT utilize?
Analyze the following screenshot. What conclusion can be drawn about the user account shown?

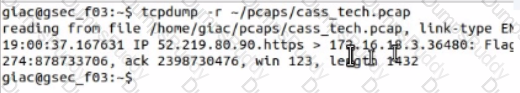
Open the MATE terminal and use the tcpdump program to read - /pcaps /cass tech.pcap.
What is the source port number?

Which of the four basic transformations in the AES algorithm involves the leftward circular movement of state data?
When using Pretty Good Privacy (PGP) to digitally sign a message, the signature is created in a two-step process. First, the message to be signed is submitted to PGP's cryptographic hash algorithm. What is one of the hash algorithms used by PGP for this process?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He wants to change the modified date and time of the file private.txt to 11 Nov 2009 02:59:58 am. Which of the following commands will John use to accomplish his task?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following are used to suppress gasoline and oil fires? Each correct answer represents a complete solution. Choose three.
Which of the following access control principles helps prevent collusion and detect abuse of access?
Use Wireshark to analyze Desktop;PCAP FILES/charile.pcap
What is the destination IP address in packet #3?

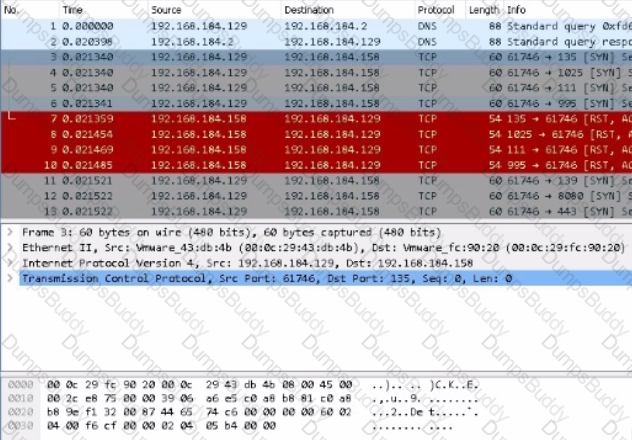
Which field in the IPv6 header is used for QoS. or specifying the priority of the packet?
Which of the following is required to be backed up on a domain controller to recover Active Directory?
You are going to upgrade your hard disk's file system from FAT to NTFS. What are the major advantages of the NTFS file system over FAT16 and FAT32 file systems?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is an advantage of a Host Intrusion Detection System (HIDS) versus a Network Intrusion Detection System (NIDS)?
You work as a Network Administrator for McNeil Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest domain-based network. The company's management has decided to provide laptops to its sales team members. These laptops are equipped with smart card readers. The laptops will be configured as wireless network clients. You are required to accomplish the following tasks:
The wireless network communication should be secured.
The laptop users should be able to use smart cards for getting authenticated. In order to accomplish the tasks, you take the following steps:
Configure 802.1x and WEP for the wireless connections. Configure the PEAP-MS-CHAP v2 protocol for authentication. What will happen after you have taken these steps?
Which of the following works at the network layer and hides the local area network IP address and topology?
Which Defense-in-Depth principle starts with an awareness of the value of each section of information within an organization?
Use sudo to launch Snort with the, /etc /snort /snort.conf file In full mode to generate alerts based on incoming traffic to echo. What is the source IP address of the traffic triggering an alert with a destination port of 156?
Note: Snort Is configured to exit after It evaluates 50 packets.

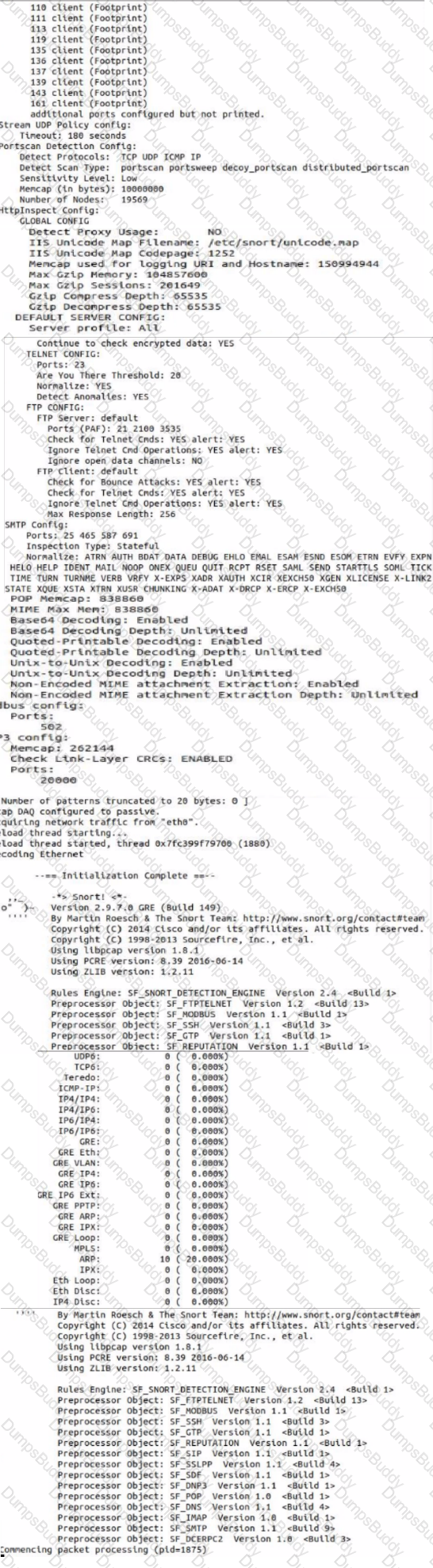
Which of the following choices accurately describes how PGP works when encrypting email?
You work as a Network Administrator for McNeil Inc. The company has a Linux-based network. David, a Sales Manager, wants to know the name of the shell that he is currently using. Which of the following commands will he use to accomplish the task?
There is not universal agreement on the names of the layers in the TCP/IP networking model. Which of the following is one of the functions of the bottom layer which is sometimes called the Network Access or Link Layer?
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network. You have configured a firewall on the network. A filter has been applied to block all the ports. You want to enable sending and receiving of emails on the network. Which of the following ports will you open?
Each correct answer represents a complete solution. Choose two.
An organization monitors the hard disks of its employees' computers from time to time. Which policy does this pertain to?
What would the following IP tables command do?
IP tables -I INPUT -s 99.23.45.1/32 -j DROP
Which of the following protocols are used to provide secure communication between a client and a server over the Internet?
Each correct answer represents a part of the solution. Choose two.
When are Group Policy Objects (GPOs) NOT applied automatically to workstations?
You are reviewing a packet capture file from your network intrusion detection system. In the packet stream, you come across a long series of "no operation" (NOP) commands. In addition to the NOP commands, there appears to be a malicious payload. Of the following, which is the most appropriate preventative measure for this type of attack?
Which of the following utilities can be used to manage the Windows Firewall (WF) from the command line?
What is the key difference between Electronic Codebook mode and other block cipher modes like Cipher Block Chaining, Cipher-Feedback and Output-Feedback?
What Windows log should be checked to troubleshoot a Windows service that is falling to start?
Use Hashcat to crack a local shadow file. What Is the password for the user account AGainsboro?
Hints
• The shadow file (shadow) and Hashcat wordlist (gsecwordlist.txt) are located in the directory /home /giac /PasswordHashing/
• Run Hashcat in straight mode (flag -a 0) to crack the MD5 hashes (flag -m 500) In the shadow file.
• Use the hash values from the Hashcat output file and the shadow file to match the cracked password with the user name.
• If required, a backup copy of the original files can be found in the shadowbackup directory.

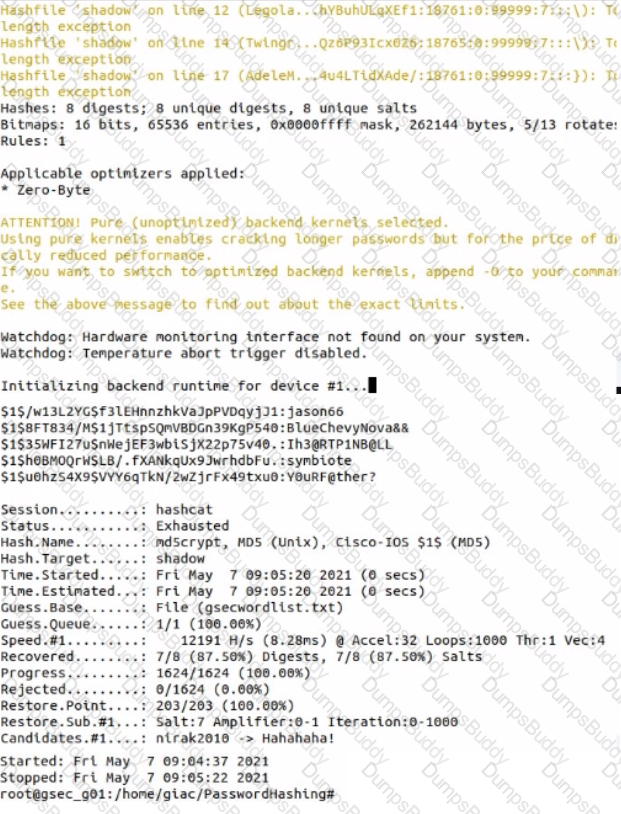
What is needed for any of the four options for Azure AD multi-factor user authentication?
Which of the following is a term that refers to unsolicited e-mails sent to a large number of e-mail users?
Which of the following processes Is used to prove a user Is who they claim to be based upon something they know, have, are, and/or their physical location?
What would the file permission example "rwsr-sr-x" translate to in absolute mode?
You work as a Network Administrator for McNeil Inc. You are installing an application. You want to view the log file whenever a new entry is added to the /var/log/messages log file. Which of the following commands will you use to accomplish this?
Which common firewall feature can be utilized to generate a forensic trail of evidence and to identify attack trends against your network?
What is the purpose of notifying stakeholders prior to a scheduled vulnerability scan?
You are examining a packet capture session in Wire shark and see the packet shown in the accompanying image. Based on what you see, what is the appropriate protection against this type of attempted attack?
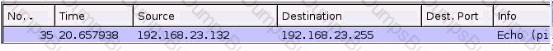
A Network Engineer is charged with maintaining and protecting a network with a high availability requirement. In addition to other defenses, they have chosen to implement a NIPS. How should the NIPS failure conditions be configured to ensure availability if the NIPS is installed in front of the Firewall that protects the DMZ?
A Windows administrator wants to automate local and remote management tasks in Active Directory. Which tool is most appropriate for this?
Which AWS service integrates with the Amazon API Gateway to provision and renew TLS encryption needs for data in transit?
An attacker is able to trick an IDS into ignoring malicious traffic through obfuscation of the packet payload. What type of IDS error has occurred?
Which of the following statements about DMZ are true?
Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for World Perfect Inc. The company has a Linux-based network. You have configured a Linux Web server on the network. A user complains that the Web server is not responding to requests. The process list on the server shows multiple instances of the HTTPD process. You are required to stop the Web service. Which of the following commands will you use to resolve the issue?
A database is accessed through an application that users must authenticate with, on a host that only accepts connections from a subnet where the business unit that uses the data is located. What defense strategy is this?
In addition to securing the operating system of production honey pot hosts, what is recommended to prevent the honey pots from assuming the identities of production systems that could result in the denial of service for legitimate users?
Who is responsible for deciding the appropriate classification level for data within an organization?
What requirement must an administrator remember when utilizing Security Configuration and Analysis (SCA) to apply security templates to Windows systems?
You are the security director for an off-shore banking site. From a business perspective, what is a major factor to consider before running your new vulnerability scanner against the company's business systems?
Which access control mechanism requires a high amount of maintenance since all data must be classified, and all users granted appropriate clearance?
When Net Stumbler is initially launched, it sends wireless frames to which of the following addresses?