Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate a multimedia enabled mobile phone, which is suspected to be used in a cyber crime. Adam uses a tool, with the help of which he can recover deleted text messages, photos, and call logs of the mobile phone. Which of the following tools is Adam using?
GSM uses either A5/1 or A5/2 stream cipher for ensuring over-the-air voice privacy. Which of the following cryptographic attacks can be used to break both ciphers?
Network mapping provides a security testing team with a blueprint of the organization. Which of the following steps is NOT a part of manual network mapping?
Which of the following techniques are NOT used to perform active OS fingerprinting?
Each correct answer represents a complete solution. Choose all that apply.
In which of the following attacking methods does an attacker distribute incorrect IP address?
You work as an IT Technician for uCertify Inc. You have to take security measures for the wireless network of the company. You want to prevent other computers from accessing the company's wireless network. On the basis of the hardware address, which of the following will you use as the best possible method to accomplish the task?
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com network. Now, when you have finished your penetration testing, you find that the weare- secure.com server is highly vulnerable to SNMP enumeration. You advise the we-are-secure Inc. to turn off SNMP; however, this is not possible as the company is using various SNMP services on its remote nodes. What other step can you suggest to remove SNMP vulnerability?
Each correct answer represents a complete solution. Choose two.
You want to retrieve password files (stored in the Web server's index directory) from various Web sites. Which of the following tools can you use to accomplish the task?
You work as an IT Technician for uCertify Inc. You have to take security measures for the wireless network of the company. You want to prevent other computers from accessing the company's wireless network. On the basis of the hardware address, which of the following will you use as the best possible method to accomplish the task?
How can a non-privileged user on a Unix system determine if shadow passwords are being used?
You are done pen testing a Windows system and need to clean up some of the changes you have made. You created an account ‘pentester’ on the system, what command would you use to delete that account?
Approximately how many packets are usually required to conduct a successful FMS attack onWEP?
Which of the following describes the direction of the challenges issued when establishing a wireless (IEEE 802.11) connection?
You've been contracted by the owner of a secure facility to try and break into their office in the middle of the night. Your client requested photographs of any sensitive information found as proof of your accomplishments. The job you've been hired to perform is an example of what practice?
What is the MOST important document to obtain before beginning any penetration testing?
Which of the following file transfer programs will automatically convert end-of line characters between different platforms when placed in ASCII Mode?
Which of the following is the number of bits of encryption that 64-bit Wired Equivalent Privacy (WEP) effectively provides?
Analyze the command output below, what action is being performed by the tester?
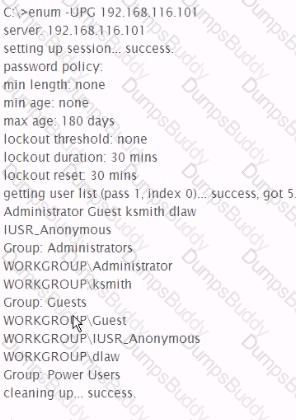
Which Metasploit payload includes simple upload and download functionality for moving files to and from compromised systems?
Analyze the command output below. What action is being performed by the tester?
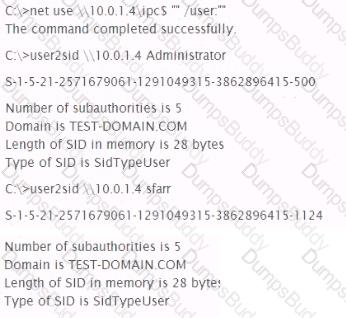
You have been contracted to map me network and try to compromise the servers for a client. Which of the following would be an example of scope creep' with respect to this penetration testing project?
A penetration tester obtains telnet access to a target machine using a captured credential. While trying to transfer her exploit to the target machine, the network intrusion detection systems keeps detecting her exploit and terminating her connection. Which of the following actions will help the penetration tester transfer an exploit and compile it in the target system?
Which of the following penetration testing phases involves gathering data from whois, DNS, and network scanning, which helps in mapping a target network and provides valuable information regarding the operating system and applications running on the systems?
Which of the following tools is spyware that makes Windows clients send their passwords as clear text?
Which of the following tools is used to verify the network structure packets and confirm that the packets are constructed according to specification?
You work as a Network Penetration tester in the Secure Inc. Your company takes the projects to test the security of various companies. Recently, Secure Inc. has assigned you a project to test the security of a Web site. You go to the Web site login page and you run the following SQL query:
SELECT email, passwd, login_id, full_name
FROM members
WHERE email = 'attacker@somehwere.com'; DROP TABLE members; --'
What task will the above SQL query perform?
You have just set up a wireless network for customers at a coffee shop. Which of the following are good security measures to implement?
Each correct answer represents a complete solution. Choose two.
You want to use a Windows-based GUI tool which can perform MITM attacks, along with sniffing and ARP poisoning. Which of the following tools will you use?
Which of the following Web authentication techniques uses a single sign-on scheme?
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com Website. The we-are-secure.com Web server is using Linux operating system. When you port scanned the we-are-secure.com Web server, you got that TCP port 23, 25, and 53 are open. When you tried to telnet to port 23, you got a blank screen in response. When you tried to type the dir, copy, date, del, etc. commands you got only blank spaces or underscores symbols on the screen. What may be the reason of such unwanted situation?
Write the appropriate attack name to fill in the blank.
In a _____________ DoS attack, the attacker sends a spoofed TCP SYN packet in which the IP address of the target is filled in both the source and destination fields.
Which of the following Web attacks is performed by manipulating codes of programming languages such as SQL, Perl, Java present in the Web pages?
Ryan wants to create an ad hoc wireless network so that he can share some important files with another employee of his company. Which of the following wireless security protocols should he choose for setting up an ad hoc wireless network?
Each correct answer represents a part of the solution. Choose two.
Fill in the blank with the appropriate tool.
____scans IP networks for NetBIOS name information and works in the same manner as nbtstat, but it operates on a range of addresses instead of just one.
You are concerned about war driving bringing hackers attention to your wireless network. What is the most basic step you can take to mitigate this risk?
Which of the following tools can be used to perform Windows password cracking, Windows enumeration, and VoIP session sniffing?
You want to perform an active session hijack against Secure Inc. You have found a target that allows Telnet session. You have also searched an active session due to the high level of traffic on the network. What should you do next?
You want to search Microsoft Outlook Web Access Default Portal using Google search on the
Internet so that you can perform the brute force attack and get unauthorized access. What search string will you use to accomplish the task?
In which of the following attacks does the attacker overload the CAM table of the switch?
You want that some of your Web pages should not be crawled. Which one of the following options will you use to accomplish the task?
You want to connect to your friend's computer and run a Trojan on it. Which of the following tools will you use to accomplish the task?
Which of the following standards is used in wireless local area networks (WLANs)?