Which of the following refers to a condition in which a hacker sends a bunch of packets that leave TCP ports half open?
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases.
The email header of the suspicious email is given below:
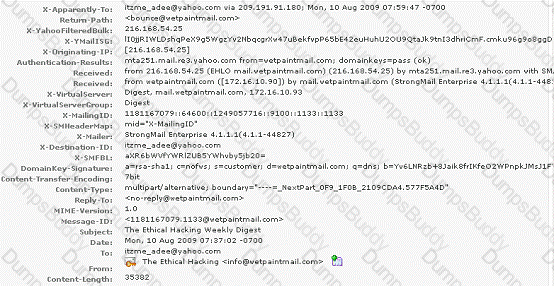
What is the IP address of the sender of this email?
Which of the following are the levels of public or commercial data classification system?
Each correct answer represents a complete solution. Choose all that apply.
Peter is a merchant. He uses symmetric encryption to send confidential messages to different users of his Web site. Which of the following is the other name for asymmetric encryption?
In a complex network, Router transfers data packets by observing some form of parameters or metrics provided in the routing table. Which of the following metrics is NOT included in the routing table?
How should you configure USSOWA1 and USSTIME1 to allow secure access for remote employees?
(Click the Exhibit button on the toolbar to see the case study.)
Each correct answer represents a complete solution. Choose three.
Which of the following are the types of access controls?
Each correct answer represents a complete solution. Choose three.
You are the Administrator for a corporate network. You are concerned about denial of service attacks. Which of the following measures would be most helpful in defending against a Denial-of-Service (DoS) attack?
Web applications play a vital role in deploying different databases with user accessibility on the Internet. Which of the following allows an attacker to get unauthorized access to the database of a Web application by sending (attacking) user-supplied data to an interpreter as part of a command or query?
Which of the following is the process of making additional copies of data so that they may be used to restore the original after a data loss event?
Shoulder surfing is a type of in-person attack in which the attacker gathers information about the premises of an organization. This attack is often performed by looking surreptitiously at the keyboard of an employee's computer while he is typing in his password at any access point such as a terminal/Web site. Which of the following is violated in a shoulder surfing attack?
Which of the following types of firewall functions by creating two different communications, one between the client and the firewall, and the other between the firewall and the end server?
You work as a Network Administrator for McRoberts Inc. You are required to upgrade a client computer on the company's network to Windows Vista Ultimate. During installation, the computer stops responding, and the screen does not change. What is the most likely cause?
You are responsible for virus protection for a large college campus. You are very concerned that your antivirus solution must be able to capture the latest virus threats. What sort of virus protection should you implement?
Which of the following are parts of applying professional knowledge? Each correct answer represents a complete solution. Choose all that apply.
John is a merchant. He has set up a LAN in his office. Some important files are deleted as a result of virus attack. John wants to ensure that it does not happen again. What will he use to protect his data from virus?
You work as the project manager for Bluewell Inc. Your project has several risks that will affect several stakeholder requirements. Which project management plan will define who will be available to share information on the project risks?
Fred is the project manager for the TCC Company. His company has an internal policy that states each year they will provide free services to a nonprofit organization. Therefore, the company and its employees are not allowed to charge or receive money or gifts from the nonprofit organization they choose to provide free services. This year, the TCC Company offers to provide project management services to the children's hospital for a marketing campaign to raise money. Due to the TCC Company's project management services, the nonprofit agency exceeded previous years fund raising efforts. To show appreciation the nonprofit organization offered to reimburse the project manager for his travel expenses. Which of the following best describes how the project manager should handle the situation?
Which of the following are the benefits of information classification for an organization?
Which of the following technologies is used to detect unauthorized attempts to access and manipulate computer systems locally or through the Internet or an intranet?
You work as the Security Administrator for Prodotxiss Inc. You want to ensure the security of your Wi-Fi enterprise network against the wireless snooping attacks. Which of the following measures will you take over the site network devices of the network?
You are the Network Administrator for a software development company. Your company creates various utilities and tools. You have noticed that some of the files your company creates are getting deleted from systems. When one is deleted, it seems to be deleted from all the computers on your network. Where would you first look to try and diagnose this problem?
The Intrusion Detection System (IDS) instructs the firewall to reject any request from a particular IP address if the network is repeatedly attacked from this address. What is this action known as?
Which of the following Windows Security Center features is implemented to give a logical layer protection between computers in a networked environment?
You work as an Application Developer for uCertify Inc. The company uses Visual Studio .NET Framework 3.5 as its application development platform. You are working on a WCF service. You have decided to implement transport level security. Which of the following security protocols will you use?
Which of the following protocols is used to prevent switching loops in networks with redundant switched paths?
Which of the following Web attacks is performed by manipulating codes of programming languages such as SQL, Perl, Java present in the Web pages?
Which of the following protocols provides secured transaction of data between two computers?
You are configuring the Terminal service. What Protocols are required with Terminal services? (Click the Exhibit button on the toolbar to see the case study.) Each correct answer represents a part of the solution. Choose two.
The MBR of a hard disk is a collection of boot records that contain disk information such as disk architecture, cluster size, and so on. The main work of the MBR is to locate and run necessary operating system files that are required to run a hard disk. In the context of the operating system, MBR is also known as the boot loader. Which of the following viruses can infect the MBR of a hard disk?
Each correct answer represents a complete solution. Choose two.
Based on the case study, to implement more security, which of the following additional technologies should you implement for laptop computers?
(Click the Exhibit button on the toolbar to see the case study.)
Each correct answer represents a complete solution. Choose two.
Which of the following statements are TRUE regarding asymmetric encryption and symmetric encryption? Each correct answer represents a complete solution. Choose all that apply.
You are an Incident manager in Orangesect.Inc. You have been tasked to set up a new extension of your enterprise. The networking, to be done in the new extension, requires different types of cables and an appropriate policy that will be decided by you. Which of the following stages in the Incident handling process involves your decision making?
The security of a computer against the unauthorized usage largely depends upon the efficiency of the applied access control method. Which of the following statements are true about a computer access control method?
Each correct answer represents a complete solution. Choose all that apply.
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He wants to test the effect of a virus on the We-are-secure server. He injects the virus on the server and, as a result, the server becomes infected with the virus even though an established antivirus program is installed on the server. Which of the following do you think are the reasons why the antivirus installed on the server did not detect the virus injected by John?
Each correct answer represents a complete solution. Choose all that apply.
Fill in the blank with the appropriate layer name.
The Network layer of the OSI model corresponds to the______ layer of the TCP/IP model.
You work as a security manager in Mariotiss Inc. Your enterprise has been facing network and software security threats since a few months. You want to renew your current security policies and management to enhance the safety of your information systems. Which of the following is the best practice to initiate the renewal process from the lowest level with the least managerial effort?
Which of the following cryptographic algorithm uses public key and private key to encrypt or decrypt data?