If an attacker wanted to dump hashes or run wmic commands on a target machine, which of the following tools would he use?
Which of the following statements is appropriate in an incident response report?
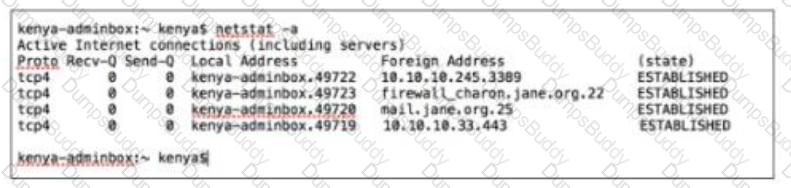
Kenya is a system administrator for SANS. Per the recommendations of the CIS Controls she has a dedicated host (kenya- adminbox / 10.10.10.10) for any administrative tasks. She logs into the dedicated host with her domain admin credentials. Which of the following connections should not exist from kenya-adminbox?
What tool creates visual network topology output and results that can be analyzed by Ndiff to determine if a service or network asset has changed?
Which of the following actions will assist an organization specifically with implementing web application software security?
An administrator looking at a web application’s log file found login attempts by the same host over several seconds. Each user ID was attempted with three different passwords. The event took place over 5 seconds.
What is the most likely source of this event?
An organization is implementing an application software security control their custom-written code that provides web—based database access to sales partners. Which action will help mitigate the risk of the application being compromised?