Which of the following states that a user should never be given more privileges than are required to carry out a task?
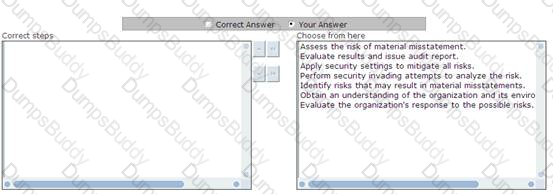
Choose and reorder the appropriate steps that you will take to perform auditing.
You work as a Security Administrator for uCertify Inc. You need to make a documentation to provide ongoing education and awareness training of disciplinary actions of your company. What are the primary reasons to create this documentation?
Each correct answer represents a complete solution. Choose all that apply.
Mark works as a Security Administrator for uCertify Inc. For the last few days, he is getting an error message, i.e., 'Remove the Boot.ini file because it is harmful for operating system'. When Mark reads about the Boot.ini file, he finds that it is a system file that is used to load the operating system on a computer. Which of the following types of virus has attacked Mark's computer?
Cigital Risk Management Method was developed by Gary McGraw of Cigital and John Viega of Stonewall Software, and it defines software security risk management process. Choose and re-order the risk management steps that are included in this method.
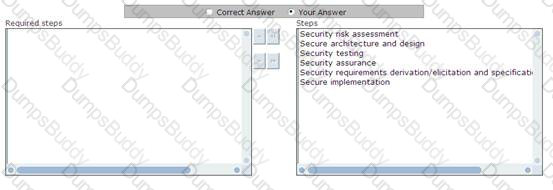
The stronger points of CRAMM assist prioritization by providing a countermeasure with high priority if some conditions are met. Which of the following are these conditions?
Each correct answer represents a complete solution. Choose all that apply.
The Information Security Officer (ISO) of Blue Well Inc. wants to have a list of security measures put together. What should be done before security measures are selected by the Information Security Officer?
Mark works as a Network Security Administrator for uCertify Inc. An employee of the organization comes to Mark and tells him that a few months ago, the employee had filled an online bank form due to some account related work. Today, when again visiting the site, the employee finds that some of his personal information is still being displayed in the webpage. Which of the following types of cookies should be disabled by Mark to resolve the issue?
Which of the following are the things included by sensitive system isolation?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Security Administrator for uCertify Inc. You have been assigned the task to verify the identity of the employees recruited in your organization. Which of the following components of security deals with an employee's verification in the organization?
You work as an Information Security Manager for uCertify Inc. You are working on asset management. You need to differentiate various assets of your organization. Which of the following are information assets?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following are the two methods that are commonly used for applying mandatory access control?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tasks are performed by Information Security Management?
Each correct answer represents a complete solution. Choose all that apply.
You work as the Network Administrator for a defense contractor. Your company works with sensitive materials and all IT personnel have at least a secret level clearance. You are still concerned that one individual could perhaps compromise the network (intentionally or unintentionally) by setting up improper or unauthorized remote access. What is the best way to avoid this problem?
Which of the following activities are performed by the 'Do' cycle component of PDCA (plan-docheck- act)?
Each correct answer represents a complete solution. Choose all that apply.
You work as an Information Security Manager for uCertify Inc. You are working on asset management. You need to make a document on the classification of information assets. Which of the following controls of the ISO standard provides guidelines on the classification of information?
A honey pot is a computer trap that is used to attract potential intruders or attackers. Which of the following are some advantages of honey pots?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Security Administrator for uCertify Inc. You have developed a user manual for internal use, which will help your colleagues to work efficiently in the organization. However, you are concerned about the possibility of the user manual being distributed to the public. Therefore, you have decided to implement a system of classification so that you can secure information. Which of the following information classification levels will you use to implement the system?
You work as an Information Security Manager for uCertify Inc. You are working on a software asset management plan to provide backup for Active Directory. Which of the following data is required to be backed up for this purpose?
Service Level Agreement (SLA) provides one service for all customers of that service. Which of the following are the contents included by SLAs?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following statements about incremental backup are true?
Each correct answer represents a complete solution. Choose two.
You work as a Security Professional for uCertify Inc. You have been assigned the task to calculate the Recovery Time Objective for particular outage duration. Which of the following should be included in the Recovery Time Objective?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is a formula, practice, process, design, instrument, pattern, or compilation of information which is not generally known, but by which a business can obtain an economic advantage over its competitors?
As an attacker, you are sending very small sized packets with durations of 15 minutes per packet to the IIS Web server. Since an IIS session remains alive for a long time, the IDS may be tricked into accepting them as regular packet transformations. Which of the following types of attacking methods are you using?
Mark works as a Network Security Administrator for uCertify Inc. He has installed IDS for matching incoming packets against known attacks. Which of the following types of intrusion detection techniques is being used?
Your company is covered under a liability insurance policy, which provides various liability coverage for information security risks, including any physical damage of assets, hacking attacks, etc. Which of the following risk management techniques is your company using?
Diane is the project manager of the HGF Project. A risk that has been identified and analyzed in the project planning processes is now coming into fruition. What individual should respond to the risk with the preplanned risk response?
You work as a System Administrator for uCertify Inc. You have been given the task to create a new corporate policy. Which of the following approaches must be followed to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is used to hide the existence of a message from a third party?
You work as a Security Administrator for uCertify Inc. You observe that an employee is spreading personal data of your organization. Which of the following standards of information security deals with the employees handling personal data in an organization?
Rick works as a Computer Forensic Investigator for BlueWells Inc. He has been informed that some confidential information is being leaked out by an employee of the company. Rick suspects that someone is sending the information through email. He checks the emails sent by some employees to other networks. Rick finds out that Sam, an employee of the Sales department, is continuously sending text files that contain special symbols, graphics, and signs. Rick suspects that Sam is using the Steganography technique to send data in a disguised form. Which of the following techniques is Sam using?
Each correct answer represents a part of the solution. Choose all that apply.
Which of the following is NOT a common information-gathering technique while performing risk analysis?
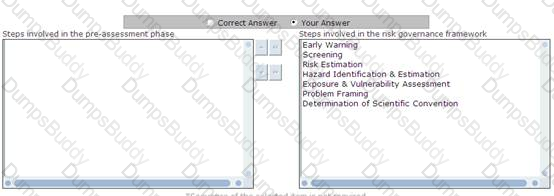
You work as a CRO for uCertify Inc. You and your team are involved in the pre-assessment phase of the risk governance framework. One of your newly joined team member wants to know the steps involved in the pre-assessment phase. Choose and reorder the steps performed in the pre-assessment phase.
Which of the following should be considered while calculating the costs of the outage?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Security Administrator for uCertify Inc. You have developed a user manual for internal use, which will help your colleagues to work efficiently in the organization. However, you are concerned about the possibility of the user manual being distributed to the public. Therefore, you have decided to implement a system of classification so that you can secure information.
Which of the following information classification levels will you use to implement the system?
Which of the following tasks are accomplished in the Act phase of the PDCA cycle?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following are security design principles required for information protection?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following creates policies, plans, and procedures to minimize the impact of risks to the organizational processes?
You work as an HR Manager for uCertify Inc. You are working on a checklist to develop an orderly exit process for the employees leaving your company. Which of the following actions should be included in that checklist?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following are the valid reasons for the occurrence of Drive-by download?
Each correct answer represents a complete solution. Choose all that apply.
You work as an Information Security Manager for uCertify Inc. You are working on asset management. You are making the documentation on control A.7.2. Which of the following are the main objectives of control A.7.2?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following refers to the process of adjusting the capacity of a company to meet the changed or predicted demands?
Which of the following formulas is used to represent the annualized loss expectancy (ALE)?
Sam is one of the four network administrators in Blue Well Inc. They have been assigned together the task to implement PDCA on the project. Sam has to work on the Plan stage of the project. Which of the following tasks should be performed by Sam?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Security Administrator for uCertify Inc. You are concerned about the password security. Therefore, you have decided to apply a policy that will be helpful for others to create strong passwords. Which of the following are the important things that should be remembered to create a strong password?
Each correct answer represents a complete solution. Choose all that apply.
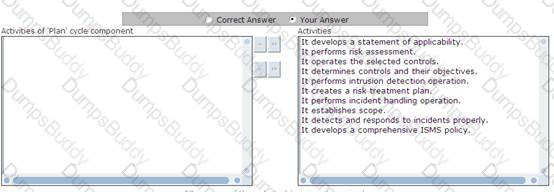
Choose and re-order the activities that are performed by the 'Plan' cycle component of PDCA (plan-docheck- act).
Which of the following identifies a company's exposure to threats and provides effective prevention and recovery for the company?
You are the Network Administrator for a school. You are concerned that end users' might accidentally have access to resources they do not require. What concept should you implement in your network security management to best address this concern?
You work as a Network Administrator for Net Soft Inc. You are designing a data backup plan for your company's network. The backup policy of the company requires high security and easy recovery of data. Which of the following options will you choose to accomplish this?
Which formula will you use to calculate the estimated average cost of 1 hour of downtime?
You want to use PGP files for steganography. Which of the following tools will you use to accomplish the task?
Mark is the project manager of the NHQ project in StarTech Inc. The project has an asset valued at $195,000 and is subjected to an exposure factor of 35 percent. What will be the Single Loss Expectancy of the project?
Which of the following are the variables on which the structure of Service Level Agreement depends?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following utilize information system in order to recognize, control, and protect information or any equipment used?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Security Administrator for uCertify Inc. You have been assigned a task for helping employees in determining appropriate technical security measures available for electronic information that is deemed sensitive. Which of the following policies will you apply to accomplish the task?
Which of the following are the steps of the Do stage of the project?
Each correct answer represents a part of the solution. Choose all that apply.
Which of the following are the activities of Incident Management?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following defines the interdependent relationships among the internal support groups of an organization working to support a Service Level Agreement?
David works as the Network Administrator for Blue Well Inc. One of his tasks is to develop and maintain risk management plan. Which of the following are the objectives of risk management plan?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following standards was concerned with corporate governance and directors' remuneration and issued in 1998?