Which of the following would be best to use to store a project task list that will be updated by multiple team members?
An administrator grants permission for a user to access data in a database. Which of the following actions was performed?
A user connects a wireless router to a home network and notices another wireless access point uses the same name. Which of the following should the user change?
A user revisits a website and receives a message that the site may not be secure. The user is prompted to click
a link to continue to the site. Which of the following would MOST likely identify the issue?
Which of the following is most likely to disclose the data collection practices of an application?
Which of the following utilities has the ability to remove drivers and scan for hardware changes?
A user is trying to set up a new wireless access point. Which of the following should the user do first?
Which of the following components is most likely to have a dedicated, active cooling method to prevent it from overheating during operation?
A technician wants to reset the boot order on a computer. Which of the following would the technician most likely use?
A technician has established a plan of action. Which of the following should the technician do next?
A technician replaces the video card in a user’s PC. The user reports the resolution on the display seems very low, but the operating system will not let the user adjust it any higher. Which of the following steps would MOST likely fix this problem?
A technician is configuring a new Windows PC and needs to choose a filesystem that supports encryption. Which of the following is the technician most likely to choose?
Which of the following notational systems uses the most characters to represent the decimal number 10?
A user has purchased a high-end graphics card that contains a GPU. Which of the following processes is being performed by the GPU on the graphics card?
A developer is writing a program to process a long list of employees and apply a cost-of-living increase of 3.2% to all employees making less than $15 per hour. Which of the following pseudocode snippets provides the best solution?
Which of the following software types is best suited for storing large amounts of data in a way that allows for concurrent, indexed access?
A large payment website was breached recently. A user is concerned that the breach will affect account
security on other sites. Which of the following password best practices would mitigate this risk?
Which of the following operating systems is best used in creating and managing virtual machines?
Which of the following business continuity concepts is the best example of fault tolerance?
Which of the following internet service types is most susceptible to weather disruptions?
A user opens an application that is installed locally on a PC. The application connects directly to a database that is located on a server in a data closet in the same building. Which of the following application architecture models does this describe?
A programmer is generating results by iterating rows that provide values needed for one calculation. Which of the following functions best accomplishes this task?
A startup company has created a logo. The company wants to ensure no other entity can use the logo for any purpose. Which of the following should the company use to BEST protect the logo? (Select TWO).
An executive is sharing a series of slides with coworkers in a conference room. Which of the following applications is the executive most likely to use?
Which of the following authorization techniques is used to assign permissions and authorize a user based on job title or function?
A user is selecting software to use to prepare handouts for a presentation. The user would like the information to be easy to format and printer friendly. Which of the following software types should the user select?
Which of the following elements is most important in order for data reports to have value?
Which of the following is the best way to prevent malicious code from executing on a laptop based on attack signatures?
A technician is concerned that sensitive data transmitted over the Internet can be intercepted and viewed during
a MITM attack. Which of the following should the technician enable to reduce the risk?
The finance department needs software that includes depreciation functionality for asset management. Which of the following types of software would best accomplish this goal?
A technician is troubleshooting an error message and tests the same program on a separate, identical
machine. Which of the following troubleshooting methodology steps is this an example of?
A user needs to enter text and numbers to produce charts that demonstrate sales figures. Which of the
following types of software would BEST complete this task?
Which of the following types of memory can retain its content after a system reboot?
A software developer has created a program for the accounting department. The finance department requests the same program but requires some changes to the code to meet its needs. Which of the following should be performed?
Which of the following is most appropriate to list on a social media site about an employer?
Which of the following would be the easiest component to upgrade on a laptop that is experiencing slow performance?
An application is hosted on a local network. Which of the following descriptions is correct?
A company has installed an application that only requires a workstation to function. Which of the following
architecture types is this application using?
A systems administrator wants to run a script at a certain time every day. Which of the following is the BEST
way to achieve this?
Which of the following application delivery mechanisms BEST describes infrastructure located in an individual organization’s datacenter?
Which of the following filesystems is compatible with the greatest number of operating systems?
A user is purchasing from an online retailer. The user has entered all the required information and has clicked the "Submit" button, yet the page does not refresh, and the user does not get a confirmation. Which of the following might be the causes of the issue? (Select two).
Which of the following programming languages would most likely include tables and the select command?
Which of the following best describes the process of comparing MD5 values after downloading software?
A company purchased a software program. The EULA states that the software can be installed on as many computers as the company wants, but only four users can be using the software at any point in time. Which of the following types of licenses is this an example of?
Multiple users need to access the same data simultaneously. Which of the following is the best place to store the data?
Which of the following allows wireless devices to communicate to a wired network?
A technician reading workstation security logs notices that an unidentified device is plugged into a USB port several hours a day but is never plugged in when the technician goes to check the machine. File audits reveal nothing unexpected. Which of the following devices is most likely causing this message?
Which of the following would MOST likely prevent malware sent as compromised file via email from infecting a person’s computer?
Which of the following would be BEST to keep the data on a laptop safe if the laptop is lost or stolen?
A computer user is downloading software from the Internet and notices the following at the end of the install file: “…x86.exe”. Which of the following statements BEST represents what the “…x86.exe” means in the installation file?
A user works at a health insurance company. Which of the following is the best method for ensuring a customer's personal information is kept confidential when it needs to be shared with another authorized employee?
A programmer is modifying the code of an existing application to include an additional subroutine that is needed for a new product line. Which of the following will most likely be added to the existing code?
Which of the following categories describes commands used to extract information from a database?
The sales department needs to keep a customer list that contains names, contact information, and sales
records. This list will need to be edited by multiple people at the same time. Which of the following applications should be used to create this list?
NO: 56
A technician needs to install a wireless router for a client that supports speeds up to 11Mbps and operates on the 2.4GHz band. Which of the following should the technician select?
A company wants an application to be accessed by concurrent users and store company information securely.
Which of the following would be the BEST option for storing the information?
Which of the following commands would most likely be used to add data to an existing database table?
A small company wants to set up a server that is accessible from the company network as well as the Internet.
Which of the following is MOST important to determine before allowing employees to access the server
remotely?
An employee’s laptop does not connect to the Internet when it is used in a coffee shop. Which of the following
is the MOST likely cause?
Users are required to install a certificate in order to access commercial web pages through a corporate proxy server. Which of the following Windows Control Panel applets would enable users to verify the needed certificate is installed?
A network administrator requires that a non-magnetic drive be used to store critical data for a project. The project is expected to last a few years. Which of the following would the administrator most likely choose for the project?
A user is getting an error message when trying to go to a website. A technician asks the user a few questions to find out more about the issue. The technician opens a browser locally and browses to the same site as the user. Which of the following troubleshooting steps is the technician using by browsing to the same site?
A flatbed scanner that is connected to a laptop is used to convert photographic prints to digital images for reproduction on a color printer. Which of the following is considered the input device for this process?
A help desk technician encounters an issue and wants to find out if a colleague has encountered the same issue before. Which of the following should the technician do FIRST?
A user wants to ensure port 3389 is open for remote desktop on a PC. Which of the following describes where the user should verify the port is open?
Joe, a user, finds out his password for a social media site has been compromised. Joe tells a friend that his email and banking accounts are probably also compromised. Which of the following has Joe MOST likely performed?
Which of the following is an example of information a company would ask employees to handle in a sensitive manner?
A user inserts a USB flash drive into a computer tor the first time and sees a message on the screen indicating the device is being set up. The message quickly changes to indicate the device is ready for use. Which of the following device configuration types most likely occurred?
Joe, a developer, is writing a program in which he needs to store a number that changes over the duration of the program’s run. Which of the following would Joe MOST likely use to accomplish this?
A programmer chooses a database for a new application that needs to store information, including dates, times, names, and amounts. Which of the following database features is this an example of?
Which of the following network protocols will MOST likely be used when sending and receiving Internet email?
(Select TWO.)
An administrator is preparing a workstation for deployment. Which of the following is the first step the administrator should take in this process?
Which of the following BEST explains the use of float over integer to store monetary values?
Which of the following connection types is typically used for a display monitor?
A user is attempting to print a document to a wireless printer and receives an error stating the operation could not be completed. Which of the following should the user do to correct this issue?
Given the following pseudocode:
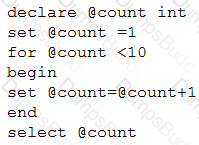
Which of the following is the output of the code?
A systems administrator is setting up a new server using RAID technology. If one hard drive in the array fails,
the data is stored on another drive, preventing data loss. Which of the following business continuity concepts
does this explain?