The PRIMARY benefit of conducting a risk workshop using a top-down approach instead of a bottom-up approach is the ability to:
identify specific project risk.
obtain a holistic view of IT strategy risk.
understand risk associated with complex processes.
incorporate subject matter expertise.
Obtaining a holistic view of IT strategy risk is the primary benefit of conducting a risk workshop using a top-down approach instead of a bottom-up approach, because it helps to identify and assess the risks that may affect the alignment and integration of IT with the organization’s objectives and strategy. A risk workshop is a collaborative and interactive method of conducting a risk assessment, where the risk practitioner facilitates a group discussion with the relevant stakeholders to identify, analyze, and evaluate the risks and their controls. A top-down approach is a method of conducting a risk workshop that starts from the high-level or strategic perspective, and then drills down to the lower-level or operational details. A bottom-up approach is a method of conducting a risk workshop that starts from the low-level or operational details, and then aggregates them to the higher-level or strategic perspective. A top-down approach can offer a holistic view of IT strategy risk, as it helps to understand the big picture and the interrelationships of the risks and their impacts across the organization. A bottom-up approach can offer a detailed view of specific project or process risk, as it helps to capture the granular and technical aspects of the risks and their controls. Therefore, obtaining a holistic view of IT strategy risk is the primary benefit of using a top-down approach, as it supports the strategic alignment and integration of IT with the organization. Identifying specific project risk, understanding risk associated with complex processes, and incorporating subject matter expertise are all possible benefits of conducting a risk workshop, but they are not the primary benefit of using a top-down approach, as they are more suitable for a bottom-up approach. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.2.2, page 87
Which of the following situations reflects residual risk?
Risk that is present before risk acceptance has been finalized
Risk that is removed after a risk acceptance has been finalized
Risk that is present before mitigation controls have been applied
Risk that remains after mitigation controls have been applied
Detailed Explanation:Residual riskrefers to the risk that remains after mitigation measures have been applied. It represents the exposure that an organization decides to accept, transfer, or further address, aligning with its risk appetite and tolerance.
Which of the following is the BEST approach for determining whether a risk action plan is effective?
Comparing the remediation cost against budget
Assessing changes in residual risk
Assessing the inherent risk
Monitoring changes of key performance indicators(KPIs)
According to the CRISC Review Manual (Digital Version), assessing changes in residual risk is the best approach for determining whether a risk action plan is effective, as it measures the impact and value of the risk response actions and controls on the risk level. Residual risk is the risk that remains after the risk response actions and controls have been implemented. Assessing changes in residual risk helps to:
Evaluate the extent to which the risk response actions and controls have reduced the likelihood and/or impact of the risk to an acceptable level
Identify and report any deviations, errors, or weaknesses in the risk response actions and controls and their performance
Recommend and implement corrective actions or improvement measures to address any issues or deficiencies in the risk response actions and controls
Monitor and measure the effectiveness and efficiency of the risk response actions and controls and their alignment with the organization’s risk appetite and risk tolerance
Update the risk register and the risk treatment plan to reflect the current risk status and the residual risk levels
References = CRISC Review Manual (Digital Version), Chapter 3: IT Risk Response, Section 3.2: Risk Response Process, pp. 161-1621
When implementing an IT risk management program, which of the following is the BEST time to evaluate current control effectiveness?
Before defining a framework
During the risk assessment
When evaluating risk response
When updating the risk register
The best time to evaluate current control effectiveness when implementing an IT risk management program is during the risk assessment, as it involves measuring and testing the performance and adequacy of the existing controls, and identifying any control gaps or deficiencies that may affect the risk level and response. Before defining a framework, when evaluating risk response, and when updating the risk register are not the best times, as they are more related to the design, selection, or reporting of the controls, respectively, rather than the evaluation of the control effectiveness. References = CRISC Review Manual, 7th Edition, page 154.
Which of the following is the GREATEST concern when using artificial intelligence (AI) language models?
The model could be hacked or exploited.
The model could be used to generate inaccurate content.
Staff could become overly reliant on the model.
It could lead to biased recommendations.
Biased recommendations from AI models pose significant risks to decision-making and organizational ethics. Such biases can propagate systemic issues and impact regulatory compliance, emphasizing the need for robust controls in AI development and deployment underEmerging Technology Risks.
An organization's decision to remain noncompliant with certain laws or regulations is MOST likely influenced by:
The region in which the organization operates.
Established business culture.
Risk appetite set by senior management.
Identified business process controls.
Risk appetite determined by senior management reflects the enterprise's willingness to accept certain levels of risk, including noncompliance. This decision underscores the strategic trade-offs made in risk management, a key element inGovernance and Risk Policy Alignment.
Within the three lines of defense model, the responsibility for managing risk and controls resides with:
operational management.
the risk practitioner.
the internal auditor.
executive management.
According to the three lines of defense model, the responsibility for managing risk and controls resides with the operational management, which forms the first line of defense. The operational management is the function that owns and manages risk as part of their accountability for achieving objectives. They are responsible for identifying, assessing, mitigating, and reporting on risks and controls within their areas ofoperation. They are also responsible for implementing and maintaining effective internal controls and ensuring compliance with policies, standards, and regulations.
References:
•ISACA, Risk IT Framework, 2nd Edition, 2019, p. 741
•Internal audit: three lines of defence model explained2
The MOST important measure of the effectiveness of risk management in project implementation is the percentage of projects:
introduced into production without high-risk issues.
having the risk register updated regularly.
having key risk indicators (KRIs) established to measure risk.
having an action plan to remediate overdue issues.
The percentage of projects introduced into production without high-risk issues is the most important measure of the effectiveness of risk management in project implementation, as it reflects the ability of risk management to ensure that the project deliverables meet the quality, functionality, and security requirements, and do not introduce unacceptable risks to the organization. The percentage of projects having the risk register updated regularly, having key risk indicators (KRIs) established to measure risk, or having an action plan to remediate overdue issues are not the most important measures, as they are more related to the process, performance, or compliance of risk management, rather than the outcome or value of risk management. References = CRISC Review Manual, 7th Edition, page 110.
Which of the following is MOST important to the effectiveness of key performance indicators (KPIs)?
Management approval
Annual review
Relevance
Automation
The most important factor to the effectiveness of key performance indicators (KPIs) is relevance. KPIs are metrics that measure the achievement of the objectives or the performance of the processes. Relevance means that the KPIs are aligned with and support the strategic goals and priorities of the organization, and that they reflect the current and desired state of the outcomes or outputs. Relevance also means that the KPIs are meaningful and useful for the decision makers and stakeholders, and that they provide clear and actionable information for improvement or optimization. The other options are not as important as relevance, as they are related to the approval, review, or automation of the KPIs, not the quality or value of the KPIs. References = Risk and Information Systems Control Study Manual, Chapter 4: Risk and Control Monitoring and Reporting, Section 4.2: Key Performance Indicators, page 183.
The BEST way for management to validate whether risk response activities have been completed is to review:
the risk register change log.
evidence of risk acceptance.
control effectiveness test results.
control design documentation.
Reviewing the risk register change log is the best way for management to validate whether risk response activities have been completed, because it helps to track and monitor the changes and updates that have been made to the risk register, and to verify that the risk response activities have been implemented and closed. A risk register is a document that captures, identifies, assesses and tracks risk as part of the risk management process4. A risk register change log is a record that documents the date, description, and reason for each change or update that is made to the risk register. A risk response activity is an action or task that is performed to implement the chosen risk response strategy for a specific risk, such as avoid, transfer, mitigate, or accept. Reviewing the risk register change log is the best way, as it helps to ensure that the risk register is accurate and current, and that the risk response activities have been completed and reported. Reviewing evidence of risk acceptance, control effectiveness test results, and control design documentation are all possible ways to validate whether risk response activities have been completed, but they are not the best way, as they may not cover all the risk response activities, and they may not reflect the changes or updates in the risk register. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.4.1, page 101
What is a risk practitioner's BEST approach to monitor and measure how quickly an exposure to a specific risk can affect the organization?
Create an asset valuation report.
Create key performance indicators (KPls).
Create key risk indicators (KRIs).
Create a risk volatility report.
Key risk indicators (KRIs) are metrics that measure the exposure to a given risk at a particular time. They can also provide early warning signs of a potential change in risk level. By monitoring KRIs, risk practitioners can assess how quickly an exposure to a specific risk can affect the organization and take appropriate actions.
References
•Risk management at the speed of business - PwC
•Risk velocity measures how fast an exposure can affect an organization | Business Insurance
A risk practitioner wants to identify potential risk events that affect the continuity of a critical business process. Which of the following should the risk practitioner do FIRST?
Evaluate current risk management alignment with relevant regulations.
Determine if business continuity procedures are reviewed and updated on a regular basis.
Review the methodology used to conduct the business impact analysis (BIA).
Conduct a benchmarking exercise against industry peers.
Reviewing the methodology used to conduct the business impact analysis (BIA) is the first thing that a risk practitioner should do when wanting to identify potential risk events that affect the continuity of a critical business process, because it helps to ensure that the BIA is conducted in a consistent, comprehensive, and reliable manner, and that it covers all the relevant aspects and scenarios of the business process and its continuity. A BIA is a process of analyzing the potential impact of disruption to the critical business functions or processes, and identifying the recovery priorities and requirements. A BIA methodology is a set of principles, standards, and techniques that guide and support the BIA process, such as the scope, objectives, data sources, data collection methods, data analysis methods, and reporting methods. Reviewing the BIA methodology is the first thing to do, as it helps to establish the foundation and framework for the BIA process, and to ensure that the BIA results are valid and useful for identifying the potential risk events and their consequences. Evaluating current risk management alignment with relevant regulations, determining if business continuity proceduresare reviewed and updated on a regular basis, and conducting a benchmarking exercise against industry peers are all possible things to do after reviewing the BIA methodology, but they are not the first thing to do, as they depend on the quality and accuracy of the BIA process and outcomes. References = Risk and Information Systems Control Study Manual, Chapter 4, Section 4.2.1, page 143
Which of the following is the PRIMARY purpose for ensuring senior management understands the organization’s risk universe in relation to the IT risk management program?
To define effective enterprise IT risk appetite and tolerance levels
To execute the IT risk management strategy in support of business objectives
To establish business-aligned IT risk management organizational structures
To assess the capabilities and maturity of the organization’s IT risk management efforts
Ensuring senior management understands the organization’s risk universe in relation to the IT risk management program is primarily to define effective enterprise IT risk appetite and tolerance levels. This understanding is essential for setting the boundaries within which the organization is willing to operate regarding IT risks.
Defining Effective IT Risk Appetite and Tolerance Levels (Answer A):
Purpose: Senior management needs to understand the range and nature of IT risks to set appropriate risk appetite and tolerance levels.
Impact: This enables the organization to make informed decisions about which risks to accept, mitigate, transfer, or avoid.
Alignment: It ensures that the IT risk management strategy is aligned with the overall business objectives and risk posture of the organization.
Comparison with Other Options:
B. To execute the IT risk management strategy in support of business objectives:
Purpose: While important, it follows the definition of risk appetite and tolerance.
Limitation: Without understanding the risk universe, execution may be misaligned.
C. To establish business-aligned IT risk management organizational structures:
Purpose: Structural alignment is crucial but secondary to setting risk appetite and tolerance.
D. To assess the capabilities and maturity of the organization’s IT risk management efforts:
Purpose: This is part of the ongoing process but not the primary purpose of understanding the risk universe.
References:
ISACA CRISC Review Manual, Chapter 1, "Governance", which discusses the importance of risk appetite and tolerance in the context of IT risk management.
Which of the following events is MOST likely to trigger the need to conduct a risk assessment?
An incident resulting in data loss
Introduction of a new product line
Changes in executive management
Updates to the information security policy
The introduction of a new product line is most likely to trigger the need to conduct a risk assessment. Here’s a detailed explanation:
Risk Assessment Triggers:
New Initiatives: New initiatives, such as the introduction of a new product line, significantly alter the business landscape. They introduce new processes, technologies, and potentially new regulatory requirements, all of which bring new risks that must be assessed.
Business Impact: A new product line can affect multiple areas of the business, including production, marketing, sales, and customer service. It can also impact the existing product portfolio and market position, requiring a thorough risk assessment to understand these impacts.
Comparison with Other Events:
Incident Resulting in Data Loss: While significant, an incident resulting in data loss is typically a reactive trigger for a specific security or forensic investigation rather than a comprehensive risk assessment.
Changes in Executive Management: Changes in executive management may necessitate a review of strategic risks but are less likely to trigger a comprehensive risk assessment compared to launching a new product.
Updates to the Information Security Policy: Updating the information security policy is an internal process that may not fundamentally alter the risk landscape like introducing a new product line.
Best Practices:
Comprehensive Planning: Before launching a new product, conduct a comprehensive risk assessment to identify potential risks, develop mitigation strategies, and ensure alignment with business objectives.
Stakeholder Involvement: Engage key stakeholders from various departments to provide insights and ensure all potential risks are considered.
References:
CRISC Review Manual: Highlights the importance of conducting risk assessments in response to significant changes in the business environment, such as new product introductions.
ISACA Guidelines: Emphasize the need for risk assessments to ensure that new initiatives align with organizational risk appetite and tolerance.
WhichT5f the following is the MOST effective way to promote organization-wide awareness of data security in response to an increase in regulatory penalties for data leakage?
Enforce sanctions for noncompliance with security procedures.
Conduct organization-w>de phishing simulations.
Require training on the data handling policy.
Require regular testing of the data breach response plan.
The most effective way to promote organization-wide awareness of data security in response to an increase in regulatory penalties for data leakage is to require training on the data handling policy, as it educates the employees on the importance, requirements, and procedures of data protection, and enhances their knowledge and skills to prevent, detect, and respond to data leakage incidents. Enforcingsanctions for noncompliance with security procedures, conducting organization-wide phishing simulations, and requiring regular testing of the data breach response plan are not the most effective ways, as they are more related to the enforcement, evaluation, or improvement of the data security, respectively, rather than the promotion of the data security awareness. References = CRISC Review Manual, 7th Edition, page 155.
Which of the following is the BEST control for a large organization to implement to effectively mitigate risk related to fraudulent transactions?
Segregation of duties
Monetary approval limits
Clear roles and responsibilities
Password policies
Segregation of duties is a key control for preventing and detecting fraudulent transactions, especially in a large organization where there are many employees and transactions involved. Segregation of duties means that no single person has the authority or ability to initiate, approve, execute, and record a transaction without the involvement or oversight of another person. This reduces the opportunity and incentive for fraud, as well as the risk of errors or omissions. Segregation of duties also facilitates the detection of fraud by creating an audit trail and increasing the likelihood of whistleblowing.
The other options are not as effective as segregation of duties for mitigating risk related to fraudulent transactions. Monetary approval limits (B) are useful for controlling the amount and frequency of transactions, but they do not prevent unauthorized or fraudulent transactions from occurring. Clear roles and responsibilities © are important for defining the expectations and accountabilities of employees, but they do not ensure that employees comply with them or that their actions are monitored and verified. Password policies (D) are essential for securing access to systems and data, but they do not prevent fraudsters from exploiting weak or compromised passwords or from using legitimate passwords for fraudulent purposes.
An organization plans to implement a new Software as a Service (SaaS) speech-to-text solution Which of the following is MOST important to mitigate risk associated with data privacy?
Secure encryption protocols are utilized.
Multi-factor authentication is set up for users.
The solution architecture is approved by IT.
A risk transfer clause is included in the contact
Utilizing secure encryption protocols is the most important factor to mitigate risk associated with data privacy when implementing a new Software as a Service (SaaS) speech-to-text solution, as it ensures that the data is protected from unauthorized access, interception, or modification during the transmission and storage in the cloud. Setting up multi-factor authentication for users, approving the solution architecture by IT, and including a risk transfer clause in the contract are not the most important factors, as they may not address the data privacy issue, but rather the data access, quality, or liability issue, respectively. References = CRISC Review Manual, 7th Edition, page 153.
Which of the following is the BEST criterion to determine whether higher residual risk ratings in the risk register should be accepted?
Risk maturity
Risk policy
Risk appetite
Risk culture
Risk appetite is the best criterion to determine whether higher residual risk ratings in the risk register should be accepted, as it reflects the amount and type of risk that an organization is willing to take in pursuit of its objectives. Residual risk is the level of risk that remains after applying controls or other risk treatments. By comparing the residual risk ratings against the risk appetite, an organization can decide whether to accept, reduce, transfer, or avoid the risk. If the residual risk is within or below the risk appetite, the organization may accept the risk as tolerable. If the residual risk is above the risk appetite, the organization may not accept the risk as acceptable, and may seek further risk treatments or escalation.
References:
•ISACA, Risk IT Framework, 2nd Edition, 2019, p. 751
•ISACA, Risk and Information Systems Control Review Manual, 7th Edition, 2020, p. 2112
Which of the following roles should be assigned accountability for monitoring risk levels?
Risk practitioner
Business manager
Risk owner
Control owner
The risk owner should be assigned accountability for monitoring risk levels, as they have the authority and responsibility to manage the risk and its associated controls, and to report on the risk status and performance. The risk practitioner, the business manager, and the control owner are not the best choices, as they have different roles and responsibilities related to risk identification, assessment, response, and reporting, but they are not accountable for the risk and its monitoring. References = CRISC Review Manual, 7th Edition, page 101.
Which of the following should be the PRIMARY input to determine risk tolerance?
Regulatory requirements
Organizational objectives
Annual loss expectancy (ALE)
Risk management costs
Organizational objectives should be the primary input to determine risk tolerance, as they define the desired outcomes and performance of the organization, and guide the selection of the acceptable level of risk that the organization is willing to take to achieve those objectives. Regulatory requirements, annual loss expectancy (ALE), and risk management costs are not the primary inputs, as they are more related to the external or internal constraints or factors that affect the risk tolerance, rather than the drivers or determinants of the risk tolerance. References = CRISC Review Manual, 7th Edition, page 109.
Which of the following is the MOST important reason to restrict access to the risk register on a need-to-know basis?
It contains vulnerabilities and threats.
The risk methodology is intellectual property.
Contents may be used as auditable findings.
Risk scenarios may be misinterpreted.
Restricting access to the risk register on a need-to-know basis is important because it contains vulnerabilities and threats that could expose the organization to potential harm or loss if they are disclosed or exploited by unauthorized parties. The risk register is a tool that captures and documents the risk identification, analysis, evaluation, and treatment processes1. The risk register contains sensitive information such as the sources and causes of risk, the potential impacts and consequences of risk, the likelihood and frequency of risk occurrence, and the risk response actions and plans1. If this information is accessed by unauthorized parties, such as competitors, hackers, or malicious insiders, they could use it to launch attacks, sabotage operations, or gain an unfair advantage over the organization. Therefore, access to the risk register should be limited to those who have a legitimate need and authorization to view, modify, or use the information, such as the risk owners, managers, or practitioners
Which of the following provides the MOST useful information to trace the impact of aggregated risk across an organization's technical environment?
Business case documentation
Organizational risk appetite statement
Enterprise architecture (EA) documentation
Organizational hierarchy
Enterprise architecture (EA) documentation provides the most useful information to trace the impact of aggregated risk across the organization’s technical environment, because it describes the structure and behavior of the organization’s IT systems, applications, infrastructure, and processes, and how they support and enable the organization’s strategy and objectives. EA documentation also defines the principles, standards, and guidelines that govern the design and implementation of the IT solutions and services. Aggregated risk is the total or combined level of risk that the organization faces from multiple or interrelated sources or scenarios. Aggregated risk may have a greater impact than the sum of the individual risks, due to the synergistic or compounding effects of the risks. The technical environment is the set of IT components and capabilities that support the organization’s business functions and processes. Tracing the impact of aggregated risk across the technical environment is a process of identifying and assessing the potential or actual consequences of the aggregated risk on the performance, functionality, or security of the IT systems, applications, infrastructure, or processes. EA documentation provides the most useful information, as it helps to understand and analyze the interdependencies and relationships of the IT components and capabilities, andto evaluate the effect of the aggregated risk on the alignment and integration of IT with the organization’s strategy and objectives. Business case documentation, organizational risk appetite statement, and organizational hierarchy are all possible sources of information to trace the impact of aggregated risk, but they are not the most useful information, as they do not provide a comprehensive and detailed view of the technical environment and its architecture. References = Risk and Information Systems Control Study Manual, Chapter 5, Section 5.2.1, page 183
Which of the following would provide the MOST useful input when evaluating the appropriateness of risk responses?
Incident reports
Cost-benefit analysis
Risk tolerance
Control objectives
Risk tolerance is the most useful input when evaluating the appropriateness of risk responses, as it defines the acceptable level of risk for the organization and guides the selection of the optimal risk response. Incident reports, cost-benefit analysis, and control objectives are also useful inputs, but they are not the most useful, as they provide information on the actual or potential impact, cost, and effectiveness of the risk responses, but not the desired level of risk. References = CRISC Review Manual, 7th Edition, page 108.
Which of the following scenarios is MOST likely to cause a risk practitioner to request a formal risk acceptance sign-off?
Residual risk in excess of the risk appetite cannot be mitigated.
Inherent risk is too high, resulting in the cancellation of an initiative.
Risk appetite has changed to align with organizational objectives.
Residual risk remains at the same level over time without further mitigation.
Requesting a formal risk acceptance sign-off is the most likely scenario when the residual risk in excess of the risk appetite cannot be mitigated, because it indicates that the organization is willing to tolerate a higher level of risk than it normally would, and that the risk owner has the authority and accountability to accept the risk and its consequences. Risk acceptance is a risk response strategy that involves acknowledging the existence ofa risk and deciding not to take any action to reduce it. Risk acceptance is usually chosen when the cost or effort of mitigating the risk outweighs the potential benefits, or when no feasible mitigation options are available. Residual risk is the risk that remains after applying controls or mitigating factors. Risk appetite is the amount and type of risk that an organization is willing to accept in pursuit of its objectives. Inherent risk, cancellation of an initiative, change of risk appetite, and constant residual risk are all possible scenarios that may affect the risk management process, but they are not the most likely to cause a risk practitioner to request a formal risk acceptance sign-off, as they do not necessarily involve a risk owner accepting a higher level of risk than the organization’s risk appetite. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.4.2, page 103
A poster has been displayed in a data center that reads. "Anyone caught taking photographs in the data center may be subject to disciplinary action." Which of the following control types has been implemented?
Corrective
Detective
Deterrent
Preventative
A deterrent control is a type of control that has been implemented by displaying a poster that reads “Anyone caught taking photographs in the data center may be subject to disciplinary action.”, as it aims to discourage or prevent unauthorized or malicious activities by warning the potential perpetrators of the consequences or sanctions. The other options are not the correct types of control, as they are more related to the correction, detection, or prevention of unauthorized or malicious activities, respectively, rather than the deterrence of unauthorized or malicious activities. References = CRISC Review Manual, 7th Edition, page 154.
After an annual risk assessment is completed, which of the following would be MOST important to communicate to stakeholders?
A decrease in threats
A change in the risk profile
An increase in reported vulnerabilities
An increase in identified risk scenarios
A change in the risk profile would be the most important information to communicate to stakeholders after an annual risk assessment is completed, as it indicates how the risk landscape of the organization has changed over time, and how it affects the achievement of the business goals and objectives. A decrease in threats, an increase in reported vulnerabilities, and an increase in identified risk scenarios are also important information, but they are not the most important, as they are specific aspects of the risk profile, and do not provide a holistic view of the risk exposure and appetite of the organization. References = CRISC Review Manual, 7th Edition, page 109.
Which of the following is a PRIMARY objective of privacy impact assessments (PIAs)?
To identify threats introduced by business processes
To identify risk when personal information is collected
To ensure senior management has approved the use of personal information
To ensure compliance with data privacy laws and regulations
A risk practitioner learns that a risk owner has been accepting gifts from a supplier of IT products. Some of these IT products are used to implement controls and to mitigate risk to acceptable levels. Which of the following should the risk practitioner do FIRST?
Initiate disciplinary action against the risk owner.
Reassess the risk and review the underlying controls.
Review organizational ethics policies.
Report the activity to the supervisor.
Reporting the activity to the supervisor is the first thing that the risk practitioner should do when learning that a risk owner has been accepting gifts from a supplier of IT products. This is because accepting gifts from a supplier of IT products can create a conflict of interest, compromise the integrity and objectivity of the risk owner, and violate the organizational ethics policies. Reporting the activity to the supervisor can help ensure that the issue is escalated to the appropriate authority, investigated, and resolved in a timely and transparent manner. According to the CRISC Review Manual 2022, one of the key risk response techniques is to report the risk to the relevant stakeholders, such as the supervisor1. According to the web search results, reporting the activity to the supervisor is a common and recommended action when encountering a potential ethical violation in the workplace
Which of the following should be a risk practitioner's NEXT step after learning of an incident that has affected a competitor?
Activate the incident response plan.
Implement compensating controls.
Update the risk register.
Develop risk scenarios.
The risk practitioner’s next step after learning of an incident that has affected a competitor is to develop risk scenarios, as it involves identifying and describing the potential sources, events, impacts, and responses of the risk that may affect the organization in a similar way as the competitor, and assessing the likelihood and magnitude of the risk. Activating the incident response plan, implementing compensating controls, and updating the risk register are not the next steps, as they are more related to the reaction, mitigation, or reporting of the risk, respectively, rather than the identification and assessment of the risk. References = CRISC Review Manual, 7th Edition, page 100.
A global organization is considering the transfer of its customer information systems to an overseas cloud service provider in the event of a disaster. Which of the following should be the MOST important risk consideration?
Regulatory restrictions for cross-border data transfer
Service level objectives in the vendor contract
Organizational culture differences between each country
Management practices within each company
Regulatory restrictions for cross-border data transfer can significantly impact compliance, making this the most critical consideration. Addressing such restrictions ensures adherence toLegal and Regulatory Requirementsin risk management.
A risk practitioner has been asked to evaluate the adoption of a third-party blockchain integration platform based on the value added by the platform and the organization's risk appetite. Which of the following is the risk practitioner's BEST course of action?
Conduct a risk assessment with stakeholders.
Conduct third-party resilience tests.
Update the risk register with the process changes.
Review risk related to standards and regulations.
Conducting a risk assessment with stakeholders is the best course of action for the risk practitioner to evaluate the adoption of a third-party blockchain integration platform, because it helps to identify, analyze, and evaluate the risks and opportunities associated with the platform, and to compare them with the organization’s risk appetite and value proposition. A risk assessment is a process of systematically identifying and assessing the sources and types of risk that an organization faces, and estimating their likelihood and impact. A risk assessment also involves identifying and evaluating the existing or proposed controls or mitigating factors that can reduce or eliminate the risk. A stakeholder is a person or group that has an interest or influence in the organization or its activities, such as customers, employees, shareholders, suppliers, regulators, or partners. A blockchain integration platform is a software solution that enables the organization to connect and interact with blockchain networks or applications, such as cryptocurrencies, smart contracts, or distributed ledgers. A blockchain integration platform can offer benefits such as transparency, security, efficiency, and innovation, but it can also pose risks such as technical complexity, interoperability issues, regulatory uncertainty, or cyberattacks. Therefore, conducting a risk assessment with stakeholders is the best way to evaluate the adoption of a third-party blockchain integration platform, as it helps to understand the benefits and risks of the platform, and to align them with the organization’s objectives and risk appetite. Conducting third-party resilience tests, updating the risk register with the process changes, and reviewing risk related to standards and regulations are all important tasks to perform after conducting a risk assessment, but they are not the best course of action, as they depend on the results of the risk assessment. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.2.2, page 87
Which of the following should be the MOST important consideration when determining controls necessary for a highly critical information system?
The number of threats to the system
The organization's available budget
The number of vulnerabilities to the system
The level of acceptable risk to the organization
Determining Controls:
Acceptable Risk Level: The level of acceptable risk to the organization is the most important consideration because it directly influences the type and extent of controls implemented. Controls must be designed to keep risk within acceptable levels.
Risk Management Strategy: Aligning controls with the organization's risk appetite ensures that resources are used effectively and that critical information systems are adequately protected.
Comparison with Other Options:
Number of Threats: Important for understanding risk exposure but secondary to determining acceptable risk levels.
Available Budget: Budget constraints are important but should not compromise the implementation of necessary controls.
Number of Vulnerabilities: Identifying vulnerabilities is part of the risk assessment process, but controls are prioritized based on the acceptable risk level.
Best Practices:
Risk Assessment: Conduct thorough risk assessments to understand the potential impact of threats and vulnerabilities.
Control Effectiveness: Implement controls that are both cost-effective and capable of reducing risk to acceptable levels.
Continuous Monitoring: Regularly monitor and review controls to ensure they remain effective and aligned with the organization's risk tolerance.
References:
CRISC Review Manual: Highlights the importance of aligning controls with the acceptable risk levels determined by the organization .
ISACA Standards: Recommend focusing on acceptable risk levels to guide control implementation and ensure effective risk management .
Which of the following is the MOST important key performance indicator (KPI) for monitoring the user access management process?
Proportion of end users having more than one account
Percentage of accounts disabled within the service level agreement (SLA)
Proportion of privileged to non-privileged accounts
Percentage of accounts that have not been activated
User Access Management:
Effective user access management ensures that accounts are properly created, managed, and disabled to prevent unauthorized access.
Monitoring the percentage of accounts disabled within the SLA helps ensure that the organization responds promptly to changes in user status, reducing the risk of unauthorized access.
Importance of KPI:
This KPI measures the efficiency and effectiveness of the user access management process by tracking how quickly accounts are disabled when no longer needed.
A high percentage indicates timely action, reducing the risk of orphaned accounts being exploited.
Comparing Other KPIs:
Proportion of End Users Having More Than One Account:Useful but not directly related to the timeliness of disabling accounts.
Proportion of Privileged to Non-Privileged Accounts:Important for monitoring privilege distribution but does not measure process efficiency.
Percentage of Accounts Not Activated:Indicates potential inefficiencies but does not address the risk of active accounts.
References:
The CRISC Review Manual highlights the importance of timely account management to mitigate access risks (CRISC Review Manual, Chapter 3: Risk Response and Mitigation, Section 3.3 User Access Management).
An organization has implemented a policy requiring staff members to take a minimum of five consecutive days' leave per year to mitigate the risk of malicious insider activities. Which of the following is the BEST key performance indicator (KPI) of the effectiveness of this policy?
Percentage of staff turnover following five consecutive days of leave
Average number of consecutive days of leave per staff member
Number of suspected malicious activities reported since policy implementation
Financial loss incurred due to malicious activities since policy implementation
The number of suspected malicious activities reported since the policy's implementation directly measures thepolicy's effectiveness in identifying and mitigating insider threats. This aligns withKey Performance Indicators (KPIs)used to evaluate control outcomes.
Which of the following is the MOST critical consideration when awarding a project to a third-party service provider whose servers are located offshore?
Difficulty of monitoring compliance due to geographical distance
Cost implications due to installation of network intrusion detection systems (IDSs)
Delays in incident communication
Potential impact on data governance
When determining risk ownership, the MAIN consideration should be:
who owns the business process.
the amount of residual risk.
who is responsible for risk mitigation.
the total cost of risk treatment.
It was discovered that a service provider's administrator was accessing sensitive information without the approval of the customer in an Infrastructure as a Service (laaS) model. Which of the following would BEST protect against a future recurrence?
Data encryption
Intrusion prevention system (IPS)
Two-factor authentication
Contractual requirements
The best option to protect against a future recurrence of unauthorized access by a service provider’s administrator is D. Contractual requirements. Data encryption, intrusion prevention system, and two-factor authentication are all technical measures that can enhance the security of the data stored in the Infrastructure as a Service (IaaS) model, but they do not prevent the service provider’s administrator from accessing the data if they have the necessary credentials, keys, or permissions. Contractual requirements, on the other hand, are legal obligations that bind the service provider to respect the customer’s privacy and confidentiality, and to limit the access to the data to only authorized and necessary personnel. Contractual requirements can also specify the penalties or remedies for any breach of contract, which can deter the service provider’s administrator from violating the terms of the agreement. Therefore, contractual requirements are the most effective way to protect against a future recurrence of unauthorized access by a service provider’s administrator12
1: What is Data Encryption? | Forcepoint 2: The elements of a contract: understanding contract requirements - Juro
A risk practitioner has been asked to assess the risk associated with a new critical application used by a financial process team that the risk practitioner was a member of two years ago. Which of the following is the GREATEST concern with this request?
The risk assessment team may be overly confident of its ability to identify issues.
The risk practitioner may be unfamiliar with recent application and process changes.
The risk practitioner may still have access rights to the financial system.
Participation in the risk assessment may constitute a conflict of interest.
Participation in the risk assessment may constitute a conflict of interest, because it may create a situation where the risk practitioner’s personal or professional interests or relationships interfere with their objectivity, independence, or impartiality in conducting the risk assessment. A conflict of interest is a type of risk that may compromise the integrity, quality, or validity of the risk assessment process and outcomes, and may damage the reputation or trust of the risk practitioner or the organization. A conflict of interest may arise when the risk practitioner has a direct or indirect connection or involvement with the subject or stakeholder of the risk assessment, such as a previous or current role, responsibility, or relationship, that may influence or bias theirjudgment or decision. Participation in the risk assessment may constitute a conflict of interest, as the risk practitioner may have a prior or residual interest or loyalty to the financial process team or the new critical application, and may not be able to assess the risk in a fair and unbiased manner.
The risk assessment team being overly confident of its ability to identify issues, the risk practitioner being unfamiliar with recent application and process changes, and the risk practitioner still having access rights to the financial system are all possible concerns with the request, but they are not the greatest concern, as they do not necessarily imply a conflict of interest, and they may be mitigated or resolved by other means, such as training, documentation, or review.
The number of tickets to rework application code has significantly exceeded the established threshold. Which of the following would be the risk practitioner s BEST recommendation?
Perform a root cause analysis
Perform a code review
Implement version control software.
Implement training on coding best practices
A root cause analysis is a process of identifying and understanding the underlying or fundamental causes or factors that contribute to or result in a problem or incident that has occurred or may occur in the organization. A root cause analysis can provide useful insights and solutions on the origin and nature of the problem or incident, and prevent or reduce its recurrence or impact.
Performing a root cause analysis is the risk practitioner’s best recommendation when the number of tickets to rework application code has significantly exceeded the established threshold, because it can help the organization to address the following questions:
Why did the application code require rework?
What were the errors or defects in the application code?
How did the errors or defects affect the functionality or usability of the application?
Who was responsible or accountable for the application code development and testing?
When and how were the errors or defects detected and reported?
What were the costs or consequences of the rework for the organization and its stakeholders?
How can the errors or defects be prevented or minimized in the future?
Performing a root cause analysis can help the organization to improve and optimize the application code quality and performance, and to reduce or eliminate the need for rework. It can also help the organization to align the application code development and testing with the organization’s objectives and requirements, and to comply with the organization’s policies and standards.
The other options are not the risk practitioner’s best recommendations when the number of tickets to rework application code has significantly exceeded the established threshold, because they do not address the main purpose and benefit of performing a root cause analysis, which is to identify and understand the underlying or fundamental causes or factors that contribute to or result in the problem or incident.
Performing a code review is a process of examining and evaluating the application code for its quality, functionality, and security, using the input and feedback from the peers, experts, or tools. Performing a code review can help the organization to identify and resolve the errors or defects in the application code, but it is not the risk practitioner’s best recommendation, because it does not indicate why the application code required rework, and how the errors or defects affected the organization and its stakeholders.
Implementing version control software is a process of using a software tool to manage and track the changes and modifications to the application code, and to ensure the consistency and integrity of the application code. Implementing version control software can help theorganization to control and monitor the application code development and testing, but it is not the risk practitioner’s best recommendation, because it does not indicate why the application code required rework, and how the errors or defects affected the organization and its stakeholders.
Implementing training on coding best practices is a process of providing and facilitating the learning and development of the skills and knowledge on the principles, guidelines, and standards for the application code development and testing. Implementing training on coding best practices can help the organization to enhance the competence and performance of the application code developers and testers, but it is not the risk practitioner’s best recommendation, because it does not indicate why the application code required rework, and how the errors or defects affected the organization and its stakeholders. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 40-41, 47-48, 54-55, 58-59, 62-63
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 189
CRISC Practice Quiz and Exam Prep
Calculation of the recovery time objective (RTO) is necessary to determine the:
time required to restore files.
point of synchronization
priority of restoration.
annual loss expectancy (ALE).
The recovery time objective (RTO) is a metric that defines the maximum acceptable time frame for restoring a system or service after a disruption. The RTO is determined by the business impact and requirements of the system or service, as well as the risk appetite and tolerance of the organization. The calculation of the RTO is necessary to determine the priority of restoration, which means the order and urgency of recovering the systems or services based on their criticality and dependency. The priority of restoration helps to optimize the use of resources and minimize the downtime and losses during a disaster recovery. The other options are not the correct answers, as they are not the main purpose of calculating the RTO. The time required to restore files is a factor that affects the RTO, but it is not the outcome of the RTO calculation. The point of synchronization is the point in time to which the data must be restored to ensure consistency and accuracy. The point of synchronization is related to the recovery point objective (RPO), not the RTO. The annual loss expectancy (ALE) is a measure of the expected loss per year due to a specific risk or threat. The ALE is calculated by multiplying the single loss expectancy (SLE) by the annualized rate of occurrence (ARO). The ALE is not directly related to the RTO, although it may influence the RTO determination. References = Recovery Time Objective (RTO) - What Is It, Examples, Calculation; CRISC Review Manual, pages 197-1981; CRISC Review Questions, Answers & Explanations Manual, page 842
Which of the following is the BEST metric to demonstrate the effectiveness of an organization's patch management process?
Average time to implement patches after vendor release
Number of patches tested prior to deployment
Increase in the frequency of patches deployed into production
Percent of patches implemented within established timeframe
The percent of patches implemented within established timeframe is the best metric to demonstrate the effectiveness of an organization’s patch management process, as it measures how well the organization meets its patching objectives and reduces its exposure to vulnerabilities. This metric reflects the timeliness, completeness, and quality of the patching process, and can be compared against the organization’s patch management policy and standards. A high percent of patches implemented within established timeframe indicates that the organization has a mature and efficient patch management process that minimizes the risk of security breaches or operational disruptions due to unpatched systems.
References:
•ISACA, Risk and Information Systems Control Review Manual, 7th Edition, 2020, p. 2501
•ISACA, Practical Patch Management and Mitigation2
•NIST, Guide to Enterprise Patch Management Planning3
Which of the following is MOST critical when designing controls?
Involvement of internal audit
Involvement of process owner
Quantitative impact of the risk
Identification of key risk indicators
The most critical factor when designing controls is the involvement of the process owner, who is the person responsible for the performance and outcomes of a business process. The process owner has the best knowledge and understanding of the process objectives, activities, inputs, outputs, resources, and risks. The process owner can provide valuable input and feedback on the design of controls that are relevant, effective, efficient, and aligned with the process goals. The process owner can also ensure that the controls are implemented, monitored, and improved as needed. The involvement of the process owner can also increase the acceptance and ownership of the controls by the process participants and stakeholders. The other options are less critical when designing controls. The involvement of internal audit can provide assurance and advice on the adequacy and effectiveness of the controls, but internal audit is not responsible for the design or implementation of the controls. The quantitative impact of the risk can help to prioritize and justify the controls, but it is not sufficient to determine the appropriate type and level of controls. The identification of key risk indicators can help to monitor and measure the risk and the performance of the controls, but it is not the main driver of the control design. References = Risk IT Framework, ISACA, 2022, p. 181
A risk practitioner is involved in a comprehensive overhaul of the organizational risk management program. Which of the following should be reviewed FIRST to help identify relevant IT risk scenarios?
Technology threats
IT assets
Security vulnerabilities
IT risk register
IT assets are the resources that support the organization’s business processes and objectives, such as hardware, software, data, and information. IT assets are the primary targets of IT risk, as they may be exposed to threats, vulnerabilities, and control deficiencies that could compromise their confidentiality, integrity, availability, or value. Therefore, identifying and classifying IT assets is the first step in developing relevant IT risk scenarios, as it helps to determine the scope, boundaries, and dependencies of the IT risk environment.
The other options are not the first things to review for identifying IT risk scenarios. Technology threats (A) are the potential sources of harm or damage to IT assets, such as natural disasters, cyberattacks, human errors, or sabotage. Technology threats are important to consider, but they are not the starting point for IT risk scenarios, as they depend on the context and characteristics of the IT assets. Security vulnerabilities © are the weaknesses or flaws in IT assets or controls that could be exploited by threats, such as outdated software, misconfigured systems, or insufficient encryption. Security vulnerabilities are also important to identify, but they are not the first thing to review, as they are specific to the IT assets and their configurations. IT risk register (D) is a document that records and tracks the identified IT risks, their analysis, evaluation, and response. IT risk register is a result of the IT risk assessment process, not an input to it.
Which of the following is the BEST key performance indicator (KPI) to measure the maturity of an organization's security incident handling process?
The number of security incidents escalated to senior management
The number of resolved security incidents
The number of newly identified security incidents
The number of recurring security incidents
A security incident handling process is a set of procedures and activities that aim to identify, analyze, contain, eradicate, recover from, and learn from security incidents that affect the confidentiality, integrity, or availability of information assets12.
The maturity of a security incident handling process is the degree to which the process is defined, managed, measured, controlled, and improved, and the extent to which it meets the organization’s objectives and expectations34.
The best key performance indicator (KPI) to measure the maturity of a security incident handling process is the number of recurring security incidents, which is the frequency or rate of security incidents that are repeated or reoccur after being resolved or closed56.
The number of recurring security incidents is the best KPI because it reflects the effectiveness and efficiency of the security incident handling process, and the ability of the process to prevent or reduce the recurrence of security incidents through root cause analysis, corrective actions, and continuous improvement56.
The number of recurring security incidents is also the best KPI because it is directly related to the organization’s objectives and expectations, such as minimizing the impact and cost of security incidents, enhancing the security posture and resilience of the organization, and complying with the relevant standards and regulations56.
The other options are not the best KPIs, but rather possible metrics that may support or complement the measurement of the maturity of the security incident handling process. For example:
The number of security incidents escalated to senior management is a metric that indicates the severity or complexity of security incidents, and the involvement or awareness of the senior management in the security incident handling process56. However, this metric doesnot measure the effectiveness or efficiency of the process, or the ability of the process to prevent or reduce security incidents56.
The number of resolved security incidents is a metric that indicates the output or outcome of the security incident handling process, and the performance or productivity of the security incident handling team56. However, this metric does not measure the quality or sustainability of the resolution, or the ability of the process to prevent or reduce security incidents56.
The number of newly identified security incidents is a metric that indicates the input or demand of the security incident handling process, and the capability or capacity of the security incident detection and identification mechanisms56. However, this metric does not measure the effectiveness or efficiency of the process, or the ability of the process to prevent or reduce security incidents56. References =
1: Computer Security Incident Handling Guide, NIST Special Publication 800-61, Revision 2, August 2012
2: ISO/IEC 27035:2016 Information technology — Security techniques — Information security incident management
3: Capability Maturity Model Integration (CMMI) for Services, Version 1.3, November 2010
4: COBIT 2019 Framework: Introduction and Methodology, ISACA, 2018
5: KPIs for Security Operations & Incident Response, SecurityScorecard Blog, June 7, 2021
6: Key Performance Indicators (KPIs) for Security Operations and Incident Response, DFLabs White Paper, 2018
Of the following, who should be responsible for determining the inherent risk rating of an application?
Application owner
Senior management
Risk practitioner
Business process owner
Inherent risk rating is a measure of the natural level of risk that is part of an application, before any controls are applied1. Inherent risk rating helps to identify and prioritize the applications that pose the highest risk to the organization and require the most attention and resources for risk management2. The responsibility for determining the inherent risk rating of an application should belong to the risk practitioner, as they have the expertise and knowledge to perform a comprehensive and consistent risk assessment of the application, using a standard methodology and criteria3. The risk practitioner should also communicate and report the inherent risk rating of the application to the relevant stakeholders, such as the application owner, senior management, and business process owner, and provide recommendations for risk mitigation4. The application owner, senior management, and business process owner are not the best choices for determining the inherent risk rating of an application, as they may not have the same level of skill and objectivity as the risk practitioner. The application owner is the person who has the authority and accountability for the application and its performance5. The application owner may be involved in providing input and feedback to the risk practitioner during the risk assessment process, but they may not be able to assess the inherent risk rating of the application independently and impartially, as they may have a vested interest in the application’s success and reputation6. Senior management is the group of executives who set the strategic direction and objectives of the organization and oversee its performance7. Senior management may be involved in approving and endorsing the risk assessment process and its results, but they may not be able to assess the inherent risk rating of the application in detail and depth, as they may have a broader and higher-level perspective of the organization’s risk profile and priorities8. The business process owner is the person who has the authority and accountability for a business process that is supported or enabled by the application. The business process owner may be involved in providing input and feedback to the risk practitioner during the risk assessment process, but they may not be able to assess the inherent risk rating of the application accurately and comprehensively, as they may have a limited and specific view of the application’s functionality and value. References = 2: Introduction toapplication risk rating & assessment | Infosec3: Application Security Risk: Assessment and Modeling - ISACA4: Risk and Information Systems Control Study Manual, Chapter 4: Risk and Control Monitoring and Reporting, Section 4.2: Risk Monitoring, pp. 189-191.1: Inherent Risk Rating - Shared Assessments - Third Party Risk Management5: [Application Owner - Gartner IT Glossary] 6: Perform Inherent Risk Analysis - Oracle7: [Senior Management - Definition, Roles and Responsibilities] 8: Rating Inherent and Residual Risk - Barn Owl : [Business Process Owner - Gartner IT Glossary] : [Business Process Owner - Roles and Responsibilities]
Which of the following would be the result of a significant increase in the motivation of a malicious threat actor?
Increase in mitigating control costs
Increase in risk event impact
Increase in risk event likelihood
Increase in cybersecurity premium
The result of a significant increase in the motivation of a malicious threat actor would be an increase in risk event likelihood. The likelihood of a risk event is influenced by the factors of threat, vulnerability, and exposure. The motivation of a threat actor is a key component of the threat factor, as it reflects the intent and capability of the actor to exploit a vulnerability. Therefore, a higher motivation would imply a higher probability of an attack. An increase in mitigating control costs, risk event impact, or cybersecurity premium are possible consequences of a risk event, but they are not directly affected by the motivation of the threat actor. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 6; CRISC Review Manual, 6th Edition, page 67.
Which of The following BEST represents the desired risk posture for an organization?
Inherent risk is lower than risk tolerance.
Operational risk is higher than risk tolerance.
Accepted risk is higher than risk tolerance.
Residual risk is lower than risk tolerance.
The best representation of the desired risk posture for an organization is when the residual risk is lower than the risk tolerance. Residual risk is the remaining risk after the implementation of risk responses or controls. Risk tolerance is the acceptable level of risk that the organization is willing to take or bear. Thedesired risk posture is when the organization has reduced the residual risk to a level that is equal to or lower than the risk tolerance, which means that the organization has achieved its risk objectives and is comfortable with the remaining risk exposure. The other options are not the best representation of the desired risk posture, as they indicate that the organization has not effectively managed its risk. Inherent risk is lower than risk tolerance means that the organization has not identified or assessed its risk properly, as inherent risk is the risk before any controls or responses are applied. Operational risk is higher than risk tolerance means that the organization has not implemented or monitored its risk responses or controls adequately, as operational risk is the risk of loss resulting from inadequate or failed internal processes, people, and systems. Accepted risk is higher than risk tolerance means that the organization has not aligned its risk appetite and risk tolerance, as accepted risk is the risk that the organization chooses to retain or take without any further action. References = Risk and Information Systems Control Study Manual, Chapter 2, Section 2.3.1, page 2-23.
Which of the following would BEST help an enterprise prioritize risk scenarios?
Industry best practices
Placement on the risk map
Degree of variances in the risk
Cost of risk mitigation
A risk map, also known as a risk heat map, is a visual tool that helps an enterprise prioritize risk scenarios by plotting them on a matrix based on their likelihood and impact. A risk map can help to compare and contrast different risk scenarios, as well as to identify the most critical and urgent risks that require attention. A risk map can also help to communicate and report the risk profile and status to the stakeholders and decision makers. Therefore, the placement on the risk map would best help an enterprise prioritize risk scenarios. The other options are not the best ways to help an enterprise prioritize risk scenarios, although they may be relevant and useful. Industry best practices are the standards or guidelines that are widely accepted and followed by the organizations in a specific industry or domain. Industry best practices can help to benchmark and improve the risk management process and performance, but they may not reflect the specific risk context and needs of the enterprise. Degree of variances in the risk is the measure of the variability or uncertainty of the risk, which may affect the accuracy or reliability of the risk assessment and response. Degree of variances in the risk can help to adjust and refine the risk analysis and treatment, but it may not indicate the priority or importance of the risk. Cost of risk mitigation is the amount of resources or expenses that are required or allocated to implement the risk response actions, such as avoiding, transferring, mitigating, or accepting the risk. Cost of risk mitigation can help to evaluate and optimize therisk response options, but it may not determine the priority or urgency of the risk. References = CRISC Review Manual, pages 38-391; CRISC Review Questions, Answers & Explanations Manual, page 892
Which of the following BEST protects an organization against breaches when using a software as a service (SaaS) application?
Control self-assessment (CSA)
Security information and event management (SIEM) solutions
Data privacy impact assessment (DPIA)
Data loss prevention (DLP) tools
Software as a service (SaaS) is a cloud computing model that provides software applications over the internet, without requiring the customer to install or maintain them on their own devices1. SaaS applicationscan offer many benefits, such as scalability, accessibility, and cost-efficiency, but they also pose security risks, such as data breaches, unauthorized access, and compliance violations2.
One of the best ways to protect an organization against breaches when using a SaaS application is to use data loss prevention (DLP) tools. DLP tools are software solutions that monitor, detect, and prevent the unauthorized transmission or leakage of sensitive data from an organization’s network or devices3. DLP tools can help an organization to:
Identify and classify sensitive data, such as personal information, intellectual property, or financial records, and apply appropriate policies and controls to protect them
Encrypt data in transit and at rest, and use secure protocols and encryption keys to ensure data confidentiality and integrity
Block or alert on suspicious or malicious data transfers, such as unauthorized uploads, downloads, or sharing of data to external sources or devices
Audit and report on data activities and incidents, and provide evidence for compliance with data protection regulations and standards, such as GDPR, HIPAA, or PCI-DSS4
References = What is SaaS?, Top 7 SaaS Security Risks (and How to Fix Them), What is Data Loss Prevention (DLP)?, Data Loss Prevention (DLP) for SaaS Applications
An organization has identified a risk exposure due to weak technical controls in a newly implemented HR system. The risk practitioner is documenting the risk in the risk register. The risk should be owned by the:
chief risk officer.
project manager.
chief information officer.
business process owner.
The business process owner should be the risk owner for the risk exposure due to weak technical controls in a newly implemented HR system, because they are responsible for the performance and outcomes of the HR business process, and they understand the business requirements, expectations, and impact of the HR system. The business process owner can also evaluate the trade-offs between the potential benefits and costs of the HR system, and the potential risks and consequences of a failure or breach of the system. The business process owner can also communicate and justify their risk acceptance or mitigation decision to the senior management and other stakeholders, and ensure that the risk is monitored and reviewed regularly. The other options are less appropriate to be the risk owner for this risk exposure. The chief risk officer is responsible for overseeing the enterprise-wide risk management framework and process, which includesensuring the identification, assessment, and reporting of risks. However, they are not the owner of the HR system or the HR business process, and they may not have the full knowledge or authority to accept or mitigate the risk on behalf of the business. The project manager is responsible for managing the implementation of the HR system, which includes ensuring the delivery of the system within the scope, time, and budget constraints. However, they are not the owner of the HR system or the HR business process, and they may not have the full knowledge or authority to accept or mitigate the risk on behalf of the business. The chief information officer is responsible for managing the IT function and resources, which includes providing the technical support and security for the HR system. However, they are not the owner of the HR system or the HR business process, and they may not have the full knowledge or authority to accept or mitigate the risk on behalf of the business. References = Getting risk ownership right 1
A trusted third-party service provider has determined that the risk of a client's systems being hacked is low. Which of the following would be the client's BEST course of action?
Perform their own risk assessment
Implement additional controls to address the risk.
Accept the risk based on the third party's risk assessment
Perform an independent audit of the third party.
A risk assessment is a process that identifies, analyzes, and evaluates the risks that an organization faces in relation to its objectives, assets, and operations. A risk assessment helps to determine the likelihood and impact of potential threats, as well as the adequacy and effectiveness of existing controls. A risk assessment also provides the basis for risk treatment, which involves selecting and implementing the appropriate risk responses, such as avoiding, transferring, mitigating, or accepting the risk. The client’s best course of action in this scenario is to perform their own risk assessment, rather than relying on the third-party service provider’s risk assessment. This is because the third-party service provider may have different risk criteria, assumptions, methods, or perspectives than the client, and may not fully understand or address the client’s specific risk context, needs, and expectations. The third-party service provider’s risk assessment may also be biased, outdated, or inaccurate, and may not reflect the current or future risk environment. By performing their own risk assessment, the client can ensure that the risk of their systems being hacked is properly identified, measured, and managed, and that the risk level is acceptable and aligned with their risk appetite and tolerance. The other options are not the best courses of action for the client, as they may expose the client to unnecessary or unacceptable risk. Implementing additional controls to address the risk may be costly, ineffective, or redundant, and may not be justified by the actual risk level. Accepting the risk based on the third-party service provider’s risk assessment may be risky, as the client may not have a clear or accurate understanding of the risk exposure or consequences. Performing an independent audit of the third party may be useful, but it may not be sufficient or timely to assess and address the risk of the client’s systems being hacked. References = CRISC Review Manual, pages 38-391; CRISC Review Questions, Answers & Explanations Manual, page 792
Which of the following will BEST ensure that controls adequately support business goals and objectives?
Using the risk management process
Enforcing strict disciplinary procedures in case of noncompliance
Reviewing results of the annual company external audit
Adopting internationally accepted controls
Using the risk management process will best ensure that controls adequately support business goals and objectives, as it involves identifying, assessing, responding, and monitoring the risks that may affect the achievement of the business goals and objectives, and designing and implementing controls to mitigate those risks. Enforcing strict disciplinary procedures in case of noncompliance, reviewing results of the annual company external audit, and adopting internationally accepted controls are also good practices, but they are not the best, as they do not necessarily align the controls with the business goals and objectives. References = CRISC Review Manual, 7th Edition, page 146.
Which of the following is the MOST important benefit of key risk indicators (KRIs)'
Assisting in continually optimizing risk governance
Enabling the documentation and analysis of trends
Ensuring compliance with regulatory requirements
Providing an early warning to take proactive actions
The most important benefit of key risk indicators (KRIs) is providing an early warning to take proactive actions, because this helps organizations to prevent or mitigate potential risks that may impact their operations, objectives, or performance. KRIs are specific metrics that measure the level and impact of risks, and provide timely signals that something may be going wrong or needs urgent attention. By monitoring and analyzing KRIs, organizations can identify and assess emerging or existing risks, and initiate appropriate risk responses before the risks escalate into significant issues. This can enhance the organization’s resilience, competitiveness, and value creation. The other options are less important benefits of KRIs. Assisting in continually optimizing risk governance is a benefit of KRIs, but it is not the most important one. Risk governance is the framework and process that defines how an organization manages its risks, including the roles, responsibilities, policies, and standards. KRIs can help to evaluate and improve the effectiveness and efficiency of risk governance, but they are not the only factor that influences it. Enabling the documentation and analysis of trends is a benefit of KRIs, but it is not the most important one. Documenting and analyzingtrends can help organizations to understand the patterns, causes, and consequences of risks, and to learn from their experiences. However, this benefit is more relevant for historical or retrospective analysis, rather than for proactive action. Ensuring compliance with regulatory requirements is a benefit of KRIs, but it is not the most important one. Compliance is the adherence to the laws, regulations, and standards that apply to an organization’s activities and operations. KRIs can help to monitor and demonstrate compliance, but they are not the only tool or objective for doing so. References = Why Key Risk Indicators Are Important for Risk Management 1
Which of the following is MOST important to review when evaluating the ongoing effectiveness of the IT risk register?
The costs associated with mitigation options
The status of identified risk scenarios
The cost-benefit analysis of each risk response
The timeframes for risk response actions
The status of identified risk scenarios, because it helps to monitor and track the current level and direction of the IT risks, and to determine whether the risk responses and controls are adequate and effective. An IT riskregister is a document that records and tracks the key IT risks that an organization faces, along with their likelihood, impact, and response strategies. An IT risk scenario is a hypothetical situation or event that describes the source, cause, consequence, and impact of an IT risk. The status of identified risk scenarios is the most important factor, as it reflects the actual and potential outcomes of the IT risks, and the performance and progress of the risk management process. The costs associated with mitigation options, the cost-benefit analysis of each risk response, and the timeframes for risk response actions are all possible factors to review when evaluating the ongoing effectiveness of the IT risk register, but they are not the most important factor, as they do not directly measure and report the status of the IT risk scenarios.
A data processing center operates in a jurisdiction where new regulations have significantly increased penalties for data breaches. Which of the following elements of the risk register is MOST important to update to reflect this change?
Risk impact
Risk trend
Risk appetite
Risk likelihood
Risk impact is the potential loss or damage that a risk event can cause to an organization. Risk impact can be expressed in qualitative or quantitative terms, such as financial, reputational, operational, or legal. A risk register is a tool that records and tracks the key information about the identified risks, such as their description, likelihood, impact, response, and status. A risk register helps an organization to monitor and manage its risks effectively and efficiently. When there is a change in the external or internal environment that affects the organization’s risks, such as new regulations, the risk register should be updated to reflect this change. The most important element of the risk register to update in this case is the risk impact, because the new regulations have significantly increased the penalties for data breaches, which means that the potential loss or damage that a data breach can cause to the organization has also increased. By updating the risk impact, the organization can reassess the severity and priority of the data breach risk, and adjust its risk response accordingly. The other elements of the risk register are less important to update in this case. The risk trend shows the direction and rate of change of the risk over time, which may or may not be affected by the new regulations. The risk appetite is the amount and type of risk that the organization is willing to accept in pursuit of its objectives, which is unlikely to change due to the new regulations. The risk likelihood is the probability of a risk event occurring, which is also independent of the new regulations. References = Risk IT Framework, ISACA, 2022, p. 131
An organization practices the principle of least privilege. To ensure access remains appropriate, application owners should be required to review user access rights on a regular basis by obtaining:
business purpose documentation and software license counts
an access control matrix and approval from the user's manager
documentation indicating the intended users of the application
security logs to determine the cause of invalid login attempts
The best way to ensure that access remains appropriate for an organization that practices the principle of least privilege is to review user access rights on a regular basis by obtaining an access control matrix and approval from the user’s manager. An access control matrix is a table that shows the access rights and permissions of each user or role for each resource or function. An access control matrix helps to verify that the users have the minimum level of access required to perform their duties, and to identify any unauthorized or excessive access rights. Approval from the user’s manager helps to confirm that the user’s access rights are consistent with their current role and responsibilities, and to authorize any changes or exceptions as needed. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 3, Section 3.2.2, page 1281
Which of the following would be the GREATEST challenge when implementing a corporate risk framework for a global organization?
Privacy risk controls
Business continuity
Risk taxonomy
Management support
The greatest challenge when implementing a corporate risk framework for a global organization is the management support. A corporate risk framework is a set of principles, policies, standards, and processes that guide and govern the risk management activities across the organization. A corporate risk framework helps to establish a consistent and integrated approach to risk management, and to align the risk management objectives and strategies with the business goals and values. Implementing a corporate risk framework for a global organization requires the management support, which is the commitment, involvement, and endorsement of the senior management and the board. Management support is essential for providing the vision, direction, and resources for the risk management initiatives, and for ensuring the accountability, responsibility, and ownership of the risk management roles and functions. Management support is also critical for creating and sustaining a risk-aware culture, and for promoting the risk management awareness and communication among the stakeholders. Management support can be challenging to obtain and maintain, especially for a global organization, as it may face various barriers, such as different expectations, priorities, preferences, or perspectives of the management, lack of trust or confidence in the risk management value or performance, resistance to change or innovation, or competing interests or agendas. Privacy risk controls, business continuity, and risk taxonomy are not as challenging as management support, as they are the components or outcomes of the corporate risk framework, andthey can be addressed or improved by applying the appropriate methods, techniques, or tools. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 35.
Key risk indicators (KRIs) are MOST useful during which of the following risk management phases?
Monitoring
Analysis
Identification
Response selection
Key risk indicators (KRIs) are most useful during the monitoring phase of the risk management process, as they provide timely and relevant information on the current and future risk status and performance. KRIs are metrics that measure the level of risk exposure and the effectiveness of risk response strategies, and they have predefined thresholds that indicate the acceptable or unacceptable risk status. By monitoring the KRIs, the risk practitioner can identify and report any changes or deviations in the risk level, and take appropriate actions to manage the risk. KRIs are not most useful during the analysis, identification, or response selection phases, as they do not help to assess the likelihood or impact of the risk, to find the sources or causes of the risk, or to evaluate or choose the optimal risk response option. References = CRISC: Certified in Risk & Information Systems Control Sample Questions, question 222.
Which of the following should be the FIRST step when a company is made aware of new regulatory requirements impacting IT?
Perform a gap analysis.
Prioritize impact to the business units.
Perform a risk assessment.
Review the risk tolerance and appetite.
New regulatory requirements impacting IT are those that impose new obligations, restrictions, or standards on how an organization uses, manages, or secures its IT systems, data, or services1. Examples of such regulations include the GDPR, the CCPA, the HIPAA, or the PCI-DSS2. New regulatory requirements impacting IT can pose significant challenges and risks for an organization, such as:
Compliance costs and efforts, such as updating policies, procedures, and systems, training staff, or hiring experts
Noncompliance penalties and consequences, such as fines, lawsuits, sanctions, or reputational damages
Operational disruptions or inefficiencies, such as system changes, data migrations, or service interruptions
Competitive disadvantages or opportunities, such as losing or gaining customers, partners, or markets3
The first step that should be done when a company is made aware of new regulatory requirements impacting IT is to review the risk tolerance and appetite. Risk tolerance is the acceptable level of variation that an organization is willing to accept around its risk appetite. Risk appetite is the amount and type of risk that an organization is willing to take in order to meet its strategic objectives. By reviewing the risk tolerance and appetite, the company can:
Establish a clear and consistent understanding of the organization’s goals, values, and expectations regarding the new regulatory requirements impacting IT
Assess the current and potential impacts of the new regulatory requirements impacting IT on the organization’s performance, operations, or assets
Determine the level of risk exposure and acceptance that the organization is comfortable with, and identify the risk thresholds or limits that should not be exceeded
Align the risk management strategies and actions with the organization’s risk tolerance and appetite, and prioritize the most critical and urgent risks to be addressed
Communicate and report the risk tolerance and appetite to the stakeholders and regulators, and ensure transparency and accountability
References = Regulating emerging technology | Deloitte Insights, Ten Key Regulatory Challenges of 2024 - kpmg.com, The Risks of Non-Compliance with Data Protection Laws, [Risk Tolerance - COSO], [Risk Appetite - COSO], [Risk Appetite and Tolerance - IRM]
The BEST way to mitigate the high cost of retrieving electronic evidence associated with potential litigation is to implement policies and procedures for.
data logging and monitoring
data mining and analytics
data classification and labeling
data retention and destruction
The best way to mitigate the high cost of retrieving electronic evidence associated with potential litigation is to implement policies and procedures for data retention and destruction. Data retention and destruction policies and procedures define the criteria, methods, and schedules for retaining and disposing of electronic data. They help to ensure that the electronic data is stored, managed, and deleted in a consistent, secure, and compliant manner. They also help to reduce the volume, complexity, and cost of retrieving electronic evidence, as they limit the scope, duration, and frequency of the data preservation and discovery process. The other options are not as effective as data retention and destruction policies and procedures, as they are related to the collection, analysis, or classification of electronic data, not the retention or destruction of electronic data. References = Risk and Information Systems Control Study Manual, Chapter 3: IT Risk Response, Section 3.3: IT Risk Response Implementation, page 145.
Which risk response strategy could management apply to both positive and negative risk that has been identified?
Transfer
Accept
Exploit
Mitigate
Accepting risk is the only risk response strategy that could be applied to both positive and negative risk that has been identified. Accepting risk means taking no action to change the likelihood or impact of the risk, but being prepared to deal with the consequences if the risk occurs. Accepting risk is usually chosen when the risk is low, unavoidable, or outweighed by the benefits. For positive risks, accepting risk means taking advantage of the opportunities if they arise. For negative risks, accepting risk means setting aside contingency reserves or plans to cope with the threats. The other risk response strategies are specific to either positive or negative risks. Transfer, exploit, and mitigate are strategies for negative risks, while share, enhance, and avoid are strategies for positive risks. References = Risk and Information Systems Control Study Manual, Chapter 4, Section 4.3.1, page 4-23.
Which of the following provides the MOST reliable evidence of a control's effectiveness?
A risk and control self-assessment
Senior management's attestation
A system-generated testing report
detailed process walk-through
The most reliable evidence of a control’s effectiveness is a system-generated testing report. A system-generated testing report is a document that shows the results of automated tests performed by the system to verify that the control is functioning as intended and producing the expected outcomes. A system-generated testing report is reliable, because it is objective, consistent, accurate, and timely, and because it can provide a high level of assurance and confidence in the control’s effectiveness. The other options are not as reliable as a system-generated testing report, although they may provide some evidence of the control’s effectiveness. A risk and control self-assessment, senior management’s attestation, and a detailed process walk-through are all examples of manual or subjective evidence, which may be prone to errors, biases, or inconsistencies, and which may provide a lower level of assurance and confidence in the control’s effectiveness. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.4.1, page 3-32.
An organization recently implemented an automated interface for uploading payment files to its banking system to replace manual processing. Which of the following elements of the risk register is MOST appropriate for the risk practitioner to update to reflect the improved control?
Risk scenarios
Risk ownership
Risk impact
Risk likelihood
Updating the risk likelihood in the risk register is appropriate when an improved control, such as an automated interface, is implemented. This change affects the probability of the risk occurring, thus reflecting the enhanced control environment.
Which of the following is MOST useful when performing a quantitative risk assessment?
RACI matrix
Financial models
Management support
Industry benchmarking
Which of the following is MOST important requirement to include in a Software as a Service (SaaS) vendor contract to ensure data is protected?
The vendor must provide periodic independent assurance reports.
The vendor must host data in a specific geographic location.
The vendor must be held liable for regulatory fines for failure to protect data.
The vendor must participate in an annual vendor performance review.
The vendor must host data in a specific geographic location to ensure that the data is protected by the applicable data protection laws of the EU or the country where the data originates. This is especially important for SaaS customers who transfer personal data from the EU to third countries, as they need to comply with the GDPR and the new Standard Contractual Clauses (SCCs) that regulate such transfers. The vendor must also provide adequate security measures and guarantees to protect the data from unauthorized access, disclosure, or loss. References = Risk and Information Systems Control Study Manual, Chapter 5: IT Risk Mitigation, Section 5.3: IT Risk Mitigation Strategies and Approaches, Page 253; Data Protection – New EU Standard Contractual Clauses - Bodle Law.
Which of the following is the BEST way to validate whether controls to reduce user device vulnerabilities have been implemented according to management's action plan?
Survey device owners.
Rescan the user environment.
Require annual end user policy acceptance.
Review awareness training assessment results
The best way to validate whether controls to reduce user device vulnerabilities have been implemented according to management’s action plan is to rescan the user environment, as it provides an objective and reliable way to measure and verify the effectiveness and adequacy of the controls, and to detect any remaining or new vulnerabilities. Surveying device owners, requiring annual end user policy acceptance, and reviewing awareness training assessment results are not the best ways, as they may not provide sufficient assurance, evidence, or timeliness of the control validation, respectively. References = CRISC Review Manual, 7th Edition, page 154.
Which types of controls are BEST used to minimize the risk associated with a vulnerability?
Detective
Preventive
Deterrent
Directive
Preventive controls are the best types of controls to minimize the risk associated with a vulnerability, because they aim to avoid or reduce the occurrence of a threat or an exploit. Preventive controls can include physical, technical, or administrative measures, such as locks, firewalls, encryption, policies, training, or backup. Preventive controls can also involve eliminating or substituting the source of the vulnerability, such as outdated software or hardware.
References
•ISACA CRISC Review Manual, 7th Edition, Domain 3: Risk Response, Section 3.2.1: Control Types
•Hazard Controls - Princeton University
•Risk Control | Techniques and Importance of Risk Control - EDUCBA
A risk register BEST facilitates which of the following risk management functions?
Analyzing the organization's risk appetite
Influencing the risk culture of the organization
Reviewing relevant risk scenarios with stakeholders
Articulating senior management's intent
Purpose of a Risk Register:
A risk register consolidates all identified risks, their status, and mitigation actions in one place. It serves as a tool for tracking and managing risks systematically.
Facilitating Risk Management Functions:
By documenting risk scenarios, a risk register provides a comprehensive view of potential threats and their impact on the organization.
It enables effective communication and review of these scenarios with stakeholders, ensuring that all relevant parties are aware of and understand the risks.
Engaging Stakeholders:
Reviewing the risk register with stakeholders helps in validating the risks, assessing their impact, and determining appropriate responses.
It fosters collaboration and ensures that risk management activities are aligned with the stakeholders' expectations and the organization's objectives.
Comparing Other Functions:
Analyzing Risk Appetite:While important, this is not the primary function of a risk register.
Influencing Risk Culture:The risk register contributes to risk culture but is primarily a tracking and communication tool.
Articulating Senior Management's Intent:This is more related to policy and strategy documents, whereas the risk register is a practical tool for managing specific risks.
References:
The CRISC Review Manual highlights the role of the risk register in consolidating risk information and facilitating stakeholder engagement (CRISC Review Manual, Chapter 2: IT Risk Assessment, Section 2.6 Risk Register) .
Which of the following would MOST likely cause a risk practitioner to change the likelihood rating in the risk register?
Risk appetite
Control cost
Control effectiveness
Risk tolerance
The likelihood rating in the risk register is a measure of how probable it is that a risk event will occur, given the current conditions and controls. The risk practitioner should change the likelihood rating if there is a significant change in the effectiveness of the controls that are implemented to prevent or reduce the risk. For example, if a control becomes obsolete, ineffective, or bypassed, the likelihood rating should increase, as the risk event becomes more likely to happen. Conversely, if a control becomes more efficient, reliable, or robust, the likelihood rating should decrease, as the risk event becomes less likely to happen. The other options are not likely to cause a change in the likelihood rating, as they are not directly related to the probability of the risk event. Risk appetite is the amount of risk that an organization is willing to accept in pursuit of its objectives. Control cost is the amount of resources that are required to implement and maintain a control. Risk tolerance is the acceptable level of variation that an organization is willing to allow for a risk to deviate from its desired level or expected outcome. These factors may influence the risk response or the risk acceptance, but not the likelihood rating. References = Risk and Information Systems Control Study Manual, Chapter 1: IT Risk Identification, Section 1.4: Risk Register, p. 25-26.
Senior management has requested more information regarding the risk associated with introducing a new application into the environment. Which of the following should be done FIRST?
Perform an audit.
Conduct a risk analysis.
Develop risk scenarios.
Perform a cost-benefit analysis.
Understanding Risk Analysis:
Risk analysis involves identifying potential risks associated with a new application and assessing their likelihood and impact on the organization.
It provides a detailed understanding of the potential threats, vulnerabilities, and consequences, enabling informed decision-making.
Steps in Conducting a Risk Analysis:
Identify Risks:Determine what risks could arise from the new application, including security vulnerabilities, compliance issues, and operational disruptions.
Assess Risks:Evaluate the likelihood and impact of each identified risk. This includes both qualitative and quantitative assessments.
Prioritize Risks:Rank the risks based on their assessed impact and likelihood to focus on the most significant threats first.
Importance of Risk Analysis:
Provides senior management with a comprehensive view of the risks involved, enabling them to make informed decisions about proceeding with the application.
Helps in developing mitigation strategies to address the identified risks.
Comparing Other Options:
Perform an Audit:Audits are useful for evaluating existing controls but are not the first step in assessing risks for a new application.
Develop Risk Scenarios:This is part of the risk analysis process but comes after identifying and assessing risks.
Perform a Cost-Benefit Analysis:Important for decision-making but follows the initial risk analysis to understand potential impacts.
References:
The CRISC Review Manual emphasizes the importance of conducting a risk analysis to understand and manage risks associated with new applications (CRISC Review Manual, Chapter 2: IT Risk Assessment, Section 2.2.1 Conducting Risk Analysis).
Which of the following has the GREATEST positive impact on ethical compliance within the risk management process?
Senior management demonstrates ethics in their day-to-day decision making.
An independent ethics investigation team has been established.
Employees are required to complete ethics training courses annually.
The risk practitioner is required to consult with the ethics committee.
According to the ISACA Risk IT Framework, one of the key principles for effective risk management is to establish tone at the top and accountability. This means that senior management should set an example of ethical behavior and culture, and communicate the importance of ethics and compliance to the entire organization. Senior management should also ensure that the risk management process is aligned with the organization’s mission, vision, values, and code of conduct, and that ethical risks are identified, assessed, and treated appropriately. By demonstrating ethics in their day-to-day decision making, senior management can have the greatest positive impact on ethical compliance within the risk management process, as they can influence the attitudes, behaviors, and actions of all stakeholders.
References:
•ISACA, Risk IT Framework, 2nd Edition, 2019, p. 741
•ISACA, The Role of Ethics in Risk Management2
Which of the following is the BEST key performance indicator (KPI) to measure how effectively risk management practices are embedded in the project management office (PMO)?
Percentage of projects with key risk accepted by the project steering committee
Reduction in risk policy noncompliance findings
Percentage of projects with developed controls on scope creep
Reduction in audits involving external risk consultants
The percentage of projects with developed controls on scope creep is the best key performance indicator (KPI) to measure how effectively risk management practices are embedded in the project management office (PMO), as it reflects the ability of the PMO to identify, assess, and respond to the risk of project scope changes that may affect the project objectives, budget, and schedule. The other options are not the best KPIs, as they do not directly measure the effectiveness of risk management practices in the PMO, but rather the outcomes or consequences of risk management decisions. References = CRISC Review Manual, 7th Edition, page 110.
A risk assessment has revealed that the probability of a successful cybersecurity attack is increasing. The potential loss could exceed the organization's risk appetite. Which of the following ould be the MOST effective course of action?
Re-evaluate the organization's risk appetite.
Outsource the cybersecurity function.
Purchase cybersecurity insurance.
Review cybersecurity incident response procedures.
Cybersecurity incident response procedures are the plans and actions that an organization takes to respond to and recover from a cybersecurity attack. They include identifying the source and scope of the attack, containing and eradicating the threat, restoring normal operations, and analyzing the root cause and lessons learned. Reviewing cybersecurity incident response procedures is the most effective course of action when the probability of a successful cybersecurity attack is increasing and the potential loss could exceed the organization’s risk appetite, as it helps to prepare the organization for minimizing the impact and duration of the attack, as well as improving the resilience and security posture of the organization.
In order to determining a risk is under-controlled the risk practitioner will need to
understand the risk tolerance
monitor and evaluate IT performance
identify risk management best practices
determine the sufficiency of the IT risk budget
To determine if a risk is under-controlled, the risk practitioner will need to understand the risk tolerance. Risk tolerance is the acceptable or allowable level of variation or deviation from the expected or desired outcomes or objectives. Risk tolerance reflects the amount and type of risk that the organization is willing and able to take. A risk is under-controlled when the risk exposure exceeds the risk tolerance, meaning that the organization is taking on more risk than it can handle or afford. Therefore, the risk practitioner will need to understand the risk tolerance to compare it with the risk exposure and identify the gap or difference. The other options are not as relevant as understanding the risk tolerance, as they are related to the monitoring, identification, or determination of the risk or the IT performance, not the comparison or evaluation of the risk. References = Risk and Information Systems Control Study Manual, Chapter 2: IT Risk Assessment, Section 2.4: IT Risk Response, page 87.
In an organization with a mature risk management program, which of the following would provide the BEST evidence that the IT risk profile is up to date?
Risk questionnaire
Risk register
Management assertion
Compliance manual
A risk register is a tool that records and tracks the risks that may affect the organization, as well as the actions that are taken or planned to manage them1. A risk register provides the best evidence that the IT risk profile is up to date, because it reflects the current and potential IT risks that the organization faces, as well as their likelihood, impact, severity, owner, status, and response2. An IT risk profile is a document that describes the types, amounts, and priority of IT risk that the organization finds acceptable and unacceptable3. An IT risk profile is developed collaboratively with various stakeholders within the organization, including business leaders, data and process owners, enterprise risk management, internal and external audit, legal, compliance, privacy, and IT risk management and security4. By maintaining and updating the risk register regularly, the organization can ensure that the IT risk profile is aligned with the changing IT risk environment, and that the IT risk management activities and performance are consistent and effective. The other options are not the best evidence that the IT risk profile is up to date, as they are either less comprehensive or less relevant than the risk register. A risk questionnaire is a tool that collects and analyzes the opinions and perceptions of the stakeholders about the risks that may affect the organization5. A risk questionnaire can help to identify and assess the risks, as well as to communicate and report on the risk status and issues. However, a risk questionnaire is not the best evidence that the IT risk profile is up to date, as it may not capture all the IT risks that the organization faces, or reflect the actual or objective level and nature of the IT risks. A management assertion is a statement or declaration made by the management about the accuracy and completeness of the information or data that they provide or report. A management assertion can help to increase the confidence and trust of the stakeholders and auditors in the information or data, as well as to demonstrate the accountability and responsibility of the management. However, a management assertion is not the best evidence that the IT risk profile is up to date, as it does not provide the details or outcomes of the IT risk management activities or performance, or verify the validity and reliability of the IT risk information or data. A compliance manual is a document that contains the policies, procedures, and standards that the organization must follow to meet the legal, regulatory, or contractual requirements that apply to its activities or operations. A compliance manual can help to ensure the quality and consistency of the organization’s compliance activities or performance, as well as to avoid or reduce the penalties or sanctions for non-compliance. However, a compliance manual is not the best evidence that the IT risk profile is up to date, as it does not address the IT risks that the organization faces, or the IT risk management activities or performance. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.1.5, Page 55.
Print jobs containing confidential information are sent to a shared network printer located in a secure room. Which of the following is the BEST control to prevent the inappropriate disclosure of confidential information?
Requiring a printer access code for each user
Using physical controls to access the printer room
Using video surveillance in the printer room
Ensuring printer parameters are properly configured
The best control to prevent the inappropriate disclosure of confidential information when print jobs containing confidential information are sent to a shared network printer located in a secure room is to require a printer access code for each user. A printer access code is a unique and secret code that the user needs to enter on the printer device to release and retrieve the print job. Requiring a printer access code for each user is the best control, as it helps to prevent or limit the unauthorized access, viewing, or copying ofthe confidential information on the print job, especially if the print job is left unattended or forgotten on the printer device. Requiring a printer access code for each user also helps to ensure the accountability and traceability of the user who sent the print job, and to support the audit and monitoring of the printer activity. Using physical controls to access the printer room, using video surveillance in the printer room, and ensuring printer parameters are properly configured are also useful controls, but they are not as effective as requiring a printer access code for each user, as they do not directly prevent or limit the inappropriate disclosure of confidential information on the print job, and they may not deter or detect the unauthorized access or misuse of the print job by the authorized users who have access to the printer room or device. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 217.
Participants in a risk workshop have become focused on the financial cost to mitigate risk rather than choosing the most appropriate response. Which of the following is the BEST way to address this type of issue in the long term?
Perform a return on investment analysis.
Review the risk register and risk scenarios.
Calculate annualized loss expectancy of risk scenarios.
Raise the maturity of organizational risk management.
The maturity of organizational risk management refers to the degree to which risk management is embedded and integrated into the organization’s culture, processes, and decision-making1. A higher level of maturity implies that the organization has a clear and consistent understanding of its risk appetite and tolerance, and that it can effectively identify, assess, respond, monitor, and communicate risks2.
The best way to address the issue of participants focusing on the financial cost to mitigate risk rather than choosing the most appropriate response is to raise the maturity of organizational risk management. This can help to:
Ensure that risk management is aligned with the organization’s strategic objectives and values, and that risk responses are based on the potential impact and likelihood of risks, not just on the cost of mitigation
Foster a risk-aware culture that encourages proactive and collaborative risk management, and that recognizes and rewards good risk management practices
Provide adequate training and guidance for risk management roles and responsibilities, and ensure that risk management skills and competencies are developed and maintained
Implement a robust and consistent risk management framework, methodology, and tools that support the risk management process and enable continuous improvement and learning
Enhance the quality and reliability of risk information and reporting, and ensure that risk management performance and outcomes are measured and evaluated3
References = Risk Maturity Model - Wikipedia, Risk Maturity Model - ISACA, Risk Maturity Model - IRM
Which of the following is the MOST important consideration when selecting key risk indicators (KRIs) to monitor risk trends over time?
Ongoing availability of data
Ability to aggregate data
Ability to predict trends
Availability of automated reporting systems
Ongoing availability of data is the most important consideration when selecting key risk indicators (KRIs) to monitor risk trends over time, as it ensures that the KRIs can provide timely and reliable information on the current and future risk status and performance. KRIs are metrics that measure the level of risk exposureand the effectiveness of risk response strategies, and they should be aligned with the enterprise’s risk appetite and objectives. Ongoing availability of data means that the data sources and collection methods for the KRIs are consistent, accessible, and sustainable, and that the data quality and integrity are maintained and verified. Ability to aggregate data, ability to predict trends, and availability of automated reporting systems are not the most important considerations, as they do not affect the validity and usefulness of the KRIs, but rather the presentation and analysis of the KRI data. References = CRISC Certified in Risk and Information Systems Control – Question213; ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 213.
To communicate the risk associated with IT in business terms, which of the following MUST be defined?
Compliance objectives
Risk appetite of the organization
Organizational objectives
Inherent and residual risk
According to the CRISC Review Manual, risk appetite is the amount and type of risk that an organization is willing to accept in pursuit of its objectives. Risk appetite is a key factor in communicating the risk associated with IT in business terms, because it helps to align the IT risk management with the business strategy and goals. Risk appetite also helps to define the risk tolerance and thresholds, which are the acceptable levels of variation around the objectives. The other options are not the correct answers, because they are not essential for communicating the risk associated with IT in business terms. Compliance objectives are the objectives that an organization must achieve to comply with the applicable laws, regulations, standards, and contracts. Organizational objectives are the objectives that an organization sets to achieve its mission, vision, and values. Inherent and residual risk are the risk levels before and after applying the risk responses, respectively. References = CRISC Review Manual, 7th Edition, Chapter 2, Section 2.1.1, page 66.
Which of the following is the MOST critical element to maximize the potential for a successful security implementation?
The organization's knowledge
Ease of implementation
The organization's culture
industry-leading security tools
According to the CRISC Review Manual, the organization’s culture is the most critical element to maximize the potential for a successful security implementation, because it influences the behavior, attitude, and perception of the stakeholders towards security. The organization’s culture includes the values, beliefs, norms, and practices that are shared by the members of the organization. A positive and supportive culture can foster the awareness, commitment, and collaboration of the stakeholders in achieving the security objectives and complying with the security policies and standards. The other options are not the most critical elements, as they are less influential or less challenging than the organization’s culture. The organization’s knowledge is the collective understanding and expertise of the organization regardingsecurity, which can be enhanced through training and education. Ease of implementation is the degree of difficulty and complexity of implementing security, which can be reduced by using appropriate methods and tools. Industry-leading security tools are the best-in-class solutions and technologies that can provide effective and efficient security, which can be acquired through market research and evaluation. References = CRISC Review Manual, 7th Edition, Chapter 1, Section 1.3.1, page 32.
Which of the following is MOST important when developing risk scenarios?
Reviewing business impact analysis (BIA)
Collaborating with IT audit
Conducting vulnerability assessments
Obtaining input from key stakeholders
The most important factor when developing risk scenarios is obtaining input from key stakeholders. A risk scenario is a description of a possible event or situation that could affect the enterprise’s objectives, processes, or resources. Obtaining input from key stakeholders, such as business owners, process owners, subject matter experts, or external parties, helps to ensure that the risk scenarios are realistic, relevant, and comprehensive. It also helps to identify the sources, drivers, indicators, likelihood, impact, and responses of the risk scenarios, and to align them with the enterprise’s risk appetite and tolerance. Obtaining input from key stakeholders also fosters a collaborative and participatory approach to risk management, and enhances the risk awareness and ownership among the stakeholders. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.1.3, page 621
Winch of the following can be concluded by analyzing the latest vulnerability report for the it infrastructure?
Likelihood of a threat
Impact of technology risk
Impact of operational risk
Control weakness
A vulnerability report for the IT infrastructure is a document that identifies and evaluates the weaknesses or gaps in the IT systems, networks, or devices that could be exploited by threats or cause incidents. By analyzing the latest vulnerability report, one can conclude the existence and extent of control weaknesses in the IT infrastructure, because control weaknesses are the deficiencies or failures of the controls that are supposed to prevent, detect, or correct the vulnerabilities. The other options are not the correct answers, because they are not directly concluded by analyzing the latest vulnerability report. The likelihood of a threat, the impact of technology risk, and the impact of operational risk are examples of risk factors or consequences that depend on the vulnerability and the threat, but they are not determined by the vulnerability report alone. References = CRISC: Certified in Risk & Information Systems Control Sample Questions
An IT risk practitioner has been asked to regularly report on the overall status and effectiveness of the IT risk management program. Which of the following is MOST useful for this purpose?
Balanced scorecard
Capability maturity level
Internal audit plan
Control self-assessment (CSA)
A balanced scorecard is a strategic management tool that helps to measure and communicate the performance of an organization or a program against its goals and objectives. A balanced scorecard typicallyconsists of four perspectives: financial, customer, internal process, and learning and growth. Each perspective has a set of key performance indicators (KPIs) that reflect the critical success factors and desired outcomes of the organization or the program1.
A balanced scorecard is most useful for reporting on the overall status and effectiveness of the IT risk management program, because it can provide a comprehensive and balanced view of the program’s performance across multiple dimensions. A balanced scorecard can help to align the IT risk management program with the business strategy and vision, and to demonstrate the value and impact of the program to the stakeholders. A balanced scorecard can also help to identify the strengths and weaknesses of the IT risk management program, and to monitor and improve the program’s processes and outcomes2.
The other options are not as useful as a balanced scorecard for reporting on the overall status and effectiveness of the IT risk management program. A capability maturity level is a measure of the maturity and quality of a process or a practice, based on a predefined set of criteria and standards. A capability maturity level can help to assess and benchmark the IT risk management program’s processes and practices, but it does not provide a holistic view of the program’s performance and results3. An internal audit plan is a document that outlines the scope, objectives, and methodology of an internal audit activity. An internal audit plan can help to evaluate and verify the IT risk management program’s controls and compliance, but it does not provide a strategic view of the program’s goals and outcomes4. A control self-assessment (CSA) is a technique that involves the participation of the process owners and the staff in assessing the effectiveness and efficiency of their own controls. A CSA can help to enhance the awareness and ownership of the IT risk management program’s controls, but it does not provide an objective and independent view of the program’s performance and impact. References =
Balanced Scorecard Basics - Balanced Scorecard Institute
Using the Balanced Scorecard to Measure and Manage IT Risk
Capability Maturity Model Integration (CMMI) Overview
Internal Audit Planning: The Basics - The IIA
[Control Self-Assessment - ISACA]
Which of the following is a drawback in the use of quantitative risk analysis?
It assigns numeric values to exposures of assets.
It requires more resources than other methods
It produces the results in numeric form.
It is based on impact analysis of information assets.
The drawback in the use of quantitative risk analysis is that it requires more resources than other methods. Quantitative risk analysis is a method of risk analysis that assigns numeric values to the exposures of assets, the impact and likelihood of risk events, and the cost and benefit of risk responses. Quantitative risk analysis can provide more precise and objective results, and support the risk-based decision making process. However, quantitative risk analysis also requires more resources than other methods, such as data, time, expertise, and tools, to collect, validate, and analyze the quantitative information, and to perform the complex calculations and simulations. Quantitative risk analysis may also be limited by the availability, reliability, and accuracy of the data, and the assumptions and models used. Assigning numeric values to exposures of assets, producing the results in numeric form, and being based on impact analysis of information assets are not drawbacks, but characteristics of quantitative risk analysis. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 49.
Which of the following should be the PRIMARY focus of a risk owner once a decision is made to mitigate a risk?
Updating the risk register to include the risk mitigation plan
Determining processes for monitoring the effectiveness of the controls
Ensuring that control design reduces risk to an acceptable level
Confirming to management the controls reduce the likelihood of the risk
The primary focus of a risk owner once a decision is made to mitigate a risk is to ensure that the control design reduces the risk to an acceptable level. This means that the risk owner should verify that the control objectives, specifications, and implementation are aligned with the risk mitigation plan, and that the control is effective in reducing the risk exposure to within the risk appetite and tolerance of the enterprise. The risk owner should also ensure that the control design is consistent with the enterprise’s policies, standards, and procedures, and that it complies with any relevant laws, regulations, or contractual obligations. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 4, Section 4.2.4, page 185.
Which of the following BEST represents a critical threshold value for a key control indicator (KCI)?
The value at which control effectiveness would fail
Thresholds benchmarked to peer organizations
A typical operational value
A value that represents the intended control state
A critical threshold value for a key control indicator (KCI) is the value that indicates that the control is no longer performing its intended function of mitigating a risk. If the KCI reaches or exceeds this value, it means that the control effectiveness has failed and corrective actions are needed. The other options are not the best representations of a critical threshold value for a KCI, because they do not reflect the actual performance or outcome of the control. Thresholds benchmarked to peer organizations, a typical operational value, and a value that represents the intended control state are examples of target or acceptable values for a KCI, not critical or unacceptable values. References = CRISC: Certified in Risk & Information Systems Control Sample Questions
While reviewing an organization's monthly change management metrics, a risk practitioner notes that the number of emergency changes has increased substantially Which of the following would be the BEST approach for the risk practitioner to take?
Temporarily suspend emergency changes.
Document the control deficiency in the risk register.
Conduct a root cause analysis.
Continue monitoring change management metrics.
According to the CRISC Review Manual, a root cause analysis is a technique that identifies the underlying causes of an event or a problem. It helps to determine the most effective actions to prevent or mitigate the recurrence of the event or problem. A root cause analysis is the best approach for the risk practitioner to take in this scenario, because it will help to understand why the number of emergency changes has increased substantially and what can be done to address the issue. The other options are not the best approaches, because they do not address the underlying causes of the problem. Temporarily suspending emergency changes may disrupt the business operations and create more risks. Documenting the control deficiency in the risk register is a passive action that does not resolve the problem. Continuing monitoring change management metrics is an ongoing activity that does not provide any insight into the problem. References = CRISC Review Manual, 7th Edition, Chapter 3, Section 3.2.4, page 130.
Which of the following would be MOST helpful to an information security management team when allocating resources to mitigate exposures?
Relevant risk case studies
Internal audit findings
Risk assessment results
Penetration testing results
The most helpful factor for an information security management team when allocating resources to mitigate exposures is the risk assessment results. The risk assessment results provide a comprehensive and objective analysis of the risks facing the enterprise, including their likelihood, impact, and root causes. The risk assessment results also help to identify the gaps and weaknesses in the existing controls, and to prioritize the risks based on their severity and urgency. The risk assessment results enable the information security management team to allocate the resources in a cost-effective and risk-based manner, and to implement the most appropriate risk responses to reduce the exposures to an acceptable level. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 4, Section 4.1.1, page 1751
An organization has recently been experiencing frequent data corruption incidents. Implementing a file corruption detection tool as a risk response strategy will help to:
reduce the likelihood of future events
restore availability
reduce the impact of future events
address the root cause
Implementing a file corruption detection tool as a risk response strategy will help to reduce the impact of future events, as it will enable the organization to identify and correct the corrupted files before they cause further damage or loss. A file corruption detection tool is a software that scans and verifies the integrity and validity of the files, and alerts the users or administrators of any anomalies or errors. This helps to minimize the disruption and downtime caused by the data corruption incidents, and to preserve the quality and reliability of the data. Implementing a file corruption detection tool will not reduce the likelihood of future events, as it does not prevent or mitigate the causes or sources of the data corruption incidents. It will not restore availability, as it does not recover or restore the corrupted files, but only detects them. It will not address the root cause, as it does not analyze or eliminate the underlying factors that lead to the data corruption incidents. References = CRISC Certified in Risk and Information Systems Control – Question215; ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 215.
Which of the following would BEST enable a risk-based decision when considering the use of an emerging technology for data processing?
Gap analysis
Threat assessment
Resource skills matrix
Data quality assurance plan
The best way to enable a risk-based decision when considering the use of an emerging technology for data processing is to perform a gap analysis. A gap analysis is a technique that compares the current state and the desired state of a process, system, or capability, and identifies the gaps or differences between them. A gap analysis can help to evaluate the benefits, costs, risks, and opportunities of using an emerging technology for data processing, and to determine the feasibility, suitability, and readiness of adopting the emerging technology. The other options are not as helpful as a gap analysis, as they are related to the specific aspects or components of the data processing, not the overall assessment and comparison of the current and desired state of the data processing. References = Risk and Information Systems Control Study Manual, Chapter 1: IT Risk Identification, Section 1.2: IT Risk Identification Methods, page 19.
Which of the following is the BEST approach when a risk treatment plan cannot be completed on time?
Implement compensating controls until the preferred action can be completed.
Develop additional key risk indicators (KRIs) until the preferred action can be completed.
Replace the action owner with a more experienced individual.
Change the risk response strategy of the relevant risk to risk avoidance.
Implement compensating controls until the preferred action can be completed, because it helps to reduce the residual risk to an acceptable level, while allowing the preferred action to be delayed or postponed. A risk treatment plan is a document that describes the actions and resources required to implement the chosen risk response strategy for a specific risk. A risk response strategy is a course of action that is selected to address a risk, such as avoid, transfer, mitigate, or accept. A compensating control is a control that provides an alternative or additional measure of protection or assurance, when the primary or preferred control is not feasible or effective. Implementing compensating controls is the best approach, as it helps to maintain the risk management process and objectives, and to avoid or minimize the negative consequences of the delay or postponement of the preferred action.
Developing additional key risk indicators (KRIs), replacing the action owner with a more experienced individual, and changing the risk response strategy of the relevant risk to risk avoidance are all possible approaches when a risk treatment plan cannot be completed on time, but they are not the best approach, as they may not address the residual risk level, and they may introduce new risks or issues.
Which of the following should a risk practitioner review FIRST when evaluating risk events associated with the organization's data flow model?
Results of data classification activities
Recent changes to enterprise architecture (EA)
High-level network diagrams
Notes from interviews with the data owners
Which of the following is the PRIMARY benefit of stakeholder involvement in risk scenario development?
Ability to determine business impact
Up-to-date knowledge on risk responses
Decision-making authority for risk treatment
Awareness of emerging business threats
Risk scenario development is a process that involves identifying and describing the potential risk events that can affect an organization’s objectives and operations. Risk scenario development requires the input and participation of various stakeholders, such as the management, the staff, the customers, the suppliers, the regulators, and the competitors. The primary benefit of stakeholder involvement in risk scenario development is that it increases the awareness of emerging business threats, meaning that it helps to identify and anticipate the new or changing sources and impacts of risk that may not be captured by theexisting risk assessment methods or tools. Stakeholder involvement can also help to improve the quality and completeness of the risk scenarios, as well as to enhance the communication and collaboration among the stakeholders regarding the risk management process. References = Risk and Information Systems Control Study Manual, Chapter 2, Section 2.2.1.1, p. 66-67
An organization has determined a risk scenario is outside the defined risk tolerance level. What should be the NEXT course of action?
Develop a compensating control.
Allocate remediation resources.
Perform a cost-benefit analysis.
Identify risk responses
According to the CRISC Review Manual (Digital Version), the next course of action when an organization has determined a risk scenario is outside the defined risk tolerance level is to identify risk responses, which are the actions or measures taken to address the risk. Identifying risk responses helps to:
Reduce the likelihood and/or impact of the risk to an acceptable level
Align the risk response with the organization’s risk appetite and risk tolerance
Optimize the value and benefits of the risk response
Balance the costs and efforts of the risk response with the potential losses or damages caused by the risk
Coordinate and communicate the risk response with the relevant stakeholders
References = CRISC Review Manual (Digital Version), Chapter 3: IT Risk Response, Section 3.2: Risk Response Process, pp. 161-1621
Whether the results of risk analyses should be presented in quantitative or qualitative terms should be based PRIMARILY on the:
requirements of management.
specific risk analysis framework being used.
organizational risk tolerance
results of the risk assessment.
The results of risk analyses should be presented in quantitative or qualitative terms based primarily on the requirements of management, because they are the intended audience and users of the risk information, and they have the authority and responsibility to make risk-based decisions. The requirements of management may vary depending on the purpose, scope, and context of the risk analysis, and the level of detail, accuracy, and reliability that they need. Quantitative risk analysis uses numerical data and mathematical models to estimate the probability and impact of risks, and to express the risk exposure and value in monetary or other measurable units. Qualitative risk analysis uses descriptive data and subjective judgments to assess the likelihood and severity of risks, and to rank the risks according to their relative importance or priority. Both methods have their advantages and disadvantages, and they can be used separately or together, depending on the situation and the availability of data and resources. However, the primary factor that determines the choice of the method is the requirements of management, as they are the ones who will use the risk information to support their objectives, strategies, and actions. References = Risk IT Framework, ISACA, 2022, p. 141
An organization's Internet-facing server was successfully attacked because the server did not have the latest security patches. The risk associated with poor patch management had been documented in the risk register and accepted. Who should be accountable for any related losses to the organization?
Risk owner
IT risk manager
Server administrator
Risk practitioner
The risk owner is the person who should be accountable for any related losses to the organization, because they are the person who has the authority and responsibility to manage the risk and its associated controls.The risk owner is also the person who accepts the risk and its residual level, and who monitors and reports on the risk status and performance. The IT risk manager, the server administrator, and the risk practitioner are all involved in the risk management process, but they are not the person who should be accountable for the risk and its outcomes, as they do not have the ultimate decision-making power and accountability for the risk. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.1.1, page 79
Which of the following would BEST mitigate the ongoing risk associated with operating system (OS) vulnerabilities?
Temporarily mitigate the OS vulnerabilities
Document and implement a patching process
Evaluate permanent fixes such as patches and upgrades
Identify the vulnerabilities and applicable OS patches
The best way to mitigate the ongoing risk associated with operating system (OS) vulnerabilities is to document and implement a patching process. A patching process is a set of procedures and guidelines that define how to identify, evaluate, test, apply, and monitor patches for the OS. Patches are updates or fixes that address the known vulnerabilities or bugs in the OS. By documenting and implementing a patching process, the organization can ensure that the OS is regularly updated and protected from the potential exploits or attacks that may exploit the vulnerabilities. The other options are not as effective as documenting and implementing a patching process, as they are related to the temporary, partial, or reactive measures to deal with the OS vulnerabilities, not the proactive and continuous measures to prevent or reduce the OS vulnerabilities. References = Risk and Information Systems Control Study Manual, Chapter 3: IT Risk Response, Section 3.3: IT Risk Response Implementation, page 145.
Which of the following is the MOST effective way for a large and diversified organization to minimize risk associated with unauthorized software on company devices?
Scan end points for applications not included in the asset inventory.
Prohibit the use of cloud-based virtual desktop software.
Conduct frequent reviews of software licenses.
Perform frequent internal audits of enterprise IT infrastructure.
The most effective way for a large and diversified organization to minimize risk associated with unauthorized software on company devices is to scan end points for applications not included in the asset inventory. An asset inventory is a document that records and tracks all the hardware and software assets that are owned, used, or managed by the organization, such as laptops, tablets, smartphones, servers, applications, etc. An asset inventory helps to identify and classify the assets based on their type, model, location, owner, status, etc. An asset inventory also helps to monitor and control the assets, such as enforcing security policies, applying patches and updates, detecting and resolving issues, etc. Scanningend points for applications not included in the asset inventory helps to minimize the risk of unauthorized software, because it helps to discover and remove any software that is not approved, authorized, or licensed by the organization, and that may pose security, legal, or operational risks, such as malware, spyware, pirated software, etc. The other options are not as effective as scanning end points for applications not included in the asset inventory, although they may provide some protection or compliance for the software assets. Prohibiting the use of cloud-based virtual desktop software, conducting frequent reviews of software licenses, and performing frequent internal audits of enterprise IT infrastructure are all examples of preventive or detective controls, which may help to prevent or deter the installation or use of unauthorized software, or to verify or validate the software assets, but they do not necessarily discover or remove the unauthorized software. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.2.1, page 3-11.
Which of the following presents the GREATEST challenge to managing an organization's end-user devices?
Incomplete end-user device inventory
Unsupported end-user applications
Incompatible end-user devices
Multiple end-user device models
The greatest challenge to managing an organization’s end-user devices is having an incomplete end-user device inventory. An end-user device inventory is a document that records and tracks all the devices that are owned, used, or managed by the organization’s end-users, such as laptops, tablets, smartphones, etc. An end-user device inventory helps to identify and classify the devices based on their type, model, location, owner, status, etc. An end-user device inventory also helps to monitor and control the devices, such as enforcing security policies, applying patches and updates, detecting and resolving issues, etc. Having an incomplete end-user device inventory could lead to a lack of visibility and accountability for the devices, which could increase the risk of data loss, theft, or compromise, as well as the cost and complexity of device management. The other options are not as challenging as having an incomplete end-user device inventory, although they may also pose some difficulties or limitations for the device management. Unsupported end-user applications, incompatible end-user devices, and multiple end-user device models are all factors that could affect the functionality and compatibility of the devices, but they do not necessarily affect the visibility and accountability of the devices. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.2.1, page 3-11.
Which of the following has the GREATEST influence on an organization's risk appetite?
Threats and vulnerabilities
Internal and external risk factors
Business objectives and strategies
Management culture and behavior
Risk appetite is the amount and type of risk that an organization is willing to accept in pursuit of its objectives. Risk appetite is influenced by various factors, such as the organization’s mission, vision, values, culture, stakeholders, resources, capabilities, etc. However, the factor that has the greatest influence on the organization’s risk appetite is the business objectives and strategies, which are the desired outcomes and the plans to achieve them. The business objectives and strategies define the direction and scope of the organization, and the risk appetite reflects the level of risk that the organization is prepared to take to accomplish them. The risk appetite should be aligned with the business objectives and strategies, andshould provide guidance for the risk management activities and decisions. References = CRISC Review Manual, 7th Edition, page 61.
Which of the blowing is MOST important when implementing an organization s security policy?
Obtaining management support
Benchmarking against industry standards
Assessing compliance requirements
Identifying threats and vulnerabilities
The most important thing when implementing an organization’s security policy is to obtain management support. Management support means that the senior management and the board of directors endorse, approve, and fund the security policy and its implementation. Management support also means that the management communicates, promotes, and enforces the security policy across the organization. Management support can help to ensure that the security policy is aligned with the organizational strategy and objectives, and that it is effective, consistent, and sustainable. The other options are not as important as obtaining management support, as they are related to the specific aspects or components of the security policy implementation, not the overall success and acceptance of the security policy implementation. References = Risk and Information Systems Control Study Manual, Chapter 3: IT Risk Response, Section 3.3: IT Risk Response Implementation, page 145.
Which of the following practices would be MOST effective in protecting personality identifiable information (Ptl) from unauthorized access m a cloud environment?
Apply data classification policy
Utilize encryption with logical access controls
Require logical separation of company data
Obtain the right to audit
The most effective practice in protecting personally identifiable information (PII) from unauthorized access in a cloud environment is to utilize encryption with logical access controls. Encryption is a technique that transforms the data into an unreadable or unintelligible form, making it inaccessible or unusable by unauthorized parties. Logical access controls are the mechanisms or rules that regulate who can access, view, modify, or delete the data, based on their identity, role, or privilege. By utilizing encryption with logical access controls, the PII can be protected from unauthorized access, disclosure, or theft, both in transit and at rest, in a cloud environment. The other options are not as effective as utilizing encryption with logical access controls, as they are related to the classification, separation, or audit of the data, not the protection or security of the data. References = Risk and Information Systems Control Study Manual, Chapter 3: IT Risk Response, Section 3.3: IT Risk Response Implementation, page 145.
During a risk assessment, a risk practitioner learns that an IT risk factor is adequately mitigated by compensating controls in an associated business process. Which of the following would enable the MOST effective management of the residual risk?
Schedule periodic reviews of the compensating controls' effectiveness.
Report the use of compensating controls to senior management.
Recommend additional IT controls to further reduce residual risk.
Request that ownership of the compensating controls is reassigned to IT
A compensating control is a control that is implemented to reduce the risk exposure when the primary control is not feasible or cost-effective. A compensating control may not directly address the root cause of the risk, but it can provide an alternative or supplementary way of mitigating the risk. A residual risk is the risk that remains after the risk response has been implemented. A residual risk can be accepted, monitored, or further reduced depending on the risk tolerance and appetite of the organization. During a risk assessment, a risk practitioner is a person who is responsible for identifying and analyzing the potential sources and consequences of risk events. When a risk practitioner learns that an IT risk factor is adequately mitigated by compensating controls in an associated business process, the action that would enable the most effective management of the residual risk is to schedule periodic reviews of the compensating controls’ effectiveness, which means to measure and evaluate the performance and compliance of the compensating controls on a regular basis. By scheduling periodic reviews of the compensating controls’ effectiveness, the risk practitioner can ensure that the compensating controls are still operating as intended, and that they are delivering the expected results. The risk practitioner can also identify any gaps or weaknesses in the compensating controls, and recommend any improvements or adjustments as needed. References = CRISC Review Manual, 7th Edition, page 177.
Which of the following should be done FIRST when a new risk scenario has been identified
Estimate the residual risk.
Establish key risk indicators (KRIs).
Design control improvements.
Identify the risk owner.
•A risk owner is the person or entity that has the authority and responsibility to manage a specific risk1. The risk owner is accountable for the implementation and effectiveness of the risk response strategy and the risk treatment plan2.
•Identifying the risk owner is the first step when a new risk scenario has been identified, because the risk owner is the key stakeholder who will be involved in the subsequent steps of the risk management process, such as risk analysis, risk evaluation, risk treatment, and risk monitoring2.
•Identifying the risk owner also helps to clarify the roles and responsibilities of different parties involved in the risk management process, such as the risk manager, the risk analyst, the risk committee, and the risk auditor3. This can improve the communication, coordination, and collaboration among the risk management team and ensure that the risk is managed effectively and efficiently.
•Estimating the residual risk (option A) is not the first step when a new risk scenario has been identified, because the residual risk is the risk that remains after the risk treatment plan has been implemented2. Therefore, estimating the residual risk requires prior steps such as risk analysis, risk evaluation, and risk treatment.
•Establishing key risk indicators (KRIs) (option B) is not the first step when a new risk scenario has been identified, because KRIs are metrics or data points that provide early warning signals or information about the level or trend of a risk4. Therefore, establishing KRIs requires prior steps such as risk identification, risk analysis, and risk evaluation.
•Designing control improvements (option C) is not the first step when a new risk scenario has been identified, because control improvements are part of the risk treatment plan, which is the set of actions and resources needed to implement the chosen risk response strategy2. Therefore, designing control improvements requires prior steps such as risk analysis, risk evaluation, and risk response selection.
References =
•Risk Owner - Institute of Internal Auditors
•Risk Treatment Plan - ISACA
•Risk Management Roles and Responsibilities - 360factors
•Key Risk Indicators: A Practical Guide | SafetyCulture
Which of the following is the MOST effective way to incorporate stakeholder concerns when developing risk scenarios?
Evaluating risk impact
Establishing key performance indicators (KPIs)
Conducting internal audits
Creating quarterly risk reports
The most effective way to incorporate stakeholder concerns when developing risk scenarios is to evaluate the risk impact. Risk impact is the extent of the potential consequences or losses that may result from arisk event. Evaluating the risk impact involves considering the stakeholder concerns, expectations, and perspectives, as they may have different views on the value of the assets, the severity of the threats, and the acceptability of the outcomes. Evaluating the risk impact can help to ensure that the risk scenarios reflect the stakeholder interests and priorities, and that the risk responses are aligned with the stakeholder objectives. Establishing key performance indicators (KPIs), conducting internal audits, and creating quarterly risk reports are not as effective as evaluating the risk impact, as they are not directly related to the development of risk scenarios, and may not capture the stakeholder concerns adequately. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 50.
Because of a potential data breach, an organization has decided to temporarily shut down its online sales order system until sufficient controls can be implemented. Which risk treatment has been selected?
Avoidance
Transfer
Mitigation
Acceptance
Shutting down operations to prevent exposure to risk exemplifies risk avoidance, which eliminates the activity causing the risk. This aligns withRisk Treatment Strategies.
Which of the following is the MOST important update for keeping the risk register current?
Modifying organizational structures when lines of business merge
Adding new risk assessment results annually
Retiring risk scenarios that have been avoided
Changing risk owners due to employee turnover
Understanding the Question:
The question asks what the most important update for keeping the risk register current is.
Analyzing the Options:
A. Modifying organizational structures when lines of business merge:Reflects significant changes in the organization that impact risk profiles.
B. Adding new risk assessment results annually:Important but periodic.
C. Retiring risk scenarios that have been avoided:Necessary but not as impactful as major organizational changes.
D. Changing risk owners due to employee turnover:Important but secondary to major structural changes.
Detailed Explanation:
Organizational Changes:When lines of business merge, it can significantly alter the risk landscape, introducing new risks and changing the impact and likelihood of existing ones. Updating the risk register to reflect these changes is crucial for accurate risk management.
Impact on Risk Profiles:Mergers and acquisitions can affect every aspect of an organization, from operational processes to regulatory compliance, making it essential to update the risk register accordingly.
References:
CRISC Review Manual, Chapter 3: Risk Response and Reporting, discusses the importance of keeping the risk register updated to reflect organizational changes and ensure effective risk management.
Which of the following BEST mitigates ethical risk?
Ethics committees
Contingency scenarios
Awareness of consequences for violations
Routine changes in senior management
Ethics committees are typically responsible for developing, implementing, and overseeing an organization’s ethical guidelines and policies. They play a crucial role in mitigating ethical risk by ensuring that the organization’s operations align with its ethical standards123.
References
1What Is Ethically Informed Risk Management? - Journal of Ethics
2Five Ways to Reduce Ethics and Compliance Risk - Free Ethics Toolkit
35 Ways to Manage Ethical Risks - ClearRisk
Which strategy employed by risk management would BEST help to prevent internal fraud?
Require control owners to conduct an annual control certification.
Conduct regular internal and external audits on the systems supporting financial reporting.
Ensure segregation of duties are implemented within key systems or processes.
Require the information security officer to review unresolved incidents.
Ensuring segregation of duties are implemented within key systems or processes is the best strategy employed by risk management to prevent internal fraud, because it reduces the opportunity for a single person to manipulate or misuse the system or process for fraudulent purposes. Segregation of duties is a control that assigns different roles and responsibilities to different individuals, such that no one person can perform all the steps of a transaction or process. Requiring control owners to conduct an annual control certification, conducting regular internal and external audits on the systems supporting financial reporting, and requiring the information security officer to review unresolved incidents are all useful strategies to detect or deter internal fraud, but they are not the best strategy to prevent it, as they do not directly address the root cause of fraud. References = Risk and Information Systems Control Study Manual, Chapter 5, Section 5.3.1, page 197
The risk to an organization's reputation due to a recent cybersecurity breach is PRIMARILY considered to be:
financial risk.
data risk.
operational risk.
strategic risk.
Understanding Strategic Risk:
Strategic risk refers to the potential losses that can arise from adverse business decisions, improper implementation of decisions, or lack of responsiveness to changes in the business environment.
Reputational Impact of Cybersecurity Breaches:
A cybersecurity breach can severely damage an organization's reputation, affecting customer trust, investor confidence, and market value.
Such impacts go beyond immediate financial losses and can have long-term strategic implications for the organization's competitive position and strategic objectives.
Classification of Risk:
Financial Risk:Direct financial losses due to a breach (e.g., fines, legal costs) but does not cover reputational impacts.
Data Risk:Focuses on the loss or compromise of data but not the broader strategic impact.
Operational Risk:Pertains to disruptions in business operations, while reputational damage influences the organization’s strategic direction and goals.
Strategic Risk and Reputation:
Reputational damage from a cybersecurity breach can lead to a loss of customer base, reduced market share, and difficulties in strategic partnerships, all of which are strategic concerns.
Addressing reputational risk requires strategic planning, proactive communication, and long-term efforts to rebuild trust and credibility.
References:
The CRISC Review Manual highlights that reputational risk is a significant aspect of strategic risk, especially following cybersecurity incidents (CRISC Review Manual, Chapter 1: Governance, Section 1.1.3 Importance and Value of IT Risk Management).
The risk associated with an asset before controls are applied can be expressed as:
a function of the likelihood and impact
the magnitude of an impact
a function of the cost and effectiveness of control.
the likelihood of a given threat
The risk associated with an asset before controls are applied is also known as the inherent risk. It is the level of risk that exists in the absence of any mitigating actions or measures. To express the inherent risk, one needs to consider two factors: the likelihood and the impact of a potential threat. The likelihood is the probability or frequency of a threat occurring, while the impact is the magnitude or severity of the consequences if the threat materializes. The inherent risk can be calculated by multiplying the likelihood and the impact, or by using a risk matrix that assigns a risk rating based on the combination of these two factors. The other options are not correct ways of expressing the inherent risk, as they do not account for both the likelihood and the impact of a threat. The magnitude of an impact is only one component of the risk, and it does not reflect how likely the threat is to happen. The function of the cost and effectiveness of control is related to the residual risk, which is the risk that remains after controls are applied. The likelihood of a given threat is also only one component of the risk, and it does not indicate how severe the impact would be if the threat occurs. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.1.1, Page 47.
When a risk practitioner is determining a system's criticality. it is MOST helpful to review the associated:
process flow.
business impact analysis (BIA).
service level agreement (SLA).
system architecture.
The most helpful information to review when determining a system’s criticality is the associated business impact analysis (BIA). A BIA is a process of identifying and evaluating the potential effects of disruptions to the organization’s critical business functions and processes. A BIA can help to determine the system’s criticality by assessing its impact on the organization’s objectives, performance, and value. Process flow, service level agreement (SLA), and system architecture are other possible information sources, but they are not as helpful as the BIA. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 4; CRISC Review Manual, 6th Edition, page 153.
Which of the following provides the MOST useful information for developing key risk indicators (KRIs)?
Business impact analysis (BIA) results
Risk scenario ownership
Risk thresholds
Possible causes of materialized risk
Key risk indicators (KRIs) are metrics that provide an early warning of increasing risk exposure in various areas of the organization. They help to monitor changes in the level of risk and enable timely actions to mitigate the risk. The most useful information for developing KRIs is the possible causes of materialized risk, which are the factors or events that trigger or contribute to the occurrence of a risk. By identifying the possible causes of materialized risk, an organization can design KRIs that measure the likelihood and impact of the risk, and alert the management when the risk exceeds the acceptable level. References = CRISC Review Manual, 7th Edition, page 101.
An organization is adopting block chain for a new financial system. Which of the following should be the GREATEST concern for a risk practitioner evaluating the system's production readiness?
Limited organizational knowledge of the underlying technology
Lack of commercial software support
Varying costs related to implementation and maintenance
Slow adoption of the technology across the financial industry
The greatest concern for a risk practitioner when an organization is adopting blockchain for a new financial system is the limited organizational knowledge of the underlying technology. Blockchain is a distributed ledger technology that enables secure and transparent transactions among multiple parties without the need for intermediaries or central authorities. Blockchain technology has many potential benefits for the financial sector, such as reducing costs, increasing efficiency, enhancing security, and improving trust. However, blockchain technology also poses many challenges and risks for the organization, such as technical complexity, interoperability issues, regulatory uncertainty, and cultural resistance. The limited organizational knowledge of the underlying technology is the greatest concern, because it affects the ability and readiness of the organization to adopt, implement, use, and maintain the blockchain system effectively and securely. The limited organizational knowledge could also result in poor decision-making, inadequate governance, insufficient training, and increased vulnerability to errors, fraud, or attacks. The other options are not as concerning as the limited organizational knowledge, although they may also pose some difficulties or limitations for the blockchain adoption. Lack of commercial software support, varying costs related to implementation and maintenance, and slow adoption of the technology across the financial industry are all factors that could affect the feasibility and sustainability of the blockchain system, but they do not directly affect the capability and maturity of the organization. References = 5
Which of the following is MOST important when conducting a post-implementation review as part of the system development life cycle (SDLC)?
Verifying that project objectives are met
Identifying project cost overruns
Leveraging an independent review team
Reviewing the project initiation risk matrix
The most important activity when conducting a post-implementation review as part of the system development life cycle (SDLC) is to verify that the project objectives are met. The project objectives are the specific and measurable outcomes that the project aims to achieve. By verifying that the project objectives are met, the post-implementation review can evaluate the success and value of the project, and identify the lessons learned and best practices for future projects. Identifying project cost overruns, leveraging an independent review team, and reviewing the project initiation risk matrix are other possible activities, but they are not as important as verifying that the project objectives are met. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 4; CRISC Review Manual, 6th Edition, page 153.
Which of the following should be the PRIMARY basis for prioritizing risk responses?
The impact of the risk
The replacement cost of the business asset
The cost of risk mitigation controls
The classification of the business asset
The primary basis for prioritizing risk responses is the impact of the risk. The impact of the risk is the consequence or effect of the risk on the organization’s objectives or operations, such as financial loss, reputational damage, operational disruption, or legal liability. The impact of the risk is one of the key dimensions of risk analysis, along with the likelihood of the risk. The impact of the risk helps to determine the severity and priority of the risk, and to select the most appropriate and effective risk response. The impact of the risk also helps to evaluate the cost-benefit and trade-off of the risk response, and to measure the residual risk and the risk performance. The other options are not the primary basis for prioritizing risk responses, although they may be considered or influenced by the impact of the risk. The replacement cost of the business asset, the cost of risk mitigation controls, and the classification of the business asset are all factors that could affect the value or importance of the business asset, but they do not necessarily reflect the impact of the risk on the business asset or the organization. References = Risk and Information Systems Control Study Manual, Chapter 4, Section 4.3.1, page 4-25.
Which of the following is MOST important for senior management to review during an acquisition?
Risk appetite and tolerance
Risk framework and methodology
Key risk indicator (KRI) thresholds
Risk communication plan
The most important factor for senior management to review during an acquisition is the risk appetite and tolerance of the target organization. The risk appetite and tolerance reflect the amount and type of risk that an organization is willing to accept in pursuit of its objectives. By reviewing the risk appetite and tolerance of the target organization, senior management can determine if they are compatible with their own, and if the acquisition will create any significant risk exposure or opportunity for the acquiring organization. Risk framework and methodology, key risk indicator (KRI) thresholds, and risk communication plan are other factors that may be reviewed, but they are not as important as the risk appetite and tolerance. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 8; CRISC Review Manual, 6th Edition, page 97.
Which of the following is the BEST way for a risk practitioner to present an annual risk management update to the board''
A summary of risk response plans with validation results
A report with control environment assessment results
A dashboard summarizing key risk indicators (KRIs)
A summary of IT risk scenarios with business cases
A dashboard summarizing key risk indicators (KRIs) is the best way for a risk practitioner to present an annual risk management update to the board because it provides a concise and visual overview of the current risk status, trends, and performance of the organization. KRIs are metrics that measure the likelihood and impact of risks, and help the board monitor and prioritize the most critical risks. A summary of risk response plans, a report with control environment assessment results, and a summary of IT risk scenarios are all useful information, but they are too detailed and technical for the board, who needs a high-level and strategic view of the risk management program. References = Risk and Information Systems Control Study Manual, Chapter 4, Section 4.4.1, page 4-36.
Which of the following trends would cause the GREATEST concern regarding the effectiveness of an organization's user access control processes? An increase in the:
ratio of disabled to active user accounts.
percentage of users with multiple user accounts.
average number of access entitlements per user account.
average time between user transfers and access updates.
The average time between user transfers and access updates is a trend that would cause the greatest concern regarding the effectiveness of an organization’s user access control processes, as it indicates thedelay or inefficiency in updating the user access rights and privileges according to the user’s current role and responsibilities. This can result in unauthorized or excessive access to the organization’s information assets, and increase the risk of data leakage, fraud, or misuse. The user access control processes should ensure that the user access rights and privileges are reviewed and modified regularly, and especially when the user’s role or status changes, such as transfer, promotion, demotion, or termination. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, Question 241. CRISC: Certified in Risk & Information Systems Control Sample Questions, Question 241. CRISC Sample Questions 2024, Question 241.
Which of the following will BEST help to ensure new IT policies address the enterprise's requirements?
involve IT leadership in the policy development process
Require business users to sign acknowledgment of the poises
involve business owners in the pokey development process
Provide policy owners with greater enforcement authority
To ensure that new IT policies address the enterprise’s requirements, it is important to involve the business owners who are the primary stakeholders of the IT services and processes. Business owners can provide valuable input on the business objectives, risks, and expectations that the IT policies should align with and support. By involving business owners in the policy development process, the IT policies will be more relevant, realistic, and acceptable to the business units. References = Risk and Information Systems Control Study Manual, Chapter 1: IT Risk Identification, Section 1.3: IT Risk Scenarios, page 23.
Which of the following is the MOST important information to cover a business continuity awareness Ira nine, program for all employees of the organization?
Recovery time objectives (RTOs)
Segregation of duties
Communication plan
Critical asset inventory
The most important information to cover in a business continuity awareness training program for all employees of the organization is the communication plan. A communication plan is a document that defines the roles, responsibilities, procedures, and resources for communicating with the internal and external stakeholders before, during, and after a business continuity event. A communication plan helps to ensure that the relevant and accurate information is delivered to the appropriate parties in a timely and consistent manner, and that the feedback and responses are received and addressed accordingly. A communication plan also helps to maintain the trust, confidence, and reputation of the organization, and to comply with the legal or regulatory requirements. A communication plan is the most important information to cover in a business continuity awareness training program, because it helps to prepare and educate the employees on how to communicate effectively and efficiently in a business continuity event, and how to avoid or minimize the communication errors, gaps, or conflicts that could affect the business continuity performance and recovery. The other options are not as important as the communication plan, although they may also be covered in a business continuity awareness training program. Recovery time objectives (RTOs), segregation of duties, and critical asset inventory are all factors that could affect the business continuity planning and implementation, but they are not the most important information to cover in a business continuity awareness training program. References = 6
Which of the following should be the FIRST consideration when establishing a new risk governance program?
Developing an ongoing awareness and training program
Creating policies and standards that are easy to comprehend
Embedding risk management into the organization
Completing annual risk assessments on critical resources
The first consideration when establishing a new risk governance program is embedding risk management into the organization. Embedding risk management means integrating risk management principles and practices into the organization’s culture, values, processes, and decision-making. Embedding risk management helps to ensure that risk management is not seen as a separate or isolated activity, but as a part of the organization’s normal operations and strategic objectives. Embedding risk management also helps to create a risk-aware and risk-responsive organization, where risk management is shared and supported by all stakeholders. The other options are not the first consideration, although they may be important steps or components of the risk governance program. Developing an ongoing awareness and training program, creating policies and standards that are easy to comprehend, and completing annual risk assessments on critical resources are all activities that can help to embed risk management into the organization, but they are not the initial or primary consideration. References = Risk and Information Systems Control Study Manual, Chapter 1, Section 1.2.1, page 1-8.
Which of the following is the MOST important consideration when developing risk strategies?
Organization's industry sector
Long-term organizational goals
Concerns of the business process owners
History of risk events
Risk strategies are the plans and actions that an organization adopts to manage its risks and to achieve its objectives. Risk strategies should be aligned with the organization’s vision, mission, values, and culture, as well as its internal and external environment. The most important consideration when developing risk strategies is the long-term organizational goals, meaning that the risk strategies should support and enable the organization to pursue and attain its desired future state and outcomes. The long-term organizational goals should guide the risk identification, assessment, response, and monitoring processes, as well as the risk appetite and tolerance levels. The long-term organizational goals should also be communicated and cascaded throughout the organization to ensure the risk awareness and engagement of all stakeholders. References = Risk and Information Systems Control Study Manual, Chapter 1, Section 1.3.2, p. 27-28
What is the BEST recommendation to reduce the risk associated with potential system compromise when a vendor stops releasing security patches and updates for a business-critical legacy system?
Segment the system on its own network.
Ensure regular backups take place.
Virtualize the system in the cloud.
Install antivirus software on the system.
The best recommendation to reduce the risk associated with potential system compromise when a vendor stops releasing security patches and updates for a business-critical legacy system is to segment the system on its own network. Network segmentation is the process of dividing a network into smaller subnetworks or segments, based on different criteria, such as function, location, or security level. Network segmentation helps to isolate the system from the rest of the network, and limit the exposure and access to the system. Network segmentation also helps to improve the performance and security of the network, by reducing the network traffic and congestion, and enhancing the monitoring and control capabilities. The other options are not as effective as segmenting the system on its own network, although they may provide some additional protection or recovery options. Ensuring regular backups take place, virtualizing the system in the cloud, and installing antivirus software on the system are all measures that can help to reduce the risk of data loss or system damage, but they do not address the root cause of the risk, which is the lack of security patches and updates for the system. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.2.1, page 3-11.
Which stakeholder is MOST important to include when defining a risk profile during me selection process for a new third party application'?
The third-party risk manager
The application vendor
The business process owner
The information security manager
A risk profile is a summary of the nature and level of risk that an organization faces. It includes information such as the sources, causes, and consequences of the risks, their likelihood and impact, their interrelationships and dependencies, and their alignment with the risk appetite and tolerance. A risk profile is influenced by various factors, such as the organization’s objectives, strategies, activities, processes, resources, capabilities, culture, etc. When defining a risk profile during the selection process for a new third party application, the stakeholder that is most important to include is the business process owner, who is the person who has the authority and responsibility for the design, execution, and performance of a business process. The business process owner can provide valuable input and insight into the requirements, expectations, and dependencies of the business process that will use the new third party application, and the potential risks and opportunities that may arise from the selection of the application. The business process owner can also help to prioritize and address the risks, and ensure that the risk profile is aligned with the business objectives and strategies. References = 5
Which of the following management action will MOST likely change the likelihood rating of a risk scenario related to remote network access?
Updating the organizational policy for remote access
Creating metrics to track remote connections
Implementing multi-factor authentication
Updating remote desktop software
The management action that will most likely change the likelihood rating of a risk scenario related to remote network access is implementing multi-factor authentication. Multi-factor authentication is a technique that requires the user to provide two or more pieces of evidence to verify their identity, such as a password, a token, or a biometric factor. Multi-factor authentication can help to reduce the likelihood of unauthorized or malicious access to the remote network, as it adds an extra layer of security and makes it harder for the attackers to compromise the user credentials. The other options are not as likely to change the likelihood rating of the risk scenario, as they are related to the update, creation, or maintenance of the remote network access, not the verification or protection of the remote network access. References = Risk and Information Systems Control Study Manual, Chapter 3: IT Risk Response, Section 3.3: IT Risk Response Implementation, page 145.
Who is MOST appropriate to be assigned ownership of a control
The individual responsible for control operation
The individual informed of the control effectiveness
The individual responsible for resting the control
The individual accountable for monitoring control effectiveness
A control is a measure or action that is implemented to reduce the likelihood or impact of a risk event, or to enhance the benefits or opportunities of a risk event. A control owner is a person who is assigned the responsibility and authority for the design, implementation, operation, and maintenance of a control. The most appropriate person to be assigned ownership of a control is the individual accountable for monitoring control effectiveness, which is the process of measuring and evaluating the performance and compliance of the control. By assigning the control ownership to the individual accountable for monitoring control effectiveness, the organization can ensure that the control is aligned with the risk objectives, operates as intended, and delivers the expected results. References = 4
A recent big data project has resulted in the creation of an application used to support important investment decisions. Which of the following should be of GREATEST concern to the risk practitioner?
Data quality
Maintenance costs
Data redundancy
System integration
The greatest concern for the risk practitioner when a big data project has resulted in the creation of an application used to support important investment decisions is the data quality. Data quality is the degree to which the data is accurate, complete, consistent, reliable, relevant, and timely. Data quality is essential for the success of any big data project, as it affects the validity and reliability of the analysis and the outcomes. Poor data quality could lead to erroneous or misleading results, which could have negative consequences for the investment decisions and the organization’s performance and reputation. The other options are not as concerning as the data quality, although they may also pose some challenges or risks for the big data project. Maintenance costs, data redundancy, and system integration are all factors that could affect the efficiency and effectiveness of the big data project, but they do not directly affect the accuracy and reliability of the analysis and the outcomes. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.3.1, page 3-20.
An internal audit report reveals that a legacy system is no longer supported Which of the following is the risk practitioner's MOST important action before recommending a risk response'
Review historical application down me and frequency
Assess the potential impact and cost of mitigation
identify other legacy systems within the organization
Explore the feasibility of replacing the legacy system
A legacy system is an old or outdated IT system that is still in use by an organization. A legacy system may pose various risks to the organization, such as security vulnerabilities, compatibility issues, performance degradation, maintenance challenges, etc. When an internal audit report reveals that a legacy system is no longer supported by the vendor or the manufacturer, the risk practitioner’s most important action before recommending a risk response is to assess the potential impact and cost of mitigation, which means to estimate the consequences and expenses of the risk event if the legacy system fails or malfunctions. By assessing the potential impact and cost of mitigation, the risk practitioner can evaluate the risk exposure and determine the appropriate risk response, such as accepting, avoiding, transferring, or reducing the risk. References = 4
An organization's recovery team is attempting to recover critical data backups following a major flood in its data center. However, key team members do not know exactly what steps should be taken to address this crisis. Which of the following is the MOST likely cause of this situation?
Failure to test the disaster recovery plan (DRP)
Lack of well-documented business impact analysis (BIA)
Lack of annual updates to the disaster recovery plan (DRP)
Significant changes in management personnel
The most likely cause of the situation where the recovery team does not know what steps to take to recover critical data backups following a major flood is the failure to test the disaster recovery plan (DRP). A DRP is a document that describes the procedures and resources needed to restore the normal operations of an organization after a disaster. Testing the DRP is essential to ensure that the plan is feasible, effective, and up-to-date. Testing the DRP also helps to train the recovery team members, identify and resolve any issues or gaps, and improve the confidence and readiness of the organization. The lack of a well-documented business impact analysis (BIA), the lack of annual updates to the DRP, and the significant changes in management personnel are also possible factors that could affect the recovery process, butthey are not as likely or as critical as the failure to test the DRP. References = Risk and Information Systems Control Study Manual, Chapter 5, Section 5.3.1, page 5-19.
Which of the following will BEST help to ensure implementation of corrective action plans?
Establishing employee awareness training
Assigning accountability to risk owners
Selling target dates to complete actions
Contracting to third parties
The best way to ensure the implementation of corrective action plans is to assign accountability to risk owners. Corrective action plans are the plans that describe the actions and resources that are needed to correct or improve the performance or compliance of the processes or controls. Risk owners are the persons who have the authority and responsibility for managing the risks and their responses. By assigning accountability to risk owners, the implementation of corrective action plans can be monitored, evaluated, and enforced, and the results and outcomes can be reported and communicated. The other options are not as effective as assigning accountability to risk owners, as they are related to the training, scheduling, or outsourcing of the corrective action plans, not the oversight or governance of the corrective action plans. References = Risk and Information Systems Control Study Manual, Chapter 4: Risk and Control Monitoring and Reporting, Section 4.4: Key Control Indicators, page 211.
Which of the following is the PRIMARY reason to perform periodic vendor risk assessments?
To provide input to the organization's risk appetite
To monitor the vendor's control effectiveness
To verify the vendor's ongoing financial viability
To assess the vendor's risk mitigation plans
The primary reason to perform periodic vendor risk assessments is to monitor the vendor’s control effectiveness. A vendor risk assessment is a process of evaluating the risks associated with outsourcing a service or function to a third-party vendor. The assessment should be performed periodically to ensure that the vendor is complying with the contractual obligations, service level agreements, and security standards, and that the vendor’s controls are operating effectively to mitigate the risks. Providing input to the organization’s risk appetite, verifying the vendor’s ongoing financial viability, and assessing the vendor’s risk mitigation plans are other possible reasons, but they are not as important as monitoring the vendor’s control effectiveness. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 11; CRISC Review Manual, 6th Edition, page 144.
Which of the following is the BEST control to minimize the risk associated with scope creep in software development?
An established process for project change management
Retention of test data and results for review purposes
Business managements review of functional requirements
Segregation between development, test, and production
The best control to minimize the risk associated with scope creep in software development is an established process for project change management. Scope creep is the uncontrolled expansion of the project scope due to changes in requirements, specifications, or expectations. A project change management process can help to prevent or reduce scope creep by defining the procedures for requesting, reviewing, approving, and implementing changes in the project. Retention of test data and results, business management review of functional requirements, and segregation between development, test, and production are other possible controls, but they are not as effective as a project change management process. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 11; CRISC Review Manual, 6th Edition, page 144.
Which of the following is the MOST important consideration when multiple risk practitioners capture risk scenarios in a single risk register?
Aligning risk ownership and control ownership
Developing risk escalation and reporting procedures
Maintaining up-to-date risk treatment plans
Using a consistent method for risk assessment
A risk register is a document that records and tracks the information and status of the identified risks and their responses. It includes the risk description, category, source, cause, impact, probability, priority, response, owner, action plan, status, etc.
A risk scenario is a description or representation of a possible or hypothetical situation or event that may cause or result in a risk for the organization. A risk scenario usually consists of three elements: a threat or source of harm, a vulnerability or weakness, and an impact or consequence.
Multiple risk practitioners are the individuals or groups that are involved or responsible for the identification, analysis, evaluation, and communication of the risks and their responses. They may include the risk owners, risk managers, risk analysts, risk consultants, risk auditors, etc.
A single risk register is a risk register that is shared or used by multiple risk practitioners across the organization, and that contains the information and status of all the risks and their responses that are relevant or applicable to the organization.
The most important consideration when multiple risk practitioners capture risk scenarios in a single risk register is using a consistent method for risk assessment, which is the process of determining the significance and urgency of the risks that may affect the organization’s objectives and operations. Risk assessment involves measuring and comparing the likelihood and impact of various risk scenarios, and prioritizing them based on their magnitude and importance.
Using a consistent method for risk assessment when multiple risk practitioners capture risk scenarios in a single risk register ensures that the risk scenarios are captured and recorded in a uniform and standardized way, and that they are comparable and compatible with each other. It alsohelps to avoid or reduce the inconsistencies, discrepancies, or conflicts that may arise from the different perspectives, assumptions, or judgments of the multiple risk practitioners, and to ensure the accuracy, reliability, and validity of the risk register.
The other options are not the most important considerations when multiple risk practitioners capture risk scenarios in a single risk register, because they do not address the main challenge or issue that may arise from the multiple risk practitioners capturing risk scenarios in a single risk register, which is the lack of consistency or standardization in the risk assessment method.
Aligning risk ownership and control ownership means ensuring that the individuals or groups that are accountable and responsible for the risks and their responses are clearly defined and assigned, and that they have the authority and resources to perform their roles and duties. Aligning risk ownership and control ownership is important when multiple risk practitioners capture risk scenarios in a single risk register, but it is not the most important consideration, because it does not ensure that the risk scenarios are captured and recorded in a uniform and standardized way, and that they are comparable and compatible with each other.
Developing risk escalation and reporting procedures means establishing and implementing the processes and guidelines for communicating and sharing the information and status of the risks and their responses among the relevant stakeholders, and for escalating or transferring the risks and their responses to the appropriate levels or parties when necessary or required. Developing risk escalation and reporting procedures is important when multiple risk practitioners capture risk scenarios in a single risk register, but it is not the most important consideration, because it does not ensure that the risk scenarios are captured and recorded in a uniform and standardized way, and that they are comparable and compatible with each other.
Maintaining up-to-date risk treatment plans means updating and revising the actions or plans that are selected and implemented to address or correct the risks and their responses, based on the changes or developments that may occur in the risk environment or performance. Maintaining up-to-date risk treatment plans is important when multiple risk practitioners capture risk scenarios in a single risk register, but it is not the most important consideration, because it does not ensure that the risk scenarios are captured and recorded in a uniform and standardized way, and that they are comparable and compatible with each other. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 19-20, 23-24, 27-28, 31-32, 40-41, 47-48, 54-55, 58-59, 62-63
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 178
CRISC Practice Quiz and Exam Prep
Which of the following would be MOST helpful when estimating the likelihood of negative events?
Business impact analysis
Threat analysis
Risk response analysis
Cost-benefit analysis
According to the CRISC Review Manual (Digital Version), threat analysis would be the most helpful when estimating the likelihood of negative events, as it involves identifying and evaluating the sources and causes of potential harm or loss to the IT assets and processes. Threat analysis helps to:
Determine the frequency and probability of occurrence of different types of threats, such as natural disasters, human errors, malicious attacks, system failures, etc.
Assess the impact and severity of the threats on the confidentiality, integrity and availability of the IT assets and processes
Prioritize the threats based on their likelihood and impact
Develop appropriate risk response strategies to prevent, mitigate, transfer or accept the threats
References = CRISC Review Manual (Digital Version), Chapter 1: IT Risk Identification, Section 1.5: IT Risk Identification Methods and Techniques, pp. 35-361
A penetration testing team discovered an ineffectively designed access control. Who is responsible for ensuring the control design gap is remediated?
Control owner
Risk owner
IT security manager
Control operator
Role of the Control Owner:
The control owner is responsible for the design, implementation, and maintenance of a specific control.
They have detailed knowledge of the control’s purpose, its intended functionality, and its operational context within the organization.
Responsibility for Remediation:
When a penetration testing team discovers an ineffectively designed access control, it is the control owner’s responsibility to ensure the design gap is remediated.
The control owner must assess the findings, determine the root cause of the ineffectiveness, and take necessary actions to redesign or enhance the control to address the identified weaknesses.
Steps to Remediate Control Design Gap:
Assess the Findings:Understand the specific issues identified by the penetration testing team.
Redesign the Control:Modify the control design to address the identified gaps and ensure it meets security requirements.
Implement Changes:Apply the redesigned control and test its effectiveness.
Continuous Monitoring:Regularly review the control to ensure it remains effective over time.
Comparing Other Roles:
Risk Owner:Manages overall risk but does not directly handle control design.
IT Security Manager:Oversees the security posture but delegates specific control responsibilities to control owners.
Control Operator:Operates the control but is not responsible for its design or remediation.
References:
The CRISC Review Manual emphasizes the control owner's responsibility in maintaining and improving control effectiveness (CRISC Review Manual, Chapter 3: Risk Response and Mitigation, Section 3.7 Control Design and Selection).
An organization has outsourced its customer management database to an external service provider. Of the following, who should be accountable for ensuring customer data privacy?
The organization's business process owner
The organization's information security manager
The organization's vendor management officer
The vendor's risk manager
A risk practitioner has identified that the organization's secondary data center does not provide redundancy for a critical application. Who should have the authority to accept the associated risk?
Business continuity director
Disaster recovery manager
Business application owner
Data center manager
The business application owner should have the authority to accept the associated risk, because they are responsible for the performance and outcomes of the critical application, and they understand the business requirements, expectations, and impact of the application. The business application owner can also evaluate the trade-offs between the potential benefits and costs of the application, and the potential risks and consequences of a disruption or failure of the application. The business application owner can also communicate and justify their risk acceptance decision to the senior management and other stakeholders, and ensure that the risk is monitored and reviewed regularly. The other options are less appropriate to have the authority to accept the associated risk. The business continuity director is responsible for overseeing the planning and execution of the business continuity strategy, which includes ensuring the availability and resilience of the critical business processes and applications. However, they are not the owner of the application, and they may not have the full knowledge or authority to accept the risk on behalf of the business. The disaster recovery manager is responsible for managing the recovery and restoration of the IT systems and applications in the event of a disaster or disruption. However, they are not the owner of the application, and they may not have the full knowledge or authority to accept the risk on behalf of the business. The data center manager is responsible for managing the operation and maintenance of the data center infrastructure, which includes providing the physical and environmental security, power, cooling, and network connectivity for the IT systems and applications. However, they are not the owner of the application, and they may not have the full knowledge or authority to accept the risk on behalf of the business. References = Risk IT Framework, ISACA, 2022, p. 181
When an organization’s disaster recovery plan (DRP) has a reciprocal agreement, which of the following risk treatment options is being applied?
Acceptance
Mitigation
Transfer
Avoidance
A reciprocal agreement is an agreement made by two or more organizations to use each other’s resources during a disaster1. For example, two organizations with similar IT infrastructure may agree to provide backup servers or data centers for each other in case of a major disruption. By doing so, they transfer the risk of losing their IT capabilities to the other party, who agrees to share the responsibility and cost of recovery.
A reciprocal agreement is a form of risk transfer, which is one of the four risk treatment options according to ISO 270012. Risk transfer means that the organization shifts the potential negative consequences of a risk to another party, such as an insurance company, a vendor, or a partner. This reduces the organization’s exposure and liability to the risk, but it does not eliminate the risk completely, as the other party may fail to fulfill their obligations or charge a high price for their services.
References = Reciprocal Agreement - Risky Thinking, ISO 27001 Risk Assessment & Risk Treatment: The Complete Guide - Advisera
When of the following is the BEST key control indicator (KCI) to determine the effectiveness of en intrusion prevention system (IPS)?
Percentage of system uptime
Percentage of relevant threats mitigated
Total number of threats identified
Reaction time of the system to threats
The percentage of relevant threats mitigated is the best key control indicator (KCI) to determine the effectiveness of an intrusion prevention system (IPS), because it measures how well the IPS is performing its intended function of preventing unauthorized access or attacks. The percentage of system uptime is not a good KCI, because it does not reflect the quality or accuracy of the IPS. The total number of threats identified is not a good KCI, because it does not indicate how many of those threats were actually prevented by the IPS. The reaction time of the system to threats is not a good KCI, because it does not measure the impact or severity of the threats that were prevented or not prevented by the IPS. References = CRISC: Certified in Risk & Information Systems Control Sample Questions2
Which of the following is MOST important to the effective monitoring of key risk indicators (KRIS)?
Updating the threat inventory with new threats
Automating log data analysis
Preventing the generation of false alerts
Determining threshold levels
Key risk indicators (KRIs) are metrics that provide information about the level of exposure to a specific risk or a group of risks.
The most important factor to the effective monitoring of KRIs is determining threshold levels. This means that the acceptable or unacceptable values or ranges of the KRIs are defined and agreed upon by the relevant stakeholders.
Determining threshold levels helps to evaluate the actual performance and impact of the risks, compare them with the risk appetite and tolerance of the organization, identify any deviations or breaches that may require attention or action, and report them to the appropriate parties for decision making or improvement actions.
The other options are not the most important factors to the effective monitoring of KRIs. They are either secondary or not essential for KRIs.
The references for this answer are:
Risk IT Framework, page 15
Information Technology & Security, page 9
Risk Scenarios Starter Pack, page 7
Which of the following is MOST helpful in developing key risk indicator (KRl) thresholds?
Loss expectancy information
Control performance predictions
IT service level agreements (SLAs)
Remediation activity progress
Key risk indicator (KRI): A metric that measures the level of risk exposure or the likelihood of a risk event1.
KRI threshold: A predefined value or range that triggers an alert or action when the KRI reaches or exceeds it2.
Loss expectancy: The estimated amount of loss that an organization may incur due to a risk event3.
The most helpful thing in developing KRI thresholds is loss expectancy information. Loss expectancy information provides an estimate of the potential or expected impact of a risk event on the organization’s operations, reputation, or objectives. Loss expectancy information can help an organization to:
Quantify and prioritize the risks that pose the greatest threat to the organization
Determine the acceptable level of risk exposure or tolerance for each risk
Set the appropriate value or range for the KRI threshold that reflects the risk appetite and the risk mitigation strategy
Monitor and measure the performance and effectiveness of the risk management process and controls
Loss expectancy information can be derived from various sources, such as historical data, statistical analysis, expert judgment, or simulation models3.
The other options are not as helpful as loss expectancy information in developing KRI thresholds, because they do not directly address the potential or expected impact of a risk event. Control performance predictions, which are the forecasts or estimates of how well the risk management controls will perform in preventing, detecting, or mitigating risks, may help to evaluate the adequacy and efficiency of the risk management process and controls, but they do not provide a clear and quantifiable measure of the risk impact. IT service level agreements (SLAs), which are the contracts or agreements that define the quality and availability of IT services, may help to establish the standards and expectations for IT service delivery and performance, but they do not provide a comprehensive and current view of the risk exposure or likelihood. Remediation activity progress, which is the status or outcome of the actions taken to address and resolve a risk event, may help to monitor and report the effectiveness and compliance of the risk management process and controls, but it is usually done after the risk event has occurred and resolved, not before.
References = Key Risk Indicators: Definition, Examples, and Best Practices, KRI Framework for Operational Risk Management | Workiva, Loss Expectancy: Definition, Calculation, and Examples
During the initial risk identification process for a business application, it is MOST important to include which of the following stakeholders?
Business process owners
Business process consumers
Application architecture team
Internal audit
The MOST important stakeholders to include during the initial risk identification process for a business application are the business process owners, because they are the ones who have the authority and responsibility for the business processes that are supported or enabled by the business application. The business process owners can provide valuable input and feedback on the business objectives, requirements, and expectations of the business application, as well as the potential risks, impacts, and opportunities that may affect the business processes and outcomes. The other options are not as important as the business process owners, because:
Option B: Business process consumers are the ones who use or benefit from the business processes that are supported or enabled by the business application, such as customers, employees, or partners. They can provide useful information and perspectives on the user needs, preferences, and satisfaction of the business application, but they are not as important as the business process owners, who have the ultimate accountability and authority for the business processes and outcomes.
Option C: Application architecture team is the one who designs and develops the technical architecture and components of the business application, such as the hardware, software, network, and data. They can provide technical expertise and guidance on the feasibility, functionality, and security of the business application, but they are not as important as the business process owners, who have the primary stake and interest in the business application and its alignment with the business processes and objectives.
Option D: Internal audit is the one who provides independent assurance and consulting services on the governance, risk management, and control processes of the organization, including the business application. They can provide objective and impartial evaluation and recommendation on the effectiveness and efficiency of the business application and its compliance with the internal and external standards and regulations, but they are not as important as the business process owners, who have the direct involvement and influence on the business application and its performance and value. References = Risk and Information Systems Control Study Manual, 7th Edition, ISACA, 2020, p. 103.
Which of the following would MOST likely result in updates to an IT risk appetite statement?
External audit findings
Feedback from focus groups
Self-assessment reports
Changes in senior management
An IT risk appetite statement is a document that expresses the amount and type of IT risk that an organization is willing to accept or pursue in order to achieve its objectives. An IT risk appetite statement can help guide the IT risk management process, by setting the boundaries, criteria, and targets for IT risk identification, assessment, response, and reporting. An IT risk appetite statement should be aligned with the organization’s overall risk appetite and strategy, and should be reviewed and updated periodically to reflect the changes in the internal and external environment. One of the factors that would most likely result in updates to an IT risk appetite statement is changes in senior management. Senior management is the group of executives who have the authority and responsibility for the strategic direction and performance of the organization. Changes in senior management can affect the IT risk appetite statement, as they may introduce new perspectives, priorities, expectations, or preferences for IT risk taking or avoidance. Changes in senior management can also affect the IT risk appetite statement, as they may require new or revised IT objectives, goals, or initiatives, which may entail different levels or types of IT risk. Therefore, changes in senior management should trigger a review and update of the IT risk appetite statement, to ensure that it is consistent and compatible with the new leadership and direction of the organization. References = Organisations must define their IT risk appetite and tolerance, Risk Appetite Statements - Institute of Risk Management, Develop Your Technology Risk Appetite - Gartner.
Which of the following is the PRIMARY reason to establish the root cause of an IT security incident?
Prepare a report for senior management.
Assign responsibility and accountability for the incident.
Update the risk register.
Avoid recurrence of the incident.
The primary reason to establish the root cause of an IT security incident is to avoid recurrence of the incident. By identifying and addressing the underlying cause of the incident, the organization can prevent or reduce the likelihood of similar incidents in the future. This can also help to improve the security posture and resilience of the organization. The other options are not the primary reason, but they may be secondary or tertiary reasons. Preparing a report for senior management is an important step in communicating the incident and its impact, but it does not address the root cause. Assigning responsibility and accountability for the incident is a way to ensure that the appropriate actions are taken to remediate the incident and prevent recurrence, but it is not the reason to establish the root cause. Updating the risk register is a part of the risk management process, but it does not necessarily prevent recurrence of the incident. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 4: Risk Response and Reporting, Section 4.3: Incident Management, p. 223-224.
A department has been granted an exception to bypass the existing approval process for purchase orders. The risk practitioner should verify the exception has been approved by which of the following?
Internal audit
Control owner
Senior management
Risk manager
A purchase order approval process is a set of procedures that companies use to authorize the purchase of goods or services from suppliers1. This process typically involves multiple levels of approvals, ensuring that purchases are compliant with company regulations and policies, and within budget limitations1. Sometimes, a department may be granted an exception to bypass the existing approval process for purchase orders, for example, due to urgency, emergency, or special circumstances2. However, such exceptions should not compromise the effectiveness and integrity of the purchase order approval process, and should be properly documented and justified2. Therefore, the risk practitioner should verify that the exception has been approved by senior management, as they are ultimately responsible for setting and overseeing the purchase order approval process, and for ensuring that the exceptions are reasonable and aligned with the company’s objectives and risk appetite3. Internal audit is not the correct answer, as they are not involved in approving the purchase order approval process or its exceptions. Internal audit’s role is to provide independent assurance and advice on the adequacy and effectiveness of the purchase order approval process and its controls, and to report any issues or recommendations for improvement4. Control owner is not the correct answer, as they are not involved in approving the purchase order approval process or its exceptions. Control owner’s role is to design, implement, and operate the controls that support the purchase order approval process, and to monitor and report on the performance and compliance of the controls5. Risk manager is not the correct answer, as they are not involved in approving the purchase order approval process or its exceptions. Risk manager’s role is to identify, assess, and mitigate the risks associated with the purchase order approval process, and to communicate and report on the risk status and issues6. References = 1: A Step-by-Step Guide to a Purchase Order Approval Process2: Purchase Order Exceptions | Fordham3: Purchase Order (PO) Approval Process and Approval Workflow - ProcureDesk4: IT Risk Resources | ISACA5: CRISC Resources [updated 2021] | Infosec6: Risk and Information Systems Control Study Manual, Chapter 4: Risk and Control Monitoring and Reporting, Section 4.2: Risk Monitoring, pp. 189-191.
The maturity of an IT risk management program is MOST influenced by:
the organization's risk culture
benchmarking results against similar organizations
industry-specific regulatory requirements
expertise available within the IT department
The maturity of an IT risk management program is most influenced by the organization’s risk culture, as this reflects the shared values, beliefs, and attitudes that shape how the organization perceives and responds to risk. The risk culture determines the level of awareness, commitment, and involvement of the stakeholders in the IT risk management process, as well as the degree of integration and alignment with the enterprise’s objectives and strategy. A mature IT risk management program requires a strong and positive risk culture that fosters trust, collaboration, and accountability among the stakeholders, and supports continuous improvement and learning. The other options are not the most influential factors for the maturity of an IT risk management program, although they may have some impact or relevance. Benchmarking results against similar organizations can provide useful insights and comparisons, but they do not necessarily reflect the organization’s own risk culture or context. Industry-specific regulatory requirements can impose certain standards and expectations, but they do not guarantee the effectiveness or efficiency of the IT risk management program. Expertise available within the IT department can enhance the technical and operational aspects of the IT risk management program, but it does not ensure the strategic and cultural alignment with the enterprise. References = Risk and Information Systems Control Study Manual, Chapter 1: IT Risk Identification, page 23.
Which of the following would BEST help identify the owner for each risk scenario in a risk register?
Determining which departments contribute most to risk
Allocating responsibility for risk factors equally to asset owners
Mapping identified risk factors to specific business processes
Determining resource dependency of assets
A risk register is a tool that records and tracks the identified risks, their causes, impacts, likelihood, responses, and owners. The owner for each risk scenario is the person or group who has the authority and accountability to manage the risk and its response. The best way to identify the owner for each risk scenario in a risk register is to map the identified risk factors to specific business processes. Risk factors are the internal and external variables that influence the occurrence and impact of risks. Business processes are the activities that produce value for the enterprise, such as sales, marketing, production, or delivery. By mapping the risk factors to the business processes, the risk practitioner can determine which business process is affected by or contributes to the risk, and who is responsible for the business process. The owner for each risk scenario should be the person or group who is responsible for the business process that is associated with the risk. The other options are not the best way to identify the owner for each risk scenario, as they involve different criteria or methods:
Determining which departments contribute most to risk means that the risk practitioner evaluates the degree of involvement or exposure of each department to the risk. This may not be a reliable or consistent way to identify the owner for each risk scenario, as the risk may span across multiple departments, or the department may not have the authority or accountability to manage the risk.
Allocating responsibility for risk factors equally to asset owners means that the risk practitioner assigns the same level of responsibility to each person or group who owns an asset that is affected by or contributes to the risk. An asset is a resource that has value for the enterprise, such as hardware, software, data, or people. This may not be a fair or effective way to identify the owner for each risk scenario, as the asset owners may have different levels of involvement or exposure to the risk, or may not have the authority or accountability to manage the risk.
Determining resource dependency of assets means that the risk practitioner analyzes the relationship and interdependence of the assets that are affected by or contribute to the risk. This may help to identify the potential impact or likelihood of the risk, but it does not directly help to identify the owner for each risk scenario, as the resource dependency may not reflect the authority or accountability to manage the risk. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 3, Section 3.1.1.1, pp. 95-96.
Which of the following should be a risk practitioner's NEXT action after identifying a high probability of data loss in a system?
Enhance the security awareness program.
Increase the frequency of incident reporting.
Purchase cyber insurance from a third party.
Conduct a control assessment.
A control assessment is the process of evaluating the design and effectiveness of controls that are implemented to mitigate risks. A control assessment can help identify the root causes of data loss, thegaps in the existing controls, and the potential solutions to improve the control environment. A control assessment should be conducted after identifying a high probability of data loss in a system, as it can provide valuable information for risk response and reporting. References = Risk and Information Systems Control Study Manual, Chapter 3: Risk Response and Mitigation, Section 3.2: Control Assessment, p. 147-149.
Malware has recently affected an organization. The MOST effective way to resolve this situation and define a comprehensive risk treatment plan would be to perform:
a gap analysis
a root cause analysis.
an impact assessment.
a vulnerability assessment.
The most effective way to resolve the situation and define a comprehensive risk treatment plan would be to perform a root cause analysis. A root cause analysis is a method of identifying and addressing the underlying factors or causes that led to the occurrence of a problem or incident1. In this case, the problem or incident is the malware infection that affected the organization. By performing a root cause analysis, the organization can determine how and why the malware was able to infect the systems, what vulnerabilities or weaknesses were exploited, what controls or processes failed or were missing, and what actions or decisions contributed to the situation. A root cause analysis can help the organization to prevent or reduce the recurrence of similar incidents, as well as to improve the effectiveness and efficiency of the risk management process. A root cause analysis can also help the organization to define a comprehensive risk treatment plan, which is a set of actions or measures that are taken to modify the risk, such as reducing, avoiding, transferring, or accepting the risk2. Based on the findings and recommendations of the root cause analysis, the organization can select and implement the most appropriate risk treatment option for the malware risk, as well as for any other related or emerging risks. The risk treatment plan should also include the roles and responsibilities, resources, timelines, and performance indicators for the risk treatmentactions3. The other options are not the most effective ways to resolve the situation and define a comprehensive risk treatment plan, as they are either less thorough or less relevant than a root cause analysis. A gap analysis is a method of comparing the current state and the desired state of a process, system, or organization, and identifying the gaps or differences between them4. A gap analysis can help the organization to identify the areas of improvement or enhancement, as well as the opportunities or challenges for achieving the desired state. However, a gap analysis is not the most effective way to resolve the situation and define a comprehensive risk treatment plan, as it does not address the causes or consequences of the malware infection, or the actions or measures to mitigate the risk. An impact assessment is a method of estimating the potential effects or consequences of a change, decision, or action on a process, system, or organization5. An impact assessment can help the organization to evaluate the benefits and costs, as well as the risks and opportunities, of a proposed or implemented change, decision, or action. However, an impact assessment is not the most effective way to resolve the situation and define a comprehensive risk treatment plan, as it does not investigate the origin or nature of the malware infection, or the solutions or alternatives to manage the risk. A vulnerability assessment is a method of identifying and analyzing the weaknesses or flaws in a process, system, or organization that can be exploited by threats to cause harm or loss6. A vulnerability assessment can help the organization to discover and prioritize the vulnerabilities, as well as to recommend and implement the controls or measures to reduce or eliminate them. However, a vulnerability assessment is not the most effective way to resolve the situation and define a comprehensive risk treatment plan, as it does not consider the root causes or impacts of the malware infection, or the risk treatment options or plans to address the risk. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.1.8, Page 61.
Which of the following is MOST important to consider when assessing the likelihood that a recently discovered software vulnerability will be exploited?
The skill level required of a threat actor
The amount of personally identifiable information (PH) disclosed
The ability to detect and trace the threat action
The amount of data that might be exposed by a threat action
When assessing the likelihood that a recently discovered software vulnerability will be exploited, the most important consideration is the skill level required of a threat actor. Here's an explanation:
Skill Level of Threat Actors:
The skill level required to exploit a vulnerability determines how accessible the exploit is to potential attackers.
If a vulnerability requires advanced technical skills to exploit, it is less likely to be targeted by less sophisticated attackers.
Conversely, if the exploit can be easily executed with minimal skills, it increases the likelihood of widespread exploitation.
Factors Influencing Likelihood of Exploitation:
Availability of Exploit Tools:If automated tools or scripts are available to exploit the vulnerability, even less skilled attackers can take advantage of it.
Publication of Exploit Details:If the vulnerability and its exploitation method are widely published, it becomes more accessible to a broader range of attackers.
Assessment of Likelihood:
Security teams assess the skill level required by analyzing whether the exploit is straightforward or complex.
They also consider the presence of exploit kits in the wild that could lower the barrier to entry for potential attackers.
Comparison with Other Factors:
Amount of PII Disclosed:While important, it relates more to the impact rather than the likelihood of exploitation.
Ability to Detect and Trace:This is crucial for response but does not directly influence the likelihood of exploitation.
Amount of Data Exposed:Similar to PII, this factor pertains to the impact rather than the likelihood of exploitation.
References:
The CRISC Review Manual discusses the importance of understanding the threat landscape, including the skill level of potential attackers (CRISC Review Manual, Chapter 2: IT Risk Assessment, Section 2.2.1 Internal Threats).
A risk assessment has been completed on an application and reported to the application owner. The report includes validated vulnerability findings that require mitigation. Which of the following should be the NEXT step?
Report the findings to executive management to enable treatment decisions.
Reassess each vulnerability to evaluate the risk profile of the application.
Conduct a penetration test to determine how to mitigate the vulnerabilities.
Prepare a risk response that is aligned to the organization's risk tolerance.
Preparing a risk response that is aligned to the organization’s risk tolerance is the next step after completing a risk assessment and reporting the validated vulnerability findings that require mitigation to the application owner, because it helps to define and implement the appropriate actions to reduce or eliminate the risk, or to prepare for and recover from the potential consequences. A risk response is a strategy or tactic for managing the identified risks, such as avoiding, transferring, mitigating, or accepting the risk. A risk response should be aligned to the organization’s risk tolerance, which is the acceptable level of variation from the organization’s objectives or expectations. A vulnerability is a weakness or flaw in an IT system or application that can be exploited by a threat or attack to cause harm or damage. A vulnerability finding is a result of a vulnerability assessment, which is a process of identifying and evaluating the vulnerabilities in an IT system or application. A vulnerability finding requires mitigation, which is a type of risk response that involves applying controls or countermeasures to reduce the likelihood or impact of the risk. Therefore, preparing a risk response that is aligned to the organization’s risk tolerance is the next step, as it helps to address the vulnerability findings and to achieve the desired level of risk. Reporting the findings to executive management, reassessing each vulnerability, and conducting a penetration test are all possible steps to perform after preparing a risk response, but they are not the next step, as they depend on the results and approval of the risk response. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.4.2, page 103
Which of the following information is MOST useful to a risk practitioner for developing IT risk scenarios?
Published vulnerabilities relevant to the business
Threat actors that can trigger events
Events that could potentially impact the business
IT assets requiring the greatest investment
Developing IT Risk Scenarios:
Risk scenarios are hypothetical events that describe potential threats and their impact on business operations. These scenarios are essential for identifying and assessing risks.
Importance of Potential Impact Events:
Events that could potentially impact the business provide the most useful information for developing risk scenarios because they directly relate to the organization’s objectives and operations.
Understanding these events helps in crafting realistic and relevant risk scenarios that can guide risk assessment and mitigation efforts.
Components of Risk Scenarios:
Threat Actors:Identify who might exploit vulnerabilities.
Threat Events:Describe the specific events that could impact the business.
Business Impact:Assess how these events would affect business operations, finances, reputation, etc.
Using Impact Events for Scenario Development:
Focusing on events that could disrupt critical business functions ensures that the scenarios are relevant and actionable.
It enables the risk practitioner to communicate the potential consequences effectively to stakeholders and prioritize mitigation efforts accordingly.
Comparing Other Information Sources:
Published Vulnerabilities:Useful for understanding specific threats but may not directly relate to business impact.
Threat Actors:Important for identifying potential sources of risk but not sufficient alone for scenario development.
IT Assets:Relevant for risk assessment but secondary to understanding potential impact events.
References:
The CRISC Review Manual discusses the importance of considering events that could impact the business when developing risk scenarios (CRISC Review Manual, Chapter 2: IT Risk Assessment, Section 2.4 Risk Scenario Development).
The cost of maintaining a control has grown to exceed the potential loss. Which of the following BEST describes this situation?
Insufficient risk tolerance
Optimized control management
Effective risk management
Over-controlled environment
The situation where the cost of maintaining a control has grown to exceed the potential loss is best described as an over-controlled environment, as it indicates that the control is not cost-effective and may be unnecessary or excessive. Insufficient risk tolerance, optimized control management, and effective risk management are not the best descriptions, as they do not reflect the imbalance between the control cost and the potential loss. References = CRISC Review Manual, 7th Edition, page 149.
Which of the following is the PRIMARY accountability for a control owner?
Communicate risk to senior management.
Own the associated risk the control is mitigating.
Ensure the control operates effectively.
Identify and assess control weaknesses.
The primary accountability for a control owner is to ensure the control operates effectively, as they have the authority and responsibility to design, implement, monitor, and report on the performance and adequacy of the control, and to identify and address any control gaps or deficiencies. Communicating risk to senior management, owning the associated risk the control is mitigating, and identifying and assessing control weaknesses are not the primary accountabilities, as they are more related to the roles and responsibilities of the risk owner, the risk practitioner, or the auditor, respectively, rather than the control owner. References = CRISC Review Manual, 7th Edition, page 101.
Who is PRIMARILY accountable for identifying risk on a daily basis and ensuring adherence to the organization's policies?
Third line of defense
Line of defense subject matter experts
Second line of defense
First line of defense
To implement the MOST effective monitoring of key risk indicators (KRIs), which of the following needs to be in place?
Threshold definition
Escalation procedures
Automated data feed
Controls monitoring
Key risk indicators (KRIs) are the metrics or measures that provide information and insight on the level and trend of the risks that may affect the organization’s objectives and operations. KRIs can help the organization to monitor and communicate the risks, and to support the decision making and planning for the risk management.
To implement the most effective monitoring of KRIs, one of the essential elements that needs to be in place is threshold definition, which is the process of establishing and specifying the acceptable or tolerable ranges or limits for the KRIs, based on the organization’s risk appetite and tolerance. Threshold definition can help the organization to monitor KRIs by providing the following benefits:
It can enable the comparison and evaluation of the actual or current values of the KRIs with the expected or desired values of the KRIs, and to identify and quantify the deviations or variations that may indicate the changes or developments in the risk level or performance.
It can trigger the alerts or notifications when the values of the KRIs exceed or fall below the thresholds, and to initiate the appropriate actions or responses to address or correct the risks and their impacts.
It can provide useful references and benchmarks for the alignment and integration of the KRIs with the organization’s risk management function, and for the compliance with the organization’s risk policies and standards.
The other options are not the essential elements that need to be in place to implement the most effective monitoring of KRIs, because they do not address the main purpose and benefit of threshold definition, which is to establish and specify the acceptable or tolerable ranges or limits for the KRIs.
Escalation procedures are the processes and guidelines for communicating and sharing the information and status of the risks and their responses among the relevant stakeholders, and for escalating or transferring the risks and their responses to the appropriate levels orparties when necessary or required. Escalation procedures can help the organization to monitor KRIs by ensuring the awareness and involvement of the stakeholders, but they are not the essential elements that need to be in place, because they do not establish and specify the acceptable or tolerable ranges or limits for the KRIs.
Automated data feed is the process of using a software tool or system to collect and transmit the data or information that are related or relevant to the KRIs, and to ensure the accuracy, reliability, and timeliness of the data or information. Automated data feed can help the organization to monitor KRIs by providing the data or information that are necessary and relevant for the KRIs, but they are not the essential elements that need to be in place, because they do not establish and specify the acceptable or tolerable ranges or limits for the KRIs.
Controls monitoring is the process of verifying and validating the adequacy and effectiveness of the controls that are intended to ensure the confidentiality, integrity, availability, and reliability of the information systems and resources that are affected by the risks. Controls monitoring can help the organization to monitor KRIs by providing the assurance and evidence on the performance and compliance of the controls, but they are not the essential elements that need to be in place, because they do not establish and specify the acceptable or tolerable ranges or limits for the KRIs. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 40-41, 47-48, 54-55, 58-59, 62-63
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 206
CRISC Practice Quiz and Exam Prep
Which of the following is the GREATEST benefit for an organization with a strong risk awareness culture?
Reducing the involvement by senior management
Using more risk specialists
Reducing the need for risk policies and guidelines
Discussing and managing risk as a team
Discussing and managing risk as a team is the greatest benefit for an organization with a strong risk awareness culture, as it enables the organization to share and communicate the risk information and knowledge among all the stakeholders, and to collaborate and coordinate the risk management activities and responsibilities. Discussing and managing risk as a team can also help to foster a positive and proactive attitude toward risk, and to align the risk management process with the organization’s strategy and objectives. Discussing and managing risk as a team can also enhance the risk governance and accountability, and support the risk learning and improvement. References = Most Asked CRISC Exam Questions and Answers. CRISC: Certified in Risk & Information Systems Control Sample Questions, Question 252. ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, Question 252. CRISC by Isaca Actual Free Exam Q&As, Question 9.
When formulating a social media policy lo address information leakage, which of the following is the MOST important concern to address?
Sharing company information on social media
Sharing personal information on social media
Using social media to maintain contact with business associates
Using social media for personal purposes during working hours
The most important concern to address when formulating a social media policy to address information leakage is sharing company information on social media. Information leakage is the unauthorized or unintentional disclosure of confidential or sensitive information to unauthorized parties. Social media is a platform that enables the users to create and share content, such as text, images, videos, or links, with other users or the public. Sharing company information on social media is the most important concern, as it could expose the company’s trade secrets, intellectual property, customer data, financial data, or strategic plans to competitors, hackers, or regulators. Sharing company information on social media could also damage the company’s reputation, trust, or credibility, and result in legal or regulatory penalties, fines, or lawsuits. Therefore, a social media policy should clearly define what constitutes company information, and what are the rules and guidelines for sharing or not sharing company information on social media. A social media policy should also specify the roles and responsibilities of the employees, managers, and the social media team, and the consequences and sanctions for violating the policy. Sharing personal information on social media, using social media to maintain contact with business associates, and using social media for personal purposes during working hours are not as important as sharing company information on social media, as they do not directly involve the leakage of company information, and they may not have significant impact or risk on the company. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 217
When updating the risk register after a risk assessment, which of the following is MOST important to include?
Historical losses due to past risk events
Cost to reduce the impact and likelihood
Likelihood and impact of the risk scenario
Actor and threat type of the risk scenario
A risk register is a document that records and tracks the information about the risks that may affect the organization’s objectives, such as the risk description, category, source, cause, impact, probability, status, owner, response, etc.
When updating the risk register after a risk assessment, the most important information to include is the likelihood and impact of the risk scenario. This means that the risk register should reflect the current or updated estimates of the probability and consequence of the risk scenario, based on the risk analysis and evaluation methods and criteria.
The likelihood and impact of the risk scenario helps to determine the risk level and priority, select the most appropriate risk response, allocate the resources and budget for risk management, and monitor and report the risk performance and outcomes.
The other options are not the most important information to include when updating the risk register after a risk assessment. They are either secondary or not essential for risk management.
The references for this answer are:
Risk IT Framework, page 29
Information Technology & Security, page 23
Risk Scenarios Starter Pack, page 21
Which of the following tasks should be completed prior to creating a disaster recovery plan (DRP)?
Conducting a business impact analysis (BIA)
Identifying the recovery response team
Procuring a recovery site
Assigning sensitivity levels to data
According to the CRISC Review Manual, conducting a business impact analysis (BIA) is the task that should be completed prior to creating a disaster recovery plan (DRP), because it helps to identify the critical business processes and resources, and their dependencies, that need to be recovered in the event of a disaster. The BIA also helps to determine the recovery time objectives (RTOs) and recovery point objectives (RPOs) for each business process and resource, which are the key inputs for the DRP. The other options are not the tasks that should be completed prior to creating a DRP, as they are part of the DRP itself. Identifying the recovery response team is the task of defining the roles and responsibilities of the personnel involved in the recovery process. Procuring a recovery site is the task of selecting and acquiring an alternative location where the business operations can be resumed. Assigning sensitivity levels to data is the task of classifying the data based on its importance and protection requirements. References = CRISC Review Manual, 7th Edition, Chapter 5, Section 5.2.1, page 237.
Which of the following BEST indicates whether security awareness training is effective?
User self-assessment
User behavior after training
Course evaluation
Quality of training materials
Security awareness training is a process of educating and informing the users about the security policies, procedures, and best practices of the organization, and the potential threats and risks that may affect the confidentiality, integrity, and availability of the information and systems.
The best indicator of whether security awareness training is effective is user behavior after training. This means that the users demonstrate and apply the knowledge and skills that they have learned from the training, such as following the security rules and guidelines, reporting any security incidents or issues, avoiding any risky or malicious actions, etc.
User behavior after training helps to measure the actual impact and outcome of the training, compare them with the expected or desired objectives and standards, identify any gaps or issues that may affect the training effectiveness or efficiency, and take appropriate actions to address them.
The other options are not the best indicators of whether security awareness training is effective. They are either subjective or not essential for security awareness training.
The references for this answer are:
Risk IT Framework, page 30
Information Technology & Security, page 24
Risk Scenarios Starter Pack, page 22
Risk acceptance of an exception to a security control would MOST likely be justified when:
automation cannot be applied to the control
business benefits exceed the loss exposure.
the end-user license agreement has expired.
the control is difficult to enforce in practice.
The most likely justification for risk acceptance of an exception to a security control is when the business benefits exceed the loss exposure. Risk acceptance is a risk response strategy that involves acknowledging and tolerating the risk, without taking any action to reduce or transfer the risk. An exception to a security control is a deviation or non-compliance from the established security policy or standard, due to a valid business reason or circumstance. Risk acceptance of an exception to a security control may be justified when the business benefits exceed the loss exposure, which means that the value or advantage of the exception outweighs the potential cost or harm of the risk. For example, an exception to a security control may enable faster or easier access to the system or data, which may improve the productivity, efficiency, or satisfaction of the users or customers, and generate more revenue or profit for the business. The business benefits of the exception may exceed the loss exposure of the risk, which may be low or negligible, or may be mitigated by other controls or factors. Therefore, risk acceptance of an exception to a security control may be a reasonable and rational decision, based on the cost-benefit analysis of the exception and the risk. Automation cannot be applied to the control, the end-user license agreement has expired, and the control is difficult to enforce in practice are not the most likely justifications for risk acceptance of an exception to a security control, as they are either irrelevant or insufficient reasons, and they do not consider the business benefits or the loss exposure of the exception and the risk. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 50.
When of the following provides the MOST tenable evidence that a business process control is effective?
Demonstration that the control is operating as designed
A successful walk-through of the associated risk assessment
Management attestation that the control is operating effectively
Automated data indicating that risk has been reduced
Automated data indicating that risk has been reduced provides the most tenable evidence that a business process control is effective, because it shows the actual impact and outcome of the control on the risk level. A demonstration that the control is operating as designed, a successful walk-through of the associated risk assessment, and a management attestation that the control is operating effectively are not the most tenable evidence, because they are based on subjective judgments, assumptions, or expectations, not on objective facts or results. References = CRISC: Certified in Risk & Information Systems Control Sample Questions
What is the PRIMARY benefit of risk monitoring?
It reduces the number of audit findings.
It provides statistical evidence of control efficiency.
It facilitates risk-aware decision making.
It facilitates communication of threat levels.
Risk monitoring is the process of tracking and evaluating the performance and effectiveness of the risk management process and controls, and identifying any changes or emerging risks that may affect theenterprise’s objectives and strategy. The primary benefit of risk monitoring is that it facilitates risk-aware decision making, as it provides timely and relevant information and feedback to the decision-makers and stakeholders, and enables them to adjust the risk strategy and response actions accordingly. Risk monitoring also helps to ensure that the risk management process is aligned with the enterprise’s risk appetite and tolerance, and supports the achievement of the enterprise’s goals and value creation. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, Question 239. CRISC: Certified in Risk & Information Systems Control Sample Questions, Question 239. CRISC Sample Questions 2024, Question 239.
Which of the following is the MOST common concern associated with outsourcing to a service provider?
Lack of technical expertise
Combining incompatible duties
Unauthorized data usage
Denial of service attacks
The most common concern associated with outsourcing to a service provider is unauthorized data usage, which means the misuse, disclosure, or theft of the organization’s data by the service provider or its employees, contractors, or subcontractors1. Unauthorized data usage can pose significant risks to the organization, such as:
Data security and privacy breaches, which can compromise the confidentiality, integrity, and availability of the data, and expose the organization to legal liability, regulatory penalties, reputational damage, or loss of trust and credibility2.
Data quality and accuracy issues, which can affect the reliability and validity of the data, and impair the decision-making, reporting, or performance of the organization3.
Data ownership and control issues, which can limit the access and rights of the organization to its own data, and create dependency or lock-in with the service provider4.
The other options are not the most common concern associated with outsourcing to a service provider, because:
Lack of technical expertise is a potential but not prevalent concern associated with outsourcing to a service provider, as it may affect the quality and efficiency of the services provided by the service provider, and the compatibility and integration of the services with the organization’s systems and processes5. However, most service providers have sufficient technical expertise in their domain or field, and they can offer specialized skills or resources that the organization may not have internally6.
Combining incompatible duties is a possible but not frequent concern associated with outsourcing to a service provider, as it may create conflicts of interest or segregation of duties issues for the service provider or the organization, and increase the risk of errors, fraud, or abuse7. However, most service providers have adequate governance and control mechanisms to prevent or mitigate such issues, and they can adhere to the organization’s policies and standards regarding the separation of duties8.
Denial of service attacks is a rare but not common concern associated with outsourcing to a service provider, as it may disrupt the availability or functionality of the services provided by the service provider, and affect the operations or continuity of the organization. However, most service providers have robust security measures and contingency plans to protect and recover from such attacks, and they can ensure the resilience and reliability of the services.
References =
Unauthorized Data Usage - CIO Wiki
What is outsourcing? Definitions, benefits, challenges, processes, advice | CIO
The Pros and Cons of Outsourcing in 2023 - GrowthForce
13 Common Problems of Outsourcing and How to Avoid Them - ENOU Labs
The Top 10 Problems with Outsourcing Implementation - SSON
10 problems with outsourcing (+ Solutions for each) - Time Doctor Blog
Segregation of Duties - CIO Wiki
Outsourcing Governance - CIO Wiki
[Denial-of-Service Attack - CIO Wiki]
[Business Continuity Planning - CIO Wiki]
Which of the following is the MOST effective control to maintain the integrity of system configuration files?
Recording changes to configuration files
Implementing automated vulnerability scanning
Restricting access to configuration documentation
Monitoring against the configuration standard
According to the CRISC Review Manual, monitoring against the configuration standard is the most effective control to maintain the integrity of system configuration files, because it ensures that any unauthorized or unintended changes are detected and corrected. Monitoring against the configuration standard involves comparing the actual configuration of the system with the approved baseline and identifying any deviations or discrepancies. The other options are not the most effective controls, because they do not ensure the integrity of the system configuration files. Recording changes to configuration files is a good practice, but it does not prevent unauthorized or unintended changes from occurring. Implementing automated vulnerability scanning is a preventive control that helps to identify and remediate potential weaknesses in the system, but it does not verify the integrity of the configuration files. Restricting access to configuration documentation is a security measure that limits the exposure of sensitive information, but it does not prevent unauthorized or unintended changes to the configuration files. References = CRISC Review Manual, 7th Edition, Chapter 4, Section 4.2.3, page 184.
Which of the following is the GREATEST advantage of implementing a risk management program?
Enabling risk-aware decisions
Promoting a risk-aware culture
Improving security governance
Reducing residual risk
A risk management program is a systematic and structured approach to identify, analyze, evaluate, treat, monitor, and communicate the risks that may affect the organization’s objectives and performance.
The greatest advantage of implementing a risk management program is enabling risk-aware decisions. This means that the organization incorporates the risk information and analysis into its decision making process, such as strategic planning, resource allocation, project management, etc.
Enabling risk-aware decisions helps to optimize the outcomes and benefits of the decisions, balance the opportunities and threats of the decisions, and align the decisions with the organization’s risk appetite and tolerance.
The other options are not the greatest advantages of implementing a risk management program. They are either secondary or not essential for risk management.
The references for this answer are:
Risk IT Framework, page 25
Information Technology & Security, page 19
Risk Scenarios Starter Pack, page 17
The PRIMARY objective for requiring an independent review of an organization's IT risk management process should be to:
assess gaps in IT risk management operations and strategic focus.
confirm that IT risk assessment results are expressed as business impact.
verify implemented controls to reduce the likelihood of threat materialization.
ensure IT risk management is focused on mitigating potential risk.
The primary objective for requiring an independent review of an organization’s IT risk management process should be to assess gaps in IT risk management operations and strategic focus, as this helps to identify the strengths and weaknesses of the current process, and to provide recommendations for improvement and alignment with the enterprise’s objectives and environment. An independent review is an objective and unbiased evaluation of the IT risk management process by a qualified and competent party that is not involved in the process. An independent review can help to ensure the quality, effectiveness, and efficiency of the IT risk management process, as well as to enhance the credibility and confidence of the process. Confirming that IT risk assessment results are expressed as business impact, verifying implemented controls to reduce the likelihood of threat materialization, and ensuring IT risk management is focused on mitigating potential risk are not the primary objectives for requiring an independent review of an organization’s IT risk management process, but rather the expected outcomes or benefits of the independent review. References = CRISC Certified in Risk and Information Systems Control – Question219; ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 219.
A highly regulated organization acquired a medical technology startup company that processes sensitive personal information with weak data protection controls. Which of the following is the BEST way for the acquiring company to reduce its risk while still enabling the flexibility needed by the startup company?
Identify previous data breaches using the startup company’s audit reports.
Have the data privacy officer review the startup company’s data protection policies.
Classify and protect the data according to the parent company's internal standards.
Implement a firewall and isolate the environment from the parent company's network.
Data protection is the process of safeguarding sensitive personal information from unauthorized access, use, disclosure, modification, or destruction. Data protection can help to ensure the privacy and security ofthe data subjects, and to comply with the legal and regulatory requirements that apply to the data processing activities1.
A highly regulated organization that acquired a medical technology startup company that processes sensitive personal information with weak data protection controls faces a high risk of data breaches, fines, lawsuits, reputational damage, or loss of customer trust. The best way for the acquiring company to reduce its risk while still enabling the flexibility needed by the startup company is to classify and protect the data according to the parent company’s internal standards, because it can help to:
Identify and categorize the sensitive personal information based on its value, sensitivity, and criticality, such as confidential, restricted, internal, or public
Apply and enforce the appropriate data protection policies, procedures, and controls for each data category, such as encryption, access control, backup, retention, or disposal
Align and integrate the data protection practices and processes of the startup company with those of the parent company, and ensure the consistency and compliance across the organization
Balance and optimize the trade-off between data protection and data usability, and allow the startup company to leverage the data for innovation and growth, as long as it meets the data protection standards of the parent company23
The other options are not the best ways for the acquiring company to reduce its risk while still enabling the flexibility needed by the startup company, but rather some of the steps or aspects of data protection. Identify previous data breaches using the startup company’s audit reports is a step that can help to assess the current data protection status and gaps of the startup company, and to learn from the past incidents and mistakes, but it does not address the future data protection needs and challenges of the startup company. Have the data privacy officer review the startup company’s data protection policies is an aspect that can help to ensure the legal and regulatory compliance of the data protection activities of the startup company, and to provide guidance and oversight for the data protection issues and risks, but it does not ensure the technical and operational effectiveness and efficiency of the data protection controls of the startup company. Implement a firewall and isolate the environment from the parent company’s network is a control that can help to prevent or limit the external or internal attacks or threats to the data of the startup company, and to reduce the exposure or impact of a data breach, but it does not ensure the availability or accessibility of the data for the legitimate and authorized purposes of the startup company. References =
Data Protection - ISACA
Data Classification - ISACA
Data Protection Best Practices - ISACA
[CRISC Review Manual, 7th Edition]
Which of the following is the BEST course of action to help reduce the probability of an incident recurring?
Perform a risk assessment.
Perform root cause analysis.
Initiate disciplinary action.
Update the incident response plan.
An incident is an unplanned event that disrupts or degrades the normal operation or performance of an IT service, system, or network1. An incident can cause various negative impacts, such as service outages, data losses, security breaches, or customer dissatisfaction2. An incident can recur if the underlying cause or problem of the incident is not properly identified and resolved3.
The best course of action to help reduce the probability of an incident recurring is to perform root cause analysis. Root cause analysis is a systematic process of finding and eliminating the fundamental cause or problem that led to the incident4. Root cause analysis can help to:
Prevent or minimize the recurrence of the incident by addressing the source of the problem, not just the symptoms or effects
Identify and implement corrective or preventive actions that can effectively resolve or mitigate the problem
Learn from the incident and improve the IT service, system, or network quality and reliability
Enhance the incident management and problem management processes and capabilities5
References = What is an Incident?, Incident Management - Wikipedia, Problem Management - Wikipedia, Root Cause Analysis - Wikipedia, Root Cause Analysis: A Guide for Business Leaders
Which of the following is the MOST useful information an organization can obtain from external sources about emerging threats?
Solutions for eradicating emerging threats
Cost to mitigate the risk resulting from threats
Indicators for detecting the presence of threatsl)
Source and identity of attackers
•External sources of emerging threats are sources that provide information about the latest cyberattacks, hacking techniques, malware, and vulnerabilities that can affect an organization’s IT systems and data. Examples of external sources are security blogs, forums, newsletters, reports, and alerts from reputable organizations such as ISACA, Imperva, Aura, and BitSight123.
•The most useful information an organization can obtain from external sources is the indicators for detecting the presence of threats. Indicators are observable signs or patterns that can help identify, prevent, or mitigate cyberattacks. Examples of indicators are IP addresses, domain names, file hashes, network traffic, system logs, and user behavior4.
•Indicators for detecting the presence of threats are more useful than the other options because they can help an organization to:
oMonitor and analyze its IT environment for any suspicious or malicious activity
oRespond quickly and effectively to any potential or actual incidents
oReduce the impact and damage of cyberattacks
oImprove its security posture and resilience
•Solutions for eradicating emerging threats are not the most useful information because they may not be applicable or effective for every organization, depending on its specific context, needs, and resources. Moreover, solutions may not be available or known for some new or sophisticated threats.
•Cost to mitigate the risk resulting from threats is not the most useful information because it does not help an organization to identify or prevent cyberattacks. Cost is only one factor to consider when deciding how to manage IT risk, and it may not reflect the true value or impact of the threats.
•Source and identity of attackers are not the most useful information because they may not be relevant or accurate for every organization. Source and identity of attackers are often difficult to trace or verify, and they may not affect the organization’s risk level or response strategy.
References =
•Risk and Information Systems Control Study Manual, 7th Edition, ISACA, 2020, Chapter 2: IT Risk Assessment, Section 2.3: Risk Identification, pp. 83-84
•Risk and Information Systems Control Review Questions, Answers & Explanations Database, 12 Month Subscription, ISACA, 2020, Question ID: 100000
Which of the following should be the FIRST consideration when a business unit wants to use personal information for a purpose other than for which it was originally collected?
Informed consent
Cross border controls
Business impact analysis (BIA)
Data breach protection
According to the GDPR, personal data shall be collected for specified, explicit and legitimate purposes and not further processed in a manner that is incompatible with those purposes1. This means that a business unit can only use personal information for a different purpose if it has obtained the consent of the data subject, or if it has a clear legal basis or obligation to do so2. Therefore, informed consent should be the first consideration when a business unit wants to use personal information for a purpose other than for which it was originally collected.
References = GDPR Article 5 (1) (b) and Article 6 (4)1, ICO Principle (b): Purpose limitation2
Which of the following observations from a third-party service provider review would be of GREATEST concern to a risk practitioner?
Service level agreements (SLAs) have not been met over the last quarter.
The service contract is up for renewal in less than thirty days.
Key third-party personnel have recently been replaced.
Monthly service charges are significantly higher than industry norms.
The observation from a third-party service provider review that would be of greatest concern to a risk practitioner is that the service level agreements (SLAs) have not been met over the last quarter, as it indicates a significant performance issue or breach that may affect the quality, functionality, or security of the outsourced services, and may require a remediation or escalation action. The other options are not the greatest concerns, as they may not indicate a performance issue or breach, but rather a contractual, personnel, or financial issue, respectively, that may not affect the outsourced services directly or significantly. References = CRISC Review Manual, 7th Edition, page 111.
Which of the following would be considered a vulnerability?
Delayed removal of employee access
Authorized administrative access to HR files
Corruption of files due to malware
Server downtime due to a denial of service (DoS) attack
According to the CRISC Review Manual (Digital Version), a vulnerability is a flaw or weakness in an asset’s design, implementation, or operation and management that could be exploited by a threat. A delayed removal of employee access is a vulnerability, as it allows former employees to retain access to the organization’s IT assets and processes, which could lead to unauthorized disclosure, modification, or destruction of data or resources. A delayed removal of employee access could be caused by poor personnel management, lack of security awareness, or inadequate access control policies and procedures.
References = CRISC Review Manual (Digital Version), Chapter 1: IT Risk Identification, Section 1.5: IT Risk Identification Methods and Techniques, pp. 32-331
The BEST way to mitigate the high cost of retrieving electronic evidence associated with potential litigation is to implement policies and procedures for:
data classification and labeling.
data logging and monitoring.
data retention and destruction.
data mining and analytics.
An organization has updated its acceptable use policy to mitigate the risk of employees disclosing confidential information. Which of the following is the BEST way to reinforce the effectiveness of this policy?
Communicate sanctions for policy violations to all staff.
Obtain signed acceptance of the new policy from employees.
Train all staff on relevant information security best practices.
Implement data loss prevention (DLP) within the corporate network.
Train all staff on relevant information security best practices, because it helps to increase the awareness and understanding of the employees regarding the acceptable use policy and its purpose, and to improve their skills and knowledge on how to protect and handle confidential information. An acceptable use policy is a document that outlines the standards and expectations for the proper usage of the organization’s IT resources, such as systems, applications, networks, or devices, and the consequences of non-compliance. Confidential information is information that is sensitive or proprietary, and may cause harm or damage to the organizationor its stakeholders if disclosed or compromised, such as trade secrets, customer data, or financial records. Training all staff on relevant information security best practices is the best way to reinforce the effectiveness of the policy, as it helps to ensure that the employees are aware of and comply with the policy, and that they adopt the appropriate behaviors and techniques to prevent or mitigate the risk of disclosing confidential information.
Communicating sanctions for policy violations to all staff, obtaining signed acceptance of the new policy from employees, and implementing data loss prevention (DLP) within the corporate network are all possible ways to reinforce the effectiveness of the policy, but they are not the best way, as they do not directly address the awareness and understanding of the employees regarding the policy and its purpose, and they may not be sufficient or effective to prevent or mitigate the risk of disclosing confidential information.
Which of the following is the GREATEST benefit of centralizing IT systems?
Risk reporting
Risk classification
Risk monitoring
Risk identification
Centralizing IT systems is a process of consolidating and integrating the IT systems or resources in the organization into a single or unified platform or location. Centralizing IT systems helps to improve risk reporting, because it helps to simplify and standardize the risk management process and activities, and to enhance the visibility and transparency of the IT risks and controls. Centralizing IT systems also helps to improve risk reporting, because it helps to facilitate and automate the risk data collection, analysis, and evaluation, and to provide consistent and comprehensive risk information and insights to the organization’s stakeholders, such as the board, management, business units, and IT functions. The other options are not the greatest benefit of centralizing IT systems, although they may be related to the risk management process. Risk classification, risk monitoring, and risk identification are all activities that can help to support or improve the risk management process, but they do not necessarily benefit from centralizing IT systems
Which of the following s MOST likely to deter an employee from engaging in inappropriate use of company owned IT systems?
A centralized computer security response team
Regular performance reviews and management check-ins
Code of ethics training for all employees
Communication of employee activity monitoring
Employee activity monitoring is the process of tracking and recording the actions and behaviors of employees on company owned IT systems, such as email, internet, applications, etc. The purpose of employee activity monitoring is to ensure compliance with the company’s policies and regulations, prevent data leakage and misuse, detect and deter inappropriate or malicious activities, and improve productivity and performance. The most likely way to deter an employee from engaging in inappropriate use of company owned IT systems is to communicate the employee activity monitoring policy and practice to the employees, and make them aware of the consequences of violating the policy. By doing so, the company can create a deterrent effect and discourage the employees from misusing the IT systems, as they know that their actions are being monitored and recorded, and that they will be held accountable for any misconduct. References = CRISC Review Manual, 7th Edition, page 181.
The PRIMARY reason for tracking the status of risk mitigation plans is to ensure:
the proposed controls are implemented as scheduled.
security controls are tested prior to implementation.
compliance with corporate policies.
the risk response strategy has been decided.
The primary reason for tracking the status of risk mitigation plans is to ensure that the proposed controls are implemented as scheduled, as this can help to reduce the risk exposure of the organization and to achieve the desired risk objectives. Tracking the status of risk mitigation plans can also help to monitor and evaluate the performance and effectiveness of the risk controls, and to identify and address any issues or gaps that may arise during the implementation. Tracking the status of risk mitigation plans can also provide feedback and information to the risk owners and stakeholders, and enable them to adjust the risk strategy and response actions accordingly. References = CRISC: Certified in Risk & Information Systems Control Sample Questions, Question 251. CRISC Sample Questions 2024, Question 251. ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, Question 251. CRISC by Isaca Actual Free Exam Q&As, Question 9.
To reduce costs, an organization is combining the second and third tines of defense in a new department that reports to a recently appointed C-level executive. Which of the following is the GREATEST concern with this situation?
The risk governance approach of the second and third lines of defense may differ.
The independence of the internal third line of defense may be compromised.
Cost reductions may negatively impact the productivity of other departments.
The new structure is not aligned to the organization's internal control framework.
The greatest concern with the situation of combining the second and third lines of defense in a new department that reports to a recently appointed C-level executive is that the independence of the internal third line of defense may be compromised. The second line of defense is the function that oversees and supports the risk management activities of the first line of defense, which is the function that owns and manages the risks. The third line of defense is the function that provides independent assurance of the risk management activities, such as the internal audit function. Combining the second and third lines of defense in a new department may compromise the independence of the internal third line of defense, as it may create a conflict of interest, bias, or influence among the functions, and impair the objectivity, credibility, and quality of the assurance activities. The independence of the internal third line of defense is essential for ensuring that the risk management activities are performed in a consistent and effective manner, and that the issues and gaps are identified and reported without fear or favor. The risk governanceapproach of the second and third lines of defense may differ, cost reductions may negatively impact the productivity of other departments, and the new structure may not be aligned to the organization’s internal control framework are also concerns, but they are not as great as the compromise of the independence of the internal third line of defense, as they do not directly affect the assurance and accountability of the risk management activities. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 36.
Which of the following should be the risk practitioner's FIRST course of action when an organization plans to adopt a cloud computing strategy?
Request a budget for implementation
Conduct a threat analysis.
Create a cloud computing policy.
Perform a controls assessment.
The first course of action for a risk practitioner when an organization plans to adopt a cloud computing strategy is to perform a controls assessment. This means evaluating the existing controls in the organization and the cloud service provider, and identifying the gaps and weaknesses that need to be addressed. A controls assessment can help to determine the level of risk exposure and the suitability of the cloud service model and provider for the organization’s needs and objectives. It can also help to establish the baseline for monitoring and reporting on the cloud service performance and compliance. References = Risk and Information Systems Control Study Manual, Chapter 5, Section 5.3.2.2, p. 242-243
Which of the following is the BEST method for assessing control effectiveness against technical vulnerabilities that could be exploited to compromise an information system?
Vulnerability scanning
Systems log correlation analysis
Penetration testing
Monitoring of intrusion detection system (IDS) alerts
Penetration testing is the best method for assessing control effectiveness against technical vulnerabilities that could be exploited to compromise an information system, as it simulates a real-world attack scenario and evaluates the security posture of the system. Penetration testing is a type of security testing that involves performing authorized and ethical hacking activities on a system to identify and exploit its vulnerabilities and weaknesses. Penetration testing can help to measure and improve the effectiveness and efficiency of the controls implemented to protect the system from unauthorized access, modification, or damage.
The other options are not the best methods for assessing control effectiveness against technical vulnerabilities that could be exploited to compromise an information system. Vulnerability scanning is an automated process that uncovers potential vulnerabilities in systems and software, but it does not provide information on the impact and severity of the vulnerability or how they can be exploited using different exploitation techniques1. Systems log correlation analysis is a process of examining and analyzing the records of system activities and events, but it does not directly test the controls or simulate the attack scenarios. Monitoring of intrusion detection system (IDS) alerts is a process of tracking and auditing the system or network for any signs of malicious or anomalous activities, but it does not evaluate the control performance or identify the root causes of the vulnerabilities. References = Vulnerability Assessment Principles | Tenable®, A Complete Guide on Vulnerability Assessment Methodology, Karen Scarfone Scarfone Cybersecurity - NIST Computer Security Resource …
An organization is implementing internet of Things (loT) technology to control temperature and lighting in its headquarters. Which of the following should be of GREATEST concern?
Insufficient network isolation
impact on network performance
insecure data transmission protocols
Lack of interoperability between sensors
Insecure data transmission protocols should be of greatest concern when an organization is implementing internet of Things (IoT) technology to control temperature and lighting in its headquarters, because they can expose the IoT devices and data to unauthorized access, interception, or manipulation. Insecure data transmission protocols can also compromise the confidentiality, integrity, and availability of the IoT system and the information it collects and transmits. The other options are not the greatest concerns, although they may also pose some challenges or risks to the IoT implementation. Insufficient network isolation, impact on network performance, and lack of interoperability between sensors are examples of technical or operational issues that can affect the functionality, efficiency, or compatibility of the IoT system, but they do not have the same severity or impact as insecure data transmission protocols. References = CRISC Sample Questions 2024
The acceptance of control costs that exceed risk exposure is MOST likely an example of:
low risk tolerance.
corporate culture misalignment.
corporate culture alignment.
high risk tolerance
Corporate culture is the set of values, beliefs, and norms that shape the behavior and attitude of an organization and its people. Corporate culture alignment is the degree of consistency and compatibility between the corporate culture and the organization’s vision, mission, strategy, and objectives. Corporate culture misalignment is the situation where the corporate culture is not aligned with the organization’s goals and expectations, and may hinder or undermine the achievement of those goals. The acceptance of control costs that exceed risk exposure is most likely an example of corporate culture misalignment, as it indicates that the organization is not following a rational and optimal approach to risk management. The organization is spending more resources on controlling risks than the potential benefits or losses that the risks entail, which may result in inefficiency, waste, or opportunity cost. The organization may also be overemphasizing the importance of risk avoidance or mitigation, and neglecting the potential value creation or innovation that may arise from taking or accepting some risks. The other options are not the best answers, as they do not explain the situation of accepting control costs that exceed risk exposure. Low risk tolerance is the degree of variation from the risk appetite that the organization is not willing to accept. Low risk tolerance may lead to excessive or unnecessary controls, but it does not necessarily mean that the control costs exceed the riskexposure. High risk tolerance is the degree of variation from the risk appetite that the organization is willing to accept. High risk tolerance may lead to insufficient or ineffective controls, but it does not imply that the control costs exceed the risk exposure. Corporate culture alignment is the situation where the corporate culture is aligned with the organization’s goals and expectations, and supports and facilitates the achievement of those goals. Corporate culture alignment would not result inaccepting control costs thatexceed risk exposure, as it would imply a balanced and rational approach to risk management. References = CRISC Review Manual, pages 22-231; CRISC Review Questions, Answers & Explanations Manual, page 812
Which of the following resources is MOST helpful to a risk practitioner when updating the likelihood rating in the risk register?
Risk control assessment
Audit reports with risk ratings
Penetration test results
Business impact analysis (BIA)
Penetration test results are the most helpful resource to a risk practitioner when updating the likelihood rating in the risk register. Penetration testing is a method of simulating real-world attacks on an IT system or network to identify and exploit vulnerabilities and measure the potential impact. Penetration test results provide empirical evidence of the existence and severity of vulnerabilities, as well as the ease and probability of exploitation. These results can help the risk practitioner to update the likelihood rating of the risks associated with the vulnerabilities, and to prioritize the risk response actions. Risk control assessment, audit reports with risk ratings, and business impact analysis (BIA) are also useful resources for risk management, but they are not as directly related to the likelihood rating as penetration test results. References = Risk and Information Systems Control Study Manual, Chapter 2, Section 2.3.3, page 2-28.
Which of the following is PRIMARILY a risk management responsibly of the first line of defense?
Implementing risk treatment plans
Validating the status of risk mitigation efforts
Establishing risk policies and standards
Conducting independent reviews of risk assessment results
The primary risk management responsibility of the first line of defense is to implement risk treatment plans. The first line of defense is the operational management and staff who are directly involved in the execution of the business activities and processes. They are responsible for identifying, assessing, and responding to the risks that affect their objectives and performance. Implementing risk treatment plans means applying the appropriate risk response strategies and actions to address the identified risks, and monitoring and reporting the results and outcomes of the risk treatment. The other options are not as primary as implementing risk treatment plans, as they are related to the validation, establishment, or review of the risk management process, not the execution of the risk management process. References = Risk and Information Systems Control Study Manual, Chapter 1: IT Risk Identification, Section 1.1: IT Risk Management Process, page 15.
Which of the following will help ensure the elective decision-making of an IT risk management committee?
Key stakeholders are enrolled as members
Approved minutes ate forwarded to senior management
Committee meets at least quarterly
Functional overlap across the business is minimized
The best way to ensure the effective decision-making of an IT risk management committee is to enroll key stakeholders as members. Key stakeholders are the individuals or groups who have an interest or influence in the IT risk management process, such as business owners, senior management, IT managers, auditors, regulators, customers, and suppliers. By involving key stakeholders in the IT risk management committee, the committee can benefit from their diverse perspectives, expertise, and experience, and ensure that the IT risk management decisions are aligned with the business objectives, priorities, and expectations. Key stakeholders can also provide valuable input, feedback, and support for the IT risk management activities, and help communicate and implement the IT risk management decisions across the organization. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 36.
Which of the following presents the GREATEST risk to change control in business application development over the complete life cycle?
Emphasis on multiple application testing cycles
Lack of an integrated development environment (IDE) tool
Introduction of requirements that have not been approved
Bypassing quality requirements before go-live
The greatest risk to change control in business application development over the complete life cycle is the introduction of requirements that have not been approved. Requirements are the specifications or expectations of the business users or stakeholders for the application, such as the features, functions, or performance1. Change control is the process of identifying, evaluating, approving, and implementing changes to the application, such as the design, code, or configuration2. By introducing requirements that have not been approved, the organization can face significant risks, such as:
Scope creep, which is the uncontrolled or unauthorized expansion of the project scope, and can result in increased costs, delays, or errors3.
Quality issues, which can affect the reliability, usability, or security of the application, and can lead to defects, failures, or breaches4.
Stakeholder dissatisfaction, which can arise from the mismatch or inconsistency between the delivered application and the expected application, and can cause complaints, disputes, or litigation5.
The other options are not the greatest risk to change control, because:
Emphasis on multiple application testing cycles is not a risk, but rather a benefit or a best practice for change control, as it can help to ensure that the application meets the requirements and standards, and that the changes are effective and efficient.
Lack of an integrated development environment (IDE) tool is a challenge, but not a risk, for change control, as it can affect the productivity, collaboration, or integration of the developers, and can cause difficulties or inefficiencies in the development process. However, it does not directly affect the requirements or the quality of the application, and it can be overcome by using other tools or methods.
Bypassing quality requirements before go-live is a risk, but not the greatest risk, for change control, as it can compromise the quality or performance of the application, and can expose the organization to errors, failures, or breaches. However, it is less likely or frequent than introducing requirements that have not been approved, and it can be detected or prevented by using quality assurance or quality control techniques.
References =
Requirements - CIO Wiki
Change Control - CIO Wiki
Scope Creep - CIO Wiki
Quality - CIO Wiki
Stakeholder Management - CIO Wiki
[Software Testing - CIO Wiki]
[Integrated Development Environment (IDE) - CIO Wiki]
[Quality Requirements - CIO Wiki]
[Software Development Life Cycle - CIO Wiki]
A risk manager has determined there is excessive risk with a particular technology. Who is the BEST person to own the unmitigated risk of the technology?
IT system owner
Chief financial officer
Chief risk officer
Business process owner
The best person to own the unmitigated risk of the technology is the IT system owner. The IT system owner is the person or entity that has the authority and responsibility for the acquisition, development, maintenance, and operation of the IT system. The IT system owner is also responsible for ensuring that the IT system meets the business requirements, security standards, and compliance obligations of the enterprise. The IT system owner should own the unmitigated risk of the technology, as they are in the best position to understand the nature and impact of the risk, and to implement the appropriate risk responses to reduce the risk exposure to an acceptable level. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 1, Section 1.3.1, page 251234
Which of the following is the PRIMARY reason to use key control indicators (KCIs) to evaluate control operating effectiveness?
To measure business exposure to risk
To identify control vulnerabilities
To monitor the achievement of set objectives
To raise awareness of operational issues
Key control indicators (KCIs) are metrics that measure how well a specific control is performing in reducing the causes, consequences, or likelihood of a risk1. KCIs are used to evaluate the control operating effectiveness, which is the degree to which a control achieves its intended objectives and mitigates the risk2.
The primary reason to use KCIs to evaluate control operating effectiveness is to monitor the achievement of set objectives. This means that KCIs help to:
Track and report the progress and performance of the control against the predefined targets, standards, or benchmarks
Identify and address any gaps, deviations, or issues in the control operation or outcome
Provide feedback and assurance to the stakeholders and regulators on the adequacy and reliability of the control
Support the continuous improvement and optimization of the control3
References = Key Control Indicator (KCI) - CIO Wiki, Evaluating and Improving Internal Control in Organizations - IFAC, A Methodical Approach to Key Control Indicators
A risk practitioner is developing a set of bottom-up IT risk scenarios. The MOST important time to involve business stakeholders is when:
updating the risk register
documenting the risk scenarios.
validating the risk scenarios
identifying risk mitigation controls.
Validating the risk scenarios is the most important time to involve business stakeholders, as they can provide feedback on the relevance, completeness, and accuracy of the scenarios. They can also help to ensure that the scenarios are aligned with the business objectives, context, and risk appetite. By involving business stakeholders in the validation process, the risk practitioner can increase the credibility and acceptance of the risk scenarios.
Updating the risk register, documenting the risk scenarios, and identifying risk mitigation controls are all important steps in the risk scenario development process, but they are not the most important time to involve business stakeholders. These steps can be performed by the risk practitioner with input from othersources, such as subject matter experts, historical data, industry standards, etc. References = CRISC Review Manual, 7th Edition, ISACA, 2020, page 47-481
A risk practitioner has been asked by executives to explain how existing risk treatment plans would affect risk posture at the end of the year. Which of the following is MOST helpful in responding to this request?
Assessing risk with no controls in place
Showing projected residual risk
Providing peer benchmarking results
Assessing risk with current controls in place
Showing projected residual risk is the most helpful way to respond to the request of explaining how existing risk treatment plans would affect risk posture at the end of the year. Residual risk is the level of risk that remains after the implementation of risk responses1. Projected residual risk is the estimated level of risk that will remain at a future point in time, based on the assumptions and expectations of the risk responses2. By showing projected residual risk, the risk practitioner can:
Demonstrate the effectiveness and efficiency of the risk treatment plans, and how they reduce the risk level from the inherent risk (the risk before the risk responses) to the residual risk3.
Compare the projected residual risk with the risk appetite and tolerance, which are the amount and type of risk that the organization is willing to accept or pursue in order to achieve its objectives4. This can help to determine whether the projected residual risk is acceptable or not, and whether the risk treatment plans are consistent and proportional to the risk level5.
Identify and address any gaps, issues, or challenges that may affect the achievement of the projected residual risk, and recommend and implement appropriate improvement actions or contingency plans6.
The other options are not the most helpful ways to respond to the request, because:
Assessing risk with no controls in place is not the most helpful way, as it does not reflect the current or future risk posture of the organization. Controls are the measures or actions that are implemented to modify the risk, such as prevent, detect, correct, or mitigate the risk7. Assessing risk with no controls in place can help to measure the inherent risk, but it does not show the impact or outcome of the risk treatment plans.
Providing peer benchmarking results is not the most helpful way, as it does not reflect the specific or unique risk profile of the organization. Peer benchmarking is the process of comparing the organization’s risk level and performance with its peers or competitors, based on a common set of criteria or indicators8. Providing peer benchmarking results can help to provide a reference or a standard for the risk posture, but it does not show the effect or result of the risk treatment plans.
Assessing risk with current controls in place is not the most helpful way, as it does not reflect the future or projected risk posture of the organization. Assessing risk with current controls in place can help to measure the current residual risk, but it does not show the expected or estimated residual risk at the end of the year.
References =
Residual Risk - CIO Wiki
Projected Residual Risk - CIO Wiki
Risk Treatment Plan - CIO Wiki
Risk Appetite and Tolerance - CIO Wiki
Risk Appetite: What It Is and Why It Matters - Gartner
Risk Monitoring and Review - The National Academies Press
Control - CIO Wiki
Benchmarking - CIO Wiki
[Risk Treatment - CIO Wiki]
A risk practitioner is preparing a report to communicate changes in the risk and control environment. The BEST way to engage stakeholder attention is to:
include detailed deviations from industry benchmarks,
include a summary linking information to stakeholder needs,
include a roadmap to achieve operational excellence,
publish the report on-demand for stakeholders.
A risk practitioner is preparing a report to communicate changes in the risk and control environment, such as new or emerging risks, changes in risk levels, risk responses, or control effectiveness. The best way to engage stakeholder attention is to include a summary linking information to stakeholder needs, meaning that the report should highlight the key points and findings that are relevant and important for the stakeholder’s role, responsibility, and interest. The summary should also explain how the information affects the stakeholder’s objectives, expectations, and decisions. The summary should be concise, clear, and compelling, and should capture the stakeholder’s attention and interest. The report can also include detailed deviations from industry benchmarks, a roadmap to achieve operational excellence, or an option to publish the report on-demand for stakeholders, but these are not the best ways to engage stakeholder attention, as they may not be directly related to the stakeholder’s needs or may overwhelm the stakeholder with too much information. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.4.1, p. 124-125
The PRIMARY objective of a risk identification process is to:
evaluate how risk conditions are managed.
determine threats and vulnerabilities.
estimate anticipated financial impact of risk conditions.
establish risk response options.
The primary objective of a risk identification process is to determine threats and vulnerabilities, which are the sources and causes of the risks that may affect the organization’s objectives. Threats are any events or circumstances that have the potential to harm or exploit the organization’s assets, such as people, information, systems, processes, or infrastructure1. Vulnerabilities are any weaknesses or gaps in the organization’s capabilities, controls, or defenses that may increase the likelihood or impact of the threats2. By determining threats and vulnerabilities, the organization can:
Identify and document all possible risks, regardless of whether they are internal or external, current or emerging, or positive or negative3.
Understand the nature and characteristics of the risks, such as their sources, causes, consequences, and interrelationships4.
Provide the basis for further risk analysis and evaluation, such as assessing the probability and severity of the risks, and prioritizing the risks according to their significance and urgency5.
References =
Threat - CIO Wiki
Vulnerability - CIO Wiki
Risk Identification - CIO Wiki
Risk Identification and Analysis - The National Academies Press
Risk Analysis - CIO Wiki
Which of the following should be the PRIMARY driver for the prioritization of risk responses?
Residual risk
Risk appetite
Mitigation cost
Inherent risk
Risk Appetite:
Risk appetite defines the level of risk that an organization is willing to accept in pursuit of its objectives. It serves as a benchmark for evaluating and prioritizing risk responses.
Prioritizing Risk Responses:
When determining how to address risks, the primary consideration should be whether the residual risk falls within the organization’s risk appetite.
If a risk exceeds the appetite, it needs to be mitigated, transferred, or avoided. If it is within the appetite, it might be accepted.
Influence of Other Factors:
Residual Risk:Important but must be evaluated against the risk appetite to determine if it is acceptable.
Mitigation Cost:Relevant for decision-making but secondary to aligning with risk appetite.
Inherent Risk:Initial risk assessment before controls are applied, but prioritization is based on residual risk and risk appetite.
References:
The CRISC Review Manual highlights the role of risk appetite in guiding the prioritization of risk responses (CRISC Review Manual, Chapter 3: Risk Response and Mitigation, Section 3.2.1 Prioritizing Risk Responses).
Which of the following would provide the MOST reliable evidence of the effectiveness of security controls implemented for a web application?
Penetration testing
IT general controls audit
Vulnerability assessment
Fault tree analysis
The most reliable evidence of the effectiveness of security controls implemented for a web application is penetration testing. Penetration testing is a process that simulates an attack on the web application by exploiting its vulnerabilities, using the same tools and techniques as real attackers. Penetration testing helps to evaluate the effectiveness of security controls, because it helps to verify that the security controls can prevent, detect, or mitigate the attack, and to measure the impact and severity of the attack. Penetration testing also helps to identify and address any weaknesses or gaps in the security controls, and to provide recommendations and solutions for improving the security of the web application. The other options are not as reliable as penetration testing, although they may provide some evidence of the effectiveness of security controls. IT general controls audit, vulnerability assessment, and fault tree analysis are all examples of analytical or evaluative methods, which may help to assess or estimate the effectiveness of security controls, but they do not necessarily test or measure the effectiveness of security controls in a realistic scenario. References = 10
Which of the following is the GREATEST concern associated with the use of artificial intelligence (AI) language models?
The model could be hacked or exploited.
The model could be used to generate inaccurate content.
Staff could become overly reliant on the model.
It could lead to biased recommendations.
Biased recommendations from AI models can perpetuate or exacerbate organizational risks, especially in decision-making processes, regulatory compliance, and ethical standards. Addressing such concerns is vital under theEmerging Technology Risksdomain in risk management.
Which of the following factors will have the GREATEST impact on the implementation of a risk mitigation strategy for an organization?
Cost-benefit analysis
Risk tolerance
Known vulnerabilities
Cyber insurance
Risk tolerance defines the boundaries for acceptable risk levels and directly impacts decision-making for mitigation strategies. A well-defined tolerance helps prioritize actions and allocate resources effectively, emphasizing its central role in theRisk Responsedomain.
Which of the following BEST indicates that an organization has implemented IT performance requirements?
Service level agreements(SLA)
Vendor references
Benchmarking data
Accountability matrix
Service level agreements (SLA) are contracts that define the expected level of performance and quality of service that an IT service provider will deliver to its customers. SLA are the best indicators that an organization has implemented IT performance requirements, as they specify the measurable and verifiable criteria that the IT service provider must meet or exceed, such as availability, reliability, security, and responsiveness. SLA also establish the roles and responsibilities of the parties involved, the methods of monitoring and reporting the service performance, and the consequences of non-compliance or breach of the agreement. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, Question 232. CRISC by Isaca Actual Free Exam Q&As, Question 9. CRISC Sample Questions 2024, Question 232. CRISC: Certified in Risk & Information Systems Control Sample Questions, Question 232.
Recovery the objectives (RTOs) should be based on
minimum tolerable downtime
minimum tolerable loss of data.
maximum tolerable downtime.
maximum tolerable loss of data
Recovery time objectives (RTOs) are the acceptable timeframes within which business processes must be restored after a disruption. RTOs should be based on the maximum tolerable downtime (MTD), which is the longest time that a business process can be inoperable without causing irreparable harm to the organization. The other options are not directly related to RTOs, as they refer to the amount of data loss or corruption that can be tolerated, not the time to restore the business processes. References = Risk and Information Systems Control Study Manual, Chapter 4: Risk and Control Monitoring and Reporting, Section 4.3: Key Risk Indicators, page 197.
Which of the following controls BEST enables an organization to ensure a complete and accurate IT asset inventory?
Prohibiting the use of personal devices for business
Performing network scanning for unknown devices
Requesting an asset list from business owners
Documenting asset configuration baselines
IT asset inventory is the process of tracking and managing the financial, physical, licensing, and contractual aspects of IT assets throughout their life cycle1. IT assets include hardware, software, and network components that an organization values and uses to achieve its objectives2. A complete and accurate IT asset inventory can help an organization to optimize its IT budget, reduce security risks, ensure compliance, and improve performance3.
One of the best controls to enable an organization to ensure a complete and accurate IT asset inventory is performing network scanning for unknown devices. Network scanning is the process of identifying and collecting information about the devices connected to a network, such as their IP addresses, operating systems, open ports, services, and vulnerabilities4. Network scanning can help an organization to:
Discover and inventory all the IT assets on the network, including those that are unauthorized, unmanaged, or hidden
Detect and remove any rogue or malicious devices that may pose a threat to the network security or performance
Update and verify the asset inventory data regularly and automatically, and alert on any changes or discrepancies
Support the asset lifecycle management and maintenance activities, such as patching, upgrading, or retiring assets5
References = IT Asset Valuation, Risk Assessment and Control Implementation Model, ITAM: The ultimate guide to IT asset management, Navigating Security Threats with IT Inventory Management, Network Scanning - Wikipedia, 8 Best IT Asset Management Software (2024)
In an organization that allows employee use of social media accounts for work purposes, which of the following is the BEST way to protect company sensitive information from being exposed?
Educating employees on what needs to be kept confidential
Implementing a data loss prevention (DLP) solution
Taking punitive action against employees who expose confidential data
Requiring employees to sign nondisclosure agreements
The best way to protect company sensitive information from being exposed when an organization allows employee use of social media accounts for work purposes is to require employees to sign nondisclosure agreements. Nondisclosure agreements are legal contracts that prohibit the employees from disclosing or sharing the company sensitive information with unauthorized parties, such as competitors, media, or regulators. Nondisclosure agreements also specify the scope, duration, and conditions of the nondisclosure obligation, and the penalties or remedies for breaching the agreement. Requiring employees to sign nondisclosure agreements is the best way to protect company sensitive information, as it helps to prevent or deter the employees from exposing or leaking the company sensitive information on social media, and to hold the employees accountable and liable for their actions. Requiring employees to sign nondisclosure agreements also helps to comply with the legal and regulatory requirements for data protection and privacy. Educating employees on what needs to be kept confidential, implementing a data loss prevention (DLP) solution, and taking punitive action against employees who expose confidential data are also useful ways, but they are not as effective as requiring employees to sign nondisclosure agreements, as they are either dependent on the employees’ awareness or behavior, or reactive or corrective measures, rather than proactive or preventive measures. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 217.
While reviewing a contract of a cloud services vendor, it was discovered that the vendor refuses to accept liability for a sensitive data breach. Which of the following controls will BES reduce the risk associated with such a data breach?
Ensuring the vendor does not know the encryption key
Engaging a third party to validate operational controls
Using the same cloud vendor as a competitor
Using field-level encryption with a vendor supplied key
Encryption is a technique that transforms data into an unreadable format using a secret key, so that only authorized parties can access and decrypt the data. Encryption can help to protect sensitive data from unauthorized access or disclosure, especially when the data is stored or transmitted in the cloud1.
Ensuring the vendor does not know the encryption key is a control that will best reduce the risk associated with a data breach, because it can help to:
Prevent the vendor from accessing or disclosing the sensitive data, intentionally or unintentionally
Limit the exposure or impact of the data breach, even if the vendor’s systems or networks are compromised by hackers or malicious insiders
Maintain the confidentiality and integrity of the sensitive data, regardless of the vendor’s liability or responsibility
Enhance the trust and confidence of the customers and stakeholders, who may be concerned about the vendor’s refusal to accept liability for a data breach23
The other options are not as effective as ensuring the vendor does not know the encryption key for reducing the risk associated with a data breach. Engaging a third party to validate operational controls is a control that can help to verify and improve the vendor’s security practices and processes, but it does not guarantee that the vendor will prevent or respond to a data breach adequately or timely. Using the same cloud vendor as a competitor is not a control, but rather a business decision that may increase the risk associated with a data breach, as the vendor may have access to or disclose the sensitive data of both parties, or may favor one party over the other. Using field-level encryption with a vendor supplied key is a control that can help to encrypt specific fields or columns of data, such as names, addresses, or credit card numbers, but it does not prevent the vendor from accessing or disclosing the data, as the vendor has the encryption key4. References =
Encryption - ISACA
Cloud Encryption: Using Data Encryption in The Cloud
Cloud Encryption: Why You Need It and How to Do It Right
Field-Level Encryption - ISACA
[CRISC Review Manual, 7th Edition]
A risk assessment has identified that an organization may not be in compliance with industry regulations. The BEST course of action would be to:
conduct a gap analysis against compliance criteria.
identify necessary controls to ensure compliance.
modify internal assurance activities to include control validation.
collaborate with management to meet compliance requirements.
According to the CRISC Review Manual (Digital Version), the best course of action when a risk assessment has identified that an organization may not be in compliance with industry regulations is to conduct a gap analysis against compliance criteria, which is a method of comparing the current state of compliance with the desired or required state of compliance. Conducting a gap analysis against compliance criteria helps to:
Identify and evaluate the differences or discrepancies between the compliance requirements and the actual compliance practices and capabilities
Assess the impact and severity of the compliance gaps on the organization’s objectives and performance
Prioritize the compliance gaps based on their urgency and importance
Develop and implement appropriate actions or measures to close or reduce the compliance gaps
Monitor and measure the effectiveness and efficiency of the actions or measures taken to address the compliance gaps
References = CRISC Review Manual (Digital Version), Chapter 1: IT Risk Identification, Section 1.5: IT Risk Identification Methods and Techniques, pp. 34-351
Which of the following controls will BEST detect unauthorized modification of data by a database administrator?
Reviewing database access rights
Reviewing database activity logs
Comparing data to input records
Reviewing changes to edit checks
Unauthorized modification of data by a database administrator is a security risk that involves altering, deleting, or inserting data on a database without proper authorization or approval, by a person who has privileged access to the database, such as a database administrator12.
The best control to detect unauthorized modification of data by a database administrator is to review database activity logs, which are records that capture and store the details and history of the transactions or activities that are performed on the database, such as who, what, when, where, and how34.
Reviewing database activity logs is the best control because it provides evidence and visibility of the database operations, and enables the detection and reporting of any deviations, anomalies, or issues that may indicate unauthorized modification of data by a database administrator34.
Reviewing database activity logs is also the best control because it supports the accountability and auditability of the database operations, and facilitates the investigation and resolution of any unauthorized modification of data by a database administrator34.
The other options are not the best controls, but rather possible measures or techniques that may supplement or enhance the review of database activity logs. For example:
Reviewing database access rights is a measure that involves verifying and validating the permissions and privileges that are granted or revoked to the users or roles who can access or modify the data on the database56. However, this measure is not the best control because it does not directly detect unauthorized modification of data by a database administrator, especially if the database administrator has legitimate access rights to the data56.
Comparing data to input records is a technique that involves matching and reconciling the data on the database with the original or source data that are entered or imported into the database, and identifying and correcting any discrepancies or errors78. However, this technique is not the best control because it does not directly detect unauthorized modification of data by a database administrator, especially if the input records are also modified or compromised78.
Reviewing changes to edit checks is a technique that involves examining and evaluating the modifications or updates to the edit checks, which are rules or validations that are applied to the data on the database to ensure their accuracy, completeness, andconsistency9 . However, this technique is not the best control because it does not directly detect unauthorized modification of data by a database administrator, especially if the edit checks are bypassed or disabled9 . References =
1: Database Security: Attacks and Solutions | SpringerLink2
2: Unauthorised Modification of Data With Intent to Cause Impairment3
3: Database Activity Monitoring - Wikipedia4
4: Database Activity Monitoring (DAM) | Imperva5
5: Database Access Control - Wikipedia6
6: Database Access Control: Best Practices for Database Security7
7: Data Reconciliation - Wikipedia8
8: Data Reconciliation and Gross Error Detection9
9: Edit Check - Wikipedia
Edit Checks: A Data Quality Tool
A risk practitioner has observed that there is an increasing trend of users sending sensitive information by email without using encryption. Which of the following would be the MOST effective approach to mitigate the risk associated with data loss?
Implement a tool to create and distribute violation reports
Raise awareness of encryption requirements for sensitive data.
Block unencrypted outgoing emails which contain sensitive data.
Implement a progressive disciplinary process for email violations.
According to the CRISC Review Manual (Digital Version), the most effective approach to mitigate the risk associated with data loss due to users sending sensitive information by email without using encryption is to block unencrypted outgoing emails which contain sensitive data. This is an example of a risk avoidance strategy, which aims to eliminate the risk by removing the source of the risk or the activity that causes the risk. Blocking unencrypted outgoing emails which contain sensitive data can prevent unauthorized access, disclosure, modification or destruction of the sensitive information, and thus protect the confidentiality, integrity and availability of the data. This approach can also deter users from violating the encryption policy and enforce compliance with the security standards and regulations.
References = CRISC Review Manual (Digital Version), Chapter 3: IT Risk Response, Section 3.3: Risk Response Options, pp. 167-1681
Which of the following describes the relationship between Key risk indicators (KRIs) and key control indicators (KCIS)?
KCIs are independent from KRIs KRIs.
KCIs and KRIs help in determining risk appetite.
KCIs are defined using data from KRIs.
KCIs provide input for KRIs
Key risk indicators (KRIs) are metrics that provide information on the level of exposure to a given risk. Key control indicators (KCIs) are metrics that measure the performance or effectiveness of a control in mitigating a risk. KCIs provide input for KRIs, because they help to assess the residual risk after applying the control. For example, if the KRI is the number of security incidents, and the KCI is the percentage of incidents detected by the intrusion prevention system (IPS), then the KCI provides input for the KRI by showing how well the IPS is reducing the risk of security breaches. References = CRISC: Certified in Risk & Information Systems Control Sample Questions
Which of the following approaches will BEST help to ensure the effectiveness of risk awareness training?
Piloting courses with focus groups
Using reputable third-party training programs
Reviewing content with senior management
Creating modules for targeted audiences
The best approach to ensure the effectiveness of risk awareness training is to create modules for targeted audiences. This means that the risk awareness training should be customized and tailored to the specific needs, roles, and responsibilities of different groups of staff, such as business owners, process owners, IT staff, or external parties. Creating modules for targeted audiences helps to ensure that the risk awareness training is relevant, engaging, and applicable to the participants, and that it covers the appropriate level of detail and complexity. It also helps to enhance the learning outcomes and retention of the risk awareness training, and to foster a culture of risk awareness and responsibility within the enterprise. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 5, Section 5.4.1, page 2491
Which of the following BEST assists in justifying an investment in automated controls?
Cost-benefit analysis
Alignment of investment with risk appetite
Elimination of compensating controls
Reduction in personnel costs
A cost-benefit analysis is the best method to assist in justifying an investment in automated controls, as it helps to compare and evaluate the costs and benefits of the investment and to determine its feasibility and profitability. A cost-benefit analysis is a process of identifying, measuring, and comparing the expected costs and benefits of a project or a decision, such as investing in automated controls. A cost-benefit analysis can help to justify an investment in automated controls by providing the following benefits:
It enables a data-driven and evidence-based approach to decision making, rather than relying on subjective or qualitative judgments.
It facilitates a consistent and standardized way of assessing and communicating the value and impact of the investment across the organization and to the external stakeholders.
It supports the alignment of the investment with the organizational strategy and objectives, and helps to evaluate the achievement of the desired outcomes.
It helps to identify and prioritize the opportunities and challenges of the investment, and to develop and implement appropriate strategies and actions to address them.
It provides feedback and learning opportunities for the investment and its outcomes, and helps to foster a culture of continuous improvement and innovation.
The other options are not the best methods to assist in justifying an investment in automated controls. Alignment of investment with risk appetite is an important aspect of risk management, but it does not directly address the costs and benefits of the investment. Risk appetite is the amount and type of risk that an organization is willing to accept in pursuit of its objectives. Alignment of investment with risk appetite helps to ensure that the investment is consistent with the organizational risk tolerance and preferences,and does not expose the organization to excessive or unacceptable risk. Elimination of compensating controls is a possible benefit of investing in automated controls, but it is not a method to justify the investment. Compensating controls are alternative or additional controls that are implemented to mitigate the risk when the primary or preferred controls are not feasible or effective. Elimination of compensating controls can help to reduce the complexity and costs of the control environment, and to improve the efficiency and reliability of the controls. Reduction in personnel costs is a possible benefit of investing in automated controls, but it is not a method to justify the investment. Personnel costs are the expenses related to the staff and employees involved in the processes or functions that are automated. Reduction in personnel costs can help to increase the profitability and productivity of the organization, and to allocate the resources more effectively and efficiently. References = Cost Benefit Analysis: An Expert Guide | Smartsheet, IT Risk Resources | ISACA, Automation - Efficiency, Cost-Savings, Robotics | Britannica
When an organization is having new software implemented under contract, which of the following is key to controlling escalating costs?
Risk management
Change management
Problem management
Quality management
The key to controlling escalating costs when an organization is having new software implemented under contract is change management, which is the process of identifying, evaluating, approving, and implementing changes to the project scope, schedule, budget, or quality1. Change management can help to control escalating costs by:
Establishing a clear and agreed-upon baseline for the project deliverables, requirements, and expectations, and ensuring that they are aligned with the contract terms and conditions2.
Defining and enforcing a formal and consistent change control process, which includes the roles and responsibilities, the criteria and methods, and the documentation and communication of the changes3.
Assessing and prioritizing the proposed changes, and determining their impact and feasibility, and their alignment with the project objectives and constraints4.
Obtaining the approval and authorization of the relevant stakeholders, such as the project sponsor, the project manager, the contractor, or the customer, before implementing the changes5.
Monitoring and measuring the performance and outcome of the changes, and ensuring that they are delivered within the agreed scope, schedule, budget, and quality6.
References =
Change Management - CIO Wiki
Project Scope Management - CIO Wiki
Change Control - CIO Wiki
Change Impact Analysis - CIO Wiki
Change Approval - CIO Wiki
Change Evaluation - CIO Wiki
A change management process has recently been updated with new testing procedures. What is the NEXT course of action?
Monitor processes to ensure recent updates are being followed.
Communicate to those who test and promote changes.
Conduct a cost-benefit analysis to justify the cost of the control.
Assess the maturity of the change management process.
A change management process is a set of procedures and activities that ensure that any changes to the IT systems or applications are planned, approved, tested, implemented, and documented in a consistent and controlled manner.
A change management process has recently been updated with new testing procedures. This means that the process has been improved or modified to include new or additional steps or methods for verifying and validating the changes before they are deployed to the production environment.
The next course of action after updating the change management process with new testing procedures is to communicate to those who test and promote changes. This means that the change management team or function should inform and educate the people who are involved or affected by the changes, such as the developers, testers, users, customers, etc., about the new testing procedures, their purpose, benefits, requirements, and expectations.
Communicating to those who test and promote changes helps to ensure that the new testing procedures are understood and followed by all the parties, that the changes are tested and promoted in accordance with the process standards and criteria, and that the changes are delivered with the expected quality and performance.
The other options are not the next courses of action after updating the change management process with new testing procedures. They are either secondary or not essential for change management.
The references for this answer are:
Risk IT Framework, page 27
Information Technology & Security, page 21
Risk Scenarios Starter Pack, page 19
Which of the following is MOST important for a risk practitioner to verify when evaluating the effectiveness of an organization's existing controls?
Senior management has approved the control design.
Inherent risk has been reduced from original levels.
Residual risk remains within acceptable levels.
Costs for control maintenance are reasonable.
Residual risk is the risk that remains after the implementation of controls. It is important for a risk practitioner to verify that the residual risk is within the acceptable levels defined by the enterprise’s risk appetite and tolerance. This ensures that the controls are effective in reducing the risk exposure to an acceptable level and align with the enterprise’s objectives and strategy. References = CRISC Review Manual 27th Edition, page 131. Most Asked CRISC Exam Questions and Answers.
What is the PRIMARY purpose of a business impact analysis (BIA)?
To determine the likelihood and impact of threats to business operations
To identify important business processes in the organization
To estimate resource requirements for related business processes
To evaluate the priority of business operations in case of disruption
The primary purpose of a business impact analysis (BIA) is to evaluate the priority of business operations in case of disruption. A BIA is a process that identifies and analyzes the potential effects of various types of disruptions on the enterprise’s critical business functions and processes. A BIA helps to determine the recovery objectives, such as the recovery time objective (RTO) and the recovery point objective (RPO), for each business operation, based on the impact of disruption on the enterprise’s objectives, reputation, compliance, and stakeholders. A BIA also helps to identify the dependencies, resources, and interdependencies of the business operations, and to rank them according to their importance and urgency. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.2.1, page 671
Which of the following is the GREATEST benefit of analyzing logs collected from different systems?
A record of incidents is maintained.
Forensic investigations are facilitated.
Security violations can be identified.
Developing threats are detected earlier.
According to the CRISC Review Manual, the greatest benefit of analyzing logs collected from different systems is to detect developing threats earlier, because it helps to identify and correlate the patterns, trends, and anomalies that may indicate a potential attack or compromise. Log analysis is the process of examining and interpreting the log data generated by various systems, such as firewalls, servers, routers, and applications. Log analysis can provide valuable insights into the activities and events that occur on the systems, and can enable the timely detection and response to the emerging threats. The other options are not the greatest benefits of analyzing logs, as they are less proactive or less strategic than detecting developing threats earlier. Maintaining a record of incidents is a benefit of logging, but not of analyzing logs, as it involves storing and preserving the log data for future reference. Facilitating forensic investigations is a benefit of analyzing logs, but it is a reactive and tactical activity that occurs after an incident has happened. Identifying security violations is a benefit of analyzing logs, but it is a specific and operational activity that focuses on the compliance and enforcement of the security policies and standards. References = CRISC Review Manual, 7th Edition, Chapter 5, Section 5.3.2, page 263.
Winch of the following is the BEST evidence of an effective risk treatment plan?
The inherent risk is below the asset residual risk.
Remediation cost is below the asset business value
The risk tolerance threshold s above the asset residual
Remediation is completed within the asset recovery time objective (RTO)
The best evidence of an effective risk treatment plan is that the risk tolerance threshold is above the asset residual risk, because this means that the risk treatment plan has reduced the risk to a level that is acceptable to the enterprise. The risk tolerance threshold is the maximum amount of risk that the enterprise is willing to accept for a given asset or process. The asset residual risk is the remaining risk after applying the risk treatment plan. The risk treatment plan is effective if the asset residual risk is lower than or equal to the risk tolerance threshold. The other options are not the best evidence, although they may also be indicators of an effective risk treatment plan. The inherent risk being below the asset residual risk, the remediation cost being below the asset business value, and the remediation being completed within the asset recovery time objective (RTO) are examples of desirable or expected outcomes of the risk treatment plan, but they do not directly measure the effectiveness of the risk treatment plan. References = CRISC: Certified in Risk & Information Systems Control Sample Questions
When a high-risk security breach occurs, which of the following would be MOST important to the person responsible for managing the incident?
An analysis of the security logs that illustrate the sequence of events
An analysis of the impact of similar attacks in other organizations
A business case for implementing stronger logical access controls
A justification of corrective action taken
An analysis of the security logs that illustrate the sequence of events is the most important information for the person responsible for managing the incident, as it can help to identify the source, scope, and impact of the security breach, and to determine the appropriate response actions. An analysis of the security logs can also provide evidence for forensic investigation and legal action, and help to prevent or mitigate future incidents by identifying the root causes and vulnerabilities. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, Question 235. CRISC by Isaca Actual Free Exam Q&As, Question 9. CRISC: Certified in Risk & Information Systems Control Sample Questions, Question 235. CRISC Sample Questions 2024, Question 235.
Which of the following process controls BEST mitigates the risk of an employee issuing fraudulent payments to a vendor?
Performing credit verification of third-party vendors prior to payment
Conducting system access reviews to ensure least privilege and appropriate access
Performing regular reconciliation of payments to the check registers
Enforcing segregation of duties between the vendor master file and invoicing
Enforcing segregation of duties between the vendor master file and invoicing is the best process control to mitigate the risk of an employee issuing fraudulent payments to a vendor. This is because segregation of duties is a key internal control that prevents or detects errors, fraud, or abuse by ensuring that no single person can perform incompatible or conflicting tasks. The vendor master file is a database that contains the information and settings for each vendor, such as name, address, bank account, payment terms, etc. Invoicing is the process of generating and sending bills to the vendors for the goods or services they provide. If the same person can access and modify the vendor master file and issue invoices, he or she could create fictitious vendors, alter vendor information, or generate false or duplicate invoices, and then divert the payments to his or her own account. By segregating these duties, the organization can reduce the opportunity and likelihood of such fraudulent activities. According to the CRISC Review Manual 2022, segregation of duties is one of the key IT control objectives and practices1. According to the web search results, segregation of duties between the vendor master file and invoicing is a common and recommended control to prevent vendor fraud
The PRIMARY goal of conducting a business impact analysis (BIA) as part of an overall continuity planning process is to:
obtain the support of executive management.
map the business processes to supporting IT and other corporate resources.
identify critical business processes and the degree of reliance on support services.
document the disaster recovery process.
The primary goal of conducting a business impact analysis (BIA) as part of an overall continuity planning process is to identify critical business processes and the degree of reliance on support services. A BIA is a process of assessing the potential impact and consequences of a disruption or interruption of the business activities, operations, or functions. A continuity planning process is a process of developing, implementing, and maintaining a plan to ensure the continuity and recovery of the business activities, operations, or functions in the event of a disruption or interruption. The primary goal of conducting a BIA is to identify critical business processes and the degree of reliance on support services, which are the business processes that are essential for the survival and success of the business, and the support services that are required to enable or facilitate the critical business processes, such as IT systems, human resources, facilities, or suppliers. Identifying critical business processes and the degree of reliance on support services helps to determine the priorities and requirements for the continuity and recovery of the business activities, operations, or functions, and to select and implement the appropriate continuity and recovery strategies and solutions. Obtaining the support of executive management, mapping the business processes to supporting IT and other corporate resources, and documenting the disaster recovery process are not the primary goals of conducting a BIA, as they are either the benefits or the outputs of the BIA process, and they do not address the primary need of assessing the impact and consequences of the business disruption or interruption. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 50.
Which of the following will BEST mitigate the risk associated with IT and business misalignment?
Establishing business key performance indicators (KPIs)
Introducing an established framework for IT architecture
Establishing key risk indicators (KRIs)
Involving the business process owner in IT strategy
IT and business misalignment is the risk that the IT objectives, plans, and activities are not aligned with the business goals, needs, and expectations. This can result in wasted resources, missed opportunities, poor performance, and customer dissatisfaction. One of the best ways to mitigate this risk is to involve the business process owner in IT strategy. The business process owner is the person who has the authority and responsibility for a specific business process and its outcomes. By involving the business process owner in IT strategy, the organization can ensure that the IT initiatives and solutions are relevant, effective, and beneficial for the business process and its stakeholders. The business process owner can also provide valuable input, feedback, and support for the IT strategy and its implementation. The other options are not the best ways to mitigate the risk associated with IT and business misalignment, although they may be helpful and complementary. Establishing business key performance indicators (KPIs) is a technique to measure and monitor the achievement of business objectives and outcomes. However, KPIs do not necessarily ensure that the IT strategy is aligned with the business strategy or that the IT activities support the business activities. Introducing an established framework for IT architecture is a method to design and implement the IT infrastructure, systems, and services in a consistent and coherent manner. However, an IT architecture framework does not guarantee that the IT architecture is aligned with the business architecture or that the IT capabilities meet the business requirements. Establishing key risk indicators (KRIs) is a tool to monitor and communicate the level of exposure to a given risk or the potential impact of a risk. However, KRIs do not directly address the risk of IT and business misalignment or the actions needed to align them. References = CRISC Review Manual, pages 22-231; CRISC Review Questions, Answers & Explanations Manual, page 76
What information is MOST helpful to asset owners when classifying organizational assets for risk assessment?
Potential loss to tie business due to non-performance of the asset
Known emerging environmental threats
Known vulnerabilities published by the asset developer
Cost of replacing the asset with a new asset providing similar services
The potential loss to the business due to non-performance of the asset is the most helpful information for asset owners when classifying organizational assets for risk assessment, because it reflects the value and criticality of the asset to the business objectives and processes. The potential loss can be measured in terms of financial, operational, reputational, or legal impacts. The known emerging environmental threats are not relevant for asset classification, because they are external factors that affect the risk level, not the asset value. The known vulnerabilities published by the asset developer are not relevant for asset classification, because they are internal factors that affect the risk level, not the asset value. The cost of replacing the asset with a new asset providing similar services is not relevant for asset classification, because it does not reflect the business impact of losing the asset functionality or availability. References = CRISC Sample Questions 2024
Which of the following is the BEST way to ensure adequate resources will be allocated to manage identified risk?
Prioritizing risk within each business unit
Reviewing risk ranking methodology
Promoting an organizational culture of risk awareness
Assigning risk ownership to appropriate roles
The best way to ensure adequate resources will be allocated to manage identified risk is to assign risk ownership to appropriate roles. Risk ownership is the process of assigning the authority and responsibility to manage a specific risk or a group of related risks to a person or entity. Risk ownership helps to ensure adequate resources for managing risk, because it helps to define and clarify the roles and responsibilities of the risk owners, and to establish and enforce the expectations and standards for the risk owners. Risk ownership also helps to measure and evaluate the effectiveness and efficiency of the risk owners, and to identify and address any issues or gaps in the risk management activities. The other options are not as effective as assigning risk ownership to appropriate roles, although they may be related to the risk management process. Prioritizing risk within each business unit, reviewing risk ranking methodology, and promoting an organizational culture of risk awareness are all activities that can help to support or improve the risk management process, but they do not necessarily ensure adequate resources for managing risk. References = Risk and Information Systems Control Study Manual, Chapter 2, Section 2.2.1, page 2-11.
Which of the following is the BEST key performance indicator (KPI) to measure the effectiveness of a vulnerability management process?
Percentage of vulnerabilities remediated within the agreed service level
Number of vulnerabilities identified during the period
Number of vulnerabilities re-opened during the period
Percentage of vulnerabilities escalated to senior management
A vulnerability management process is a process that identifies, analyzes, prioritizes, and remediates the vulnerabilities in the IT systems and applications. The effectiveness of a vulnerability management process can be measured by the key performance indicators (KPIs) that reflect the achievement of the process objectives and the alignment with the enterprise’s risk appetite and tolerance. The best KPI to measure the effectiveness of a vulnerability management process is the percentage of vulnerabilities remediated within the agreed service level. This KPI indicates how well the process is able to address the vulnerabilities in a timely and efficient manner, and reduce the exposure and impact of the risks associated with the vulnerabilities. The other options are not as good as the percentage of vulnerabilities remediated within the agreed service level, as they may not reflect the quality or timeliness of the remediation actions, or the alignment with the enterprise’s risk appetite and tolerance. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 4, Section 4.3.2.1, pp. 171-172.
Which of the following is MOST effective against external threats to an organizations confidential information?
Single sign-on
Data integrity checking
Strong authentication
Intrusion detection system
Strong authentication is the most effective measure against external threats to an organization’s confidential information. Confidential information is any data or information that is sensitive, proprietary, or valuable to the organization, and that should not be disclosed to unauthorized parties1. External threats are malicious actors outside the organization who attempt to gain unauthorized access to the organization’s networks, systems, and data, using various methods such as malware, hacking, or social engineering2. Strong authentication is a method of verifying the identity and legitimacy of a user or device before granting access to the organization’s resources or data3. Strong authentication typically involves the use of multiple factors or methods of authentication, such as passwords, tokens, biometrics, orcertificates4. Strong authentication can prevent or reduce the risk of external threats to the organization’s confidential information, by making it more difficult and costly for the attackers to compromise the credentials or devices of the authorized users, and by limiting the access to the data or resources that are relevant and necessary for the users’ roles and responsibilities5. The other options are not the most effective measures against external threats to the organization’s confidential information, as they are either less secure or less relevant than strong authentication. Single sign-on is a method of allowing a user to access multiple systems or applications with a single set of credentials, without having to log in separately for each system or application6. Single sign-on can improve the user experience and convenience, as well as reduce the administrative burden and cost of managing multiple accounts and passwords. However, single sign-on is not the most effective measure against external threats to the organization’s confidential information, as it can also increase the risk of credential compromise or misuse, and create a single point of failure or attack for the attackers to access multiple systems or data. Data integrity checking is a method of ensuring that the data or information is accurate, complete, and consistent, and that it has not been altered or corrupted by unauthorized parties or processes. Data integrity checking can involve the use of techniques such as checksums, hashes, digital signatures, or encryption. Data integrity checking can enhance the quality and reliability of the data or information, as well as detect and prevent any unauthorized or malicious changes or tampering. However, data integrity checking is not the most effective measure against external threats to the organization’s confidential information, as it does not prevent or reduce the risk of data theft or leakage, and it does not verify the identity or legitimacy of the users or devices accessing the data. Intrusion detection system is a system that monitors the network or system activities and events, and detects and alerts any suspicious or malicious behaviors or anomalies that may indicate an attempted or successful breach or attack. Intrusion detection system can help to identify and respond to external threats to the organization’s networks, systems, and data, by providing visibility and awareness of the network or system status and activities, and by enabling timely and appropriate actions or countermeasures. However, intrusion detection system is not the most effective measure againstexternal threats to the organization’s confidential information, as it is a reactive or passive system that does not prevent or block the attacks, and it may generate false positives or negatives that can affect its accuracy and efficiency. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 4, Section 4.2.1, Page 189.
Which type of indicators should be developed to measure the effectiveness of an organization's firewall rule set?
Key risk indicators (KRIs)
Key management indicators (KMIs)
Key performance indicators (KPIs)
Key control indicators (KCIs)
The best type of indicators to measure the effectiveness of an organization’s firewall rule set are key control indicators (KCIs). A firewall is a device or software that filters the network traffic based on a set of rules or policies. A firewall rule set is the configuration of the firewall that defines the criteria for allowing or blocking the traffic. A key control indicator is a metric that measures the performance and effectiveness of a control in achieving its objectives and mitigating the risks. A key control indicator can help to evaluate the adequacy and efficiency of the firewall rule set, and to identify any gaps, weaknesses, or issues that need to be addressed. Key risk indicators (KRIs), key management indicators (KMIs), and key performance indicators (KPIs) are not as suitable as key control indicators, as they measure different aspects of the risk management process, such as the level and nature of the risk exposure, the alignment and integration of the risk management activities, and the achievement of the risk management goals and targets. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 220.
Which of the following provides the MOST useful information when determining if a specific control should be implemented?
Business impact analysis (BIA)
Cost-benefit analysis
Attribute analysis
Root cause analysis
A cost-benefit analysis is a tool that compares the costs and benefits of different alternatives, such as implementing or not implementing a specific control. A cost-benefit analysis provides the most useful information when determining if a specific control should be implemented, as it can show the potential savings, benefits, and risks of each option, and help the decision-makers choose the best course of action. A cost-benefit analysis can also include qualitative factors, such as security, compliance, performance, and customer satisfaction, that may be affected by the control implementation. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, Question 256. CRISC: Certified in Risk & Information Systems Control Sample Questions, Question 256. Most Asked CRISC Exam Questions and Answers, Question 10. CRISC by Isaca Actual Free Exam Q&As, Question 9.
Which of the following criteria associated with key risk indicators (KRIs) BEST enables effective risk monitoring?
Approval by senior management
Low cost of development and maintenance
Sensitivity to changes in risk levels
Use of industry risk data sources
Key risk indicators (KRIs) are metrics that help organizations monitor and assess potential risks that may impact their operations, financial health, or overall performance1. KRIs should have certain characteristics that make them effective for risk monitoring, such as:
Ability to measure the right thing (e.g., supports the decisions that need to be made)
Quantifiable (e.g., damages in dollars of profit loss)
Capability to be measured precisely and accurately
Relevant (measuring the right thing associated with decisions)2
Among the four options given, only option C (sensitivity to changes in risk levels) best enables effective risk monitoring. This is because KRIs should be able to capture the changes in risk levels over time and alert organizations to emerging or escalating risks3. A high sensitivity to changes in risk levels indicates that theKRI is responsive and timely, and can help organizations take preventive or corrective actions before the risks become too severe.
References = Key Risk Indicators: A Practical Guide, Key Risk Indicators: Examples & Definitions, Key Risk Indicators - Wikipedia
An organization is conducting a review of emerging risk. Which of the following is the BEST input for this exercise?
Audit reports
Industry benchmarks
Financial forecasts
Annual threat reports
The best input for conducting a review of emerging risk is the annual threat reports. Emerging risk is the risk that arises from new or evolving sources, or from existing sources that have not been previously considered or recognized. Emerging risk may have significant impact on the organization’s objectives, strategies, operations, or reputation, and may require new or different risk responses. Annual threat reports are the reports that provide information and analysis on the current and future trends, developments, and challenges in the threat landscape, such as cyberattacks, natural disasters, geopolitical conflicts, or pandemics. Annual threat reports can help to identify and assess the emerging risk, as they can provide insights into the sources, drivers, indicators, and scenarios of the emerging risk, as well as the potential impact and likelihood of the emerging risk. Annual threat reports can also help to benchmark and compare the organization’s risk exposure and preparedness with the industry and the peers, and to prioritize and respond to the emerging risk. Audit reports, industry benchmarks, and financial forecasts are not as useful as annual threat reports, as they do not focus on the emerging risk, and may not capture the latest or future changes in the threat landscape. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 50.
Which of the following is the BEST way to manage the risk associated with malicious activities performed by database administrators (DBAs)?
Activity logging and monitoring
Periodic access review
Two-factor authentication
Awareness training and background checks
According to the CRISC Review Manual, activity logging and monitoring is the best way to manage the risk associated with malicious activities performed by database administrators (DBAs), because it enables the detection and prevention of unauthorized or inappropriate actions on the database. Activity logging and monitoring involves capturing and reviewing the activities of the DBAs, such as the commands executed, the data accessed or modified, the privileges used, and the time and duration of the sessions. Activity logging and monitoring can also provide an audit trail for accountability and forensic purposes. The other options are not the best ways to manage the risk, because they do not directly address the malicious activities of the DBAs. Periodic access review is a control that verifies the appropriateness of the access rights granted to the DBAs, but it does not monitor their actual activities. Two-factor authentication is a control that enhances the security of the authentication process, but it does not prevent the DBAs from performing malicious activities once they are authenticated. Awareness training and background checks are controls that aim to reduce the likelihood of the DBAs engaging in malicious activities, but they do not guarantee their compliance or behavior. References = CRISC Review Manual, 7th Edition, Chapter 4, Section 4.1.3, page 166.
A service provider is managing a client’s servers. During an audit of the service, a noncompliant control is discovered that will not be resolved before the next audit because the client cannot afford the downtime required to correct the issue. The service provider’s MOST appropriate action would be to:
develop a risk remediation plan overriding the client's decision
make a note for this item in the next audit explaining the situation
insist that the remediation occur for the benefit of other customers
ask the client to document the formal risk acceptance for the provider
A noncompliant control is a control that does not meet the requirements or standards of an audit, regulation, or policy. A noncompliant control can expose the organization to risks such as errors, fraud, or breaches. When a noncompliant control is identified, the service provider and the client should work together to resolve the issue as soon as possible. However, sometimes the resolution may not be feasible or cost-effective, and the client may decide to accept the risk associated with the noncompliant control.
In this case, the service provider’s most appropriate action would be to ask the client to document the formal risk acceptance for the provider. This means that the client should acknowledge the existence and consequences of the noncompliant control, and provide a written justification for accepting the risk. The risk acceptance document should also specify the roles and responsibilities of the service provider and the client, and the duration and conditions of the risk acceptance. The risk acceptance document should be signed by the client’s senior management and the service provider’s management, and kept as part of the audit evidence.
The other options are not appropriate actions for the service provider. Developing a risk remediation plan overriding the client’s decision would be disrespectful and unprofessional, as it would ignore the client’s authority and preference. Making a note for this item in the next audit explaining the situation would be insufficient and misleading, as it would imply that the issue is still unresolved and that the service provider is responsible for it. Insisting that the remediation occur for the benefit of other customers would be unreasonable and impractical, as it would disregard the client’s business needs and constraints, and potentially harm the relationship between the service provider and the client. References =
Risk Acceptance - Institute of Internal Auditors
New Guidance on the Evaluation of Non-compliance with the Risk Assessment Standard and its Peer Review Impact - REVISED
The Impact of Non-compliance: Understanding The Risks And Consequences
Which of the following risk management practices BEST facilitates the incorporation of IT risk scenarios into the enterprise-wide risk register?
Key risk indicators (KRls) are developed for key IT risk scenarios
IT risk scenarios are assessed by the enterprise risk management team
Risk appetites for IT risk scenarios are approved by key business stakeholders.
IT risk scenarios are developed in the context of organizational objectives.
IT risk scenarios are hypothetical situations that describe how IT-related events or incidents could adversely affect an organization’s objectives, assets, or operations. IT risk scenarios can help to identify, analyze, and prioritize IT risks, and to develop appropriate responses and controls1.
An enterprise-wide risk register is a document that records and tracks the significant risks that an organization faces across its various functions, processes, and activities. An enterprise-wide risk register can help to provide a comprehensive and consistent view of the organization’s risk profile, and to support the decision making and reporting of the risk management function2.
The best practice that facilitates the incorporation of IT risk scenarios into the enterprise-wide risk register is to develop IT risk scenarios in the context of organizational objectives. This means that IT risk scenarios should be aligned with and derived from the organization’s strategic goals, mission, vision, and values. IT risk scenarios should also consider the interdependencies and interactions between IT and other business domains, and the potential impact of IT risks on the organization’s performance and reputation3.
By developing IT risk scenarios in the context of organizational objectives, the organization can ensure that the IT risk scenarios are relevant, realistic, and meaningful for the enterprise-wide risk management. The organization can also ensure that the IT risk scenarios are consistent and comparable with other types of risk scenarios, such as financial, operational, or reputational risk scenarios. This can facilitate the integration and consolidation of IT risk scenarios into the enterprise-wide risk register, and enable a holistic and balanced assessment and reporting of the organization’s risks4.
The other options are not as effective as developing IT risk scenarios in the context of organizational objectives for incorporating IT risk scenarios into the enterprise-wide risk register. Developing key risk indicators (KRIs) for key IT risk scenarios can help to monitor and measure the IT risk exposure and performance, but it does not ensure that the IT risk scenarios are aligned with the organizational objectives or integrated with other risk scenarios. Assessing IT risk scenarios by the enterprise risk management team can help to validate and prioritize the IT risk scenarios, but it does not ensure that the IT risk scenarios are derived from the organizational objectives or consistent with other risk scenarios. Approving risk appetites for IT risk scenarios by key business stakeholders can help to establish the acceptable level of IT risk taking and tolerance, but it does not ensure that the IT risk scenarios are based on the organizational objectives or comparable with other risk scenarios. References =
IT Risk Scenario Development - ISACA
Risk Register - ISACA
Identifying Risks and Scenarios Threatening the Organization as an Enterprise - A New Enterprise Risk Identification Framework
Risk Register 2021-2022 - UNECE
[CRISC Review Manual, 7th Edition]
Which of the following is MOST important to have in place to ensure the effectiveness of risk and security metrics reporting?
Organizational reporting process
Incident reporting procedures
Regularly scheduled audits
Incident management policy
The most important factor to have in place to ensure the effectiveness of risk and security metrics reporting is an organizational reporting process. An organizational reporting process is a set of procedures that defines the roles, responsibilities, frequency, format, and distribution of the risk and security metrics reports. An organizational reporting process helps to ensure that the risk and security metrics are relevant, accurate, consistent, and timely, and that they provide useful information for decision making and performance improvement. An organizational reporting process also helps to align the risk and security metrics reporting with the enterprise’s objectives, strategies, and policies, and to communicate the risk and security status and issues to the appropriate stakeholders. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 5, Section 5.3.2, page 2421
Several newly identified risk scenarios are being integrated into an organization's risk register. The MOST appropriate risk owner would be the individual who:
is in charge of information security.
is responsible for enterprise risk management (ERM)
can implement remediation action plans.
is accountable for loss if the risk materializes.
According to the CRISC Review Manual, a risk owner is the person who is accountable for the risk and its associated mitigation actions. The risk owner is responsible for monitoring the risk, reporting the risk status, and implementing the risk response. Therefore, the most appropriate risk owner would be the individual who is accountable for loss if the risk materializes, as it implies that they have the authority and the incentive to manage the risk effectively. The other options are not the most appropriate risk owners, as they are not directly accountable for the risk or its consequences. The person who is in charge of information security is responsible for overseeing the IT security function and ensuring that the IT security policy is enforced, but they may not have the authority or the resources to manage the risk. The person who is responsible for enterprise risk management (ERM) is responsible for establishing and maintaining the ERM framework and processes, but they may not have the knowledge or the involvement to manage the risk. The person who can implement remediation action plans is responsible for executing the risk response, but they may not have the decision-making power or the accountability to manage the risk. References = CRISC Review Manual, 7th Edition, Chapter 3, Section 3.1.2, page 108.
Which of the following should be the PRIMARY focus of an IT risk awareness program?
Ensure compliance with the organization's internal policies
Cultivate long-term behavioral change.
Communicate IT risk policy to the participants.
Demonstrate regulatory compliance.
The primary focus of an IT risk awareness program is to cultivate long-term behavioral change. An IT risk awareness program is a program that educates and informs the stakeholders, such as the employees, managers, customers, or partners, about the IT risks and the IT risk management activities. An IT risk awareness program helps to increase the knowledge and understanding of the IT risks and the IT risk management objectives, strategies, and processes, and to promote the participation and collaboration of the stakeholders in the IT risk management activities. The primary focus of an IT risk awareness program is to cultivate long-term behavioral change, which is the change in the attitudes, beliefs, values, and actions of the stakeholders regarding the IT risks and the IT risk management activities. Cultivating long-term behavioral change helps to create and sustain a risk-aware culture, which is a culture that recognizes,respects, and supports the IT risk management activities, and that encourages the stakeholders to take responsibility and ownership of the IT risks and the IT risk management activities. Cultivating long-term behavioral change also helps to improve the effectiveness and efficiency of the IT risk management activities, and to align the IT risk management activities with the business goals and values. Ensuring compliance with the organization’s internal policies, communicating IT risk policy to the participants, and demonstrating regulatory compliance are not the primary focus of an IT risk awareness program, as they are either the benefits or the objectives of the IT risk awareness program, and they do not address the primary need of changing the behavior of the stakeholders. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 36.
Which of the following is the GREATEST risk associated with the misclassification of data?
inadequate resource allocation
Data disruption
Unauthorized access
Inadequate retention schedules
According to the CRISC Review Manual, the greatest risk associated with the misclassification of data is unauthorized access, because it can result in the loss of confidentiality, integrity, and availability of the data. Data classification is the process of assigning categories to data based on its sensitivity and value to the organization. Data classification helps to determine the appropriate level of protection and handling for the data. If the data is misclassified, it may not receive the adequate level of security controls, and it may be accessed by unauthorized or inappropriate users. The other options are not the greatest risks associated with the misclassification of data, as they are less likely or less severe than unauthorized access. Inadequate resource allocation is the risk of not allocating sufficient resources to protect the data, which may affect its availability and performance. Data disruption is the risk of losing or corrupting the data, which may affect its integrity and availability. Inadequate retention schedules is the risk of not retaining the data for the required period of time, which may affect its compliance and usability. References = CRISC Review Manual, 7th Edition, Chapter 4, Section 4.1.1, page 161.
Risk mitigation procedures should include:
buying an insurance policy.
acceptance of exposures
deployment of counter measures.
enterprise architecture implementation.
Risk mitigation procedures are the actions and plans that an organization implements to reduce the likelihood and impact of identified risks. Risk mitigation procedures should include the deployment of counter measures, which are the specific controls or solutions that address the root causes or sources of the risks, and prevent or minimize the potential losses or damages. For example, a counter measure for therisk of data breach could be encrypting the data or implementing a firewall. The deployment of counter measures should be based on a cost-benefit analysis, a risk assessment, and a risk response strategy. The other options are not necessarily part of risk mitigation procedures. Buying an insurance policy is an example of risk transfer, which is a risk response strategy that shifts the responsibility or burden of the risk to another party, such as an insurer or a vendor. However, risk transfer does not eliminate or reduce the risk itself, and it may involve additional costs or conditions. Acceptance of exposures is an example of risk acceptance, which is a risk response strategy that acknowledges the existence and consequences of the risk, and decides not to take any action to change the risk situation. However, risk acceptance does not mitigate the risk, and it may require contingency plans or reserves to deal with the potential outcomes. Enterprise architecture implementation is an example of a business process or project that may involve or create risks, but it is not a risk mitigation procedure itself. Enterprise architecture is the design and structure of an organization’s IT systems, networks, and resources, and how they align with the organization’s goals and strategies. Enterprise architecture implementation may require risk management activities, such as risk identification, assessment, and response, but it is not a risk mitigation procedure itself. References = Risk IT Framework, ISACA, 2022, p. 151
The MOST important characteristic of an organization s policies is to reflect the organization's:
risk assessment methodology.
risk appetite.
capabilities
asset value.
An organization’s policies are the set of rules and guidelines that define the organization’s objectives, expectations, and responsibilities for its activities and operations. They provide the direction and framework for the organization’s governance, risk management, and compliance functions.
The most important characteristic of an organization’s policies is to reflect the organization’s risk appetite, which is the amount and type of risk that the organization is willing to accept in pursuit of its goals. The risk appetite is usually expressed as a range or a threshold, and it is aligned with the organization’s strategy and culture.
Reflecting the organization’s risk appetite in its policies ensures that the policies are consistent, appropriate, and proportional to the level and nature of the risks that the organization faces, and that they support the organization’s objectives and values. It also helps to optimize the balance between risk and return, and to create and protect value for the organization and its stakeholders.
The other options are not the most important characteristic of an organization’s policies, because they do not address the fundamental question of whether the policies are suitable and acceptable for the organization.
The risk assessment methodology is the process of identifying, analyzing, and evaluating the risks that may affect the organization’s objectives and operations. It involves determining the likelihood and impact of various risk scenarios, and prioritizing them based on their significance and urgency. The risk assessment methodology is important to inform and support the organization’s policies, but it is not the most important characteristic of the policies, because it does not indicate whether the policies are aligned with the organization’s risk appetite.
The capabilities are the resources and abilities that the organization has or can acquire to achieve its objectives and manage its risks. They include the people, processes, technologies, and assets that the organization uses or relies on. The capabilities are important to enable and implement the organization’s policies, but they are not the most important characteristic of the policies, because they do not indicate whether the policies are aligned with the organization’s risk appetite.
The asset value is the worth or importance of the assets that the organization owns or controls, and that may be affected by the risks that the organization faces. The assets include the tangible and intangible resources that the organization uses or relies on, such as data, information, systems, infrastructure, reputation, etc. The asset value is important to measure and monitor the organization’s policies, but it is not the most important characteristic of the policies, because it does not indicate whether the policies are aligned with the organization’s risk appetite. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 29-30, 34-35, 38-39, 44-45, 50-51, 54-55
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 148
CRISC Practice Quiz and Exam Prep
Which of the following is the MOST effective way to help ensure future risk levels do not exceed the organization's risk appetite?
Developing contingency plans for key processes
Implementing key performance indicators (KPIs)
Adding risk triggers to entries in the risk register
Establishing a series of key risk indicators (KRIs)
Detailed Explanation:Key Risk Indicators (KRIs)are metrics used to monitor changes in risk exposure, enabling proactive adjustments to keep risks within appetite. They provide early warnings of potential breaches in risk thresholds.
A risk practitioner discovers several key documents detailing the design of a product currently in development have been posted on the Internet. What should be the risk practitioner's FIRST course of action?
invoke the established incident response plan.
Inform internal audit.
Perform a root cause analysis
Conduct an immediate risk assessment
According to the CRISC Review Manual (Digital Version), the first course of action when a risk practitioner discovers several key documents detailing the design of a product currently in development have been posted on the Internet is to invoke the established incident response plan, which is a set of policies, procedures, and resources that enable the organization to respond to and recover from an incident that affects the confidentiality, integrity, or availability of its IT assets and processes. Invoking the incident response plan helps to:
Contain and isolate the incident and prevent further damage or loss
Identify and analyze the source, cause, and impact of the incident
Eradicate and eliminate the incident and restore normal operations
Communicate and coordinate the incident response activities and roles with the relevant stakeholders, such as the business owner, the risk owner, the senior management, and the external parties
Learn and improve from the incident and update the incident response plan and the risk register
References = CRISC Review Manual (Digital Version), Chapter 4: IT Risk Monitoring and Reporting, Section 4.1: IT Risk Monitoring, pp. 219-2201
Which of the following will BEST help mitigate the risk associated with malicious functionality in outsourced application development?
Perform an m-depth code review with an expert
Validate functionality by running in a test environment
Implement a service level agreement.
Utilize the change management process.
The risk associated with malicious functionality in outsourced application development is that the vendor may introduce unauthorized or harmful code into the enterprise’s system, which could compromise its security, integrity, or performance.
To mitigate this risk, the enterprise should perform an in-depth code review with an expert who can verify that the code meets the specifications, standards, and quality requirements, and that it does not contain any malicious or unwanted functionality.
A code review is a systematic examination of the source code of a software program, which can identify errors, vulnerabilities, inefficiencies, or deviations from best practices. A code review can also ensure that the code is consistent, readable, maintainable, and well-documented.
An expert is someone who has the knowledge, skills, and experience to perform the code review effectively and efficiently. An expert may be an internal or external resource, depending on the availability, cost, and independence of the reviewer.
A code review should be performed before the code is deployed to the production environment, and preferably at multiple stages of the development life cycle, such as design, testing, and integration.
A code review can also be complemented by other techniques, such as automated code analysis, testing, and scanning tools, which can detect common or known issues in the code. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, p. 143
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 143
An organization wants to assess the maturity of its internal control environment. The FIRST step should be to:
validate control process execution.
determine if controls are effective.
identify key process owners.
conduct a baseline assessment.
A baseline assessment is the first step in assessing the maturity of an organization’s internal control environment. A baseline assessment is a comprehensive evaluation of the current state of the internal control structure, processes, and activities across the organization. A baseline assessment helps to identify the strengths and weaknesses of the existing internal controls, as well as the gaps and opportunities for improvement. A baseline assessment also provides a reference point for measuring the progress and effectiveness of the internal control improvement initiatives. The other options are not the first steps in assessing the maturity of an internal control environment, although they may be part of the subsequent steps. Validating control process execution is a technique to verify that the internal control activities are performed as designed and intended. Determining if controls are effective is a process to evaluate the adequacy and efficiency of the internal controls in achieving the desired outcomes and mitigating the risks. Identifying key process owners is a task to assign the roles and responsibilities for the internal control design, implementation, and monitoring to the appropriate individuals or groups within theorganization. References = CRISC Review Manual, pages 153-1541; CRISC Review Questions, Answers & Explanations Manual, page 742
After a risk has been identified, who is in the BEST position to select the appropriate risk treatment option?
The risk practitioner
The business process owner
The risk owner
The control owner
After a risk has been identified, the risk owner is in the best position to select the appropriate risk treatment option. The risk owner is the person or entity with the accountability and authority to manage a risk1. The risk owner is responsible for evaluating the risk, choosing the most suitable risk treatment option, implementing the risk treatment plan, and monitoring and reviewing the risk and its treatment2. The risk owner has the most knowledge and stake in the risk and its impact on the objectives and activities of the organization. The other options are not the best choices for selecting the risk treatment option, as they do not have the same level of accountability and authority as the risk owner. The risk practitioner is the person or entity with the knowledge and skills to perform the risk management activities1. The risk practitioner can assist the risk owner in identifying, analyzing, evaluating, and treating the risk, but the final decision and responsibility lies with the risk owner. The business process owner is the person or entity with the accountability and authority to manage a business process3. The business process owner may be affected by the risk or involved in the risk treatment, but the risk owner is the one who has the overall responsibility for the risk. The control owner is the person or entity with the accountability and authority to ensure that the controls are properly designed, implemented, and operated4. The control owner can provide input and feedback on the effectiveness and efficiency of the controls, but the risk owner is the one who decides which controls are needed and how they are applied. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.1.3, Page 51.
Which of the following provides the BEST evidence of the effectiveness of an organization's account provisioning process?
User provisioning
Role-based access controls
Security log monitoring
Entitlement reviews
An organization’s account provisioning process is the process of creating, modifying, or deleting user accounts and access rights for the organization’s information systems and resources. It involves defining the access requirements, policies, and standards, and implementing and enforcing them across the organization.
The best evidence of the effectiveness of an organization’s account provisioning process is entitlement reviews, which are the periodic or regular reviews and validations of the user accounts and access rights that are granted or assigned to the users or entities that interact with the organization’s information systems and resources. Entitlement reviews can provide assurance and verification that the account provisioning process is accurate, consistent, and compliant, and that it meets the organization’s security and business objectives and requirements.
Entitlement reviews can be performed using various techniques, such as automated tools, reports, audits, surveys, etc. Entitlement reviews can also be integrated with the organization’s governance, risk management, and compliance functions, and aligned with the organization’s policies and standards.
The other options are not the best evidence of the effectiveness of an organization’s account provisioning process, because they do not provide the same level of assurance and verification that the account provisioning process is accurate, consistent, and compliant, and that it meets the organization’s security and business objectives and requirements.
User provisioning is the process of creating, modifying, or deleting user accounts and access rights for a specific user or entity, based on their identity, role, or function in the organization. User provisioning is an important part of the account provisioning process, but it is not the best evidence of the effectiveness of the account provisioning process, because it does not indicate whether the user accounts and access rights are appropriate and authorized, and whether they comply with the organization’s policies and standards.
Role-based access controls are the controls that grant or restrict user accounts and access rights based on the predefined roles or functions that the users or entities perform or assume in the organization. Role-based access controls are an important part of the account provisioning process, but they are not the best evidence of the effectiveness of the account provisioning process, because they do not indicate whether the roles or functions are defined and assigned correctly and consistently, and whether they comply with the organization’s policies and standards.
Security log monitoring is the process of collecting, analyzing, and reporting on the security events or activities that are recorded or logged by the organization’s information systems and resources. Security log monitoring is an important part of the account provisioning process, but it is not the best evidence of the effectiveness of the account provisioning process, because it does not indicate whether the security events or activities are legitimate or authorized, and whether they comply with the organization’s policies and standards. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 40-41, 47-48, 54-55, 58-59, 62-63
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 173
CRISC Practice Quiz and Exam Prep
Which of the following is the PRIMARY reason to perform ongoing risk assessments?
Emerging risk must be continuously reported to management.
New system vulnerabilities emerge at frequent intervals.
The risk environment is subject to change.
The information security budget must be justified.
The primary reason to perform ongoing risk assessments is that the risk environment is subject to change. The risk environment is the external and internal factors that influence the level and nature of the risks that the organization faces1. These factors include economic, political, social, technological, legal,and environmental aspects, as well as the organization’s objectives, strategies, culture, and resources2. The risk environment is dynamic and unpredictable, and may change due to various events, trends, ordevelopments that create new or modify existing risks3. Therefore, it is important to perform ongoing risk assessments to identify, analyze, and evaluate the changes in the risk environment, and to adjust the risk response and management accordingly. Ongoing risk assessments help to ensure that the organization’s risk profile is up to date and reflects the current reality, and that the organization’s risk appetite and tolerance are aligned with the changing risk environment4. The other options are not the primary reason to perform ongoing risk assessments, as they are either less comprehensive or less relevant than the changing risk environment. Emerging risk must be continuously reported to management. This option is a consequence or outcome of performing ongoing risk assessments, not a reason for doing so. Emerging risk is a new or evolving risk that has the potential to affect the organization’s objectives, operations, or performance5. Ongoing risk assessments can help to identify and monitor emerging risks, and to report them to management for decision making and action. However, this is not the main reason for performing ongoing risk assessments, as it does not cover the existing or modified risks that may also change due to the risk environment. New system vulnerabilities emerge at frequent intervals. This option is a specific or narrow example of a changing risk environment, not a general or broad reason for performing ongoing risk assessments. System vulnerabilities are weaknesses or flaws in the design, implementation, or operation of information systems that can be exploited by threats to cause harm or loss6. Ongoing risk assessments can help to discover and assess new system vulnerabilities that may emerge due to technological changes, cyberattacks, or human errors. However, this is not the primary reason for performing ongoing risk assessments, as it does not encompass the other types or sources of risks that may also change due to the risk environment. The information security budget must be justified. This option is a secondary or incidental benefit of performing ongoing risk assessments, not a primary or essential reason for doing so. The information security budget is the amount of money that the organization allocates for implementing and maintaining information security measures and controls7. Ongoing risk assessments can help to justify the information security budget by demonstrating the value and effectiveness of the security measures and controls in reducing the risks, and by identifying the gaps or needs for additional or improved security measures and controls. However, this is not the main reason for performing ongoing risk assessments, as it does not address the purpose or objective of risk assessment, which is to identify, analyze, and evaluate the risks and their impact on the organization. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.1.1, Page 47.
Which of the following is the MOST important characteristic of an effective risk management program?
Risk response plans are documented
Controls are mapped to key risk scenarios.
Key risk indicators are defined.
Risk ownership is assigned
The most important characteristic of an effective risk management program is that risk ownership is assigned. Risk ownership is the accountability and authority to manage a risk1. Assigning risk ownership means identifying and assigning the person or entity who is responsible for evaluating, treating, monitoring, and reporting on a specific risk2. Assigning risk ownership is essential for ensuring that the risk management program works effectively and efficiently, as it helps to:
Clarify the roles and responsibilities of the different functions or groups involved in risk management and internal control;
Ensure that the risks are managed in accordance with the organization’s objectives, strategies, and risk appetite;
Provide guidance and support to the risk owners in identifying, assessing, and mitigating the risks;
Monitor and evaluate the performance and effectiveness of the risk owners and the risk response actions;
Communicate and report on the risk status and issues to the relevant stakeholders and authorities. The other options are not the most important characteristic of an effective risk management program, as they are either less relevant or less specific than assigning risk ownership. Risk response plans are documented. This option is a consequence or outcome of an effective risk management program, not a characteristic of it. Risk response plans are the actions or measures that are taken to modify the risk, such as reducing, avoiding, transferring, or accepting the risk3. Documenting risk response plans means recording and maintaining the details and outcomes of the risk responseactions, such as the objectives, scope, resources, timelines, performance indicators, and results4. Documenting risk response plans can help to improve the consistency and transparency of the risk management process, as well as to support the monitoring and evaluation of the risk response actions. However, documenting risk response plans is not the most important characteristic of an effective risk management program, as it does not address the accountability and authority for managing the risk. Controls are mapped to key risk scenarios. This option is a specific or narrow example of an effective risk management program, not a general or broad characteristic of it. Controls are the measures or actions that are taken to reduce the likelihood or impact of a risk, or to increase the likelihood or impact of an opportunity5. Mapping controls to key risk scenarios means linking the controls to the specific situations or events that may affect the organization’s objectives, operations, or performance6. Mapping controls to key risk scenarios can help to enhance the design and implementation of the controls, as well as to evaluate the effectiveness and efficiency of the controls in mitigating the risk. However, mapping controls to key risk scenarios is not the most important characteristic of an effective risk management program, as it does not cover the other aspects of risk management, such as risk identification, assessment, treatment, and monitoring. Key risk indicators are defined. This option is a component or element of an effective risk management program, not a characteristic of it. Key risk indicators are the metrics that measure thelevel and trend of a risk that may affect the organization’s objectives, operations, or performance7. Defining key risk indicators means establishing and maintaining the criteria and methods for measuring and reporting on the risk8. Defining key risk indicators can help to enhance the risk identification, assessment, and reporting processes, as well as to support the risk decision making and prioritization. However, defining key risk indicators is not the most important characteristic of an effective risk management program, as it does not indicate the accountability and authority for managing the risk. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 3, Section 3.1.1, Page 85.
Which of the following is the BEST key performance indicator (KPI) to measure the effectiveness of a disaster recovery plan (DRP)?
Number of users that participated in the DRP testing
Number of issues identified during DRP testing
Percentage of applications that met the RTO during DRP testing
Percentage of issues resolved as a result of DRP testing
A key performance indicator (KPI) is a measurable value that demonstrates how effectively an organization is achieving its objectives. In the context of disaster recovery planning (DRP), a KPI should reflect the ability of the organization to recover its critical business processes and applications within the predefined time frames and service levels. One of the most important KPIs for DRP is the percentage of applications that met the recovery time objective (RTO) during DRP testing. The RTO is the maximum acceptable length of time that a business process or application can be down after a disaster. By measuring the percentage of applications that met the RTO during DRP testing, the organization can evaluate the performance and reliability of its DRP, identify any gaps or weaknesses, and implement corrective actions to improve its readiness and resilience. The other options are not the best KPIs for DRP, as they do not directly measure the effectiveness of the recovery process. The number of users that participated in the DRP testing is a measure of the involvement and awareness of the staff, but not of the outcome of the testing. The number of issues identified during DRP testing is a measure of the quality and completeness of the DRP, but not of the actual recovery time. The percentage of issues resolved as a result of DRP testing is a measure of the improvement and maturity of the DRP, but not of the current recovery capability. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 3, Section 3.2.3.3, Page 138.
An effective control environment is BEST indicated by controls that:
minimize senior management's risk tolerance.
manage risk within the organization's risk appetite.
reduce the thresholds of key risk indicators (KRIs).
are cost-effective to implement
According to the CRISC Review Manual (Digital Version), an effective control environment is best indicated by controls that manage risk within the organization’s risk appetite, as this reflects the alignment of thecontrol objectives and activities with the organization’s strategic goals and risk preferences. The risk appetite is the amount and type of risk that the organization is willing to accept in pursuit of its objectives. Managing risk within the organization’s risk appetite helps to:
Balance the potential benefits and costs of risk-taking and risk response
Optimize the use of the organization’s resources and capabilities
Enhance the value and performance of the organization
Foster a risk-aware culture that supports the organization’s vision and mission
References = CRISC Review Manual (Digital Version), Chapter 2: IT Risk Assessment, Section 2.3: IT Risk Assessment Process, pp. 93-941
What is the BEST approach for determining the inherent risk of a scenario when the actual likelihood of the risk is unknown?
Use the severity rating to calculate risk.
Classify the risk scenario as low-probability.
Use the highest likelihood identified by risk management.
Rely on range-based estimates provided by subject-matter experts.
Detailed Explanation:When likelihood is unknown, range-based estimates from subject-matter experts provideinformed and realistic insights into potential risk exposure. This approach helps approximate the inherent risk based on experience and expertise, supporting effective decision-making.
The PRIMARY reason for a risk practitioner to review business processes is to:
Benchmark against peer organizations.
Identify appropriate controls within business processes.
Assess compliance with global standards.
Identify risk owners related to business processes.
Detailed Explanation:A review of business processes is crucial for identifying risk owners, as risk ownership is tied to specific processes within the organization. Risk owners are accountable for managing and mitigating risks within their respective areas. This ensures that risks are effectively addressed where they arise and aligns mitigation efforts with business objectives. Properly identifying risk owners supports better governance, accountability, and alignment with the organization's risk management strategy.
Which of the following should be the PRIMARY consideration when assessing the automation of control monitoring?
impact due to failure of control
Frequency of failure of control
Contingency plan for residual risk
Cost-benefit analysis of automation
Automation of control monitoring is the application of technology to allow continuous or high-frequency, automated monitoring of controls to validate the effectiveness of controls designed to mitigate risk1.
Automation of control monitoring can provide benefits such as increased test coverage, improved timeliness, reduced risk velocity, greater visibility, improved consistency, and the ability to identify trends23.
However, automation of control monitoring also involves costs such as the acquisition, implementation, maintenance, and updating of the technology, as well as the training and support of the staff who use it45.
Therefore, the primary consideration when assessing the automation of control monitoring is the cost-benefit analysis of automation, which compares the expected benefits and costs of automation and determines whether the benefits outweigh the costs or vice versa45.
The other options are not the primary consideration, but rather secondary or tertiary factors that may influence the decision to automate or not. For example, the impact due to failure of controland the frequency of failure of control are aspects of the risk assessment that may indicate the need for automation, but they do not provide the basis for evaluating the feasibility and desirability of automation45. Similarly, the contingency plan for residual risk is a component of the risk response that may include automation as a risk mitigation strategy, but it does not measure the effectiveness and efficiency of automation45. References =
2: A Practical Approach to Continuous Control Monitoring, ISACA Journal, Volume 2, 2015
3: Continuous Controls Monitoring: The Next Generation Of Controls Testing, Forbes Technology Council, June 2, 2022
1: Making Continuous Controls Monitoring Work for Everyone, ISACA Now Blog, June 13, 2022
4: Controls Automation - Monitoring vs. Operation - Part 3, Turnkey Consulting, July 29, 2021
5: What’s Continuous Control Monitoring and Why Is It Important?, MetricStream Blog, October 15, 2019
An organization's senior management is considering whether to acquire cyber insurance. Which of the following is the BEST way for the risk practitioner to enable management’s decision?
Perform a cost-benefit analysis.
Conduct a SWOT analysis.
Provide data on the number of risk events from the last year.
Report on recent losses experienced by industry peers.
Detailed Explanation:Acost-benefit analysisevaluates the financial implications of acquiring cyber insurance versus the potential loss exposure. This approach enables informed decision-making by comparing the insurance cost with the potential savings from covered risks.
The PRIMARY benefit of maintaining an up-to-date risk register is that it helps to:
implement uniform controls for common risk scenarios.
ensure business unit risk is uniformly distributed.
build a risk profile for management review.
quantify the organization's risk appetite.
A risk register is a document that records and tracks the information and status of the identified risks and their responses. It includes the risk description, category, source, cause, impact, probability, priority, response, owner, action plan, status, etc.
A risk profile is a summary or representation of the organization’s exposure or level of risk, based on the results of the risk assessment and evaluation. A risk profile can show the distribution and comparison of the risks based on various criteria, such as likelihood, impact, category, source, etc. A risk profile can also indicate the organization’s risk appetite and tolerance, and the gaps or opportunities for improvement.
The primary benefit of maintaining an up-to-date risk register is that it helps to build a risk profile for management review, because it provides the data and information that are necessary and relevant for creating and updating the risk profile, and for communicating and reporting the risk profile to the management. Maintaining an up-to-date risk register can help to build a risk profile for management review by providing the following benefits:
It can ensure that the risk profile reflects the current and accurate state and performance of the organization’s risk management function, and that it covers all the relevant and significant risks that may affect the organization’s objectives and operations.
It can provide useful references and benchmarks for the identification, analysis, evaluation, and communication of the risks and their responses, and for the alignment and integration of the risks and their responses with the organization’s strategy and culture.
It can support the decision making and planning for the risk management function, and for the allocation and optimization of the resources, time, and budget for the risk management function.
The other options are not the primary benefits of maintaining an up-to-date risk register, because they do not address the main purpose and benefit of building a risk profile for management review, which is to summarize and represent the organization’s exposure or level of risk, and to communicate and report it to the management.
Implementing uniform controls for common risk scenarios means applying and enforcing the same or similar controls or countermeasures for the risks that have the same or similar characteristics or features, such as source, cause, impact, etc. Implementing uniform controls for common risk scenarios can help to ensure the consistency and efficiency of the risk management function, but it is not the primary benefit of maintaining an up-to-date risk register, because it does not summarize or represent the organization’s exposure or level of risk, and it may not be relevant or appropriate for the organization’s objectives and needs.
Ensuring business unit risk is uniformly distributed means ensuring that the risks that are associated with the different business units or divisions of the organization are balanced or equalized, and that they do not exceed or fall below the organization’s risk appetite and tolerance. Ensuring business unit risk is uniformly distributed can help to optimize the performance and profitability of the organization, but it is not the primary benefit of maintaining an up-to-date risk register, because it does not summarize or represent the organization’s exposure or level of risk, and it may not be feasible or realistic for the organization.
Quantifying the organization’s risk appetite means measuring and expressing the amount and type of risk that the organization is willing and able to accept or take, in pursuit of its objectives and goals. Quantifying the organization’s risk appetite can help to establish and communicate the boundaries and expectations for the organization’s risk management function, but it is not the primary benefit of maintaining an up-to-date risk register, because it does not summarize or represent the organization’s exposure or level of risk, and it may not be consistent or compatible with the organization’s strategy and culture. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 19-20, 23-24, 27-28, 31-32, 40-41, 47-48, 54-55, 58-59, 62-63
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 201
CRISC Practice Quiz and Exam Prep
Which of the following should be the risk practitioner s PRIMARY focus when determining whether controls are adequate to mitigate risk?
Sensitivity analysis
Level of residual risk
Cost-benefit analysis
Risk appetite
The risk practitioner’s primary focus when determining whether controls are adequate to mitigate risk should be the level of residual risk, because this indicates the amount and type of risk that remains after applying the controls, and whether it is acceptable or not. Residual risk is the risk that is left over after the risk responseactions have been taken, such as implementing or improving controls. Controls are the measures or actions that are designed and performed to reduce the likelihood and/or impact of a risk event, or to exploit the opportunities that a risk event may create. The adequacy of controls to mitigate risk depends on how well they address the root causes or sources of the risk, and how effectively and efficiently they reduce the risk exposure and value. The level of residual risk reflects the adequacy of controls to mitigate risk, as it shows the gap between the inherent risk and the actual risk, and whether it is within the organization’s risk appetite and tolerance. The risk practitioner should focus on the level of residual risk when determining whether controls are adequate to mitigate risk, as it helps to evaluate and compare the benefits and costs of the controls, and to decide on the best risk response strategy, such as accepting, avoiding, transferring, or further reducing the risk. The other options are less important or relevant to focus on when determining whether controls are adequate to mitigate risk. Sensitivity analysis is a technique that measures how the risk value changes when one or more input variables are changed, such as the probability, impact, or control effectiveness. Sensitivity analysis can help to identify and prioritize the most influential or critical variables that affect the risk value, and to test the robustness or reliability of the risk assessment. However, sensitivity analysis does not directly indicate the adequacy of controls to mitigate risk, as it does not measure the level of residual risk or the risk acceptance criteria. Cost-benefit analysis is a technique that compares the expected benefits and costs of a control or a risk response action, and determines whether it is worthwhile or not. Cost-benefit analysis can help to justify and optimize the investment or resource allocation for the control or the risk response action, and to ensure that it is aligned with the organization’s objectives and value. However, cost-benefit analysis does not directly indicate the adequacy of controls to mitigate risk, as it does not measure the level of residual risk or the risk acceptance criteria. Risk appetite is the amount and type of risk that an organization is willing to accept in pursuit of its objectives. Risk appetite can help to define and communicate the organization’s risk preferences and boundaries, and to guide the risk decision-making and behavior. However, risk appetite does not directly indicate the adequacy of controls to mitigate risk, as it does not measure the level of residual risk or the actual risk performance. References = Risk IT Framework, ISACA, 2022, p. 131
Which of the following BEST enables effective risk-based decision making?
Performing threat modeling to understand the threat landscape
Minimizing the number of risk scenarios for risk assessment
Aggregating risk scenarios across a key business unit
Ensuring the risk register is updated to reflect changes in risk factors
Detailed Explanation:An updatedrisk registerensures that decision-makers have accurate, timely information about current risks, enabling informed, risk-based decisions that align with organizational priorities and changes in the environment.
The PRIMARY reason a risk practitioner would be interested in an internal audit report is to:
plan awareness programs for business managers.
evaluate maturity of the risk management process.
assist in the development of a risk profile.
maintain a risk register based on noncompliance.
According to the CRISC Review Manual (Digital Version), the primary reason a risk practitioner would be interested in an internal audit report is to evaluate the maturity of the risk management process, as it provides an independent and objective assessment of the effectiveness and efficiency of the risk management activities and controls. An internal audit report helps to:
Identify and evaluate the strengths and weaknesses of the risk management process and its alignment with the organization’s objectives and strategy
Detect and report any gaps, errors, or deficiencies in the risk identification, assessment, response, and monitoring processes and controls
Recommend and implement corrective actions or improvement measures to address the issues or findings in the risk management process
Communicate and coordinate the audit results and recommendations with the relevant stakeholders, such as the risk owners, the senior management, and the board
Enhance the accountability and transparency of the risk management process and its outcomes
References = CRISC Review Manual (Digital Version), Chapter 4: IT Risk Monitoring and Reporting, Section 4.2: IT Risk Reporting, pp. 223-2241
Which of the following would be MOST useful when measuring the progress of a risk response action plan?
Percentage of mitigated risk scenarios
Annual loss expectancy (ALE) changes
Resource expenditure against budget
An up-to-date risk register
A risk response action plan is a document that outlines the specific tasks, resources, timelines, and deliverables for the risk responses, which are the actions or strategies that are taken to address the risks that may affect the organization’s objectives, performance, or value creation12.
The most useful tool when measuring the progress of a risk response action plan is an up-to-date risk register, which is a document that records and tracks the significant risks that the organization faces, and the responses and actions that are taken to address them34.
An up-to-date risk register is the most useful tool because it provides a comprehensive and consistent view of the risk landscape, and the status and performance of the risk responses and actions34.
An up-to-date risk register is also the most useful tool because it enables the monitoring and evaluation of the risk response action plan, and the identification and communication of any issues or gaps that need to be resolved or improved34.
The other options are not the most useful tools, but rather possible metrics or indicators that may be used to measure the progress of a risk response action plan. For example:
Percentage of mitigated risk scenarios is a metric that measures the proportion of risk scenarios that have been reduced or eliminated by the risk responses and actions56. However, this metric is not the most useful tool because it does not provide a comprehensive and consistent view of the risk landscape, and it may not capture the residual or emerging risks that may arise after the risk responses and actions56.
Annual loss expectancy (ALE) changes is a metric that measures the difference between the expected annual losses before and after the risk responses and actions78. However, this metric is not the most useful tool because it does not provide a comprehensive and consistent view of the risk landscape, and it may not reflect the qualitative or intangible impacts of the risks or the risk responses and actions78.
Resource expenditure against budget is a metric that measures the amount of resources and funds that have been spent or allocated for the risk responses and actions, compared to the planned or estimated budget . However, this metric is not the most useful tool because it does not provide a comprehensive and consistent view of the risk landscape, and it may not indicate the effectiveness or efficiency of the risk responses and actions . References =
1: Risk Response Plan in Project Management: Key Strategies & Tips1
2: How to Create the Ultimate Risk Response Plan | Wrike2
3: Risk Register Template and Examples | Prioritize and Manage Risk3
4: Risk Register Examples for Cybersecurity Leaders4
5: Risk Scenarios Toolkit, ISACA, 2019
6: Risk Scenarios Starter Pack, ISACA, 2019
7: Annualized Loss Expectancy (ALE) - Definition and Examples5
8: Annualized Loss Expectancy (ALE) Calculator6
Project Budgeting: How to Estimate Costs and Manage Budgets7
Project Budget Template - Download Free Excel Template8
An organization has procured a managed hosting service and just discovered the location is likely to be flooded every 20 years. Of the following, who should be notified of this new information FIRST.
The risk owner who also owns the business service enabled by this infrastructure
The data center manager who is also employed under the managed hosting services contract
The site manager who is required to provide annual risk assessments under the contract
The chief information officer (CIO) who is responsible for the hosted services
The risk owner is the person who has the authority and accountability to manage a specific risk and its associated controls. The risk owner is also responsible for ensuring that the risk is within the acceptable level and that the risk response is effective and efficient. In this case, the risk owner is also the owner of the business service that depends on the managed hosting service. Therefore, the risk owner should be notified of the new information about the flood risk first, as they have the most interest and influence on the risk and its impact on the business objectives. The risk owner can then decide on the appropriate actions to take, such as reviewing the contract terms, requesting additional controls, or changing the service provider. The other options are not the correct answers because they are not the primary stakeholders of the risk and its consequences. The data center manager is an employee of the managed hosting service provider, not the organization that procured the service. The data center manager may not have the authority or the incentive to address the flood risk or inform the organization. The site manager is also an employee of the managed hosting service provider, and their role is to conduct annual risk assessments under the contract. The site manager may not be aware of the new information or have the responsibility to communicate it to the organization. The CIO is the senior executive who oversees the IT strategy and operations of the organization. The CIO may have a general interest in the managed hosting service and its risks, but they are not the direct owner or manager of the specific risk or the business service that relies on the service. References = CRISC Review Manual, pages 32-331; CRISC Review Questions, Answers & Explanations Manual, page 702
An audit reveals that several terminated employee accounts maintain access. Which of the following should be the FIRST step to address the risk?
Perform a risk assessment
Disable user access.
Develop an access control policy.
Perform root cause analysis.
The risk of terminated employee accounts maintaining access is that the former employees or unauthorized parties may use the accounts to access or manipulate the organization’s information systems or resources, and cause harm or damage to the organization and its stakeholders, such as data loss, data breach, system failure, fraud, etc.
The first step to address the risk of terminated employee accounts maintaining access is to disable user access, which means to revoke or remove the permissions or privileges that allow the accounts to access or use the organization’s information systems or resources. Disabling user access can help the organization to address the risk by providing the following benefits:
It can prevent or stop the former employees or unauthorized parties from accessing or using the organization’s information systems or resources, and reduce or eliminate the potential harm or damage that they may cause for the organization and its stakeholders.
It can ensure the confidentiality, integrity, availability, and reliability of the organization’s information systems or resources, and protect them from unauthorized access or manipulation.
It can provide useful evidence and records for the verification and validation of the organization’s access control function, and for the compliance with the organization’s access control policies and standards.
The other options are not the first steps to address the risk of terminated employee accounts maintaining access, because they do not provide the same level of urgency and effectiveness that disabling user access provides, and they may not be sufficient or appropriate to address the risk.
Performing a risk assessment is a process of measuring and comparing the likelihood and impact of various risk scenarios, and prioritizing them based on their significance and urgency. Performing a risk assessment can help the organization to understand and document the risk of terminated employee accounts maintaining access, but it is not the first step to address the risk, because it does not prevent or stop the former employees or unauthorized parties from accessing or using the organization’s information systems or resources, and it may not be timely or feasible to perform a risk assessment before disabling user access.
Developing an access control policy is a process of defining and describing the rules or guidelines that specify the expectations and requirements for the organization’s access control function, such as who can access what, when, how, and why. Developing an access control policy can help the organization to establish and communicate the boundaries and objectives for the organization’s access control function, but it is not the first step to address the risk, because it does not prevent or stop the former employees or unauthorized parties from accessing or using the organization’s information systems or resources, and it may not be relevant or applicable to the existing or emerging risk scenarios that may affect the organization’s access control function.
Performing a root cause analysis is a process of identifying and understanding the underlying or fundamental causes or factors that contribute to or result in a problem or incident that has occurred or may occur in the organization. Performing a root cause analysis can help the organization to address and correct the risk of terminated employee accounts maintaining access, and prevent or reduce its recurrence or impact, but it is not the first step to address the risk, because it does not prevent or stop the former employees or unauthorized parties from accessing or using the organization’s information systems or resources, and it may not be timely or feasible to perform a root cause analysis before disabling user access. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 40-41, 47-48, 54-55, 58-59, 62-63
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 207
CRISC Practice Quiz and Exam Prep
From a business perspective, which of the following is the MOST important objective of a disaster recovery test?
The organization gains assurance it can recover from a disaster
Errors are discovered in the disaster recovery process.
All business-critical systems are successfully tested.
All critical data is recovered within recovery time objectives (RTOs).
A disaster recovery test is a simulation of a disaster scenario that evaluates the effectiveness and readiness of the disaster recovery plan. The main purpose of a disaster recovery test is to ensure that the organization can resume its normal operations as quickly as possible after a disaster, with minimal or no data loss. Therefore, the most important objective of a disaster recovery test from a business perspective is to verify that all critical data can be recovered within the RTOs, which are the maximum acceptable time frames for restoring the data and systems after a disaster. If the RTOs are not met, the organization may face significant financial, operational, and reputational losses. The other options are not the most important objectives of a disaster recovery test, although they may be beneficial outcomes. Gaining assurance that the organization can recover from a disaster is a subjective and qualitative goal, while recovering data within RTOs is a measurable and quantitative goal. Discovering errors in the disaster recovery process is a valuable result of a disaster recovery test, but it is not the primary objective. The objective is to correct the errors and improve the process, not just to find them. Testing all business critical systems is a necessary step in a disaster recovery test, but it is not the ultimate goal. The goal is to ensure that the systems can be restored and function properly within the RTOs. References = CRISC Review Manual, pages 197-1981; CRISC Review Questions, Answers & Explanations Manual, page 572
Which of the following is the MAIN reason to continuously monitor IT-related risk?
To redefine the risk appetite and risk tolerance levels based on changes in risk factors
To update the risk register to reflect changes in levels of identified and new IT-related risk
To ensure risk levels are within acceptable limits of the organization's risk appetite and risk tolerance
To help identify root causes of incidents and recommend suitable long-term solutions
According to the CRISC Review Manual (Digital Version), the main reason to continuously monitor IT-related risk is to ensure risk levels are within acceptable limits of the organization’s risk appetite and risk tolerance. The risk appetite is the amount and type of risk that an organization is willing to accept in pursuit of its objectives, while the risk tolerance is the acceptable variation in outcomes related to specific performance measures linked to objectives. Continuous monitoring is a process that tracks the security state of an information system on an ongoing basis and maintains the security authorization for the system over time. Continuous monitoring helps to:
Provide ongoing assurance that the implemented security controls are operating effectively and efficiently
Detect changes in the risk profile of the information system and the environment of operation
Identify new or emerging threats and vulnerabilities that may affect the information system
Support risk-based decisions by providing timely and relevant risk information to stakeholders
Facilitate the implementation of corrective actions and risk mitigation strategies
Promote accountability and transparency in the risk management process
Enhance the security awareness and culture within the organization
References = CRISC Review Manual (Digital Version), Chapter 4: IT Risk Monitoring and Reporting, Section 4.1: IT Risk Monitoring, pp. 213-2141
Which of the following is the MOST important outcome of reviewing the risk management process?
Assuring the risk profile supports the IT objectives
Improving the competencies of employees who performed the review
Determining what changes should be made to IS policies to reduce risk
Determining that procedures used in risk assessment are appropriate
The most important outcome of reviewing the risk management process is assuring that the risk profile supports the IT objectives, because this ensures that the organization is managing its IT-related risks in alignment with its business goals and priorities. The risk profile is a summary of the key risks that the organization faces, their likelihood, impact, and response strategies. The IT objectives are the specific and measurable outcomes that the organization expects to achieve from its IT investments and activities. Byreviewing the risk management process, the organization can evaluate whether the risk profile is accurate, complete, and up-to-date, and whether the risk responses are effective, efficient, and consistent with the IT objectives. The review can also identify any gaps, issues, or opportunities for improvement in the risk management process, and provide recommendations for enhancing the process and its outcomes. The review can also help to communicate and report the value and performance of the risk management process to the senior management, the board of directors, and other stakeholders. References = Risk IT Framework, ISACA, 2022, p. 17
Which of the following is the MOST important key performance indicator (KPI) to establish in the service level agreement (SLA) for an outsourced data center?
Percentage of systems included in recovery processes
Number of key systems hosted
Average response time to resolve system incidents
Percentage of system availability
The percentage of system availability is the most important key performance indicator (KPI) to establish in the service level agreement (SLA) for an outsourced data center. This KPI measures the uptime or reliability of the systems hosted by the data center provider, and reflects the ability of the provider to meet the customer’s expectations and requirements for system performance and accessibility. A high percentage of system availability indicates that the provider is delivering consistent and quality service, while a low percentage of system availability indicates that the provider is experiencing frequent or prolonged system failures or disruptions, which can negatively affect the customer’s business operations and reputation. Therefore, the percentage of system availability is a critical factor for evaluating the effectiveness and efficiency of the data center provider, and should be clearly defined and monitored in the SLA. The other options are not the most important KPIs to establish in the SLA for an outsourced data center, as they do not directly measure the quality or reliability of the service provided. The percentage of systems included in recovery processes is a measure of the scope or coverage of the disaster recovery plan (DRP) of the data center provider, but it does not indicate how well the provider can execute the DRP or restore the systems in the event of a disaster. The number of key systems hosted is a measure of the capacity or utilization of the data center provider, but it does not indicate how efficiently or securely the provider can manage the systems. The average response time to resolve system incidents is a measure of the responsiveness or agility of the data center provider, but it does not indicate how effectively or proactively the provider can prevent or mitigate system incidents. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 3, Section 3.2.3.4, Page 140.
Which of the following would provide the BEST guidance when selecting an appropriate risk treatment plan?
Risk mitigation budget
Business Impact analysis
Cost-benefit analysis
Return on investment
A cost-benefit analysis is the best guidance when selecting an appropriate risk treatment plan. A risk treatment plan is a document that describes the actions or measures that are taken or planned to modifythe risk, such as reducing, avoiding, transferring, or accepting the risk1. Selecting an appropriate risk treatmentplan means choosing the most suitable and effective option for addressing the risk, based on the organization’s objectives, strategies, and risk criteria2. A cost-benefit analysis is a method of comparing the benefits and costs of different alternatives or options, and selecting the one that maximizes the net benefit or value3. A cost-benefit analysis is the best guidance when selecting an appropriate risk treatment plan, because it helps to:
Evaluate the feasibility, effectiveness, and efficiency of the risk treatment options, and compare them against the organization’s risk appetite and tolerance;
Balance the benefits and costs of the risk treatment options, and consider both the quantitative and qualitative aspects of the risk and the risk response;
Optimize the use of the organization’s resources and capabilities, and ensure that the risk treatment options are aligned and integrated with the organization’s goals and values;
Support the risk decision making and prioritization, and provide a rational and transparent basis for selecting the best risk treatment option. The other options are not the best guidance when selecting an appropriate risk treatment plan, as they are either less comprehensive or less relevant than a cost-benefit analysis. A risk mitigation budget is a document that allocates the financial resources for implementing and maintaining the risk mitigation actions or measures4. A risk mitigation budget can help to ensure the availability and adequacy of the funds for the risk treatment options, as well as to monitor and control the risk treatment expenditures. However, a risk mitigation budget is not the best guidance when selecting an appropriate risk treatment plan, as it does not address the benefits or value of the risk treatment options, or the suitability or effectiveness of the risk treatment options. A business impact analysis is a method of estimating the potential effects or consequences of a risk on the organization’s objectives, operations, or performance5. A business impact analysis can help to assess the severity and priority of the risk, as well as to identify the critical assets and resources that are involved or impacted by the risk. However, a business impact analysis is not the best guidance when selecting an appropriate risk treatment plan, as it does not address the costs or feasibility of the risk treatment options, or the alternatives or options for the risk treatment. A return on investment is a metric that measures the profitability or efficiency of an investment, project, or activity, by comparing the benefits and costs of the investment, project, or activity6. A return on investment can help to evaluate the performance and effectiveness of the risk treatment options, as well as to compare the risk treatment options with other investments, projects, or activities. However, a return on investment is not the best guidance when selecting an appropriate risk treatment plan, as it does not address the qualitative or intangible aspects of the risk and the risk response, or the risk appetite and tolerance of the organization. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.1.8, Page 61.
A rule-based data loss prevention {DLP) tool has recently been implemented to reduce the risk of sensitive data leakage. Which of the following is MOST likely to change as a result of this implementation?
Risk likelihood
Risk velocity
Risk appetite
Risk impact
A rule-based data loss prevention (DLP) tool is a software solution that identifies and helps prevent unsafe or inappropriate sharing, transfer, or use of sensitive data. It can help an organization monitor and protect sensitive information across on-premises systems, cloud-based locations, and endpoint devices. It can also help an organization comply with regulations such as the Health Insurance Portability and Accountability Act (HIPAA) and General Data Protection Regulation (GDPR). A rule-based DLP tool works by comparing content to the organization’s DLP policy, which defines how the organization labels, shares, and protects data without exposing it to unauthorized users. The tool can then apply protective actions such as encryption, access restrictions, and alerts. As a result of implementing a rule-based DLP tool, the most likely change is the reduction of risk likelihood, which is the probability of a risk event occurring. By detecting and preventing data breaches, exfiltration, or unwanted destruction of sensitive data, a rule-based DLP tool can lower the chance of such incidents happening and thus decrease the risk likelihood. The other options are less likely to change as a result of implementing a rule-based DLP tool. Risk velocity is the speed at which a risk event impacts an organization, which depends on factors such as the nature of the threat, the response time, and the recovery process. Risk appetite is the amount and type of risk that an organization is willing to accept in pursuit of its objectives, which depends on factors such as the organization’s culture, strategy, and stakeholder expectations. Risk impact is the potential loss or damage that a risk event can cause to an organization, which depends on factors such as the severity of the incident, the extent of the exposure, andthe resilience of the organization. While a rule-based DLP tool may have some influence on these factors, it is not the primary driver of change for them. References = Risk IT Framework, ISACA, 2022, p. 13
A global organization is considering the acquisition of a competitor. Senior management has requested a review of the overall risk profile from the targeted organization. Which of the following components of this review would provide the MOST useful information?
Risk appetite statement
Enterprise risk management framework
Risk management policies
Risk register
According to the CRISC Review Manual (Digital Version), the risk register is the most useful component of the review of the overall risk profile from the targeted organization, as it provides a comprehensive and up-to-date record of the identified risks, their likelihood and impact, their risk response actions, and their residual risk levels. The risk register helps to:
Understand the current and potential threats and vulnerabilities that may affect the targeted organization’s objectives and performance
Evaluate the effectiveness and efficiency of the risk management processes and controls implemented by the targeted organization
Identify the gaps or weaknesses in the risk management practices and capabilities of the targeted organization
Assess the compatibility and alignment of the risk appetite and risk tolerance of the targeted organization with the acquiring organization
Estimate the value and benefits of the acquisition and the potential risks and costs involved
References = CRISC Review Manual (Digital Version), Chapter 1: IT Risk Identification, Section 1.5: IT Risk Identification Methods and Techniques, pp. 38-391
A risk practitioner has determined that a key control does not meet design expectations. Which of the following should be done NEXT?
Document the finding in the risk register.
Invoke the incident response plan.
Re-evaluate key risk indicators.
Modify the design of the control.
The next step after determining that a key control does not meet design expectations is to document the finding in the risk register, because this helps to record and track the information about the identified risk, such as its description, likelihood, impact, response, and status. A key control is a control that addresses a significant risk or supports a critical business process or objective. A control design expectation is a criterion or requirement that defines how the control should operate or perform to achieve its objective. If a key control does not meet its design expectation, it means that there is a gap, weakness, or deficiency in the control that may compromise its effectiveness or efficiency, and increase the risk exposure or impact. By documenting the finding in the risk register, the risk practitioner can communicate and report the risk issue to the relevant stakeholders, such as the risk owner, the management, or the auditor, and initiate the appropriate risk response actions, such as modifying the design of the control, implementing a compensating control, or accepting the risk. The other options are not the best next steps after determining that a key control does not meet design expectations. Invoking the incident response plan is a reactive measure that is triggered when a risk event occurs or is imminent, and requires immediate action to contain, mitigate, or recover from the incident. However, in this case, the risk event has not occurred yet, and there may be time to prevent or reduce it by improving the control design. Re-evaluating key risk indicators is a monitoring activity that measures and evaluates the level and impact of risks, and provides timely signals that something may be going wrong or needs urgent attention. However, in this case, the risk practitioner has already identified the risk issue, and needs to document and address it, rather than re-evaluate it. Modifying the design of the control is a possible risk response action that may be taken to improve the control and reduce the risk, but it is not the next step after determining that the key control does not meet design expectations. The next step is to document the finding in the risk register, and then decide on the best risk response action, which may or may not be modifying the design of the control, depending on the cost-benefit analysis, the risk assessment, and the risk response strategy. References = Risk IT Framework, ISACA, 2022, p. 13
Which of the following is MOST important when developing key performance indicators (KPIs)?
Alignment to risk responses
Alignment to management reports
Alerts when risk thresholds are reached
Identification of trends
Key performance indicators (KPIs) are quantifiable measures of progress toward an intended result, such as a strategic objective or a desired outcome12.
The most important factor when developing KPIs is the alignment to risk responses, which are the actions taken to address the risks that may affect the achievement of the intended result12.
Alignment to risk responses means that the KPIs should reflect the effectiveness and efficiency of the risk responses, and provide feedback and guidance for improving the risk responses12.
Alignment to risk responses also means that the KPIs should be consistent and compatible with the risk responses, and support the risk management process and objectives12.
The other options are not the most important factor, but rather possible aspects or features of KPIs that may vary depending on the context and purpose of the KPIs. For example:
Alignment to management reports is an aspect of KPIs that relates to the communication and presentation of the KPIs to the relevant stakeholders, such as senior management,board members, or external parties12. However, this aspect does not determine the quality or validity of the KPIs, or the alignment to the intended result12.
Alerts when risk thresholds are reached is a feature of KPIs that relates to the monitoring and control of the KPIs, and the triggering of actions or decisions when the KPIs exceed or fall below a certain level or range12. However, this feature does not define the content or scope of the KPIs, or the alignment to the intended result12.
Identification of trends is a feature of KPIs that relates to the analysis and interpretation of the KPIs, and the identification of patterns or changes in the KPIs over time or across different dimensions12. However, this feature does not specify the criteria or methodology of the KPIs, or the alignment to the intended result12. References =
1: What is a Key Performance Indicator (KPI)? Guide & Examples - Qlik3
2: What is a Key Performance Indicator (KPI)? - KPI.org4
Which of the following is a specific concern related to machine learning algorithms?
Low software quality
Lack of access controls
Data breaches
Data bias
Detailed Explanation:Data biasin machine learning algorithms can lead to inaccurate predictions or decisions, as biases in training data are amplified in the output. Addressing bias is essential for ethical and reliable algorithm performance.
Risk management strategies are PRIMARILY adopted to:
take necessary precautions for claims and losses.
achieve acceptable residual risk levels.
avoid risk for business and IT assets.
achieve compliance with legal requirements.
According to the CRISC Review Manual (Digital Version), risk management strategies are primarily adopted to achieve acceptable residual risk levels, which are the remaining risk levels after implementing risk response actions. Residual risk levels should be aligned with the organization’s risk appetite and risk tolerance, which are the amount and type of risk that the organization is willing to accept in pursuit of its objectives and the acceptable variation in outcomes related to specific performance measures linked to objectives. Risk management strategies are the approaches or methods used to address risks, such as avoidance, mitigation, transfer, sharing, or acceptance. Risk management strategies should be based on a cost-benefit analysis of the alternatives available and the value of the assets at risk.
References = CRISC Review Manual (Digital Version), Chapter 3: IT Risk Response, Section 3.3: Risk Response Options, pp. 166-1691
A risk heat map is MOST commonly used as part of an IT risk analysis to facilitate risk:
communication
identification.
treatment.
assessment.
A risk heat map is a tool that shows the likelihood and impact of different risks on a matrix, using colors to indicate the level of risk. A risk heat map is most commonly used as part of an IT risk analysis to facilitate risk assessment, which is the process of estimating the probability and consequences of the risks, and comparing them against the risk criteria1. A risk heat map can help to visualize, communicate, and prioritize the risks, as well as to evaluate the effectiveness of the risk response actions2. The other options are not the best choices for describing the purpose of a risk heat map, as they are either less specific or less relevant than risk assessment. Risk communication is the process of sharing and exchanging information about the risks among the stakeholders3. A risk heat map can support risk communication by providing a clear and concise representation of the risks, but it is not the main objective of the tool. Riskidentification is the process of finding, recognizing, and describing the risks that may affect the organization4. A risk heat map can help to identify the risks by categorizing them into different domains or sources, but it is not the primary function of the tool. Risk treatment is the process of selecting and implementing the appropriate measures to modify the risk5. A risk heat map can help to guide the risk treatment by showing the risk ratings and thresholds, but it is not the core purpose of the tool. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.1.1, Page 47.
The BEST way to justify the risk mitigation actions recommended in a risk assessment would be to:
align with audit results.
benchmark with competitor s actions.
reference best practice.
focus on the business drivers
The best way to justify the risk mitigation actions recommended in a risk assessment would be to focus on the business drivers, which are the factors that influence the organization’s objectives, performance, and value creation12.
Focusing on the business drivers means aligning the risk mitigation actions with the organization’s strategic goals, priorities, and values, and demonstrating how the actions will support or enhance the organization’s capabilities, opportunities, and competitive advantage12.
Focusing on the business drivers also means communicating the benefits, costs, and trade-offs of the risk mitigation actions to the relevant stakeholders, and showing how the actions will address the organization’s risk appetite, tolerance, and exposure12.
The other options are not the best way to justify the risk mitigation actions, but rather possible sources of information or guidance that may support the justification. For example:
Aligning with audit results is a way to validate the effectiveness and efficiency of the risk mitigation actions, and to identify any gaps or weaknesses that need improvement34. However, audit results may not reflect the organization’s current or future business drivers, and may not capture the full scope or impact of the risk mitigation actions34.
Benchmarking with competitor’s actions is a way to compare the organization’s risk mitigation actions with the best practices or standards of the industry or market, and to identify any areas of improvement or differentiation56. However, competitor’s actions may not be suitable or applicable for the organization’s specific context, needs, or challenges, and may not align with the organization’s business drivers56.
Referencing best practice is a way to adopt the proven or accepted methods or techniques for risk mitigation, and to ensure the quality and consistency of the risk mitigation actions78. However, best practice may not be the most optimal or innovative solution for the organization’s unique situation, and may not address the organization’s business drivers78. References =
1: Risk IT Framework, ISACA, 2009
2: IT Risk Management Framework, University of Toronto, 2017
3: IT Audit and Assurance Standards, ISACA, 2014
4: IT Audit and Assurance Guidelines, ISACA, 2014
5: Benchmarking IT Risk Management Practices, ISACA Journal, Volume 4, 2017
6: Benchmarking: A Tool for Improving IT Risk Management, ISACA Now Blog, March 27, 2017
7: IT Risk Management Best Practices, ISACA Journal, Volume 1, 2018
8: IT Risk Management Best Practices, ISACA Now Blog, January 9, 2018
The MOST effective way to increase the likelihood that risk responses will be implemented is to:
create an action plan
assign ownership
review progress reports
perform regular audits.
Risk responses are the actions or strategies that are taken to address the risks that may affect the organization’s objectives, performance, or value creation12.
The most effective way to increase the likelihood that risk responses will be implemented is to assign ownership, which is the process of identifying and appointing the individuals or groups who are responsible and accountable for the execution and monitoring of the risk responses34.
Assigning ownership is the most effective way because it ensures the clarity and commitment of the roles and responsibilities for the risk responses, and avoids the confusion or ambiguity that may arise from the lack of ownership34.
Assigning ownership is also the most effective way because it enhances the communication and collaboration among the stakeholders involved in the risk responses, and provides the feedback and input that are necessary for the improvement and optimization of the risk responses34.
The other options are not the most effective way, but rather possible steps or tools that may support or complement the assignment of ownership. For example:
Creating an action plan is a step that involves defining and documenting the specific tasks, resources, timelines, and deliverables for the risk responses34. However, this step is not the most effective way because it does not guarantee the implementation of the risk responses, especially if there is no clear or agreed ownership for the action plan34.
Reviewing progress reports is a tool that involves collecting and analyzing the information and data on the status and performance of the risk responses, and identifying the issues or gaps that need to be addressed34. However, this tool is not the most effective way because it does not ensure the implementation of the risk responses, especially if there is no ownership for the progress reports or the corrective actions34.
Performing regular audits is a tool that involves conducting an independent and objective assessment of the adequacy and effectiveness of the risk responses, and providing the findings and recommendations for improvement56. However, this tool is not the most effective way because it does not ensure the implementation of the risk responses,especially if there is no ownership for the audit results or the follow-up actions56. References =
1: Risk IT Framework, ISACA, 2009
2: IT Risk Management Framework, University of Toronto, 2017
3: Risk Response Plan in Project Management: Key Strategies & Tips1
4: ProjectManagement.com - How to Implement Risk Responses2
5: IT Audit and Assurance Standards, ISACA, 2014
6: IT Audit and Assurance Guidelines, ISACA, 2014
The PRIMARY objective for selecting risk response options is to:
reduce risk 10 an acceptable level.
identify compensating controls.
minimize residual risk.
reduce risk factors.
The primary objective for selecting risk response options is to reduce risk to an acceptable level. Risk response options are the possible actions that can be taken to address the risks that have been identified and analyzed in the risk management process. Risk response options can be classified into four categories: avoid, transfer, mitigate, and accept for negative risks (or threats), and exploit, share, enhance, and accept for positive risks (or opportunities). The selection of the risk response options depends on various factors, such as the risk level, the risk appetite and tolerance, the cost and benefit, and the feasibility and availability of the options. The main goal of selecting the risk response options is to reduce the risk to a level that is acceptable to the organization, which means that the risk exposure is within the boundaries of the risk criteria and the risk appetite. The other options are not the primary objective for selecting risk response options, although they may be related or beneficial. Identifying compensating controls is a technique to implement additional or alternative controls when the existing controls are not effective or sufficient to reduce the risk to an acceptable level. Minimizing residual risk is a result of selecting and implementing the risk response options, but it is not the main purpose. Residual risk is the risk that remains after the risk response, and it may or may not be acceptable depending on the risk appetite and tolerance. Reducing risk factors is a method to decrease the likelihood or impact of the risk by addressing the root causes or sources of the risk. However, reducing risk factors does not necessarily mean that the risk is reduced to an acceptable level,as there may be other factors or uncertainties that affect the risk. References = CRISC Review Manual, pages 32-331; CRISC Review Questions, Answers & Explanations Manual, page 862
A systems interruption has been traced to a personal USB device plugged into the corporate network by an IT employee who bypassed internal control procedures. Of the following, who should be accountable?
Business continuity manager (BCM)
Human resources manager (HRM)
Chief risk officer (CRO)
Chief information officer (CIO)
A systems interruption caused by a personal USB device plugged into the corporate network by an IT employee who bypassed internal control procedures is a serious breach of information security and IT risk management. The person who should be accountable for this incident is the chief information officer (CIO), who is responsible for overseeing the IT function and ensuring compliance with IT policies and standards. The CIO should also ensure that appropriate corrective and preventive actions are taken to prevent such incidents from recurring and to mitigate the impact of the systems interruption on the business operations and objectives. The CIO should also report the incident to the senior management and the board of directors, and communicate with the relevant stakeholders about the incident and the actions taken. References = Risk IT Framework, ISACA, 2022, p. 181
Which of the following is MOST important to understand when determining an appropriate risk assessment approach?
Complexity of the IT infrastructure
Value of information assets
Management culture
Threats and vulnerabilities
When determining an appropriate risk assessment approach, the most important factor to understand is the value of information assets. This is because the value of information assets determines the potential impact of risks and the level of protection required. The value of information assets can be assessed based on their confidentiality, integrity, availability, and relevance to the business objectives and processes. A risk assessment approach should be aligned with the value of information assets and the risk appetite of the organization. The other options are not the most important factors to understand when determining a risk assessment approach, although they may influence the choice of methods and tools. The complexity of the IT infrastructure may affect the scope and depth of the risk assessment, but it does not indicate the level of risk or the priority of risk management. The management culture may affect the risk tolerance and the risk communication, but it does not reflect the value of information assets or the risk exposure. The threats and vulnerabilities may affect the likelihood and severity of risks, but they do not measure the value of information assets or the risk acceptance. References = CRISC Review Manual, pages 38-391; CRISC Review Questions, Answers & Explanations Manual, page 582
When using a third party to perform penetration testing, which of the following is the MOST important control to minimize operational impact?
Perform a background check on the vendor.
Require the vendor to sign a nondisclosure agreement.
Require the vendor to have liability insurance.
Clearly define the project scope
When using a third party to perform penetration testing, the most important control to minimize operational impact is to clearly define the project scope. This means specifying the objectives, boundaries, methods, and deliverables of the testing, as well as the roles and responsibilities of the parties involved. A clear project scope helps to avoid misunderstandings, conflicts, and disruptions that could compromise the security, availability, or integrity of the systems under test. It also helps to ensure that the testing is aligned with the organization’s risk appetite and compliance requirements. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 3, Section 3.2.3.2, Page 137.
Which of the following tools is MOST effective in identifying trends in the IT risk profile?
Risk self-assessment
Risk register
Risk dashboard
Risk map
A risk dashboard is a graphical tool that displays the key indicators and metrics of the organization’s IT risk profile, such as the risk level, status, trend, performance, etc., using charts, graphs, tables, etc. A risk dashboard can help the organization to monitor and communicate the IT risk profile, and to support the decision making and planning for the IT risk management.
A risk dashboard is the most effective tool in identifying trends in the IT risk profile, because it provides a visual and intuitive representation of the changes and variations in the IT risk profile over time, and highlights the most significant and relevant IT risks that need to be addressed or monitored. A risk dashboard can also help to compare and contrast the IT risk profile with the organization’s IT objectives and risk appetite, and to identify the gaps or opportunities for improvement.
The other options are not the most effective tools in identifying trends in the IT risk profile, because they do not provide the same level of visibility and clarity that a risk dashboard provides, and they may not be updated or aligned with the organization’s IT objectives and risk appetite.
A risk self-assessment is a process of identifying, analyzing, and evaluating the IT risks that may affect the organization’s objectives and operations, using the input and feedback from the individuals or groups that are involved or responsible for the IT activities or functions. A risk self-assessment can help the organization to understand and document the IT risk profile, and to align it with the organization’s IT strategy and culture, but it is not the most effective tool in identifying trends in the IT risk profile, because it may not reflect the current or accurate state and performance of the IT risk profile, and it may not cover all the relevant or emerging IT risks that may exist or arise.
A risk register is a document that records and tracks the information and status of the identified IT risks and their responses. It includes the IT risk description, category, source, cause, impact, probability, priority, response, owner, action plan, status, etc. A risk register can help the organization to identify, analyze, evaluate, and communicate the IT risks and their responses, and to align them with the organization’s IT strategy and culture, but it is not the most effective tool in identifying trends in the IT risk profile, because it may not provide a visual and intuitive representation of the changes and variations in the IT risk profile over time, and it may not highlight the most significant and relevant IT risks that need to be addressed or monitored.
A risk map is a graphical tool that displays the results of the IT risk analysis in a matrix format, using colors and symbols to indicate the level and priority of the IT risks. A risk map can show the distribution and comparison of the IT risks based on various criteria, such as likelihood, impact, category, source, etc. A risk map can help the organization to assess and prioritize the IT risks, and to design and implement appropriate controls or countermeasures to mitigate or prevent the IT risks, but it is not the most effective tool in identifying trends in the IT risk profile, because it may not provide a visual and intuitive representation of the changes and variations in the IT risk profile over time, and it may not reflect the organization’s IT objectives and risk appetite. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 19-20, 23-24, 27-28, 31-32, 40-41, 47-48, 54-55, 58-59, 62-63
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 180
CRISC Practice Quiz and Exam Prep
During which phase of the system development life cycle (SDLC) should information security requirements for the implementation of a new IT system be defined?
Monitoring
Development
Implementation
Initiation
Detailed Explanation:Information security requirements should be defined during theInitiationphase of the SDLC. This ensures that security is integrated into the design from the beginning, minimizing vulnerabilities and aligning security measures with business requirements. Early identification of security needs reduces rework and costs associated with later stages.
A web-based service provider with a low risk appetite for system outages is reviewing its current risk profile for online security. Which of the following observations would be MOST relevant to escalate to senior management?
An increase in attempted distributed denial of service (DDoS) attacks
An increase in attempted website phishing attacks
A decrease in achievement of service level agreements (SLAs)
A decrease in remediated web security vulnerabilities
A web-based service provider is an organization that offers online services or applications to its customers or users, such as e-commerce, social media, cloud computing, etc. A web-based service provider depends on the availability, reliability, and security of its web servers, networks, and systems to deliver its services or applications.
A low risk appetite for system outages means that the organization is not willing to accept a high level or frequency of system outages, which are interruptions or disruptions in the normal operation or functionality of the web servers, networks, or systems. System outages can cause customer dissatisfaction, revenue loss, reputation damage, or legal liability for the web-based service provider.
A current risk profile for online security is the current state or condition of the online security risks that may affect the web-based service provider’s objectives and operations. It includes the identification, analysis, and evaluation of the online security risks, and the prioritization and response to them based on their significance and urgency.
The most relevant observation to escalate to senior management is an increase in attempted distributed denial of service (DDoS) attacks, which are malicious attacks that aim to overwhelm or overload the web servers, networks, or systems with a large volume or frequency of requests or traffic, and prevent them from responding to legitimate requests or traffic. An increase in attempted DDoS attacks indicates a high likelihood and impact of system outages, and a high level of threat or vulnerability for the web-based service provider’s online security. Escalating this observation to senior management can help them to understand the severity and urgency of the risk, and to decide on the appropriate risk response and allocation of resources.
The other options are not the most relevant observations to escalate to senior management, because they do not indicate a high likelihood or impact of system outages, and they may not be relevant or actionable for senior management.
An increase in attempted website phishing attacks means an increase in malicious attempts to deceive or trick the web-based service provider’s customers or users into providing their personal or financial information, such as usernames, passwords, credit card numbers, etc., by impersonating the web-based service provider’s website or email. An increase in attempted website phishing attacks indicates a high level of threat or vulnerability for the web-based service provider’s online security, but it may not directly cause system outages, unless the phishing attacks are used to compromise the web servers, networks, or systems. Escalating this observation to senior management may not be the most relevant, because it may not reflect the web-based service provider’s risk appetite for system outages, and it may not require senior management’s involvement or approval.
A decrease in achievement of service level agreements (SLAs) means a decrease in the extent or degree to which the web-based service provider meets or exceeds the agreed or expected standards or criteria for the quality, performance, or availability of its services or applications, as specified in the contracts or agreements with its customers or users. A decrease in achievement of SLAs indicates a low level of customer satisfaction, retention, or loyalty, and a low level of competitiveness or profitability for the web-based service provider. Escalating this observation to senior management may not be the most relevant, because it may not reflect the web-based service provider’s risk appetite for system outages, and it may not require senior management’s involvement or approval.
A decrease in remediated web security vulnerabilities means a decrease in the number or percentage of web security vulnerabilities that have been identified and resolved or mitigated by the web-based service provider. Web security vulnerabilities are weaknesses or flaws in the web servers, networks, or systems that can be exploited by malicious attackers to compromise or damage the web-based service provider’s online security. A decrease in remediated web security vulnerabilities indicates a low level of effectiveness or efficiency for the web-based service provider’s web security controls or processes. Escalating this observation to senior management may not be the most relevant, because it may not reflect the web-based service provider’s risk appetite for system outages, and it may not require senior management’s involvement or approval. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 19-20, 23-24, 27-28, 31-32, 40-41, 47-48, 54-55, 58-59, 62-63
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 161
CRISC Practice Quiz and Exam Prep
Which of the following aspects of an IT risk and control self-assessment would be MOST important to include in a report to senior management?
Changes in control design
A decrease in the number of key controls
Changes in control ownership
An increase in residual risk
An IT risk and control self-assessment (RCSA) is a process that helps organizations identify and evaluate operational risks and assess the effectiveness of their control measures12. It is a structured approach that involves identifying, assessing, mitigating, and monitoring risks across all levels of an organization12.
A report to senior management is a document that summarizes and communicates the results and findings of the RCSA, and provides recommendations and action plans for improving the risk management and control processes34.
The most important aspect of an IT risk and control self-assessment to include in a report to senior management is an increase in residual risk, which is the risk remaining after risk treatment, and represents the exposure or potential impact of the risk on the organization’s objectives56.
An increase in residual risk is the most important aspect because it indicates the level of risk that the organization is willing to accept or tolerate, and the gap between the current and desired risk profile56.
An increase in residual risk is also the most important aspect because it requires the attention and decision of the senior management, who are responsible for defining the organization’s risk appetite, strategy, and criteria, and for ensuring that the residual risk is within the acceptable range56.
The other options are not the most important aspects, but rather possible components or outcomes of an IT risk and control self-assessment that may support or complement the report to senior management. For example:
Changes in control design are components of an IT risk and control self-assessment that involve modifying or updating the control measures to address the changes in the risk environment or the organization’s objectives56. However, changes in control design are not the most important aspect because they do not measure or reflect the residual risk, which is the ultimate goal of the risk treatment56.
A decrease in the number of key controls is an outcome of an IT risk and control self-assessment that indicates the improvement or optimization of the control processes, and the reduction of the complexity or redundancy of the control measures56. However, a decrease in the number of key controls is not the most important aspect because it does not indicate or imply the residual risk, which may depend on other factors such as the effectiveness or efficiency of the controls56.
Changes in control ownership are components of an IT risk and control self-assessment that involve assigning or reassigning the responsibility and accountability for the control processes to the appropriate individuals or groups within the organization56. However,changes in control ownership are not the most important aspect because they do not affect or determine the residual risk, which is independent of the control owners56. References =
1: Risk and control self-assessment - KPMG Global1
2: Control Self Assessments - PwC2
3: How-To Guide: Implementing Risk Control Self-Assessment Steps4
4: RISK MANAGEMENT SELF-ASSESSMENT TEMPLATE - Smartsheet5
5: Risk IT Framework, ISACA, 2009
6: IT Risk Management Framework, University of Toronto, 2017
A risk practitioner is summarizing the results of a high-profile risk assessment sponsored by senior management. The BEST way to support risk-based decisions by senior management would be to:
map findings to objectives.
provide quantified detailed analysis
recommend risk tolerance thresholds.
quantify key risk indicators (KRls).
The best way to support risk-based decisions by senior management would be to map findings to objectives, because this would help them understand how the identified risks affect the achievement of the organization’s goals and priorities. Mapping findings to objectives would also help senior management evaluate the trade-offs between different risk responses and allocate resources accordingly. By linking risks to objectives, the risk practitioner can communicate the value and impact of risk management in a clear and relevant way. References = Risk IT Framework, ISACA, 2022, p. 17
During the risk assessment of an organization that processes credit cards, a number of existing controls have been found to be ineffective and do not meet industry standards. The overall control environment may still be effective if:
compensating controls are in place.
a control mitigation plan is in place.
risk management is effective.
residual risk is accepted.
Compensating controls are additional or alternative controls that are implemented when the existing controls are found to be ineffective or do not meet the required standards. Compensating controls are designed to reduce the risk exposure to an acceptable level and ensure that the organization can still comply with the relevant regulations and industry best practices. For an organization that processes credit cards, compensating controls may include enhanced encryption, monitoring, auditing, or authentication mechanisms. By having compensating controls in place, the organization can maintain an effective overall control environment despite the deficiencies in the existing controls. The other options are not correct because they do not ensure that the overall control environment is effective. A control mitigation plan is a document that outlines the actions and resources needed to address the control deficiencies, but it does not guarantee that the compensating controls will be implemented or effective. Risk management is a process that involves identifying, analyzing, evaluating, and treating risks, but it does not directly affect the control environment. Residual risk is the risk that remains after the risk treatment, and it may or may not be acceptable depending on the risk appetite of the organization. References = CRISC Review Manual, pages 153-1541; CRISC Review Questions, Answers & Explanations Manual, page 632
Which of the following roles would provide the MOST important input when identifying IT risk scenarios?
Information security managers
Internal auditors
Business process owners
Operational risk managers
Business process owners would provide the most important input when identifying IT risk scenarios. IT risk scenarios are the situations or events that may affect the organization’s objectives, operations, or performance due to the use of information and technology1. Identifying IT risk scenarios means finding,recognizing, and describing the IT risks that the organization faces, as well as their sources, drivers, consequences, and responses2. Business process owners are the persons or entities who are responsible for the design, implementation, and operation of the business processes that support the organization’s goals and values3. Business process owners would provide the most important input when identifying IT risk scenarios, because they can:
Provide the context and perspective of the business objectives, strategies, and requirements that are affected or supported by the IT risks and controls;
Identify and prioritize the IT risks that are relevant and significant to their business processes, as well as the IT assets and resources that are involved or impacted by the IT risks;
Evaluate and communicate the likelihood and impact of the IT risks on their business processes, as well as the risk appetite and tolerance of their business units;
Suggest and implement the most suitable and effective IT risk response actions or measures to mitigate the IT risks, as well as monitor and report on the IT risk and control performance;
Align and integrate the IT risk management activities and outcomes with the business risk management framework, policies, and standards. The other options are not the most important roles for providing input when identifying IT risk scenarios, as they are either less relevant or less specific than business process owners. Information security managers are the persons or entities who are responsible for the planning, implementation, and maintenance of the information security measures and controls that protect the confidentiality, integrity, and availability of the organization’s data and systems4. Information security managers can provide input when identifying IT risk scenarios, because they can:
Provide the expertise and guidance on the information security risks and controls that are related to the use of information and technology;
Identify and assess the information security vulnerabilities and threats that may affect the organization’s data and systems, as well as the information security assets and resources that are involved or impacted by the information security risks;
Recommend and implement the most appropriate and effective information security risk response actions or measures to reduce or eliminate the information security risks, as well as monitor and report on the information security risk and control performance;
Align and integrate the information security risk management activities and outcomes with the information security framework, policies, and standards. However, information security managers are not the most important roles for providing input when identifying IT risk scenarios, because they may not have the full understanding or visibility of the business objectives, strategies, and requirements that are affected or supported by the IT risks and controls, or the risk appetite and tolerance of the business units. Internal auditors are the persons or entities who are responsible for theindependent and objective assurance and consulting on the effectiveness and efficiency of the organization’s governance, risk management, and internal control system5. Internal auditors can provide input when identifying IT risk scenarios, because they can:
Provide the assurance and validation on the design and operation of the IT risks and controls that are related to the use of information and technology;
Identify and evaluate the IT risk and control gaps or deficiencies that may affect the organization’s objectives, operations, or performance, as well as the IT risk and control objectives and activities that are involved or impacted by the IT risk and control gaps or deficiencies;
Report and recommend improvements or enhancements to the IT risks and controls, as well as follow up and verify the implementation and effectiveness of the IT risk and control improvements or enhancements;
Align and integrate the IT risk and control assurance and consulting activities and outcomes with the internal audit framework, policies, and standards. However, internal auditors are not the most important roles for providing input when identifying IT risk scenarios, because they may not have the authority or responsibility to implement or operate the IT risks and controls, or to decide or prioritize the IT risk response actions or measures. Operational risk managers are the persons or entities who are responsible for the identification, analysis, evaluation, and treatment of the risks that arise from the failures or inadequacies of the organization’s people, processes, systems, or external events6. Operational risk managers can provide input when identifying IT risk scenarios, because they can:
Provide the oversight and coordination of the operational risk management activities and performance across the organization, including the IT risks and controls that are related to the use of information and technology;
Identify and prioritize the operational risks that are relevant and significant to the organization, as well as the operational assets and resources that are involved or impacted by the operational risks;
Evaluate and communicate the likelihood and impact of the operational risks on the organization, as well as the risk appetite and tolerance of the organization;
Suggest and implement the most suitable and effective operational risk response actions or measures to mitigate the operational risks, as well as monitor and report on the operational risk and control performance;
Align and integrate the operational risk management activities and outcomes with the operational risk management framework, policies, and standards. However, operational risk managers are not the most important roles for providing input when identifying IT risk scenarios, because they may not have the specific knowledge or expertise on the IT risks and controls that are related to the use of information and technology, or the context and perspective of the business processes that are affected or supported by the IT risks and controls. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 3, Section 3.1.1, Page 85.
Which of the following is the BEST metric to demonstrate the effectiveness of an organization's change management process?
Increase in the frequency of changes
Percent of unauthorized changes
Increase in the number of emergency changes
Average time to complete changes
A change management process is a set of procedures and activities that aim to ensure that changes in an organization’s IT systems and services are implemented in a controlled and coordinated manner. The effectiveness of a change management process can be measured by how well it reduces the risks and costs associated with changes, and how well it supports the business objectives and customer expectations. One of the best metrics to demonstrate the effectiveness of a change management process is the percent of unauthorized changes. Unauthorized changes are changes that are made without following the established change management process, such as obtaining approval, documenting the change, testing the change, and communicating the change. Unauthorized changes can introduce errors, defects, security breaches, and disruptions to the IT systems and services, and can negatively affect the business performance and customer satisfaction. Therefore, a low percent of unauthorized changes indicates that the change management process is effective in ensuring that changes are properly planned, approved, executed, and monitored. The other options are not the best metrics to demonstrate the effectiveness of a change management process, as they do not directly reflect the quality and control of the changes. An increase in the frequency of changes may indicate that the organization is agile and responsive to the changing business needs and customer demands, but it does not necessarily mean that the changes are well-managed and beneficial. An increase in the number of emergency changes may indicate that the organization is able to handle urgent and critical situations, but it may also suggest that the organization is reactive and lacks proper planning and analysis of the changes. The average time to complete changes may indicate the efficiency and speed of the change management process, but it does not measure the effectiveness and value of the changes. References = CRISC Review Manual, pages 156-1571; CRISC Review Questions, Answers & Explanations Manual, page 712
Which of the following would be- MOST helpful to understand the impact of a new technology system on an organization's current risk profile?
Hire consultants specializing m the new technology.
Review existing risk mitigation controls.
Conduct a gap analysis.
Perform a risk assessment.
A risk assessment is a process of measuring and comparing the likelihood and impact of various risk scenarios, and prioritizing them based on their significance and urgency. A risk assessment can help the organization to understand and document the risks that may affect its objectives and operations, and to support the decision making and planning for the risk management.
Performing a risk assessment would be the most helpful to understand the impact of a new technology system on an organization’s current risk profile, because it can help the organization to address the following questions:
What are the potential benefits and challenges of implementing the new technology system, and how do they align with the organization’s objectives and needs?
What are the existing or emerging risks that may affect the new technology system, and how do they relate to the organization’s current risk profile?
How likely and severe are the risks that may affect the new technology system, and what are the possible consequences or impacts for the organization and its stakeholders?
How can the risks that may affect the new technology system be mitigated or prevented, and what are the available or feasible options or solutions?
Performing a risk assessment can help the organization to understand the impact of the new technology system on its current risk profile by providing the following benefits:
It can enable the comparison and evaluation of the current and desired state and performance of the organization’s risk management function, and to identify and quantify the gaps or opportunities for improvement.
It can provide useful references and benchmarks for the alignment and integration of the new technology system with the organization’s risk management function, and for the compliance with the organization’s risk policies and standards.
It can support the implementation and monitoring of the new technology system, and for the allocation and optimization of the resources, time, and budget for the new technology system.
The other options are not the most helpful to understand the impact of a new technology system on an organization’s current risk profile, because they do not provide the same level of detail and insight that performing a risk assessment provides, and they may not be specific or applicable to the organization’s objectives and needs.
Hiring consultants specializing in the new technology means engaging or contracting external experts or professionals that have the skills and knowledge on the new technology system, and that can provide advice or guidance on the implementation and management of the new technology system. Hiring consultants specializing in the new technology can help the organization to enhance its competence and performance on the new technology system, but it is not the most helpful, because it does not measure and compare the likelihood and impact of the risks that may affect the new technology system, and it may not be relevant or appropriate for the organization’s current risk profile.
Reviewing existing risk mitigation controls means examining and evaluating the adequacy and effectiveness of the controls or countermeasures that are intended to reduce or eliminate the risks that may affect the organization’s objectives and operations. Reviewing existing risk mitigation controls can help the organization to improve and optimize its risk management function, but it is not the most helpful, because it does not identify and prioritize the risks that may affect the new technology system, and it may not cover all the relevant or significant risks that may affect the new technology system.
Conducting a gap analysis means comparing and contrasting the current and desired state and performance of the organization’s objectives and operations, and identifying and quantifying the gaps or differences that need to be addressed or corrected. Conducting a gap analysis can help the organization to identify and document its improvement needs and opportunities, but it is not the most helpful, because it does not measure and compare the likelihood and impact of the risks that may affect the new technology system, and it may not be aligned or integrated with the organization’s current risk profile. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 19-20, 23-24, 27-28, 31-32, 40-41, 47-48, 54-55, 58-59, 62-63
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 208
CRISC Practice Quiz and Exam Prep
In addition to the risk register, what should a risk practitioner review to develop an understanding of the organization's risk profile?
The control catalog
The asset profile
Business objectives
Key risk indicators (KRls)
In addition to the risk register, which is a tool to document and monitor the risks that affect the organization, a risk practitioner should review the business objectives of the organization to develop an understanding of its risk profile. The risk profile is a description of the set of risks that the organization faces in relation to its goals and strategies. By reviewing the business objectives, the risk practitioner can identify the sources, drivers, and consequences of the risks, as well as the alignment, prioritization, and tolerance of the risks. The business objectives also provide the context and criteria for evaluating and managing the risks. The other options are not the best choices to review for developing an understandingof the organization’s risk profile, as they do not capture the full scope and nature of the risks. The control catalog is a list of the existing controls that are implemented to mitigate the risks, but it does not reflect the effectiveness, efficiency, or sufficiency of the controls. The asset profile is a description of the resources and capabilities that the organization possesses or relies on, but it does not indicate the value, vulnerability, or interdependency of the assets. The key risk indicators (KRIs) are metrics that measure the level and trend of the risks, but they do not explain the causes, impacts, or responses to the risks. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.1.2, Page 49.
During an IT risk scenario review session, business executives question why they have been assigned ownership of IT-related risk scenarios. They feel IT risk is technical in nature and therefore should be owned by IT. Which of the following is the BEST way for the risk practitioner to address these concerns?
Describe IT risk scenarios in terms of business risk.
Recommend the formation of an executive risk council to oversee IT risk.
Provide an estimate of IT system downtime if IT risk materializes.
Educate business executives on IT risk concepts.
IT risk scenarios are hypothetical situations or occurrences that illustrate the potential impact of IT-related threats or opportunities on the organization’s objectives, performance, or value creation12.
Business risk scenarios are hypothetical situations or occurrences that illustrate the potential impact of business-related threats or opportunities on the organization’s objectives, performance, or value creation34.
The best way for the risk practitioner to address the concerns of the business executives who question why they have been assigned ownership of IT-related risk scenarios is to describe IT risk scenarios in terms of business risk, which is a technique that involves translating and communicating the IT risk scenarios into the language and context of the business risk scenarios, and highlighting the linkages and dependencies between them56.
Describing IT risk scenarios in terms of business risk is the best way because it helps the business executives to understand and appreciate the relevance and importance of IT risk scenarios, andhow they affect the achievement of the organization’s goals and the delivery of value to the stakeholders56.
Describing IT risk scenarios in terms of business risk is also the best way because it helps the business executives to accept and fulfill their roles and responsibilities as the owners of IT risk scenarios, and to collaborate and coordinate with the IT team and other stakeholders in the risk management process56.
The other options are not the best ways, but rather possible alternatives or supplements that may support or enhance the description of IT risk scenarios in terms of business risk. For example:
Recommending the formation of an executive risk council to oversee IT risk is a way that involves establishing and empowering a group of senior leaders from different business units and functions to provide the strategic direction, guidance, and oversight for the IT risk management process78. However, this way is not the best way because it does not directlyaddress the concerns of the business executives who question why they have been assigned ownership of IT risk scenarios, and it may not be feasible or effective without a clear and common understanding of IT risk scenarios among the council members78.
Providing an estimate of IT system downtime if IT risk materializes is a way that involves quantifying and communicating the potential loss or disruption of the IT systems or services that support the organization’s operations, if the IT risk scenarios occur9 . However, this way is not the best way because it does not fully capture or convey the impact of IT risk scenarios on the organization’s objectives, performance, or valuecreation, and it may not be relevant or meaningful for some IT risk scenarios that are not related to IT system downtime9 .
Educating business executives on IT risk concepts is a way that involves providing and delivering the knowledge and skills on the principles, frameworks, and techniques of IT risk management, and the roles and responsibilities of the IT risk owners and stakeholders . However, this way is not the best way because it does not specifically address the concerns of the business executives who question why they have been assigned ownership of IT risk scenarios, and it may not be sufficient or effective without a practical and contextual application of IT risk concepts to the organization’s situation and goals . References =
1: IT Scenario Analysis in Enterprise Risk Management - ISACA2
2: New Toolkit and Course From ISACA Help Practitioners Develop Risk Scenarios - ISACA1
3: Business Risk - Investopedia3
4: Business Risk: Definition, Types, Examples & How to Manage4
5: Risk IT Framework, ISACA, 2009
6: IT Risk Management Framework, University of Toronto, 2017
7: Executive Risk Council - ISACA5
8: Executive Risk Council: A Guide to Success6
9: IT System Downtime - ISACA7
IT System Downtime: Causes, Costs, and How to Prevent It8
IT Risk Education - ISACA9
IT Risk Education: A Guide to Success
Which of the following attributes of a key risk indicator (KRI) is MOST important?
Repeatable
Automated
Quantitative
Qualitative
A key risk indicator (KRI) is a metric that helps organizations monitor and assess potential risks that may impact their operations, objectives, or performance. A good KRI should have certain characteristics that make it effective for risk management. One of these characteristics is repeatability, which means that the KRI can be measured consistently over time and across different situations. A repeatable KRI ensures that the risk data is reliable, comparable, and meaningful, and that the risk trends and patterns can be identified and analyzed. A repeatable KRI also supports the decision-making process by providing timely and accurate information on the risk level and status. Therefore, repeatability is the most important attribute of a KRI. References = Risk IT Framework, ISACA, 2022, p. 441
Which of the following is the BEST method for assessing control effectiveness?
Ad hoc control reporting
Control self-assessment
Continuous monitoring
Predictive analytics
Control effectiveness is the degree to which a control achieves its intended objective and mitigates the risk that it is designed to address. It is measured by comparing the actual performance and outcome of the control with the expected or desired performance and outcome.
The best method for assessing control effectiveness is continuous monitoring, which is the process of collecting, analyzing, and reporting on the performance and outcome of the controls on an ongoing basis. Continuous monitoring provides timely and accurate information on the status and results of the controls, and enables the identification and correction of any issues or gaps in the control environment.
Continuous monitoring can be performed using various techniques, such as automated tools, dashboards, indicators, metrics, logs, audits, reviews, etc. Continuous monitoring can also be integrated with the risk management process, and aligned with the organization’s objectives and risk appetite.
The other options are not the best methods for assessing control effectiveness, because they do not provide the same level of timeliness, accuracy, and completeness of information on the performance and outcome of the controls.
Ad hoc control reporting is the process of collecting, analyzing, and reporting on the performance and outcome of the controls on an irregular or occasional basis. Ad hoc control reporting may be triggered by specific events, requests, or incidents, and it may not cover all the relevant or critical controls. Ad hoc control reporting may not provide sufficient or consistent information on the control effectiveness, and it may not enable the timely and proactive identification and correction of any issues or gaps in the control environment.
Control self-assessment is the process of allowing the control owners or operators to evaluate and report on the performance and outcome of their own controls. Control self-assessment can provide useful insights and feedback from the control owners or operators, and it can enhance their awareness and accountability for the control effectiveness. However, control self-assessment may not be objective, reliable, or independent, and it may not cover all the relevant or critical controls. Control self-assessment may not provide sufficient or consistent information on the control effectiveness, and it may not enable the timely and proactive identification and correction of any issues or gaps in the control environment.
Predictive analytics is the process of using statistical techniques and models to analyze historical and current data, and to make predictions or forecasts about future events or outcomes. Predictive analytics can provide useful insights and trends on the potential performance and outcome of the controls, and it can support the decision making and planning for the control effectiveness. However, predictive analytics may not be accurate, valid, or reliable, and it may not reflect the actual or current performance and outcome of the controls. Predictive analytics may not provide sufficient or consistent information on the control effectiveness, and it may not enable the timely and proactive identification and correction of any issues or gaps in the control environment. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 40-41, 47-48, 54-55, 58-59, 62-63
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 150
CRISC Practice Quiz and Exam Prep
Which of the following would BEST help to ensure that suspicious network activity is identified?
Analyzing intrusion detection system (IDS) logs
Analyzing server logs
Using a third-party monitoring provider
Coordinating events with appropriate agencies
An intrusion detection system (IDS) is a network security tool that monitors and analyzes network traffic for signs of malicious or suspicious activity, such as unauthorized access, data exfiltration, malware infection, or denial-of-service attack. An IDS can detect and alert the organization to potential threats based on predefined rules or signatures, or based on anomalies or deviations from normal network behavior. An IDS can also generate logs that record the details of the network events and incidents, such as the source, destination, content, and context of the network traffic. By analyzing the IDS logs, the organization can identify and validate the suspicious network activity, and determine its scope, impact, and root cause. The organization can also use the IDS logs to support the incident response and remediation process, and to improve the network security and resilience. The other options are less effective ways to ensure that suspicious network activity is identified. Analyzing server logs can provide some information about the network activity, but it may not be sufficient or timely to detect and validate the suspicious or malicious activity, as server logs only capture the events or activities that occur on the server, and not on the entire network. Using a third-party monitoring provider can help to outsource the network monitoring and analysis function, but it may not be the best option, as it may introduce additional risks, such as data privacy, vendor reliability, or service quality issues. Coordinating events with appropriate agencies can help to share information and resources with other organizations or authorities, such as law enforcement, regulators, or industry peers, but it may not be the best option, as it may depend on the availability and cooperation of theagencies, and it may not be feasible or desirable to disclose the network activity to external parties. References = Monitoring for Suspicious Network Activity: Key Tips to Secure Your Network 1
Reviewing results from which of the following is the BEST way to identify information systems control deficiencies?
Vulnerability and threat analysis
Control remediation planning
User acceptance testing (UAT)
Control self-assessment (CSA)
Information systems control deficiencies are the weaknesses or flaws in the design or implementation of the controls that are intended to ensure the confidentiality, integrity, availability, and reliability of the information systems and resources. Information systems control deficiencies may reduce the effectiveness or efficiency of the controls, and expose the organization to various risks, such as unauthorized access, data loss, system failure, etc.
Reviewing results from control self-assessment (CSA) is the best way to identify information systems control deficiencies, because CSA is a process of evaluating and verifying the adequacy and effectiveness of the information systems controls, using the input and feedback from the individuals or groups that are involved or responsible for the information systems activities or functions. CSA can help the organization to identify and document the information systems control deficiencies, and to align them with the organization’s information systems objectives and requirements.
CSA can be performed using various techniques, such as questionnaires, surveys, interviews, workshops, etc. CSA can also be integrated with the organization’s governance, risk management, and compliance functions, and aligned with the organization’s policies and standards.
The other options are not the best ways to identify information systems control deficiencies, because they do not provide the same level of detail and insight that CSA provides, and they may not be relevant or actionable for the organization.
Vulnerability and threat analysis is a process of identifying and evaluating the weaknesses or flaws in the organization’s assets, processes, or systems that can be exploited or compromised by the potential threats or sources of harm that may affect the organization’s objectives or operations. Vulnerability and threat analysis can help the organization to assess and prioritize the risks, and to design and implement appropriate controls or countermeasures to mitigate or prevent the risks, but it is not the best way to identify information systems control deficiencies, because it does not indicate whether the existing information systems controls are adequate and effective, and whether they comply with the organization’s policies and standards.
Control remediation planning is a process of selecting and implementing the actions or plans to address or correct the information systems control deficiencies that have been identified, analyzed, and evaluated. Control remediation planning involves choosing one ofthe following types of control responses: mitigate, transfer, avoid, or accept. Control remediation planning can help the organization to improve and optimize the information systems controls, and to reduce or eliminate the information systems control deficiencies, but it is not the best way to identify information systems control deficiencies, because it is a subsequent or follow-up process that depends on the prior identification of the information systems control deficiencies.
User acceptance testing (UAT) is a process of verifying and validating the functionality and usability of the information systems and resources, using the input and feedback from the end users or customers that interact with the information systems and resources. UAT can help the organization to ensure that the information systems and resources meet the user or customer expectations and requirements, and to identify and resolve any issues or defects that may affect the user or customer satisfaction, but it is not the best way to identify information systems control deficiencies, because it does not focus on the information systems controls, and it may not cover all the relevant or significant information systems control deficiencies that may exist or arise. References =
ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 40-41, 47-48, 54-55, 58-59, 62-63
ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 186
CRISC Practice Quiz and Exam Prep
The PRIMARY objective of testing the effectiveness of a new control before implementation is to:
ensure that risk is mitigated by the control.
measure efficiency of the control process.
confirm control alignment with business objectives.
comply with the organization's policy.
The primary objective of testing the effectiveness of a new control before implementation is to ensure that risk is mitigated by the control. A control is a measure or action that is taken to reduce the likelihood or impact of a risk, or to increase the likelihood or impact of an opportunity1. Testing the effectiveness of anew control before implementation means verifying whether the control can achieve its intended purpose and objective, and whether it can address the risk adequately and appropriately2. Testing the effectiveness of a new control before implementation helps to avoid wasting resources, time, and effort on implementing a control that is ineffective, inefficient, or unsuitable for the risk scenario. It also helps to ensure that the control does not introduce new or unintended risks, or adversely affect other controls or processes3. The other options are not the primary objective of testing the effectiveness of a new control before implementation, as they are either less relevant or less specific than ensuring that risk is mitigated by the control. Measuring efficiency of the control process is a secondary objective of testing the effectiveness of a new control before implementation. Efficiency refers to the optimal use of resources to achieve the desired outcome4. Measuring efficiency of the control process means evaluating whether the control can achieve its objective with the least amount of cost, time, and effort. Measuring efficiency of the control process helps to optimize the performance and value of the control, but it is not the main reason for testing the effectiveness of a new control before implementation. Confirming control alignment with business objectives is a tertiary objective of testing the effectiveness of a new control before implementation. Alignment refers to the consistency and coherence of the control with the goals and strategies of the organization5. Confirming control alignment with business objectives means ensuring that the control supports and enables the achievement of the organization’s mission, vision, and values. Confirming control alignment with business objectives helps to integrate the control with the organization’s culture and governance, but it is not the primary reason for testing the effectiveness of a new control before implementation. Complying with the organization’s policy is a quaternary objective of testing the effectiveness of a new control before implementation. Policy refers to the set of principles and rules that guide the organization’s decisions and actions6. Complying with the organization’s policy means adhering to the standards and requirements that the organization has established for implementing and operating controls. Complying with the organization’s policy helps to ensure the quality and consistency of the control, but it is not the main objective of testing the effectiveness of a new control before implementation. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.1.8, Page 61.
Which of the following is the GREATEST benefit of incorporating IT risk scenarios into the corporate risk register?
Corporate incident escalation protocols are established.
Exposure is integrated into the organization's risk profile.
Risk appetite cascades to business unit management
The organization-wide control budget is expanded.
IT risk scenarios are hypothetical situations that describe the sources, causes, and consequences of IT-related risks, and the potential impacts on the organization’s objectives, performance, and value creation12.
A corporate risk register is a document that records and tracks the significant risks that the organization faces, and the responses and actions that are taken to address them34.
The greatest benefit of incorporating IT risk scenarios into the corporate risk register is that exposure is integrated into the organization’s risk profile, which is a comprehensive and integrated representation of the risks that may affect the organization’s objectives, performance, and value creation56.
Exposure is integrated into the organization’s risk profile means that the organization has a complete and consistent view of the IT risk landscape, and the potential impacts andinterdependencies of IT risks on other types of risks, such as financial, operational, strategic, or reputational risks56.
Exposure is integrated into the organization’s risk profile also means that the organization can make informed and balanced decisions on the risk responses and actions, and allocate the appropriate resources and priorities to the IT risk management and control processes56.
The other options are not the greatest benefit, but rather possible outcomes or consequences of incorporating IT risk scenarios into the corporate risk register. For example:
Corporate incident escalation protocols are established is an outcome of incorporating IT risk scenarios into the corporate risk register that indicates the organization has defined and implemented the procedures and mechanisms for reporting and resolving IT-related incidents, and for escalating them to the appropriate authorities or levels when necessary78. However, this outcome does not measure or reflect the exposure or the risk profile of the organization, which may depend on other factors such as the frequency, severity, or complexity of the incidents78.
Risk appetite cascades to business unit management is a consequence of incorporating IT risk scenarios into the corporate risk register that indicates the organization has communicated and aligned the risk appetite, which is the amount and type of risk that the organization is willing to accept or pursue, to the business unit management, who are responsible for executing the risk strategy and objectives at the operational level . However, this consequence does not indicate or imply the exposure or the risk profile of the organization, which may vary depending on the context, environment, or stakeholder expectations .
The organization-wide control budget is expanded is an outcome of incorporating IT risk scenarios into the corporate risk register that indicates the organization has increased the amount of resources and funds that are allocated to the control processes, which are the procedures and activities that aim to ensure the effectiveness and efficiency of the organization’s operations, the reliability of its information, and the compliance with its policies and regulations . However, this outcome does not affect or determine the exposure or the risk profile of the organization, which is independent of the control budget . References =
1: IT Risk Scenarios - Morland-Austin3
2: Risk Scenarios Toolkit, ISACA, 2019
3: Risk Register Template and Examples | Prioritize and Manage Risk1
4: Risk Register Examples for Cybersecurity Leaders4
5: Risk IT Framework, ISACA, 2009
6: IT Risk Management Framework, University of Toronto, 2017
7: Security Incident Reporting and Response, University of Toronto, 2017
8: Security Incident Reporting and Response, ISACA, 2019
Risk Appetite: Linking Strategy, Risk and Performance, ISACA, 2012
Risk Appetite and Tolerance, ISACA Journal, Volume 4, 2013
The Control Process | Principles of Management2
Control Management: What it is + Why It’s Essential | Adobe Workfront5
Which of the following is MOST helpful when determining whether a system security control is effective?
Control standard operating procedures
Latest security assessment
Current security threat report
Updated risk register
Detailed Explanation:Thelatest security assessmentprovides a detailed evaluation of the control’s performance and identifies gaps or weaknesses. This is critical for determining the effectiveness of a system security control in mitigating threats.
Which of the following BEST describes the role of the IT risk profile in strategic IT-related decisions?
It compares performance levels of IT assets to value delivered.
It facilitates the alignment of strategic IT objectives to business objectives.
It provides input to business managers when preparing a business case for new IT projects.
It helps assess the effects of IT decisions on risk exposure
An IT risk profile is a document that summarizes the IT-related risks that an organization faces, as well as the information and actions related to those risks, such as the risk description, assessment, response, status, and owner. An IT risk profile is a valuable tool for managing and communicating IT risks and their impact on the organization’s objectives and operations. The best description of the role of the IT risk profile in strategic IT-related decisions is that it helps assess the effects of IT decisions on risk exposure. This means that the IT risk profile can help to evaluate the potential consequences and implications of different IT choices or actions on the level and nature of the IT risks that the organization faces. The IT risk profile can also help to identify and address the gaps or opportunities for improvement in the IT risk management process and performance. The other options are not the best descriptions of the role of the IT risk profile in strategic IT-related decisions, although they may be related or beneficial. Comparing performance levels of IT assets to value delivered is a technique to measure and optimize the efficiency and effectiveness of the IT resources and activities that support the organization’s goals and needs. However, this technique does not necessarily involve the IT risk profile, as it focuses on the output and outcome of the IT assets, not the input and impact of the IT risks. Facilitating the alignment of strategic IT objectives to business objectives is a technique toensure that the IT strategy and plans are consistent and compatible with the organization’s vision, mission, strategy, and objectives. However, this technique does not depend on the IT risk profile, as it focuses on the direction and purpose of the IT objectives, not the probability and threat of the IT risks. Providing input to business managers when preparing a business case for new IT projects is a technique to support and justify the initiation and implementation of new IT initiatives that can create value or solve problems for the organization. However, this technique does not require the IT risk profile, as it focuses on the cost and benefit of the IT projects, not the risk and response of the IT risks. References = CRISC Review Manual, pages 38-391; CRISC Review Questions, Answers & Explanations Manual, page 962; IT Risk Management Guide for 2022 | CIO Insight3; IT Risk Management Process, Frameworks & Templates4
Which of the following is the FIRST step in managing the security risk associated with wearable technology in the workplace?
Identify the potential risk.
Monitor employee usage.
Assess the potential risk.
Develop risk awareness training.
The security risk associated with wearable technology in the workplace is the possibility and impact of unauthorized access, disclosure, or use of the data or information that are collected, stored, or transmitted by the wearable devices, such as smartwatches, fitness trackers, or glasses, that are worn or used by the employees12.
The first step in managing the security risk associated with wearable technology in the workplace is to identify the potential risk, which is the process of recognizing and describing the sources,causes, and consequences of the risk, and the potential impacts on the organization’s objectives, performance, and value creation34.
Identifying the potential risk is the first step because it provides the basis and input for the subsequent steps of the risk management process, such as assessing, treating, monitoring, and communicating the risk34.
Identifying the potential risk is also the first step because it enables the organization to understand and prioritize the risk, and to allocate the appropriate resources and controls for the risk management process34.
The other options are not the first step, but rather possible subsequent steps that may depend on or follow the identification of the potential risk. For example:
Monitoring employee usage is a step that involves collecting and analyzing data and information on the frequency, duration, and purpose of the wearable devices that are used by the employees, and detecting and reporting any deviations, anomalies, or issues that may indicate a security risk5 . However, this step is not the first step because it requires theidentification of the potential risk to provide the guidance and standards for the monitoring process5 .
Assessing the potential risk is a step that involves estimating and evaluating the likelihood and impact of the risk, and the level of risk exposure or tolerance for the organization34. However, this step is not the first step because it requires the identification of the potential risk to provide the information and data for the assessment process34.
Developing risk awareness training is a step that involves educating and training the employees and other stakeholders on the security risks and best practices associated with the wearable technology, and informing them of their roles, obligations, and responsibilities for the risk management process . However, this step is not the first step because it requires the identification of the potential risk to provide the content and objectives for the training process . References =
1: Wearable Devices in the Workplace: Security Threats and Protection1
2: 10 security risks of wearables | CSO Online2
3: Risk IT Framework, ISACA, 2009
4: IT Risk Management Framework, University of Toronto, 2017
5: Continuous Monitoring - ISACA3
Continuous Monitoring: A New Approach to Risk Management - ISACA Journal4
What Is Security Awareness Training and Why Is It Important? - Kaspersky5
Security Awareness Training - Cybersecurity Education Online | Proofpoint US
Which of the following would be a risk practitioners’ BEST recommendation for preventing cyber intrusion?
Establish a cyber response plan
Implement data loss prevention (DLP) tools.
Implement network segregation.
Strengthen vulnerability remediation efforts.
A cyber intrusion is an unauthorized or malicious access to a computer system or network by an attacker. A cyber intrusion can compromise the confidentiality, integrity, or availability of the system or network, as well as the data and services that it hosts. A cyber intrusion can also cause damage, disruption, or theft to the organization or its stakeholders. One of the best ways to prevent cyber intrusion is to strengthen vulnerability remediation efforts, which means to identify and fix the weaknesses or flaws in the system or network that can be exploited by the attackers. Vulnerability remediation efforts can include conducting regularvulnerability assessments, applying security patches and updates, configuring security settings and policies, and implementing security controls and measures. By strengthening vulnerability remediation efforts, the organization can reduce the attack surface and the likelihood of cyber intrusion, as well as enhance the resilience and protection of the system or network. The other options are not the best recommendations for preventing cyber intrusion, although they may be helpful and complementary. Establishing a cyber response plan is a technique to prepare for and respond to a cyber incident, such as a cyber intrusion, by defining the roles, responsibilities, procedures, and resources that are needed to manage and recover from the incident. However, a cyber response plan is a reactive and contingency measure, while strengthening vulnerability remediation efforts is a proactive and preventive measure. Implementing data loss prevention (DLP) tools is a technology that tries to detect and stop sensitive data breaches, or data leakage incidents, in an organization. DLP tools can help to protect the data from being disclosed to an unauthorized person, whether it is deliberate or accidental. However, DLP tools do not prevent cyber intrusion itself, as they only focus on the data, not the system or network. Implementing network segregation is a method to divide a network into smaller segments or subnetworks, each with its own security policies and controls. Network segregation can help to isolate and contain the impact of a cyber intrusion, as well as to limit the access and movement of the attackers within the network. However, network segregation does not prevent cyber intrusion from occurring, as it does not address thevulnerabilities or flaws in the system or network. References = CRISC Review Manual, pages 164-1651; CRISC Review Questions, Answers & Explanations Manual, page 902; What Are Security Controls? - F53; Assessing Security Controls: Keystone of the Risk Management … - ISACA4
Which of the following would BEST help to ensure that identified risk is efficiently managed?
Reviewing the maturity of the control environment
Regularly monitoring the project plan
Maintaining a key risk indicator for each asset in the risk register
Periodically reviewing controls per the risk treatment plan
According to the CRISC Review Manual (Digital Version), periodically reviewing controls per the risk treatment plan would best help to ensure that identified risk is efficiently managed, as it involves verifying the effectiveness and efficiency of the implemented risk response actions and identifying any gaps or changes in the risk profile. Periodically reviewing controls per the risk treatment plan helps to:
Confirm that the controls are operating as intended and producing the desired outcomes
Detect any deviations, errors, or weaknesses in the controls and their performance
Evaluate the adequacy and appropriateness of the controls in relation to the current risk environment and the organization’s risk appetite and risk tolerance
Recommend and implement corrective actions or improvement measures to address any issues or deficiencies in the controls
Update the risk register and the risk treatment plan to reflect the current risk status and the residual risk levels
References = CRISC Review Manual (Digital Version), Chapter 4: IT Risk Monitoring and Reporting, Section 4.1: IT Risk Monitoring, pp. 215-2161
Which of the following controls would BEST reduce the risk of account compromise?
Enforce password changes.
Enforce multi-factor authentication (MFA).
Enforce role-based authentication.
Enforce password encryption.
Detailed Explanation:Multi-factor authentication (MFA)significantly reduces the risk of account compromise by requiring multiple forms of verification, such as a password and a one-time code, enhancing security beyond single-factor authentication methods.
Which of the following is the PRIMARY reason for sharing risk assessment reports with senior stakeholders?
To support decision-making for risk response
To hold risk owners accountable for risk action plans
To secure resourcing for risk treatment efforts
To enable senior management to compile a risk profile
The primary reason for sharing risk assessment reports with senior stakeholders is to support decision-making for risk response. Risk assessment reports are documents that summarize the results of the risk assessment process, such as the risk sources, causes, impacts, likelihood, and levels. Risk assessment reports also provide recommendations for risk response options, such as avoiding, reducing, transferring, or accepting the risk. Sharing risk assessment reports with senior stakeholders helps to inform them of the current risk situation, and to solicit their input, feedback, or approval for the risk response actions. The other options are not the primary reason for sharing risk assessment reports, although they may be secondary reasons or outcomes. References = Risk and Information Systems Control Study Manual, Chapter 4, Section 4.2.1, page 4-13.
Which of the following is the MOST effective way 10 identify an application backdoor prior to implementation'?
User acceptance testing (UAT)
Database activity monitoring
Source code review
Vulnerability analysis
A source code review is the process of examining and analyzing the source code of an application to identify any vulnerabilities, errors, or flaws that may compromise the security, functionality, or performance of the application. A source code review is the most effective way to identify an application backdoor prior to implementation, as it can detect any hidden or unauthorized code that may allow unauthorized access, bypass security controls, or execute malicious commands. A source code review can also help to improvethe quality and reliability of the application, and ensure compliance with the coding standards and best practices. References = CRISC Review Manual, 7th Edition, page 181.
Which key performance efficiency IKPI) BEST measures the effectiveness of an organization's disaster recovery program?
Number of service level agreement (SLA) violations
Percentage of recovery issues identified during the exercise
Number of total systems recovered within tie recovery point objective (RPO)
Percentage of critical systems recovered within tie recovery time objective (RTO)
The key performance indicator (KPI) that best measures the effectiveness of an organization’s disaster recovery program is the percentage of critical systems recovered within the recovery time objective (RTO). The RTO is the acceptable timeframe within which a business process or system must be restored after a disruption. The percentage of critical systems recovered within the RTO indicates how well the disaster recovery program can meet the business continuity requirements and minimize the impact of the disruption. The other options are not as good as the percentage of critical systems recovered within the RTO, as they are related to the efficiency, quality, or scope of the disaster recovery program, not the effectiveness of the disaster recovery program. References = Risk and Information Systems Control StudyManual, Chapter 4: Risk and Control Monitoring and Reporting, Section 4.2: Key Performance Indicators, page 183.
A risk practitioner is reporting on an increasing trend of ransomware attacks in the industry. Which of the following information is MOST important to include to enable an informed response decision by key stakeholders?
Methods of attack progression
Losses incurred by industry peers
Most recent antivirus scan reports
Potential impact of events
The potential impact of events is the estimated magnitude and likelihood of the consequences that may result from a risk scenario. The potential impact of events can help key stakeholders understand the severity and urgency of the risk, and prioritize the appropriate response actions. The potential impact of events can be expressed in quantitative or qualitative terms, such as financial loss, operational disruption, reputational damage, legal liability, etc. The potential impact of events is the most important information to include when reporting on an increasing trend of ransomware attacks in the industry, as it can help stakeholders assess the level of risk exposure and the adequacy of the existing controls. References = Risk and Information Systems Control Study Manual, Chapter 2: IT Risk Assessment, Section 2.3: Risk Analysis, p. 87-89.
Which of the following should management consider when selecting a risk mitigation option?
Maturity of the enterprise architecture
Cost of control implementation
Reliability of key performance indicators (KPIs)
Reliability of key risk indicators (KPIs)
When selecting a risk mitigation option, management should consider the cost of control implementation, as well as the benefits and residual risks. The cost of control implementation includes the direct costs of acquiring, installing, and maintaining the control, as well as the indirect costs of potential side effects, suchas reduced performance, increased complexity, or decreased user satisfaction. The cost of control implementation should be balanced with the expected reduction in risk exposure and the alignment with the enterprise’s risk appetite and tolerance. The maturity of the enterprise architecture, the reliability of key performance indicators (KPIs), and the reliability of key risk indicators (KRIs) are relevant factors for risk identification and assessment, but not for risk response selection. References = Risk and Information Systems Control Study Manual, Chapter 4: Risk Response, page 149.
A risk practitioner has been notified that an employee sent an email in error containing customers' personally identifiable information (Pll). Which of the following is the risk practitioner's BEST course of action?
Report it to the chief risk officer.
Advise the employee to forward the email to the phishing team.
follow incident reporting procedures.
Advise the employee to permanently delete the email.
The best course of action for the risk practitioner is to follow the incident reporting procedures established by the organization. This will ensure that the incident is properly documented, escalated, and resolved in a timely and consistent manner. Reporting the incident to the chief risk officer, advising the employee to forward the email to the phishing team, or advising the employee to permanently delete the email are not the best courses of action, as they may not comply with the organization’s policies and standards, and may not address the root cause and impact of the incident. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 4, Section 4.2.2.1, page 193.
Which of the following is a risk practitioner's BEST course of action upon learning that a control under internal review may no longer be necessary?
Obtain approval to retire the control.
Update the status of the control as obsolete.
Consult the internal auditor for a second opinion.
Verify the effectiveness of the original mitigation plan.
The best course of action for a risk practitioner upon learning that a control under internal review may no longer be necessary is to obtain approval to retire the control. This will help to ensure that the control is removed in a controlled and documented manner, and that the relevant stakeholders are informed and agree with the decision. Retiring unnecessary controls can also help to optimize the control environment, reduce costs and complexity, and improve efficiency and performance. Updating the status of the control as obsolete, consulting the internal auditor for a second opinion, and verifying the effectiveness of the original mitigation plan are not the best courses of action, as they may not address the root cause of the control’s obsolescence, and may delay or complicate the control retirement process. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 3, Section 3.1.1.2, page 1071
1: ISACA Certified in Risk and Information Systems Control (CRISC®) Exam Guide, Answer to Question 649.
Which of the following observations would be GREATEST concern to a risk practitioner reviewing the implementation status of management action plans?
Management has not determined a final implementation date.
Management has not completed an early mitigation milestone.
Management has not secured resources for mitigation activities.
Management has not begun the implementation.
The observation that would be of GREATEST concern to a risk practitioner reviewing the implementation status of management action plans is that management has not begun the implementation, because it indicates that the management action plans are not being executed or monitored, and that the risks are not being addressed or mitigated. The lack of implementation may also imply that the management action plans are not realistic, feasible, or aligned with the enterprise’s strategy and objectives. The other options are not as concerning as the lack of implementation, because:
Option A: Management has not determined a final implementation date is a concern, but not the greatest one, because it may affect the timely completion and delivery of the management action plans, but it does not necessarily mean that the management action plans are not being executed or monitored.
Option B: Management has not completed an early mitigation milestone is a concern, but not the greatest one, because it may indicate a delay or deviation in the progress and performance of the management action plans, but it does not necessarily mean that the management action plans are not being executed or monitored.
Option C: Management has not secured resources for mitigation activities is a concern, but not the greatest one, because it may affect the quality and effectiveness of the management action plans, but it does not necessarily mean that the management action plans are not being executed or monitored. References = Risk and Information Systems Control Study Manual, 7th Edition, ISACA, 2020, p. 123.
An organization is unable to implement a multi-factor authentication requirement until the next fiscal year due to budget constraints. Consequently, a policy exception must be submitted. Which of the following is MOST important to include in the analysis of the exception?
Sections of the policy that may justify not implementing the requirement
Risk associated with the inability to implement the requirement
Budget justification to implement the new requirement during the current year
Industry best practices with respect to implementation of the proposed control
The most important factor to include in the analysis of the policy exception is the risk associated with the inability to implement the multi-factor authentication requirement. A policy exception is a temporary orpermanent deviation from the established policies or standards of the organization, due to various reasons, such as budget constraints, technical limitations, or business needs. A policy exception must be submitted and approved by the appropriate authority, and it must include a clear and comprehensive analysis of the rationale, impact, and mitigation of the exception. The risk associated with the inability to implement the multi-factor authentication requirement is the most important factor to include in the analysis, because it evaluates the probability and severity of potential threats or incidents that could exploit the lack of multi-factor authentication, such as unauthorized access, data breach, or identity theft. The risk analysis also helps to justify the need and urgency of the policy exception, and to propose alternative or compensating controls to reduce or transfer the risk, such as password policies, access restrictions, or encryption. The other options are not the most important factor, although they may be relevant or supportive to the policy exception analysis. Sections of the policy that may justify not implementing the requirement are the clauses or provisions in the policy that allow or enable the policy exception, such as exemptions, waivers, or variances. These sections can help to validate the legitimacy and feasibility of the policy exception, but they do not assess the risk or the impact of the exception. Budget justification to implement the new requirement during the current year is the explanation and evidence of the financial resources and constraints that affect the implementation of the multi-factor authentication requirement. This justification can help to demonstrate the cost-benefit and return on investment of the requirement, but it does not measure the risk or the mitigation of the exception. Industry best practices with respect to implementation of the proposed control are the proven methods and standards that are adopted by the leading organizations in a specific field or sector for implementing the multi-factor authentication requirement. These best practices can help to benchmark and improve the quality and effectiveness of the requirement, but they do not quantify the risk or the impact of the exception. References = Policy Exception Management - ISACA, Multi-Factor Authentication Policy - University of Arkansas, Common Conditional Access policy: Require MFA for all users
Which of the following activities is PRIMARILY the responsibility of senior management?
Bottom-up identification of emerging risks
Categorization of risk scenarios against a standard taxonomy
Prioritization of risk scenarios based on severity
Review of external loss data
The primary responsibility of senior management in risk management is to prioritize the risk scenarios based on severity. Risk scenarios are hypothetical events or situations that could affect the achievement of the objectives. Risk severity is a measure of the overall level of risk, based on the combination of the probability and impact of the risk scenario. Prioritizing the risk scenarios based on severity is the primary responsibility of senior management, because it helps to allocate the resources and actions to the most critical and urgent risks, and to align the risk management process with the organizational strategy and risk appetite. Senior management also has the authority and accountability to make the final decisions and approve the risk response plans for the prioritized risks. The other options are not the primary responsibility of senior management, although they may be involved or consulted in these activities. Bottom-up identification of emerging risks is a process of identifying and reporting the new or changing risks that may arise from the operational or tactical level of the organization. This is usually the responsibility of the risk owners or the risk practitioners, who have the knowledge and experience of the specific functions and processes. Categorization of risk scenarios against a standard taxonomy is a process of classifying and organizing the risk scenarios into predefined categories or groups, based on their nature, source, or impact. This is usually the responsibility of the risk analysts or the risk coordinators, who have the skills and tools to perform the risk analysis and assessment. Review of external loss data is a process of collecting and analyzing the data and information on the losses or incidents that occurred in other organizations or industries, due to similar or related risks. This is usually the responsibility of the risk researchers or the risk consultants, who have the access and expertise to obtain and interpret the external data and information. References = The Role of Executive Management in ERM - Corporate Compliance Insights, Guidelines on Risk Management Practices – Board and Senior Management, Risk Manager Job Description [+2023 TEMPLATE] - Workable
The MAIN purpose of having a documented risk profile is to:
comply with external and internal requirements.
enable well-informed decision making.
prioritize investment projects.
keep the risk register up-to-date.
According to the Risk Management Essentials, a risk profile is established to enhance senior management’s analysis and decision making related to priority setting and resource allocation. A risk profile is a description of a set of risks that an organization faces, and it helps to make the risks visible and understandable. By having a documented risk profile, an organization can identify the nature and level of the threats, assess the likelihood and impact of the risks, evaluate the effectiveness of the controls, and determine the risk appetite and tolerance. This information can help the organization to make well-informed decisions on how to manage the risks and achieve its objectives. References = Risk Management Essentials, Risk Profile: Definition, Importance for Individuals & Companies
An organization has identified that terminated employee accounts are not disabled or deleted within the time required by corporate policy. Unsure of the reason, the organization has decided to monitor the situation for three months to obtain more information. As a result of this decision, the risk has been:
avoided.
accepted.
mitigated.
transferred.
Risk acceptance is a risk response strategy that involves acknowledging the existence and potential impact of a risk, but deciding not to take any action to reduce or eliminate it. Risk acceptance can be appropriate when the cost or effort of implementing a risk response outweighs the benefit, or when there are no feasible or effective risk responses available. An organization has identified that terminated employee accounts are not disabled or deleted within the time required by corporate policy, which poses a security risk to the organization. The organization is unsure of the reason for this issue, and has decided to monitor the situation for three months to obtain more information, rather than taking any immediate action to resolve the issue. As a result of this decision, the risk has been accepted, as the organization has chosen to tolerate the risk exposure for a certain period of time, and has not implemented any controls or measures to prevent or reduce the risk occurrence or impact. References = Risk Response Strategies: Avoid, Transfer, Mitigate, Accept, Risk Response Strategies: What They Are and How to Use Them, Risk Response Strategy: Definition, Types, and Examples.
Which of the following would BEST enable a risk practitioner to embed risk management within the organization?
Provide risk management feedback to key stakeholders.
Collect and analyze risk data for report generation.
Monitor and prioritize risk data according to the heat map.
Engage key stakeholders in risk management practices.
Engaging key stakeholders in risk management practices is the best way to embed risk management within the organization. This means that the risk practitioner involves and communicates with the people who have an interest or influence in the organization’s objectives, activities, and risks, such as senior management, business unit managers, employees, customers, suppliers, regulators, etc.
Engaging key stakeholders in risk management practices helps to create a risk-aware culture, align risk management with the organization’s strategy and vision, ensure the ownership and accountability of risks and controls, obtain the support and commitment for risk management initiatives, and improve the risk management performance and outcomes.
The other options are not the best ways to embed risk management within the organization. They are either secondary or not essential for risk management.
The references for this answer are:
Risk IT Framework, page 17
Information Technology & Security, page 11
Risk Scenarios Starter Pack, page 9
What are the MOST important criteria to consider when developing a data classification scheme to facilitate risk assessment and the prioritization of risk mitigation activities?
Mitigation and control value
Volume and scope of data generated daily
Business criticality and sensitivity
Recovery point objective (RPO) and recovery time objective (RTO)
Data classification is the process of organizing data in groups based on their attributes and characteristics, and then assigning class labels that describe a set of attributes that hold true for the corresponding data sets1. Data classification helps an organization understand the value of its data, determine whether the data is at risk, and implement controls to mitigate risks1. Data classification also helps an organization comply with relevant industry-specific regulatory mandates such as SOX, HIPAA, PCI DSS, and GDPR1.
The most important criteria to consider when developing a data classification scheme are the business criticality and sensitivity of the data2. Business criticality refers to the impact of data loss or compromise on the organization’s operations, reputation, and objectives2. Sensitivity refers to the level of confidentiality, integrity, and availability required for the data2. Data that is highly critical and sensitive should be classified and protected accordingly, as it poses the highest risk to the organization if mishandled or breached2.
Some of the best practices for data classification are3:
Inventory your data: Identify all data assets within your organization.
Define data categories: Create a classification scheme that suits your organization’s needs.
Assign responsibility: Designate individuals or teams responsible for data classification.
Implement classification tools: Invest in tools and technologies that facilitate data classification.
Educate and train: Raise awareness and provide guidance on data classification policies and procedures.
Review and audit: Monitor and evaluate the effectiveness and compliance of data classification.
References = What is Data Classification? | Best Practices & Data Types | Imperva, What Is Data Classification? The 5 Step Process & Best Practices for Classifying Data | Splunk, Top 10 Best Practices for Securing Your Database - 2023
The PRIMARY goal of a risk management program is to:
facilitate resource availability.
help ensure objectives are met.
safeguard corporate assets.
help prevent operational losses.
According to the What Is Risk Management & Why Is It Important? article, risk management is the systematic process of identifying, assessing, and mitigating threats or uncertainties that can affect your organization. The primary goal of a risk management program is to help ensure objectives are met, by aligning the risk management process with the organization’s strategy, vision, mission, values, and objectives. By having a risk management program, an organization can identify potential problems before they occur and have a plan for addressing them, as well as monitor and report on the effectiveness of the risk responses. This can help the organization to achieve its desired outcomes and create value for its stakeholders. References = What Is Risk Management & Why Is It Important?
To mitigate the risk of using a spreadsheet to analyze financial data, IT has engaged a third-party vendor to deploy a standard application to automate the process. Which of the following parties should own the risk associated with calculation errors?
business owner
IT department
Risk manager
Third-party provider
According to the CRISC Review Manual1, the business owner is the person who has the authority and accountability for the achievement of the business objectives and the management of the associated risks. The business owner is ultimately responsible for ensuring that the IT services and solutions support the business needs and goals, and for accepting or rejecting the residual risks after the implementation of risk responses. Therefore, the business owner should own the risk associated with calculation errors, as they are the ones who will be affected by the potential impact of the errors on the financial data and decisions. References = CRISC Review Manual1, page 194.
When assessing the maturity level of an organization's risk management framework, which of the following deficiencies should be of GREATEST concern to a risk practitioner?
Unclear organizational risk appetite
Lack of senior management participation
Use of highly customized control frameworks
Reliance on qualitative analysis methods
Senior management participation is essential for the success of an organization’s risk management framework, as it demonstrates the commitment, support, and leadership for the risk management activities. Senior management participation also ensures that the risk management framework is aligned with the organization’s strategy, objectives, and culture, and that the risk management roles and responsibilities are clearly defined and communicated. Senior management participation also facilitates the allocation of adequate resources, the establishment of risk appetite and tolerance, and the monitoring and reporting of risk performance. Therefore, the lack of senior management participation should be of greatest concern to a risk practitioner, as it indicates a low level of risk maturity and a high level of risk exposure. The other options are not as concerning as the lack of senior management participation, because they do not affect the risk management framework as significantly, and they can be addressed or improved with the involvement of senior management, as explained below:
A. Unclear organizational risk appetite is a deficiency that can affect the risk management framework, as it can lead to inconsistent or inappropriate risk decisions and responses. However, this deficiency can be resolved or mitigated with the participation of senior management, who can define and communicate the risk appetite and tolerance for the organization, and ensure that they are aligned with the organization’s strategy and objectives.
C. Use of highly customized control frameworks is a deficiency that can affect the risk management framework, as it can create complexity, confusion, or duplication in the control design and implementation. However, this deficiency can be resolved or mitigated with the participation of senior management, who can review and rationalize the control frameworks, and ensure that they are relevant, effective, and efficient for the organization’s risk profile and environment.
D. Reliance on qualitative analysis methods is a deficiency that can affect the risk management framework, as it can limit the accuracy, reliability, and comparability of the risk information and assessment. However, this deficiency can be resolved or mitigated with the participation of senior management, who can support and promote the use of quantitative analysis methods, such as the FAIR framework1, and provide the necessary data, tools, and skills for the risk analysis and evaluation. References = Risk and Information Systems Control Study Manual, Chapter 1, Section 1.3.2, page 18.
Which of the following is the BEST way to detect zero-day malware on an end user's workstation?
An antivirus program
Database activity monitoring
Firewall log monitoring
File integrity monitoring
Zero-day malware is malware that exploits unknown and unprotected vulnerabilities. This novel malware is difficult to detect and defend against, making zero-day attacks a significant threat to enterprise cybersecurity1. The best way to detect zero-day malware on an end user’s workstation is to use file integrity monitoring, which is a technique that monitors and alerts on changes to files and directories that may indicate a malware infection or compromise2. By using file integrity monitoring, the end user can detect zero-day malware that may alter or damage the files or directories on their workstation, and take appropriate actions to remove or isolate the malware. File integrity monitoring can also help to prevent the spread of zero-day malware to other systems or networks, and to restore the integrity and availability of the affected files or directories. Antivirus program, database activity monitoring, and firewall log monitoring are not the best ways to detect zero-day malware on an end user’s workstation, as they are not as effective or reliable as file integrity monitoring. Antivirus program is a software that scans and removes known malware from a system or network3. Antivirus program can help to protect the end user’s workstation from common or known malware, but it may not be able to detect zero-day malware that does not have a signature or a pattern that matches the antivirus program’s database. Database activity monitoring is a technique that monitors and audits the activities and transactions on a database, such as queries, updates, or deletions4. Database activity monitoring can help to protect the end user’s database from unauthorized or malicious access or modification, but it may not be able to detect zero-day malware that does not target or affect the database. Firewall log monitoring is a technique that monitors and analyzes the logs generated by a firewall, which is a device or software that filters and controls the incoming and outgoing network traffic based on predefined rules. Firewall log monitoring can help to protect the end user’s workstation from external or internal network attacks, but it may not be able to detect zero-day malwarethat bypasses or evades the firewall rules or that originates from the workstation itself. References = 1: What is Zero Day Malware? - Check Point Software2: File Integrity Monitoring - an overview | ScienceDirect Topics3: Antivirus Software - an overview | ScienceDirect Topics4: Database Activity Monitoring - an overview | ScienceDirect Topics : [Firewall Log Analysis - an overview | ScienceDirect Topics] : [Risk and Information Systems Control Study Manual, Chapter 5: Information Systems Control Design and Implementation, Section 5.1: Control Design, pp. 233-235.] : [Risk and Information Systems Control Study Manual, Chapter 5: Information Systems Control Design and Implementation, Section 5.2: Control Implementation, pp. 243-245.] : [Risk and Information Systems Control Study Manual, Chapter 5: Information Systems Control Design and Implementation, Section 5.3: Control Monitoring and Maintenance, pp. 251-253.] : [Zero-day attack detection: a systematic literature review | Artificial Intelligence Review] : [Zero-day Attacks Detection and Prevention Methods | Apriorit]
Which of the following would be the BEST justification to invest in the development of a governance, risk, and compliance (GRC) solution?
Facilitating risk-aware decision making by stakeholders
Demonstrating management commitment to mitigate risk
Closing audit findings on a timely basis
Ensuring compliance to industry standards
A vulnerability management process is a process that identifies, analyzes, prioritizes, and remediates the vulnerabilities in the IT systems and applications. The effectiveness of a vulnerability management process can be measured by the key performance indicators (KPIs) that reflect the achievement of the process objectives and the alignment with the enterprise’s risk appetite and tolerance. The best KPI to measure the effectiveness of a vulnerability management process is the percentage of vulnerabilities remediated within the agreed service level. This KPI indicates how well the process is able to address the vulnerabilities in a timely and efficient manner, and reduce the exposure and impact of the risks associated with the vulnerabilities. The other options are not as good as the percentage of vulnerabilities remediated within the agreed service level, as they may not reflect the quality or timeliness of the remediation actions, or the alignment with the enterprise’s risk appetite and tolerance. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 4, Section 4.3.2.1, pp. 171-172.
Which of the following would present the GREATEST challenge when assigning accountability for control ownership?
Weak governance structures
Senior management scrutiny
Complex regulatory environment
Unclear reporting relationships
Control ownership is the assignment of roles and responsibilities for the design, implementation, monitoring, and improvement of controls that mitigate risks. Control ownership can help ensure that the controls are effective, efficient, and aligned with the business objectives and risk appetite. Control ownership can also help facilitate the communication, coordination, and accountability among the stakeholders involved in the risk management process. One of the factors that would present the greatest challenge when assigning accountability for control ownership is unclear reporting relationships. Reporting relationships are the formal or informal lines of authority and communication that define who reports to whom, and who is accountable for what. Unclear reporting relationships can create confusion, ambiguity, and conflict among the control owners and other stakeholders, such as the risk owners, the business owners, the auditors, the regulators, etc. Unclear reporting relationships can also hinder the performance evaluation, feedback, and recognition of the control owners, and affect their motivation and commitment. Unclear reporting relationships can also increase the risk of duplication, inconsistency, or gaps in the control activities, and compromise the quality and reliability of the control environment. References = Defining, Assigning and Measuring: Accountability Challenges in 21st Century Governance, CRISC 351-400 topic3, Foundations of Project Management : Week 2.
The MOST important reason to monitor key risk indicators (KRIs) is to help management:
identity early risk transfer strategies.
lessen the impact of realized risk.
analyze the chain of risk events.
identify the root cause of risk events.
Key risk indicators (KRIs) are metrics used by organizations to monitor and assess potential risks that may impact their objectives and performance. KRIs also provide early warning signals that help organizations identify, analyze, and address risks before they escalate into significant issues1. The most importantreason to monitor KRIs is to help management lessen the impact of realized risk, which is the actual or expected negative consequence of a risk event2. By monitoring KRIs, management can gain insight into the current and emerging risk exposures and trends, and evaluate their alignment with the organization’s risk appetite and tolerance3. This enables management to make informed and timely decisions and actions to mitigate or eliminate the risks, and to allocate resources and prioritize efforts where they are most needed. By lessening the impact of realized risk, management can also protect and enhance the organization’s reputation, performance, and value. Identifying early risk transfer strategies, analyzing the chain of risk events, and identifying the root cause of risk events are not the most important reasons to monitor KRIs, as they do not provide the same level of benefit and value as lessening the impact of realized risk. Identifying early risk transfer strategies is a process that involves finding and implementing ways to shift or share the risk or its impact to another party, such as through insurance, outsourcing, or hedging4. Identifying early risk transfer strategies can help to reduce the organization’s risk exposure and liability, but it does not necessarily lessen the impact of realized risk, as the risk or its impact may still occur or affect the organization indirectly. Analyzing the chain of risk events is a process that involves tracing and understanding the sequence and interconnection of the risk events that lead to a specific outcome or consequence5. Analyzing the chain of risk events can help to identify and address the root causes and contributing factors of the risk events, but it does not necessarily lessen the impact of realized risk, as the outcome or consequence may have already occurred or be unavoidable. Identifying the root cause of risk events is a process that involves finding and determining the underlying or fundamental source or reason of the risk events. Identifying the root cause of risk events can help to prevent or correct the recurrence or escalation of the risk events, but it does not necessarily lessen the impact of realized risk, as the impact may have already happened or be irreversible. References = 1: Key Risk Indicators: A Practical Guide | SafetyCulture2: Risk Impact - an overview | ScienceDirect Topics3: KRI Framework for Operational Risk Management | Workiva4: Risk Transfer - an overview | ScienceDirect Topics5: Event Chain Methodology - Wikipedia : [Root Cause Analysis - an overview | ScienceDirect Topics] : [Risk and Information Systems Control Study Manual, Chapter 4: Risk and Control Monitoring and Reporting, Section 4.1: Key Risk Indicators, pp. 181-185.]
To help ensure all applicable risk scenarios are incorporated into the risk register, it is MOST important to review the:
risk mitigation approach
cost-benefit analysis.
risk assessment results.
vulnerability assessment results
To help ensure all applicable risk scenarios are incorporated into the risk register, it is most important to review the risk assessment results, which are the outputs of the process of identifying, analyzing, and evaluating the risks that affect a project or an organization. The risk assessment results provide information on the sources, causes, impacts, likelihood, and severity of the risks, as well as the existing controls and their effectiveness. The risk assessment results help to determine the risk level and priority of each risk scenario, and to select the most appropriate risk response strategy. The risk assessment results are the basis for creating and updating the risk register, which is a document that records and tracks theidentified risks, their characteristics, responses, owners, and status12. The other options are not the most important factors to review, as they are either derived from or dependent on the risk assessment results. The risk mitigation approach is the plan and actions to reduce the impact or likelihood of the risks, and it is based on the risk assessment results. The cost-benefit analysis is the comparison of the costs and benefits of implementing the risk response strategy, and it is influenced by the risk assessment results. The vulnerability assessment results are the identification and measurement of the weaknesses or gaps in the information systems or resources, and they are part of the risk assessment results. References = Risk Assessment in Project Management | PMI; Risk Assessment Process: Definition, Steps, and Examples; Risk Assessment - an overview | ScienceDirect Topics; Risk Register: A Project Manager’s Guide with Examples [2023] • Asana; What Is a Risk Register? | Smartsheet
The MOST essential content to include in an IT risk awareness program is how to:
populate risk register entries and build a risk profile for management reporting.
prioritize IT-related actions by considering risk appetite and risk tolerance.
define the IT risk framework for the organization.
comply with the organization's IT risk and information security policies.
The most essential content to include in an IT risk awareness program is how to comply with the organization’s IT risk and information security policies. This will help to ensure that the staff members are aware of their roles and responsibilities, and that they follow the best practices and standards to protect the organization’s information assets and systems. Compliance with the IT risk and information security policies also helps to reduce the likelihood and impact of IT-related incidents and breaches, and to align the IT activities with the organization’s objectives and strategies. Populating risk register entries, prioritizing IT-related actions, and defining the IT risk framework are important aspects of IT risk management, but they are not the most essential content to include in an IT risk awareness program. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 5, Section 5.1.1.2, page 2291
1: ISACA Certified in Risk and Information Systems Control (CRISC®) Exam Guide, Answer to Question 646.
Which of the following is MOST helpful in verifying that the implementation of a risk mitigation control has been completed as intended?
An updated risk register
Risk assessment results
Technical control validation
Control testing results
Control testing is the process of verifying that the risk mitigation controls are designed and operating effectively, and that they achieve the intended objectives and outcomes. Control testing can involve various methods, such as observation, inspection, inquiry, re-performance, or simulation. Control testing results can provide evidence and assurance that the implementation of a risk mitigation control has been completed as intended, and that the control is functioning properly and consistently. Control testing results can also identify any issues or deficiencies in the control design or operation, and recommend corrective actions or improvements. The other options are not as helpful as control testing results, because they do not provide a direct and objective verification of the control implementation, but rather focus on other aspects or outputs of the risk management process, as explained below:
A. An updated risk register is a document that records and tracks the identified risks, their characteristics, and their status. An updated risk register can reflect the changes in the risk profile and exposure after the implementation of a risk mitigation control, but it does not verify that the control implementation has been completed as intended, or that the control is effective and reliable.
B. Risk assessment results are the outputs of the risk analysis and evaluation process, which measure the impact and likelihood of the risks, and assign a risk rating and priority. Risk assessment results can indicate the level of risk exposure and the need for risk mitigation controls, but they do not verify that the control implementation has been completed as intended, or that the control is effective and reliable.
C. Technical control validation is the process of ensuring that the technical aspects of a control, such as hardware, software, or network components, are configured and functioning correctly. Technical control validation can verify that the control implementation meets the technical specifications and requirements, but it does not verify that the control implementation has been completed as intended, or that the control is effective and reliable from a business perspective. References = Risk and Information Systems Control Study Manual, Chapter 4, Section 4.3.3, page 130.
Which of the following criteria is MOST important when developing a response to an attack that would compromise data?
The recovery time objective (RTO)
The likelihood of a recurring attack
The organization's risk tolerance
The business significance of the information
According to the CRISC Review Manual (Digital Version), the business significance of the information is the most important criterion when developing a response to an attack that would compromise data, as it determines the impact and severity of the attack on the organization’s objectives and performance. The business significance of the information helps to:
Assess the value and sensitivity of the data that is compromised or at risk of compromise
Evaluate the potential losses or damages that the organization may incur due to the data compromise
Prioritize the data recovery and restoration activities based on the criticality and urgency of the data
Communicate and coordinate the data breach response and notification with the relevant stakeholders, such as the data owners, the customers, the regulators, and the media
Enhance the data protection and security measures to prevent or mitigate future data compromise incidents
References = CRISC Review Manual (Digital Version), Chapter 3: IT Risk Response, Section 3.3: Risk Response Options, pp. 174-1751
Which of the following is the BEST way to determine software license compliance?
List non-compliant systems in the risk register.
Conduct periodic compliance reviews.
Review whistleblower reports of noncompliance.
Monitor user software download activity.
According to the 6 Best Practices to Ensure Software License Compliance article, the best way to determine software license compliance is to conduct regular internal compliance audits. These self-assessments can be done with the help of software license management companies. The goal is to see where compliance issues lie and to take corrective actions before they become serious problems. Periodic compliance reviews can help to avoid fines, penalties, lawsuits, and reputational damage that may result from software license violations. They can also help to optimize software spending and utilization, and to identify any gaps or opportunities for improvement in the software license management process. References = 6 Best Practices to Ensure Software License Compliance
An organization has opened a subsidiary in a foreign country. Which of the following would be the BEST way to measure the effectiveness of the subsidiary's IT systems controls?
Implement IT systems in alignment with business objectives.
Review metrics and key performance indicators (KPIs).
Review design documentation of IT systems.
Evaluate compliance with legal and regulatory requirements.
The best way to measure the effectiveness of the subsidiary’s IT systems controls is to review metrics and key performance indicators (KPIs), as they provide quantitative and qualitative measures of the performance and outcomes of the IT systems and processes, and how well they meet the predefined standards and expectations. Metrics and KPIs can help to evaluate the efficiency, reliability, security, and quality of the IT systems and controls, and to identify any gaps, weaknesses, or issues that need to be addressed. Metrics and KPIs can also help to compare and benchmark the subsidiary’s IT systems and controls with those of the parent organization or other similar entities. The other options are not the best ways to measure the effectiveness of the subsidiary’s IT systems controls, although they may be useful or complementary methods. Implementing IT systems in alignment with business objectives is a good practice, but it does not measure the effectiveness of the IT systems controls, as it focuses on the alignment and integration of the IT systems with the business strategy and goals. Reviewing design documentation of IT systems can provide some information on the specifications and requirements of the IT systems, but it does not measure the effectiveness of the IT systems controls, as it does not reflect the actual implementation and operation of the IT systems. Evaluating compliance with legal and regulatory requirements can ensure that the subsidiary’s IT systems and controls meet the minimum standards and obligations of the foreign country, but it does not measure the effectiveness of the IT systems controls, as it does not consider the performance and outcomes of the IT systems and processes. References = Risk and Information Systems Control Study Manual, Chapter 5: Risk and Control Monitoring and Reporting, page 187.
When establishing leading indicators for the information security incident response process it is MOST important to consider the percentage of reported incidents:
that results in a full root cause analysis.
used for verification within the SLA.
that are verified as actual incidents.
resolved within the SLA.
When establishing leading indicators for the information security incident response process, it is most important to consider the percentage of reported incidents that are resolved within the service levelagreement (SLA). A leading indicator is a metric that can predict or influence the future performance or outcome of a process or activity. A leading indicator for the information security incident response process should measure how well the process is achieving its objectives, such as minimizing the impact of incidents, restoring normal operations as quickly as possible, and preventing recurrence of incidents. The percentage of reported incidents that are resolved within the SLA is a leading indicator that reflects the efficiency and effectiveness of the information security incident response process. It shows how well the process is meeting the expectations and requirements of the stakeholders, such as the business units, customers, and regulators. It also shows how well the process is managing the resources, such as time, budget, and personnel, that are allocated for incident response. A high percentage of reported incidents that are resolved within the SLA indicates that the information security incident response process is performing well and delivering value to the organization. A low percentage of reported incidents that are resolved within the SLA indicates that the information security incident response process is facing challenges and needs improvement. The percentage of reported incidents that are resolved within the SLA can also help identify the root causes of incidents, the gaps in the process, and the areas for improvement. For example, if the percentage of reported incidents that are resolved within the SLA is low, it may indicate that the process has issues with the following aspects: - Incident detection and reporting: The process may not have adequate tools, techniques, or procedures to detect and report incidents in a timely and accurate manner. - Incident prioritization and classification: The process may not have clear and consistent criteria to prioritize and classify incidents based on their severity, impact, and urgency. - Incident analysis and investigation: The process may not have sufficient skills, knowledge, or evidence to analyze and investigate the incidents and determine their root causes, scope, and consequences. - Incident containment and eradication: The process may not have effective methods or measures to contain and eradicate the incidents and prevent them from spreading or escalating. - Incident recovery and restoration: The process may not have reliable backup and recovery plans or systems to restore the normal operations and functionality of the affected systems or services. - Incident communication and escalation: The process may not have proper communication and escalation channels or protocols to inform and involve the relevant stakeholders, such as the management, the users, the vendors, or the authorities. - Incident documentation and closure: The process may not have adequate documentation and closure procedures to record and report the incidents and their resolution. - Incident review and improvement: The process may not have regular review and improvement activities to evaluate and enhance the process and its performance. Therefore, the percentage of reported incidents that are resolved within the SLA is the most important leading indicator for the information security incident response process, as it can provide valuable insights and feedback for the process and its improvement. References = Information Security Incident Response | Process Street1, Key Performance Indicators (KPIs) for Security Operations and Incident Response2, 7 Incident Response Metrics and How to Use Them3
An organization has four different projects competing for funding to reduce overall IT risk. Which project should management defer?
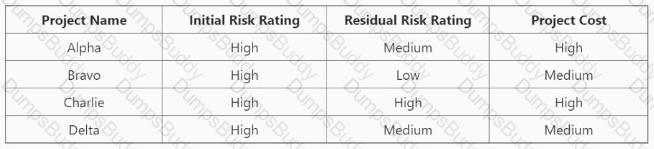
Project Charlie
Project Bravo
Project Alpha
Project Delta
Project Delta should be deferred by management, as it has the lowest return on investment (ROI) among the four competing projects. ROI is a measure of the profitability or efficiency of a project, calculated by dividing the net benefits by the total costs. Project Delta has a net benefit of $100,000 and a total cost of $200,000, resulting in an ROI of 0.5. The other projects have higher ROIs: Project Alpha has an ROI of 1.0, Project Bravo has an ROI of 0.8, and Project Charlie has an ROI of 0.6. Therefore, Project Delta is the least attractive option for reducing overall IT risk, and management should prioritize the other projects instead. References = How to Manage Project Risk: A 5-Step Guide; Matching the right projects with the right resources; Risk Types in Project Management
Which of the following should be the MAIN consideration when validating an organization's risk appetite?
Comparison against regulations
Maturity of the risk culture
Capacity to withstand loss
Cost of risk mitigation options
According to the Gaining the competitive edge – measuring and assessing an organization’s risk culture article, risk appetite is the amount and type of risk that an organization is willing to accept in pursuit of its objectives. Risk appetite should be aligned with the organization’s strategy, goals, and values, and should reflect the organization’s risk culture and capabilities. One of the main considerations when validating an organization’s risk appetite is the capacity to withstand loss, which is the ability of the organization to absorb the impact of adverse events without jeopardizing its viability or reputation. The capacity to withstand loss depends on various factors, such as the financial strength, the operational resilience, the governance structure, and the stakeholder expectations of the organization. By assessing the capacity to withstand loss, the organization can determine if its risk appetite is realistic and appropriate, or if it needs to be adjusted to match its risk profile and environment. References = Gaining the competitive edge – measuring and assessing an organization’s risk culture
Which of the following is the GREATEST concern associated with business end users developing their own applications on end user spreadsheets and database programs?
An IT project manager is not assigned to oversee development.
Controls are not applied to the applications.
There is a lack of technology recovery options.
The applications are not captured in the risk profile.
The GREATEST concern associated with business end users developing their own applications on end user spreadsheets and database programs is:
B. Controls are not applied to the applications.
When end users create their own applications, there is often a lack of formal controls that would typically be applied in a structured development environment. This can lead to issues with data integrity, security vulnerabilities, and non-compliance with organizational policies and standards.
The PRIMARY reason for periodically monitoring key risk indicators (KRIs) is to:
rectify errors in results of KRIs.
detect changes in the risk profile.
reduce costs of risk mitigation controls.
continually improve risk assessments.
The primary reason for periodically monitoring key risk indicators (KRIs) is to detect changes in the risk profile of the enterprise. KRIs are metrics that provide information on the level of exposure to a specific risk or a group of risks. By monitoring KRIs, the enterprise can identify any deviations from the expected risk level, and take appropriate actions to adjust the risk response or the risk appetite. Monitoring KRIs also helps to validate the effectiveness of risk mitigation controls and the accuracy of risk assessments. Rectifying errors in results of KRIs, reducing costs of risk mitigation controls, and continually improving risk assessments are possible benefits of monitoring KRIs, but they are not the primary reason. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 4, Section 4.1.1.2, page 175.
During an IT department reorganization, the manager of a risk mitigation action plan was replaced. The new manager has begun implementing a new control after identifying a more effective option. Which of the following is the risk practitioner's BEST course of action?
Communicate the decision to the risk owner for approval
Seek approval from the previous action plan manager.
Identify an owner for the new control.
Modify the action plan in the risk register.
A risk mitigation action plan is a document that specifies the actions to be taken to address the identified risks, the resources required, the timelines, the owners, and the expected outcomes. The risk owner is the person who has the authority and accountability to manage the risk and its response. The risk practitioner is the person who supports the risk owner in the risk management process. The best course of action for the risk practitioner when the manager of a risk mitigation action plan is replaced and a new control is implemented is to communicate the decision to the risk owner for approval. This will ensure that the risk owner is aware of the change, agrees with the new control, and approves the modification of the action plan. The other options are not the best course of action, as they may not involve the risk owner, who is ultimately responsible for the risk and its response. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 3, Section 3.1.1.1, pp. 95-96.
The PRIMARY benefit of classifying information assets is that it helps to:
communicate risk to senior management
assign risk ownership
facilitate internal audit
determine the appropriate level of control
Classifying information assets is a process of identifying and categorizing the data and information resources that are owned, controlled, or used by an organization, based on their value, sensitivity, and criticality.
Classifying information assets helps to determine the appropriate level of control that is needed to protect them from unauthorized access, use, disclosure, modification, or destruction. Control level refers to the degree of protection or assurance that a control provides against a risk.
Classifying information assets also helps to communicate risk to senior management, assign risk ownership, and facilitate internal audit. These are other benefits of risk management that are not directly related to determining the appropriate level of control.
The references for this answer are:
Risk IT Framework, page 11
Information Technology & Security, page 5
Risk Scenarios Starter Pack, page 3
A new policy has been published to forbid copying of data onto removable media. Which type of control has been implemented?
Preventive
Detective
Directive
Deterrent
A preventive control is a type of control that aims to avoid or reduce the occurrence of an undesirable event or risk. A preventive control can be implemented through technical, administrative, or physical means. A new policy that forbids copying of data onto removable media is an example of a preventive control, because it prevents unauthorized data exfiltration or leakage through removable devices, such as flash drives or external hard disk drives. A preventive control is different from the other types of controls, as explained below:
A detective control is a type of control that aims to discover or identify the occurrence of an undesirable event or risk. A detective control can be implemented through monitoring, auditing, or reporting activities. An example of a detective control is a log analysis tool that detects any unauthorized access or modification of data on a system.
A directive control is a type of control that aims to guide or instruct the behavior or actions of individuals or groups. A directive control can be implemented through policies, procedures, standards, or rules. An example of a directive control is a training program that teaches employees how to handle sensitive data securely and appropriately.
A deterrent control is a type of control that aims to discourage or dissuade individuals or groups from performing an undesirable event or risk. A deterrent control can be implemented through sanctions, penalties, or consequences. An example of a deterrent control is a warning message that informs users of the legal implications of copying data onto removable media without authorization. References = Risk and Information Systems Control Study Manual, Chapter 2, Section 2.2.1, page 38.
What is the MOST important consideration when aligning IT risk management with the enterprise risk management (ERM) framework?
Risk and control ownership
Senior management participation
Business unit support
Risk nomenclature and taxonomy
According to the CRISC Review Manual1, risk nomenclature and taxonomy is the set of terms and definitions that are used to describe and classify risks and their attributes. Risk nomenclature and taxonomy is the most important consideration when aligning IT risk management with the enterprise risk management (ERM) framework, as it helps to ensure a common and consistent understanding and communication of risks across the organization. Risk nomenclature and taxonomy also helps to integrate and harmonize the IT risk management processes and activities with the ERM framework, and to facilitatethe aggregation and reporting of risks at different levels of the organization. References = CRISC Review Manual1, page 197.
Which of the following BEST helps to identify significant events that could impact an organization?
Vulnerability analysis
Control analysis
Scenario analysis
Heat map analysis
Scenario analysis is a technique that helps to identify significant events that could impact an organization by creating and exploring plausible alternative futures. Scenario analysis can help anticipate and prepare for potential changes, opportunities, or threats in the internal or external environment, such as technological, economic, social, political, legal, or environmental factors. Scenario analysis can also help evaluate the impact and likelihood of different risk scenarios, and test the effectiveness and robustness of various risk response strategies. Scenario analysis can provide a comprehensive and holistic view of risks and their interrelationships, and support the decision making and planning process for risk management. References = Risk and Information Systems Control Study Manual, Chapter 1: IT Risk Identification, Section 1.4: IT Risk Scenarios, p. 49-50.
A PRIMARY function of the risk register is to provide supporting information for the development of an organization's risk:
strategy.
profile.
process.
map.
A primary function of the risk register is to provide supporting information for the development of an organization’s risk profile, which is a comprehensive and structured representation of the risks that the organization faces. The risk profile helps the organization to understand its risk exposure, appetite, and tolerance, and to align its risk management strategy with its business objectives and context. The risk register is a document that records and tracks the identified risks, their causes, impacts, likelihood, responses, owners, and status. The risk register is an essential input for creating and updating the risk profile, as it provides the data and analysis of the risks that need to be prioritized and addressed. The other options are not the primary function of the risk register, although they may be related to it. The risk strategy is the plan and approach for managing the risks, and it is based on the risk profile. The risk process is the set of activities and tasks for identifying, assessing, responding, and monitoring the risks, and it is facilitated by the risk register. The risk map is a graphical tool for displaying the risks based on their impact and likelihood, and it is derived from the risk register. References = Risk Register: A Project Manager’s Guide with Examples [2023] • Asana; Purpose of a risk register: Here’s what a risk register is used for; Risk Register: Definition, Importance, and Elements! - Bit Blog; What is a Risk Register? A Complete Guide | Capterra; Risk Registers: What Are They, When Should You Use Them, and Why?
An organization has completed a project to implement encryption on all databases that host customer data. Which of the following elements of the risk register should be updated the reflect this change?
Risk likelihood
Inherent risk
Risk appetite
Risk tolerance
The risk likelihood is the element of the risk register that should be updated to reflect the change of implementing encryption on all databases that host customer data. The risk likelihood is the probability or frequency of a risk event occurring, and it is one of the factors that determine the risk level and priority. By implementing encryption, the organization reduces the risk likelihood of unauthorized access, disclosure, or breach of the customer data, as encryption protects the data from being read or modified by anyone who does not have the decryption key. Therefore, the risk likelihood should be updated to reflect the lower probability of the risk event after applying the encryption control. The other options are not the elements that should be updated, as they are either not affected by or not related to the change of implementing encryption. The inherent risk is the level of risk before applying any controls or mitigation measures, and it does not change after implementing encryption. The risk appetite is the amount of risk that the organization is willing to accept in pursuit of its objectives, and it is not influenced by the change of implementing encryption. The risk tolerance is the acceptable variation between the risk thresholds and thebusiness objectives, and it is not determined by the change of implementing encryption. References = Risk Register: A Project Manager’s Guide with Examples [2023] • Asana; Risk Assessment in Project Management | PMI; Risk Assessment Process: Definition, Steps, and Examples; Risk Assessment - an overview | ScienceDirect Topics
An organization has decided to outsource a web application, and customer data will be stored in the vendor's public cloud. To protect customer data, it is MOST important to ensure which of the following?
The organization's incident response procedures have been updated.
The vendor stores the data in the same jurisdiction.
Administrative access is only held by the vendor.
The vendor's responsibilities are defined in the contract.
Outsourcing a web application and storing customer data in the vendor’s public cloud involves transferring some of the organization’s data processing and storage functions to a third-party service provider. This can bring benefits such as cost savings, scalability, and flexibility, but it also introduces risks such as data breaches, unauthorized access, compliance violations, and loss of control12.
To protect customer data, it is most important to ensure that the vendor’s responsibilities are defined in the contract. A contract is a legally binding agreement that specifies the terms and conditions of the outsourcing relationship, such as the scope, duration, quality, and cost of the services, as well as the rights and obligations of both parties. A contract should also address the following aspects of data protection :
Data ownership: The contract should clearly state that the organization retains the ownership and control of its customer data, and that the vendor has no rights to use, disclose, or retain the data for any purpose other than providing the agreed services.
Data security: The contract should define the minimum security standards and controls that the vendor must implement and maintain to protect the customer data from unauthorized or accidental access, use, disclosure, modification, or destruction. The contract should also specify the security certifications or audits that the vendor must comply with or undergo to demonstrate its security posture.
Data privacy: The contract should ensure that the vendor complies with the applicable data privacy laws and regulations that govern the collection, processing, and transfer of customer data, such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA). The contract should also require the vendor to obtain the consent of the customers before collecting or sharing their data, and to respect their rights to access, correct, delete, or restrict their data.
Data breach notification: The contract should establish the procedures and timelines for the vendor to notify the organization and the relevant authorities in the event of a data breach or security incident that affects the customer data. The contract should also define the roles and responsibilities of both parties in responding to and resolving the incident, as well as the remedies and penalties for the vendor’s failure or negligence.
Data backup and recovery: The contract should outline the backup and recovery policies and practices that the vendor must follow to ensure the availability and integrity of the customer data in case of a disaster or system failure. The contract should also specify the frequency and format of the backups, the location and security of the backup storage, and the testing and restoration procedures.
Data retention and disposal: The contract should stipulate the retention period and disposal method for the customer data, in accordance with the organization’s data retention policy and the legal or regulatory requirements. The contract should also require the vendor to return or destroy the customer data at the end of the contract or upon the organization’s request, and to provide proof of the data deletion.
By defining the vendor’s responsibilities in the contract, the organization can ensure that the customer data is protected in a consistent and compliant manner, and that the vendor is accountable and liable for any data protection issues or breaches that may arise from the outsourcing arrangement .
The other options are not as important as defining the vendor’s responsibilities in the contract, because they do not address the core issue of establishing a clear and enforceable data protection framework between the organization and the vendor. Updating the organization’s incident response procedures, which are the plans and actions to be taken in the event of a data breach or security incident, may help to mitigate the impact and consequences of such events, but it does not prevent or reduce the likelihood of them occurring in the first place. Storing the data in the same jurisdiction, which means keeping the data within the same geographic or legal boundaries as the organization, may help to avoid some of the data privacy and sovereignty challenges that arise from cross-border data transfers, but it does not guarantee the security and confidentiality of the data. Restricting the administrative access to the vendor, which means limiting the ability to view, modify, or delete the data to the vendor’s personnel only, may help to reduce the risk of unauthorized or accidental access by the organization’s staff, but it does not ensure that the vendor’s staff are trustworthy and competent, and it may also impair the organization’s oversight and control over the data.
References = Consumer data protection and privacy | McKinsey, 9 Tips for Protecting Consumer Data (& Why It’s Important to Keep It …, [Outsourcing Contracts: Key Issues and Best Practices], [Data Protection in Cloud Services: A Guide for Businesses], [Incident Response Planning: Best Practices for Businesses], [Data Localization: What is it and Why is it Important?], [Administrative Access: Definition, Risks, and Best Practices]
Which of the following IT key risk indicators (KRIs) provides management with the BEST feedback on IT capacity?
Trends in IT resource usage
Trends in IT maintenance costs
Increased resource availability
Increased number of incidents
IT capacity is the ability of an IT system or network to handle the current and future workload and performance demands. IT capacity can be affected by various factors, such as the number and type of users, applications, devices, data, transactions, etc. IT capacity management is the process of planning, monitoring, and optimizing the IT resources to ensure that they meet the business needs and objectives. IT capacity management can help prevent issues such as system slowdowns, outages, errors, or failures, and improve the efficiency, reliability, and security of the IT system or network. One of the IT key risk indicators (KRIs) that provides management with the best feedback on IT capacity is the trends in IT resource usage. IT resource usage is the measure of how much of the IT resources, such as CPU, memory, disk, bandwidth, etc., are being consumed by the IT system or network. Trends in IT resource usage can help monitor and analyze the changes in the IT capacity over time, and identify the patterns, peaks, and bottlenecks in the IT resource consumption. Trends in IT resource usage can also help forecast the future IT capacity requirements, and plan for the appropriate IT resource allocation, optimization, or expansion. Trends in IT resource usage can provide management with valuable information on the current and potential IT capacity risks, and support the decision making and risk response for IT capacity management. References = Integrating KRIs and KPIs for Effective Technology Risk Management, p. 3-4.
A risk owner should be the person accountable for:
the risk management process
managing controls.
implementing actions.
the business process.
A risk owner should be the person accountable for the business process that is affected by the risk, as they have the authority, responsibility, and knowledge to manage the risk effectively. The risk owner should collaborate with the risk practitioner, who facilitates the risk management process, and the risk action owners, who implement the risk response actions. The risk owner should also ensure that the controls are adequate and functioning properly to mitigate the risk. The other options are not the best description of what a risk owner should be accountable for, as they are either too broad (the risk management process), too narrow (managing controls or implementing actions), or not directly related to the risk (the business process). References = Why Assigning a Risk Owner is Important and How to Do It Right; Definition of Risk Owner; What Is a Risk Owner in Project Management?
Which of the following presents the GREATEST challenge for an IT risk practitioner who wants to report on trends in historical IT risk levels?
Qualitative measures for potential loss events
Changes in owners for identified IT risk scenarios
Changes in methods used to calculate probability
Frequent use of risk acceptance as a treatment option
Changes in methods used to calculate probability present the greatest challenge for an IT risk practitioner who wants to report on trends in historical IT risk levels, as they may introduce inconsistency and incomparability in the risk assessment results over time. Probability is a key factor in determining the level and priority of IT risks, and different methods may produce different values for the same risk scenario. For example, some methods may use historical data, expert judgment, or simulation techniques to estimate the likelihood of a risk event. If the methods used to calculate probability change frequently or vary across different business units or processes, the IT risk practitioner may face difficulty in aggregating, normalizing, and reporting the risk levels and trends. The other options are not the greatest challenges for reporting on trends in historical IT risk levels, although they may pose some difficulties or limitations. Qualitative measures for potential loss events are subjective and imprecise, but they can still provide a relative ranking of risks and their impacts. Changes in owners for identified IT risk scenarios may affect the accountability and responsibility for managing the risks, but they do not necessarily affect the risk levels or trends. Frequent use of risk acceptance as a treatment option may indicate a high risk appetite ortolerance, but it does not prevent the IT risk practitioner from reporting on the risk levels or trends. References = Risk and Information Systems Control Study Manual, Chapter 5: Risk and Control Monitoring and Reporting, page 181.
When preparing a risk status report for periodic review by senior management, it is MOST important to ensure the report includes
risk exposure in business terms
a detailed view of individual risk exposures
a summary of incidents that have impacted the organization.
recommendations by an independent risk assessor.
When preparing a risk status report for periodic review by senior management, it is most important to ensure the report includes risk exposure in business terms. Risk exposure is the potential loss or harm that may result from a risk event. Expressing risk exposure in business terms can help senior management to understand the impact and significance of the risk on the organization’s objectives, performance, and value. A detailed view of individual risk exposures, a summary of incidents that have impacted the organization, and recommendations by an independent risk assessor are other possible contents of the report, but they are not as important as risk exposure in business terms. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 10; CRISC Review Manual, 6th Edition, page 140.
Which of the following is the MOST important outcome of a business impact analysis (BIA)?
Understanding and prioritization of critical processes
Completion of the business continuity plan (BCP)
Identification of regulatory consequences
Reduction of security and business continuity threats
The most important outcome of a business impact analysis (BIA) is understanding and prioritization of critical processes. A BIA is a process that identifies and evaluates the potential effects of disruptions or disasters on the organization’s business functions and processes. A BIA helps to understand the dependencies, interrelationships, and impacts of the business processes, and to prioritize them based on their importance and urgency. A BIA also helps to determine the recovery objectives, strategies, and resources for the business processes, such as the recovery time objective (RTO), the recovery point objective (RPO), and the minimum operating requirements (MOR). The other options are not as important as understanding and prioritization of critical processes, although they may be part of or derived from the BIA. Completion of the business continuity plan (BCP), identification of regulatory consequences, and reduction of security and business continuity threats are all activities or outcomes that can be supported or facilitated by the BIA, but they are not the primary purpose or result of the BIA. References = CISA Review Manual, 27th Edition, Chapter 5, Section 5.2.1, page 5-9.
After the implementation of internal of Things (IoT) devices, new risk scenarios were identified. What is the PRIMARY reason to report this information to risk owners?
To reevaluate continued use to IoT devices
The add new controls to mitigate the risk
The recommend changes to the IoT policy
To confirm the impact to the risk profile
The primary reason to report the information about the new risk scenarios identified after the implementation of Internet of Things (IoT) devices to risk owners is to confirm the impact to the risk profile. The risk profile is a summary of the level and nature of the risks that the organization faces or may face in the future. The risk profile reflects the risk appetite, tolerance, and capacity of the organization, and guides the risk management decisions and actions. The implementation of IoT devices may introduce new risks or increase the likelihood or impact of existing risks, such as data privacy, security, or interoperability issues. Therefore, the information about the new risk scenarios should be reported to the risk owners, who have the authority and responsibility for managing the risks and their responses, to confirm the impact to the risk profile and to determine the appropriate risk treatment plans. The other options are not as primary as confirming the impact to the risk profile, as they are related to the reevaluation, mitigation, or recommendation of the IoT devices, not the confirmation or assessment of the risk profile. References = Risk and Information Systems Control Study Manual, Chapter 1: IT Risk Identification, Section 1.2: IT Risk Register, page 19.
Which of the following is the BEST method to maintain a common view of IT risk within an organization?
Collecting data for IT risk assessment
Establishing and communicating the IT risk profile
Utilizing a balanced scorecard
Performing and publishing an IT risk analysis
The best method to maintain a common view of IT risk within an organization is to establish and communicate the IT risk profile. An IT risk profile is a document that summarizes the key IT risks that the organization faces or accepts, and their likelihood, impact, and priority. An IT risk profile helps to identify and prioritize the most critical or relevant IT risks, and to align them with the organization’s objectives, strategy, and risk appetite. Establishing and communicating the IT risk profile is the best method to maintain a common view of IT risk, because it helps to create a shared understanding and awareness of the IT risks among the organization’s stakeholders, such as the board, management, business units, and IT functions. Establishing and communicating the IT risk profile also helps to facilitate the IT risk decision-making and reporting processes, and to monitor and control the IT risk performance and improvement. Theother options are not the best method to maintain a common view of IT risk, although they may be part of or derived from the IT risk profile. Collecting data for IT risk assessment, utilizing a balanced scorecard, and performing and publishing an IT risk analysis are all activities that can help to support or update the IT risk profile, but they are not the best method to maintain a common view of IT risk. References = Risk and Information Systems Control Study Manual, Chapter 1, Section 1.3.1, page 1-15.
Which of the following is MOST helpful in providing a high-level overview of current IT risk severity*?
Risk mitigation plans
heat map
Risk appetite statement
Key risk indicators (KRls)
A heat map is a graphical tool that displays the level of risk severity for various risk scenarios or categories using different colors, shapes, or sizes. A heat map is most helpful in providing a high-level overview of current IT risk severity, as it can show the relative importance and urgency of the risks, and highlight the areas that require attention or action. A heat map can also help to communicate the risk information to the stakeholders, and facilitate the risk prioritization and decision making. References = 5
A segregation of duties control was found to be ineffective because it did not account for all applicable functions when evaluating access. Who is responsible for ensuring the control is designed to effectively address risk?
Risk manager
Control owner
Control tester
Risk owner
The control owner is the person who is responsible for ensuring that the control is designed to effectively address risk. The control owner is also responsible for implementing, operating, monitoring, and maintaining the control. The control owner should ensure that the control is aligned with the risk owner’s risk appetite and tolerance, and that the control is periodically reviewed and updated to reflect changes in the risk environment. The risk manager, the control tester, and the risk owner are not directly responsible for the design of the control, although they may provide input, feedback, or approval. References = Risk and Information Systems Control Study Manual, Chapter 1, Section 1.3.2, page 1-15.
Which of the following should be of GREATEST concern when reviewing the results of an independent control assessment to determine the effectiveness of a vendor's control environment?
The report was provided directly from the vendor.
The risk associated with multiple control gaps was accepted.
The control owners disagreed with the auditor's recommendations.
The controls had recurring noncompliance.
The most concerning issue when reviewing the results of an independent control assessment to determine the effectiveness of a vendor’s control environment is that the controls had recurring noncompliance. This indicates that the vendor’s controls are not operating as intended or designed, and that the vendor is not taking corrective actions to address the control deficiencies. This can increase the risk exposure and liability for the organization that outsources the service or function to the vendor. The report being provideddirectly from the vendor, the risk associated with multiple control gaps being accepted, and the control owners disagreeing with the auditor’s recommendations are other possible issues, but they are not as critical as the recurring noncompliance. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 11; CRISC Review Manual, 6th Edition, page 144.
Which of the following is MOST important to promoting a risk-aware culture?
Regular testing of risk controls
Communication of audit findings
Procedures for security monitoring
Open communication of risk reporting
Open communication of risk reporting is the most important factor for promoting a risk-aware culture, because it fosters trust, transparency, and accountability among all stakeholders. It also enables timely and informed decision-making, feedback, and learning from risk events. Regular testing of risk controls, communication of audit findings, and procedures for security monitoring are all important aspects of risk management, but they do not necessarily create a risk-aware culture, which requires a shared understanding and commitment to risk management across the organization. References = Risk and Information Systems Control Study Manual, Chapter 1, Section 1.2.2, page 1-9.
Which of the following would be the BEST way for a risk practitioner to validate the effectiveness of a patching program?
Conduct penetration testing.
Interview IT operations personnel.
Conduct vulnerability scans.
Review change control board documentation.
Conducting vulnerability scans is the best way for a risk practitioner to validate the effectiveness of a patching program. Vulnerability scans are automated tools that identify and report on the vulnerabilities in a system or network, such as missing patches, misconfigurations, or outdated software. Vulnerability scans can help the risk practitioner to verify that the patches have been applied correctly and consistently, and that there are no remaining or new vulnerabilities that need to be addressed. Conducting penetration testing, interviewing IT operations personnel, and reviewing change control board documentation are also useful methods to evaluate the patching program, but they are not as comprehensive, objective, or timely as vulnerability scans. References = Risk and Information Systems Control Study Manual, Chapter 2, Section 2.3.3, page 2-28.
An unauthorized individual has socially engineered entry into an organization's secured physical premises. Which of the following is the BEST way to prevent future occurrences?
Employ security guards.
Conduct security awareness training.
Install security cameras.
Require security access badges.
Social engineering is a technique that involves manipulating or deceiving people into performing actions or divulging information that may compromise the security of an organization or its data12.
Entry into an organization’s secured physical premises is a form of physical access that allows an unauthorized individual to access, steal, or damage the organization’s assets, such as equipment, documents, or systems34.
The best way to prevent future occurrences of social engineering entry into an organization’s secured physical premises is to conduct security awareness training, which is an educational program that aims to equip the organization’s employees with the knowledge and skills they need to protect the organization’s data and sensitive information from cyber threats, such as hacking, phishing, or other breaches56.
Security awareness training is the best way because it helps the employees to recognize and resist the common and emerging social engineering techniques, such as tailgating, impersonation, or pretexting, that may be used by the attackers to gain physical access to the organization’s premises56.
Security awareness training is also the best way because it fosters a culture of security and responsibility among the employees, and encourages them to follow the best practices and policies for physical security, such as locking the doors, verifying the identity of visitors, or reporting any suspicious activities or incidents56.
The other options are not the best way, but rather possible measures or controls that may supplement or enhance the security awareness training. For example:
Employing security guards is a measure that involves hiring or contracting professional personnel who are trained and authorized to monitor, patrol, and protect the organization’s premises from unauthorized access or intrusion78. However, this measure is not the best way because it may not be sufficient or effective to prevent or deter all types of social engineering attacks, especially if the attackers are able to bypass, deceive, or coerce the security guards78.
Installing security cameras is a control that involves using electronic devices that capture and record the visual images of the organization’s premises, and provide evidence or alerts of any unauthorized access or activity . However, this control is not the best way because it is reactive rather than proactive, and may not prevent or stop the social engineering attacks before they cause any harm or damage to the organization .
Requiring security access badges is a control that involves using physical or electronic cards that identify and authenticate the employees or authorized visitors who are allowed to enter the organization’s premises, and restrict or deny the access to anyone else . However, this control is not the best way because it may not be foolproof or reliable to prevent or detect the social engineering attacks, especially if the attackers are able to steal, forge, or clone the security access badges . References =
1: What is Social Engineering? | Types & Examples of Social Engineering Attacks1
2: Social Engineering: What It Is and How to Prevent It | Digital Guardian2
3: What is physical Social Engineering and why is it important? - Integrity3603
4: What Is Tailgating (Piggybacking) In Cyber Security? - Wlan Labs4
5: What Is Security Awareness Training and Why Is It Important? - Kaspersky5
6: Security Awareness Training - Cybersecurity Education Online | Proofpoint US6
7: Security Guard - Wikipedia7
8: Security Guard Services - Allied Universal8
Security Camera - Wikipedia
Security Camera Systems - The Home Depot
Access Badge - Wikipedia
Access Control Systems - HID Global
Which of the following is the FIRST step in managing the risk associated with the leakage of confidential data?
Maintain and review the classified data inventor.
Implement mandatory encryption on data
Conduct an awareness program for data owners and users.
Define and implement a data classification policy
The risk associated with the leakage of confidential data is the possibility and impact of unauthorized disclosure, access, or use of sensitive information that may harm the organization or its stakeholders12.
The first step in managing the risk associated with the leakage of confidential data is to define and implement a data classification policy, which is a document that establishes the criteria, categories, roles, and responsibilities for identifying, labeling, and handling different types of data according to their sensitivity, value, and protection needs34.
Defining and implementing a data classification policy is the first step because it provides the foundation and framework for the data protection strategy, and enables the organization to prioritize and allocate the appropriate resources and controls for the most critical and confidential data34.
Defining and implementing a data classification policy is also the first step because it supports the compliance with the relevant laws and regulations, such as GDPR, HIPAA, or PCI-DSS, that require the organization to classify and protect the personal or financial data of its customers or clients34.
The other options are not the first step, but rather possible subsequent steps that may depend on or follow the data classification policy. For example:
Maintaining and reviewing the classified data inventory is a step that involves creating and updating a record of the data assets that have been classified, and verifying their accuracy and completeness over time34. However, this step is not the first step because it requires the data classification policy to provide the guidance and standards for the data inventory process34.
Implementing mandatory encryption on data is a step that involves applying a cryptographic technique that transforms the data into an unreadable format, and requires a key or a password to decrypt and access the data56. However, this step is not the first step because it requires the data classification policy to determine which data needs to be encrypted, and what level of encryption is appropriate56.
Conducting an awareness program for data owners and users is a step that involves educating and training the people who are responsible for or have access to the data, and informing them of their roles, obligations, and best practices for data protection78. However, this step is not the first step because it requires the data classification policy to define the data ownership and user rights, and the data protection policies and procedures78. References =
1: Top Four Damaging Consequences of Data Leakage | ZeroFox1
2: 8 Data Leak Prevention Strategies for 2023 | UpGuard2
3: Data Classification: What It Is, Why You Need It, and How to Do It3
4: Data Classification Policy Template - IT Governance USA4
5: Encryption: What It Is, How It Works, and Why You Need It5
6: Encryption Policy Template - IT Governance USA6
7: What Is Security Awareness Training and Why Is It Important? - Kaspersky7
8: Security Awareness Training - Cybersecurity Education Online | Proofpoint US8
Which of the following should be a risk practitioner's NEXT step upon learning the impact of an organization's noncompliance with a specific legal regulation?
Identify risk response options.
Implement compensating controls.
Invoke the incident response plan.
Document the penalties for noncompliance.
Detailed Explanation:The next step is toidentify risk response optionsto address the noncompliance and mitigate its impact. This may include corrective actions, implementing controls, or negotiating terms to reduce exposure.
Which of the following is MOST important to consider before determining a response to a vulnerability?
The likelihood and impact of threat events
The cost to implement the risk response
Lack of data to measure threat events
Monetary value of the asset
A vulnerability is a weakness or flaw in the IT system or environment that could be exploited by a threat. A threat event is an occurrence or action that exploits a vulnerability and causes harm or damage to the IT system or environment. The lack of data to measure threat events is the most important factor, because it may affect the accuracy and reliability of the risk assessment and evaluation, and consequently, the risk response and strategy. The lack of data to measure threat events may also create challenges or risks for the organization, such as compliance, legal, reputational, or operational risks, or conflicts or inconsistencies with the organization’s risk appetite, risk objectives, or risk policies. The other options are not as important as the lack of data to measure threat events, although they may also influence the risk response and strategy. The likelihood and impact of threat events, the cost to implement the risk response, and the monetary value of the asset are all factors that could affect the feasibility and sustainability of the risk response and strategy, but they do not necessarily affect the validity and quality of the risk assessment and evaluation
Which of the following is the BEST method to mitigate the risk of an unauthorized employee viewing confidential data in a database''
Implement role-based access control
Implement a data masking process
Include sanctions in nondisclosure agreements (NDAs)
Install a data loss prevention (DLP) tool
Implementing a data masking process is the best method to mitigate the risk of an unauthorized employee viewing confidential data in a database. Data masking is the process of replacing sensitive data with fictitious but realistic data, such as changing names, addresses, phone numbers, etc. Data masking protects the privacy and confidentiality of the data, while still allowing for testing, analysis, or training purposes. Implementing role-based access control, including sanctions in NDAs, and installing a DLP tool are also useful methods to reduce the risk of data exposure, but they are not as effective as data masking, which prevents the data from being accessed in the first place. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.3.1, page 3-21.
Which of the following findings of a security awareness program assessment would cause the GREATEST concern to a risk practitioner?
The program has not decreased threat counts.
The program has not considered business impact.
The program has been significantly revised
The program uses non-customized training modules.
The greatest concern for a risk practitioner when reviewing the findings of a security awareness program assessment is that the program uses non-customized training modules. Non-customized training modules are generic and may not address the specific security needs, issues, and challenges of the organization. They may also fail to engage and motivate the employees to follow the security policies and procedures, and to enhance their security knowledge and skills. The program not decreasing threat counts, not considering business impact, or being significantly revised are other possible findings, but they are not as concerning as the program using non-customized training modules. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 7; CRISC Review Manual, 6th Edition, page 202.
An organization is implementing robotic process automation (RPA) to streamline business processes. Given that implementation of this technology is expected to impact existing controls, which of the following is the risk practitioner's BEST course of action?
Reassess whether mitigating controls address the known risk in the processes.
Update processes to address the new technology.
Update the data governance policy to address the new technology.
Perform a gap analysis of the impacted processes.
Robotic process automation (RPA) is the use of software robots or artificial intelligence (AI) agents to automate repetitive, rule-based tasks that are normally performed by humans. RPA can improve efficiency, accuracy, and scalability of business processes, but it can also introduce new risks or change the existing risk profile. Therefore, the risk practitioner’s best course of action is to reassess whether the mitigating controls that were designed for the human-performed processes are still effective and adequate for the RPA-enabled processes. This may involve reviewing the control objectives, testing the control performance, identifying the control gaps, and recommending the control enhancements or modifications. References = CRISC Review Manual, 7th Edition, page 177.
Which of the following key performance indicators (KPis) would BEST measure me risk of a service outage when using a Software as a Service (SaaS) vendors
Frequency of business continuity plan (BCP) lasting
Frequency and number of new software releases
Frequency and duration of unplanned downtime
Number of IT support staff available after business hours
Software as a Service (SaaS) is a cloud computing model that provides software applications over the internet, without requiring the users to install or maintain them on their own devices. SaaS vendors are responsible for hosting, managing, and updating the software applications, and providing technical support and security to the users. The key performance indicator (KPI) that would best measure the risk of a service outage when using a SaaS vendor is the frequency and duration of unplanned downtime, which is the amount and length of time that the software applications are unavailable or inaccessible due to unexpected events, such as network failures, server crashes, power outages, cyberattacks, etc. The frequency and duration of unplanned downtime indicate the reliability and availability of the SaaS vendor, and the potential impact of the service outage on the users’ business operations and productivity. References = 3
An organization has agreed to a 99% availability for its online services and will not accept availability that falls below 98.5%. This is an example of:
risk mitigation.
risk evaluation.
risk appetite.
risk tolerance.
Risk tolerance is the best term to describe the situation where an organization has agreed to a 99% availability for its online services and will not accept availability that falls below 98.5%. Risk tolerance is the amount and type of risk that an organization is willing to accept in order to achieve its objectives. Risk tolerance defines the acceptable variation in outcomes related to specific performance measures, such as availability, reliability, or security. Risk tolerance is usually expressed as a range, such as 99% +/- 0.5%. Risk mitigation, risk evaluation, and risk appetite are not the correct terms to describe this situation, because they refer to different aspects of risk management, such as reducing, assessing, or pursuing risk, respectively. References = Risk and Information Systems Control Study Manual, Chapter 1, Section 1.2.1, page 1-8.
An organization retains footage from its data center security camera for 30 days when the policy requires 90-day retention The business owner challenges whether the situation is worth remediating Which of the following is the risk manager s BEST response'
Identify the regulatory bodies that may highlight this gap
Highlight news articles about data breaches
Evaluate the risk as a measure of probable loss
Verify if competitors comply with a similar policy
A risk is the possibility of an event that may have a negative impact on the achievement of an organization’s objectives. A risk can be measured by the probability and impact of the event, which indicate the likelihood and consequence of the event. A risk manager is a person who is responsible for performing risk management activities, such as identifying, analyzing, evaluating, treating, monitoring, and communicating risks. When an organization retains footage from its data center security camera for 30 days when the policy requires 90-day retention, the risk manager’s best response to the business owner who challenges whether the situation is worth remediating is to evaluate the risk as a measure of probable loss, which means to estimate the potential harm or damage that may result from the non-compliance with the policy. By evaluating the risk as a measure of probable loss, the risk manager can provide the business owner with the rationale and justification for the risk remediation, and help the business owner to understand the cost-benefit analysis of the risk response. References = CRISC Review Manual, 7th Edition, page 63.
Which of the following would MOST effectively reduce the potential for inappropriate exposure of vulnerabilities documented in an organization's risk register?
Limit access to senior management only.
Encrypt the risk register.
Implement role-based access.
Require users to sign a confidentiality agreement.
A risk register is a document that contains information about potential cybersecurity risks that could threaten a project’s success, or even the business itself2. Therefore, it is important to protect the confidentiality and integrity of the risk register from unauthorized or inappropriate access, modification, or disclosure. One way to do this is to implement role-based access, which is a method of restricting access to the risk register based on the roles or responsibilities of the users1. This way, only authorized users who need to view or edit the risk register for legitimate purposes can do so, and the access rights can be revoked or modified as needed. This would most effectively reduce the potential for inappropriate exposure of vulnerabilities documented in the risk register. The other options are not as effective or feasible as option C, as they do not address the need to balance the security and availability of the risk register. Option A, limiting access to senior management only, would compromise the availability and usefulness of the risk register, as other stakeholders such as project managers, risk owners, or auditors may need to access the risk register for risk identification, analysis, response, or monitoring purposes3. Option B, encrypting the risk register, would enhance the security of the risk register, but it would not prevent authorized users from exposing the vulnerabilities to unauthorized parties, either intentionally or unintentionally. Encryption also adds complexity and cost to the risk register management process, and may affect the performance or usability of the risk register4. Option D, requiring users to sign a confidentiality agreement, would rely on the compliance and ethics of the users, but it would not prevent or detect any breaches of the agreement. A confidentiality agreement also does not specify the access rights or roles of the users, and may not be legally enforceable in some cases5.
The MOST important objective of information security controls is to:
Identify threats and vulnerability
Ensure alignment with industry standards
Provide measurable risk reduction
Enforce strong security solutions
The most important objective of information security controls is to provide measurable risk reduction. Information security controls are the policies, procedures, techniques, or technologies that are implemented to protect the confidentiality, integrity, and availability of information assets. The main purpose of information security controls is to reduce the risk of unauthorized access, use, disclosure,modification, or destruction of information assets, and to ensure that the information assets support the enterprise’s objectives and performance. Information security controls should be measurable, meaning that they should have clear and quantifiable criteria for evaluating their effectiveness and efficiency in reducing the risk exposure to an acceptable level. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 3, Section 3.1.1, page 1151
Which of the following should be the MOST important consideration when performing a vendor risk assessment?
Results of the last risk assessment of the vendor
Inherent risk of the business process supported by the vendor
Risk tolerance of the vendor
Length of time since the last risk assessment of the vendor
The most important consideration when performing a vendor risk assessment is the inherent risk of the business process supported by the vendor, which is the risk that exists before any controls or mitigating factors are applied. The inherent risk reflects the potential impact and likelihood of the vendor’s failure or disruption on the enterprise’s objectives, operations, and reputation. The higher the inherent risk, the more rigorous and frequent the vendor risk assessment should be. The results of the last risk assessment of the vendor, the risk tolerance of the vendor, and the length of time since the last risk assessment of the vendor are not the most important considerations, as they do not directly measure the level of exposure and dependency that the enterprise has on the vendor. References = CRISC Certified in Risk and Information Systems Control – Question204; ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 204.
Which of the following should be the GREATEST concern for an organization that uses open source software applications?
Lack of organizational policy regarding open source software
Lack of reliability associated with the use of open source software
Lack of monitoring over installation of open source software in the organization
Lack of professional support for open source software
Lack of organizational policy regarding open source software should be the greatest concern for an organization that uses open source software applications, as it may expose the organization to legal, security, and operational risks. Open source software is software that is freely available and can be modified and distributed by anyone, subject to certain conditions and licenses. An organizational policy regarding open source software should define the criteria and procedures for selecting, acquiring, using, and maintaining open source software, as well as the roles and responsibilities of the stakeholders involved. Lack of reliability, lack of monitoring, and lack of professional support are not the greatest concerns, as they can be addressed by implementing quality assurance, configuration management, and community engagement practices for open source software. References = CRISC by Isaca Actual Free Exam Q&As, question 214; CRISC: Certified in Risk & Information Systems Control Sample Questions, question 214.
Which of the following BEST balances the costs and benefits of managing IT risk*?
Prioritizing and addressing risk in line with risk appetite. Eliminating risk through preventive and detective controls
Considering risk that can be shared with a third party
Evaluating the probability and impact of risk scenarios
Risk appetite is the broad-based amount of risk that an organization is willing to accept in its activities. Risk appetite reflects the level of risk that the organization is prepared to take to achieve its strategic goals, and provides guidance and boundaries for the risk management activities and decisions. The best way to balance the costs and benefits of managing IT risk is to prioritize and address risk in line with risk appetite, which means that the organization should identify, assess, treat, monitor, and communicate the risks that are within or exceed the risk appetite, and allocate the resources and efforts accordingly. By doing so, the organization can optimize its risk-return trade-off, align its risk exposure with its strategic objectives, and enhance its risk culture and performance. References = 5
A migration from an in-house developed system to an external cloud-based solution is affecting a previously rated key risk scenario related to payroll processing. Which part of the risk register should be updated FIRST?
Payroll system risk factors
Payroll system risk mitigation plans
Payroll process owner
Payroll administrative controls
Payroll system risk mitigation plans are the actions that are taken to reduce or eliminate the risk associated with payroll processing. When a migration from an in-house developed system to an external cloud-based solution is affecting a previously rated key risk scenario related to payroll processing, the first part of the risk register that should be updated is the payroll system risk mitigation plans. This is because the migration may introduce new risks or change the existing risks, and the risk mitigation plans may need to be revised or replaced accordingly. Updating the payroll system risk mitigation plans can help ensure that the risk level is acceptable and the payroll process is secure and reliable. According to the CRISC Review Manual 2022, one of the key risk treatment techniques is to update the risk action plan, which is a document that outlines the risk mitigation plans1. According to the CRISC Review Questions, Answers & Explanations Manual 2022, updating the risk mitigation plans is the correct answer to this question2.
Payroll system risk factors, payroll process owner, and payroll administrative controls are not the first part of the risk register that should be updated when a migration is affecting a key risk scenario. Payroll system risk factors are the sources or causes of risk, such as threats, vulnerabilities, or uncertainties. Payroll process owner is the person who is responsible for the payroll process and its outcomes. Payroll administrative controls are the policies, procedures, or guidelines that govern the payroll process. These parts of the risk register may also need to be updated, but they are not as urgent or critical as the risk mitigation plans. Updating the risk factors, process owner, and administrative controls can help identify, assess, and monitor the risk, but they do not directly address the risk response. The risk response is the most important part of the risk management process, as it determines how the risk is handled and controlled.
Which of the following is the PRIMARY benefit of using a risk profile?
It promotes a security-aware culture.
It enables vulnerability analysis.
It enhances internal risk reporting.
It provides risk information to auditors.
A risk profile consolidates information about risks across the enterprise, enhancing internal reporting and facilitating informed decision-making. This aligns withRisk Governanceobjectives by providing a comprehensive view of risk for management and stakeholders.
Which of the following situations presents the GREATEST challenge to creating a comprehensive IT risk profile of an organization?
Manual vulnerability scanning processes
Organizational reliance on third-party service providers
Inaccurate documentation of enterprise architecture (EA)
Risk-averse organizational risk appetite
The situation that presents the greatest challenge to creating a comprehensive IT risk profile of an organization is having inaccurate documentation of enterprise architecture (EA). EA is the blueprint that describes the structure and operation of an organization, including its business processes, information systems, technology infrastructure, and governance. EA helps to align the IT strategy and objectives with the business strategy and objectives, and to identify and manage the IT risks and opportunities. Having inaccurate documentation of EA could lead to incomplete, inconsistent, or misleading information about the organization’s IT environment, which could affect the quality and reliability of the IT risk profile. The other situations are not as challenging as having inaccurate documentation of EA, although they may also pose some difficulties or limitations for the IT risk profile. References = Risk and Information Systems Control Study Manual, Chapter 2, Section 2.2.1, page 2-12.
Which of the following would BEST mitigate an identified risk scenario?
Conducting awareness training
Executing a risk response plan
Establishing an organization's risk tolerance
Performing periodic audits
The best way to mitigate an identified risk scenario is to execute a risk response plan. A risk response plan is a document that describes the actions and resources that are needed to address the risk scenario. A risk response plan can include one or more of the following strategies: avoid, transfer, mitigate, accept, or exploit. By executing a risk response plan, the organization can reduce the likelihood and/or impact of the risk scenario, or take advantage of the opportunities that the risk scenario may present. The other options are not as effective as executing a risk response plan, as they are related to the awareness, assessment, or monitoring of the risk scenario, not the actual treatment of the risk scenario. References = Risk and Information Systems Control Study Manual, Chapter 3: IT Risk Response, Section 3.2: IT Risk Response Options, page 133.
A risk practitioner has collaborated with subject matter experts from the IT department to develop a large list of potential key risk indicators (KRIs) for all IT operations within theorganization of the following, who should review the completed list and select the appropriate KRIs for implementation?
IT security managers
IT control owners
IT auditors
IT risk owners
IT risk owners are the most appropriate people to review the completed list of potential key risk indicators (KRIs) and select the ones that should be implemented. IT risk owners are the individuals who have the authority and accountability to manage the IT risks within their scope of responsibility. They are also responsible for defining the risk appetite, tolerance, and thresholds for their IT operations, and for ensuring that the KRIs are aligned with the business objectives and risk management strategy. IT security managers, IT control owners, and IT auditors are also involved in the risk management process, but they do not have the same level of authority and accountability as IT risk owners, and they may have different perspectives and priorities on the selection of KRIs. References = Risk and Information Systems Control Study Manual, Chapter 1, Section 1.3.1, page 1-13.
An organization has recently hired a large number of part-time employees. During the annual audit, it was discovered that many user IDs and passwords were documented in procedure manuals for use by the part-time employees. Which of the following BEST describes this situation?
Threat
Risk
Vulnerability
Policy violation
Documenting user IDs and passwords in procedure manuals is a vulnerability that exposes the organization to unauthorized access, data breaches, and other security risks. A vulnerability is a weakness or flaw in a system, process, or control that can be exploited by a threat. A threat is a potential cause of an unwanted incident that may harm the system or organization. A risk is the combination of the likelihood and impact of a threat exploiting a vulnerability. A policy violation is an act of non-compliance with a rule or standard that is established by the organization. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 8; CRISC Review Manual, 6th Edition, page 67.
Which of the following should be used as the PRIMARY basis for evaluating the state of an organization's cloud computing environment against leading practices?
The cloud environment's capability maturity model
The cloud environment's risk register
The cloud computing architecture
The organization's strategic plans for cloud computing
Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources that can be rapidly provisioned and released with minimal management effort or service provider interaction. The cloud computing architecture is the structure and design of the cloud environment, which includes the components, services, interfaces, standards, and configurations. The cloud computing architecture should be used as the primary basis for evaluating the state of an organization’s cloud computing environment against leading practices, as it determines the performance, security, reliability, scalability, and interoperability of the cloud services. By comparing the cloud computing architecture with the best practices and benchmarks in the industry, an organization can identify the gaps and weaknesses in the cloud environment and implement the necessary improvements and controls. References = CRISC Review Manual, 7th Edition, page 156.
A recent vulnerability assessment of a web-facing application revealed several weaknesses. Which of the following should be done NEXT to determine the risk exposure?
Code review
Penetration test
Gap assessment
Business impact analysis (BIA)
The next step to determine the risk exposure after a vulnerability assessment of a web-facing application is to perform a penetration test. A penetration test is a simulated attack on the application to exploit the identified vulnerabilities and measure the potential impact and likelihood of a successful breach. A penetration test can help to quantify and prioritize the risks associated with the web-facing application. Code review, gap assessment, and business impact analysis (BIA) are other possible steps, but they are not as effective as a penetration test. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 7; CRISC Review Manual, 6th Edition, page 202.
Which of the following is the BEST approach for obtaining management buy-in
to implement additional IT controls?
List requirements based on a commonly accepted IT risk management framework.
Provide information on new governance, risk, and compliance (GRC) platform functionalities.
Describe IT risk impact on organizational processes in monetary terms.
Present new key risk indicators (KRIs) based on industry benchmarks.
Presenting the impact of IT risks on organizational processes in monetary terms is effective for obtaining management buy-in because it directly relates to the organization's financial health and decision-making. It provides a clear and tangible understanding of the potential financial implications of risks, making it easier for management to appreciate the need for additional controls.
Before assigning sensitivity levels to information it is MOST important to:
define recovery time objectives (RTOs).
define the information classification policy
conduct a sensitivity analyse
Identify information custodians
Before assigning sensitivity levels to information, it is most important to define the information classification policy. The information classification policy is a document that establishes the criteria, categories, roles, responsibilities, and procedures for classifying information according to its sensitivity, value, and criticality. The information classification policy provides the basis, guidance, and consistency for assigning sensitivity levels to information, and ensures that the information is protected and handled appropriately. The other options are not as important as defining the information classification policy, as they are related to the specific steps, activities, or outputs of the information classification process, not the overall structure and quality of the information classification process. References = Risk and Information Systems Control Study Manual, Chapter 4: Risk and Control Monitoring and Reporting, Section 4.4: Key Control Indicators, page 211.
A MAJOR advantage of using key risk indicators (KRIs) is that they:
Identify scenarios that exceed defined risk appetite.
Help with internal control assessments concerning risk appetite.
Assess risk scenarios that exceed defined thresholds.
Identify when risk exceeds defined thresholds.
KRIs provide measurable indicators that flag when risks exceed predefined thresholds, enabling swift and effective risk response. This supports theMonitoring and Reportingfunction in risk management, ensuring risks are managed proactively.
Which of the following is the BEST approach to mitigate the risk associated with a control deficiency?
Perform a business case analysis
Implement compensating controls.
Conduct a control sell-assessment (CSA)
Build a provision for risk
The best approach to mitigate the risk associated with a control deficiency is to implement compensating controls. A control deficiency is a situation where a control is missing, ineffective, or inefficient, and cannot provide reasonable assurance that the objectives or requirements are met. A compensating control is a control that provides an alternative or additional measure of protection when the primary or preferred control is not feasible or effective. A compensating control can help to reduce the likelihood and/or impact of the risk associated with the control deficiency, and maintain the compliance or performance level. The other options are not as effective as implementing compensating controls, as they are related to the analysis, assessment, or provision of the risk, not the mitigation of the risk. References = Risk and Information Systems Control Study Manual, Chapter 3: IT Risk Response, Section 3.3: IT Risk Response Implementation, page 145.
Which of the following is the MAIN purpose of monitoring risk?
Communication
Risk analysis
Decision support
Benchmarking
The main purpose of monitoring risk is to provide decision support for the organization. Risk monitoring is the process of tracking and reviewing the risk management activities, the risk profile, and the risk performance of the organization. By monitoring risk, the organization can obtain timely and relevant information and feedback on the risk situation, and use it to make informed and effective decisions on risk management and business objectives. Communication, risk analysis, and benchmarking are other possible purposes of risk monitoring, but they are not as important as decision support. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 12; CRISC Review Manual, 6th Edition, page 215.
During an acquisition, which of the following would provide the MOST useful input to the parent company's risk practitioner when developing risk scenarios for the post-acquisition phase?
Risk management framework adopted by each company
Risk registers of both companies
IT balanced scorecard of each company
Most recent internal audit findings from both companies
The most useful input to the parent company’s risk practitioner when developing risk scenarios for the post-acquisition phase is the risk registers of both companies. The risk register is a document that records the details of the risks, such as their sources, causes, consequences, likelihood, impact, and responses. By reviewing the risk registers of both companies, the risk practitioner can identify the existing and potential risks that may affect the post-acquisition integration, performance, and value. The risk management framework, the IT balanced scorecard, and the most recent internal audit findings are other possible inputs, but they are not as useful as the risk registers. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 11; CRISC Review Manual, 6th Edition, page 144.
Reviewing which of the following BEST helps an organization gam insight into its overall risk profile''
Risk register
Risk appetite
Threat landscape
Risk metrics
A risk register is a tool that records and tracks the information about the identified risks, such as the risk description, category, owner, probability, impact, response strategy, status, and action plan. Reviewing the risk register is the best way to help an organization gain insight into its overall risk profile, which is the summary of the nature and level of risk that the organization faces. By reviewing the risk register, the organization can obtain a comprehensive and holistic view of the sources, causes, and consequences of the risks, their likelihood and impact, their interrelationships and dependencies, and their alignment with therisk appetite and tolerance. The risk register can also help the organization to prioritize the risks, allocate the resources, select the risk responses, monitor the risk performance, and evaluate the risk outcomes. References = CRISC Review Manual, 7th Edition, page 99.
A key risk indicator (KRI) that incorporates data from external open-source threat intelligence sources has shown changes in risk trend data. Which of the following is MOST important to update in the risk register?
Impact of risk occurrence
Frequency of risk occurrence
Cost of risk response
Legal aspects of risk realization
A key risk indicator (KRI) is a metric that provides information on the level of exposure to a given risk. Changes in risk trend data indicate that the likelihood or probability of a risk occurring has changed. Therefore, the frequency of risk occurrence should be updated in the risk register to reflect the current risk profile. The impact, cost, and legal aspects of risk realization are not directly affected by the changes in risk trend data, unless the nature or severity of the risk has also changed. (Risk and Information Systems Control Review Questions, Answers & Explanations Manual, 5th Edition, page 972
Of the following, who is BEST suited to assist a risk practitioner in developing a relevant set of risk scenarios?
Internal auditor
Asset owner
Finance manager
Control owner
The asset owner is the best suited to assist a risk practitioner in developing a relevant set of risk scenarios. The asset owner is the person who has the authority and responsibility for the IT assets that support the business processes. The asset owner can provide valuable information on the business objectives, requirements, and expectations that the IT assets should meet. The asset owner can also help identify the potential threats, vulnerabilities, and impacts that may affect the IT assets and the business processes. The asset owner can also suggest possible risk responses and mitigation strategies to address the risk scenarios. The other options are not as relevant as the asset owner, as they may not have the same level of knowledge, interest, or involvement in the IT assets and the business processes. References = Risk and Information Systems Control Study Manual, Chapter 1: IT Risk Identification, Section 1.3: IT Risk Scenarios, page 23.
An organization has operations in a location that regularly experiences severe weather events. Which of the following would BEST help to mitigate the risk to operations?
Prepare a cost-benefit analysis to evaluate relocation.
Prepare a disaster recovery plan (DRP).
Conduct a business impact analysis (BIA) for an alternate location.
Develop a business continuity plan (BCP).
The best way to mitigate the risk to operations caused by severe weather events is to develop a business continuity plan (BCP). A BCP is a document that describes the procedures and resources needed to ensure the continuity of the organization’s critical functions and processes in the event of a disruption or disaster. A BCP helps to identify the recovery objectives, strategies, and priorities, as well as the roles and responsibilities of the recovery team members. A BCP also helps to prepare and test the recovery capabilities and resources, such as alternate locations, backup systems, and communication channels. The other options are not as effective as developing a BCP, although they may be part of the BCP process or outcomes. Preparing a cost-benefit analysis to evaluate relocation, preparing a disaster recovery plan (DRP), and conducting a business impact analysis (BIA) for an alternate location are all activities that can help to develop or implement a BCP, but they are not the best way to mitigate the risk to operations. References = Risk and Information Systems Control Study Manual, Chapter 5, Section 5.2.1, page 5-9.
When performing a risk assessment of a new service to support a core business process, which of the following should be done FIRST to ensure continuity of operations?
Define metrics for restoring availability.
Identify conditions that may cause disruptions.
Review incident response procedures.
Evaluate the probability of risk events.
When performing a risk assessment of a new service to support a core business process, the first step is to identify the conditions that may cause disruptions to the service or the process. This involves identifying the sources and causes of potential risk events, such as natural disasters, cyberattacks, human errors, equipment failures, power outages, etc. that may affect the availability, integrity, or confidentiality of the service or the process. By identifying the conditions that may cause disruptions, the risk practitioner can then analyze the probability and impact of the risk events, evaluate the risk exposure, and determine theappropriate risk responses to ensure the continuity of operations. References = CRISC Review Manual, 7th Edition, page 66.
The following is the snapshot of a recently approved IT risk register maintained by an organization's information security department.
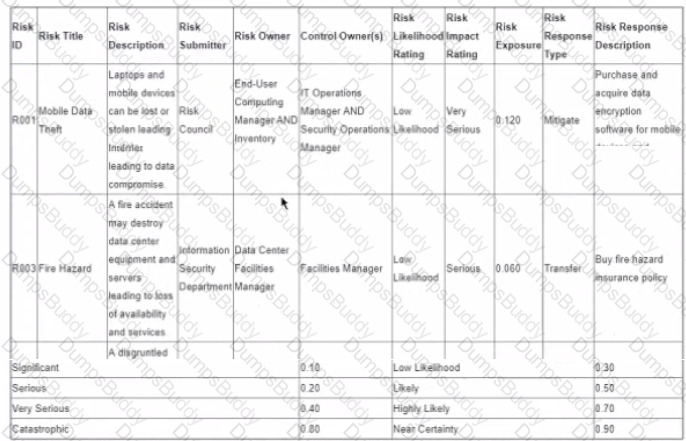
After implementing countermeasures listed in ‘’Risk Response Descriptions’’ for each of the Risk IDs, which of the following component of the register MUST change?
Risk Impact Rating
Risk Owner
Risk Likelihood Rating
Risk Exposure
Risk exposure is the product of risk likelihood and risk impact ratings. It represents the potential loss or damage that may result from a risk event. After implementing countermeasures, the risk likelihood and/or impact ratings may change, depending on the effectiveness of the countermeasures. Therefore, the risk exposure must also change to reflect the updated risk ratings. The other components of the register, such as risk owner, risk impact rating, and risk likelihood rating, may or may not change depending on the nature and scope of the countermeasures. References = Risk and Information Systems Control Study Manual, Chapter 2: IT Risk Assessment, Section 2.4: IT Risk Response, page 87.
An organization has decided to commit to a business activity with the knowledge that the risk exposure is higher than the risk appetite. Which of the following is the risk practitioner's MOST important action related to this decision?
Recommend risk remediation
Change the level of risk appetite
Document formal acceptance of the risk
Reject the business initiative
The risk practitioner’s most important action related to the decision to commit to a business activity with the knowledge that the risk exposure is higher than the risk appetite is to document formal acceptance of the risk. Formal acceptance of the risk means that the organization acknowledges and agrees to bear the risk and its potential consequences. Formal acceptance of the risk should be documented and approved by the appropriate authority level, such as senior management or the board of directors. Formal acceptance of the risk should also include the rationale, assumptions, and conditions for accepting the risk, as well as the monitoring and reporting mechanisms for the risk. Formal acceptance of the risk provides evidence and accountability for the risk management decision and helps to avoid disputes or misunderstandings in the future. The other options are not as important as documenting formal acceptance of the risk, as they are related to the alternatives, adjustments, or rejections of the risk, not the actual acceptance of the risk. References = Risk and Information Systems Control Study Manual, Chapter 3: IT Risk Response, Section 3.2: IT Risk Response Options, page 133.
An organization is analyzing the risk of shadow IT usage. Which of the following is the MOST important input into the assessment?
Business benefits of shadow IT
Application-related expresses
Classification of the data
Volume of data
The most important input into the assessment of the risk of shadow IT usage is the classification of the data that is being processed, stored, or transmitted by the unauthorized applications or devices. This determines the level of confidentiality, integrity, and availability that is required for the data and the potential impact of a breach or loss. Business benefits of shadow IT, application-related expenses, and volume of data are less important inputs that may affect the risk analysis, but not as much as the data classification. References = Risk IT Framework, 2nd Edition, page 28; CRISC Review Manual, 6th Edition, page 98.
Which of the following is MOST important for successful incident response?
The quantity of data logged by the attack control tools
Blocking the attack route immediately
The ability to trace the source of the attack
The timeliness of attack recognition
The most important factor for successful incident response is the timeliness of attack recognition. Incident response is the process of detecting, analyzing, containing, eradicating, recovering, and reporting on security incidents that could affect the organization’s IT systems or data. The timeliness of attack recognition is the speed and accuracy with which the organization can identify and confirm that an attack has occurred or is in progress. The timeliness of attack recognition is crucial for successful incident response, as it affects the ability and effectiveness of the organization to respond to and mitigate the attack, and to minimize the damage and impact of the attack. The other options are not as important as the timeliness of attack recognition, although they may also contribute to or influence the incident response. The quantity of data logged by the attack control tools, the ability to trace the source of the attack, and the blocking of the attack route immediately are all factors that could help or hinder the incident response, but they are not the most important factor for successful incident response. References = CISA Review Manual, 27th Edition, Chapter 5, Section 5.4.1, page 5-32.
Which of the following will BEST help to ensure key risk indicators (KRIs) provide value to risk owners?
Ongoing training
Timely notification
Return on investment (ROI)
Cost minimization
The best way to ensure key risk indicators (KRIs) provide value to risk owners is to provide timely notification of the changes in the risk exposure. KRIs are metrics that provide an early warning of increasing risk exposure in various areas of the organization. By providing timely notification of the KRI values, the risk owners can be alerted of the risk situation and take appropriate actions to manage the risk. Ongoing training, return on investment (ROI), and cost minimization are other possible ways to ensure KRIs provide value, but they are not as effective as timely notification. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 10; CRISC Review Manual, 6th Edition, page 140.
Which of the following BEST supports the management of identified risk scenarios?
Collecting risk event data
Maintaining a risk register
Using key risk indicators (KRIs)
Defining risk parameters
The best tool to support the management of identified risk scenarios is maintaining a risk register, as it provides a comprehensive and structured record of the risk information and decisions, such as the risk description, rating, ownership, response, and status, and facilitates the communication and accountability of the risk management process and activities. The other options are not the best tools, as they are more related to the collection, measurement, or definition of the risk scenarios, respectively, rather than the management of the risk scenarios. References = CRISC Review Manual, 7th Edition, page 101.
Business management is seeking assurance from the CIO that IT has a plan in place for early identification of potential issues that could impact the delivery of a new application Which of the following is the BEST way to increase the chances of a successful delivery'?
Implement a release and deployment plan
Conduct comprehensive regression testing.
Develop enterprise-wide key risk indicators (KRls)
Include business management on a weekly risk and issues report
The best way to increase the chances of a successful delivery of a new application and to assure the business management that IT has a plan in place for early identification of potential issues is to include business management on a weekly risk and issues report. A risk and issues report is a document that summarizes the current status, progress, and challenges of the IT project, as well as the actions and resources needed to address them. A risk and issues report helps to communicate and align the expectations and objectives of the IT and business stakeholders, and to facilitate timely and effective decision-making and problem-solving. A risk and issues report also helps to monitor and control the project scope, schedule, budget, and quality, and to ensure that the project delivers the desired value and benefits to the organization. The other options are not as effective as including business management on a weekly risk and issues report, although they may be part of the IT project management process or outcomes. Implementing a release and deployment plan, conducting comprehensive regression testing, and developing enterprise-wide key risk indicators (KRIs) are all activities that can help to ensure the quality and reliability of the new application, but they do not necessarily involve the business management or provide assurance for the early identification of potential issues. References = Risk and Information Systems Control Study Manual, Chapter 5, Section 5.4.1, page 5-32.
Which of the following is MOST important for mitigating ethical risk when establishing accountability for control ownership?
Ensuring processes are documented to enable effective control execution
Ensuring regular risk messaging is Included in business communications from leadership
Ensuring schedules and deadlines for control-related deliverables are strictly monitored
Ensuring performance metrics balance business goals with risk appetite
The most important thing for mitigating ethical risk when establishing accountability for control ownership is to ensure that the performance metrics balance business goals with risk appetite. Performance metrics are the measures that evaluate the achievement of the objectives or the performance of the processes or controls. Business goals are the desired or expected outcomes or results of the business activities or processes. Risk appetite is the amount and type of risk that the organization is willing and able to take. Ethical risk is the risk that arises from the violation or breach of the ethical principles or standards of the organization or the profession. To mitigate ethical risk, the performance metrics should balance business goals with risk appetite, meaning that they should not encourage or reward excessive or inappropriate risk-taking or unethical behavior, but rather promote and support responsible and ethical risk management and decision making. The other options are not as important as ensuring performance metrics balance business goals with risk appetite, as they are related to the documentation, communication, or monitoring of the processes or controls, not the evaluation or alignment of the performance metrics. References = Risk and Information Systems Control Study Manual, Chapter 4: Risk and Control Monitoring and Reporting, Section 4.2: Key Performance Indicators, page 183.
Which of the following is MOST important to update when an organization's risk appetite changes?
Key risk indicators (KRIs)
Risk reporting methodology
Key performance indicators (KPIs)
Risk taxonomy
The most important element to update when an organization’s risk appetite changes is the key risk indicators (KRIs). KRIs are metrics that provide an early warning of increasing risk exposure in various areas of the organization. They help to monitor the level of risk and to trigger risk responses when the risk exceeds the risk appetite. The risk appetite is the amount and type of risk that an organization is willing to accept in pursuit of its objectives. Risk reporting methodology, key performance indicators (KPIs), and risk taxonomy are other elements that may be updated, but they are not as important as the KRIs. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 12; CRISC Review Manual, 6th Edition, page 215.
Which of the following is the PRIMARY objective of maintaining an information asset inventory?
To provide input to business impact analyses (BIAs)
To protect information assets
To facilitate risk assessments
To manage information asset licensing
An information asset inventory is a list of all the information assets that an organization owns or uses. It includes information such as the asset name, description, owner, location, classification, value, and dependencies. The primary objective of maintaining an information asset inventory is to provide input to business impact analyses (BIAs), which are used to identify the criticality and recovery priorities of information assets in the event of a disruption. By having an updated and accurate information asset inventory, an organization can ensure that the BIAs reflect the current state and needs of the business processes that rely on the information assets. References = CRISC Review Manual, 7th Edition, page 74.
When defining thresholds for control key performance indicators (KPIs). it is MOST helpful to align:
information risk assessments with enterprise risk assessments.
key risk indicators (KRIs) with risk appetite of the business.
the control key performance indicators (KPIs) with audit findings.
control performance with risk tolerance of business owners.
The most helpful factor to align when defining thresholds for control key performance indicators (KPIs) is the control performance with the risk tolerance of business owners. Control KPIs are metrics that measurethe effectiveness and efficiency of the controls that are implemented to mitigate the risks. By aligning the control performance with the risk tolerance of business owners, the thresholds for control KPIs can reflect the acceptable level of risk and the desired level of control for the business processes and objectives. Information risk assessments with enterprise risk assessments, key risk indicators (KRIs) with risk appetite of the business, and control KPIs with audit findings are other possible factors to align, but they are not as helpful as control performance with risk tolerance of business owners. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 12; CRISC Review Manual, 6th Edition, page 215.
Which of the following BEST helps to identify significant events that could impact an organization?
Control analysis
Vulnerability analysis
Scenario analysis
Heat map analysis
Scenario analysis is the best method to identify significant events that could impact an organization. Scenario analysis is the process of creating and evaluating hypothetical situations or scenarios that represent plausible outcomes of various events or actions. Scenario analysis helps to anticipate and prepare for potential risks and opportunities, as well as to test the robustness and resilience of the organization’s strategies and plans. Control analysis, vulnerability analysis, and heat map analysis are not as effective as scenario analysis, because they focus on the existing or current state of the organization, rather than the future or alternative states. References = Risk and Information Systems Control Study Manual, Chapter 4, Section 4.2.1, page 4-13.
Which of the following sources is MOST relevant to reference when updating security awareness training materials?
Risk management framework
Risk register
Global security standards
Recent security incidents reported by competitors
The most relevant source to reference when updating security awareness training materials is the recent security incidents reported by competitors. This can help to illustrate the real-world threats and consequences of poor security practices, and to motivate the employees to follow the security policies and procedures. Risk management framework, risk register, and global security standards are other sources that may be useful, but they are not as relevant as the recent security incidents. References = ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 9; CRISC Review Manual, 6th Edition, page 214.
A newly incorporated enterprise needs to secure its information assets From a governance perspective which of the following should be done FIRST?
Define information retention requirements and policies
Provide information security awareness training
Establish security management processes and procedures
Establish an inventory of information assets
The first thing that should be done from a governance perspective to secure the information assets of a newly incorporated enterprise is to establish an inventory of information assets. An inventory of information assets is a document that lists and categorizes all the information assets that the organization owns, uses, or manages, such as data, documents, systems, applications, and devices. An inventory of information assets helps to identify and classify the information assets based on their value, sensitivity, and criticality, and to determine the appropriate level of protection and control for each asset. An inventory of information assets also helps to support the development and implementation of other information security activities, such as risk assessment, policy formulation, awareness training, and incident response. The other options are not the first thing that should be done, although they may be important steps or components of the information security governance. Defining information retention requirements and policies, providing information security awareness training, and establishing security management processes and procedures are all activities that can help to secure the information assets, but they require the prior knowledge and understanding of the information assets. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.1.1, page 3-3.
Which of the following is MOST helpful to understand the consequences of an IT risk event?
Fault tree analysis
Historical trend analysis
Root cause analysis
Business impact analysis (BIA)
Business impact analysis (BIA) is a process that involves analyzing the potential consequences of an IT risk event on the organization’s critical business functions and processes. BIA can help to understand the severity and duration of the disruption, the financial and operational losses, the recovery time objectives, and the recovery point objectives. BIA can also help to prioritize the recovery activities and resources, as well as to determine the acceptable level of risk and the risk mitigation strategies. BIA is the most helpful tool to understand the consequences of an IT risk event, as it provides a comprehensive and quantitative assessment of the impact and the recovery requirements. References = Risk and Information Systems Control Study Manual, Chapter 4, Section 4.4.2, p. 206-207
Which of the following potential scenarios associated with the implementation of a new database technology presents the GREATEST risk to an organization?
The organization may not have a sufficient number of skilled resources.
Application and data migration cost for backups may exceed budget.
Data may not be recoverable due to system failures.
The database system may not be scalable in the future.
The potential scenario that presents the greatest risk to an organization when implementing a new database technology is that data may not be recoverable due to system failures. Data recovery is the process of restoring or retrieving data that has been lost, corrupted, or damaged due to system failures, such as hardware malfunctions, software errors, power outages, or natural disasters. Data recovery is essential for the continuity and integrity of the organization’s operations and information, as data is one of the most valuable and critical assets of the organization. Data recovery is also important for the compliance and accountability of the organization, as data may be subject to legal or regulatory requirements, such as retention, backup, or audit. Data recovery may be challenging or impossible when implementing a new database technology, because the new technology may not be compatible or interoperable with the existing systems, applications, or backups, or because the new technology may nothave adequate or tested recovery mechanisms or procedures. Data recovery may also be costly or time-consuming when implementing a new database technology, because the new technology may require additional or specialized resources, tools, or expertise, or because the new technology may involve large or complex data sets or structures. The other options are not as risky as data recovery, although they may also pose some difficulties or limitations for the new database technology implementation. The organization may not have a sufficient number of skilled resources, application and data migration cost for backups may exceed budget, and the database system may not be scalable in the future are all factors that could affect the feasibility and sustainability of the new database technology, but they do not directly affect the continuity and integrity of the organization’s operations and information. References = 2
The MAJOR reason to classify information assets is
maintain a current inventory and catalog of information assets
determine their sensitivity and critical
establish recovery time objectives (RTOs)
categorize data into groups
Information asset classification is the process of assigning a level of sensitivity and criticality to an information asset based on its value, importance, and impact to the organization. The major reason to classify information assets is to determine their sensitivity and criticality, which are the measures of how confidential, proprietary, or sensitive the information is, and how essential, urgent, or time-sensitive the information is for the business operations. By determining the sensitivity and criticality of information assets, the organization can prioritize the protection and recovery of the information assets, implement the appropriate security controls and safeguards, comply with the regulatory and contractual requirements, and manage the information lifecycle and disposal. References = CRISC Review Manual, 7th Edition, page 74.
An organization is subject to a new regulation that requires nearly real-time recovery of its services following a disruption. Which of the following is the BEST way to manage the risk in this situation?
Move redundant IT infrastructure to a closer location.
Obtain insurance and ensure sufficient funds are available for disaster recovery.
Review the business continuity plan (BCP) and align it with the new business needs.
Outsource disaster recovery services to a third-party IT service provider.
Updating the BCP to align with real-time recovery requirements ensures the organization’s resilience to disruptions while meeting regulatory standards. This action reflectsBusiness Continuity and Disaster Recovery Planningbest practices.
If concurrent update transactions to an account are not processed properly, which of the following will MOST likely be affected?
Confidentiality
Accountability
Availability
Integrity
Integrity is the property of data that ensures its accuracy, completeness, and consistency2. If concurrent update transactions to an account are not processed properly, the integrity of the data may be compromised, as it may lead to concurrency problems such as lost update, unrepeatable read, or phantom read3. These problems can cause the data to be incorrect, incomplete, or inconsistent, which may affect the reliability and validity of the data. Therefore, option D is the correct answer, as it reflects the impact of improper concurrent update transactions on the data integrity. The other options are not correct, as they do not directly relate to the effect of concurrent update transactions on the data. Option A, confidentiality, is the property of data that ensures its protection from unauthorized access or disclosure2. Concurrent update transactions do not necessarily affect the confidentiality of the data, as they do not involve exposing the data to unauthorized parties. Option B, accountability, is the property of data that ensures its traceability and auditability2. Concurrent update transactions do not necessarily affect the accountability of the data, as they do not involve losing the records or logs of the data transactions. Option C, availability, is the property of data that ensures its accessibility and usability2. Concurrent update transactions do not necessarily affect the availability of the data, as they do not involve preventing the access or use of the data.
An organization operates in an environment where reduced time-to-market for new software products is a top business priority. Which of the following should be the risk practitioner's GREATEST concern?
Sufficient resources are not assigned to IT development projects.
Customer support help desk staff does not have adequate training.
Email infrastructure does not have proper rollback plans.
The corporate email system does not identify and store phishing emails.
In an environment where reduced time-to-market for new software products is a top business priority, the risk practitioner’s greatest concern should be whether sufficient resources are assigned to IT development projects. Resources include human, financial, technical, and physical assets that are needed to plan, design, develop, test, and deliver high-quality software products in a timely manner. If the IT development projects are under-resourced, they may face challenges such as delays, errors, defects, rework, scope creep, or failure to meet customer expectations or requirements. These challenges can increase the risk of losing competitive advantage, market share, customer satisfaction, or reputation. The other options are less critical, as they are not directly related to the core business priority of reducing time-to-market for new software products. Customer support help desk staff training, email infrastructure rollback plans, and corporate email system phishing detection are important aspects of information security and customer service, but they are not the primary drivers of software product development and delivery. References = Risk and Information Systems Control Study Manual, Chapter 3: IT Risk Response, Section 3.2: Risk Response Options, p. 115-116.
An IT department originally planned to outsource the hosting of its data center at an overseas location to reduce operational expenses. After a risk assessment, the department has decided to keep the data center in-house. How should the risk treatment response be reflected in the risk register?
Risk mitigation
Risk avoidance
Risk acceptance
Risk transfer
The risk treatment response that should be reflected in the risk register when an IT department decides to keep the data center in-house instead of outsourcing it to an overseas location is risk avoidance. Risk avoidance is a risk response strategy that involves eliminating the source of the risk, or changing the plan or scope of the activity, to avoid the risk altogether. Risk avoidance can help to reduce the risk exposure and impact to zero, by removing the possibility of the risk occurrence. In this case, the IT department avoids the risk of outsourcing the data center to an overseas location, which could involve various threats, vulnerabilities, and uncertainties, such as data security, legal compliance, service quality, communication, or cultural issues. By keeping the data center in-house, the IT department maintains the control and ownership of the data center, and eliminates the potential risk associated with the outsourcing. Risk mitigation, risk acceptance, and risk transfer are not the correct risk treatment responses, as they do not reflect the actual decision and action taken by the IT department, and they do not eliminate the risk source or occurrence. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 51.
Which of the following BEST supports ethical IT risk management practices?
Robust organizational communication channels
Mapping of key risk indicators (KRIs) to corporate strategy
Capability maturity models integrated with risk management frameworks
Rigorously enforced operational service level agreements (SLAs)
Robust organizational communication channels are the best way to support ethical IT risk management practices, as they enable transparent and consistent sharing of risk information and decisions among all stakeholders. Ethical IT risk management requires that the risk management process and outcomes are aligned with the enterprise’s values, objectives, and obligations, and that the risk management activities are conducted with integrity, accountability, and respect. Robust organizational communication channels facilitate these aspects by ensuring that the risk management roles and responsibilities are clearly defined and communicated, that the risk management policies and procedures are widely disseminated and understood, that the risk management performance and results are regularly reported and reviewed, and that the risk management feedback and improvement suggestions are solicited and addressed. Mapping of key risk indicators (KRIs) to corporate strategy, capability maturity models integrated with risk management frameworks, and rigorously enforced operational service level agreements (SLAs) are not directly related to ethical IT risk management practices, but rather to the effectiveness and efficiency of the risk management process. References = CRISC Certified in Risk and Information Systems Control – Question201; ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, question 201.
Which of the following is the PRIMARY risk management responsibility of the second line of defense?
Monitoring risk responses
Applying risk treatments
Providing assurance of control effectiveness
Implementing internal controls
The primary risk management responsibility of the second line of defense is to monitor the risk responses. The second line of defense is the function that oversees and supports the risk management activities of the first line of defense, which is the function that owns and manages the risks. The second line of defense includes the risk management, compliance, and quality assurance functions, among others. The second line of defense is responsible for monitoring the risk responses, which are the actions taken to address the risks, such as avoiding, transferring, mitigating, or accepting the risks. The second line of defense monitors the risk responses to ensure that they are implemented effectively and efficiently, that they achieve the desired outcomes, and that they are aligned with the risk appetite and tolerance of the organization. The second line of defense also provides guidance, advice, and feedback to the first line of defense on the risk responses, and reports the results and issues to the senior management and the board. Applying risk treatments, providing assurance of control effectiveness, and implementing internal controls are not the primary risk management responsibilities of the second line of defense, as they are either the responsibilities of the first line of defense or the third line of defense, which is the function that provides independent assurance of the risk management activities, such as the internal audit function. References = CRISC Review Manual, 6th Edition, ISACA, 2015, page 36.
A risk practitioner has been asked to advise management on developing a log collection and correlation strategy. Which of the following should be the MOST important consideration when developing this strategy?
Ensuring time synchronization of log sources.
Ensuring the inclusion of external threat intelligence log sources.
Ensuring the inclusion of all computing resources as log sources.
Ensuring read-write access to all log sources
Ensuring time synchronization of log sources is the most important consideration when developing a log collection and correlation strategy, as it enables the accurate and consistent analysis and correlation of log data from different sources and systems. Time synchronization can help to identify the sequence and causality of events, and to detect and respond to any anomalies or incidents. Time synchronization can also facilitate the compliance and audit of the log data, and support the forensic investigation and legal action if needed. References = Most Asked CRISC Exam Questions and Answers, Question 10. CRISC: Certified in Risk & Information Systems Control Sample Questions, Question 248. ISACA Certified in Risk and Information Systems Control (CRISC) Certification Exam Question and Answers, Question 248. CRISC by Isaca Actual Free Exam Q&As, Question 9.
Which of the following will MOST likely change as a result of the decrease in risk appetite due to a new privacy regulation?
Key risk indicator (KRI) thresholds
Risk trends
Key performance indicators (KPIs)
Risk objectives
KRI thresholds are the levels or points that trigger an action or a response when a KRI reaches or exceeds them. They reflect the risk appetite of the organization, which is the amount and type of risk that it is willing to accept in pursuit of its objectives. A new privacy regulation may reduce the risk appetite of the organization, as it may impose stricter requirements and penalties for non-compliance. Therefore, the organization may need to adjust its KRI thresholds to lower levels, to ensure that it can identify and manage privacy risks more effectively and proactively
Which of the following is MOST important for a risk practitioner to confirm once a risk action plan has been completed?
The risk register has been updated.
The risk tolerance has been recalibrated.
The risk has been mitigated to the intended level.
The risk owner has reviewed the outcomes.
Confirming that the risk has been mitigated to the intended level is paramount to ensure that the risk response was effective. This ties toRisk Mitigation and Treatment, ensuring that controls implemented have reduced the risk to within the organization's appetite. Updating registers or recalibrating tolerances comes secondary to verifying the effectiveness of mitigation.
Which of the following provides the MOST useful input to the development of realistic risk scenarios?
Balanced scorecard
Risk appetite
Risk map
Risk events
Risk events are specific occurrences or changes that have a potential impact on the achievement of objectives. They can be positive or negative, and they can be internal or external to the organization. Risk events provide the basis for developing realistic risk scenarios, which are hypothetical situations that illustrate the possible consequences of a risk event. Risk scenarios help to understand and communicate the nature, sources, and causes of risk, as well as the potential impact and likelihood of risk occurrence. Risk scenarios can also be used to test the effectiveness of risk responses and controls.
The other options are not as useful as risk events for developing realistic risk scenarios. A balanced scorecard (A) is a strategic management tool that measures the performance of the organization against its objectives, vision, and strategy. It does not provide specific information about risk events or their consequences. A risk appetite (B) is the amount and type of risk that an organization is willing to accept in pursuit of its objectives. It does not describe the risk events or their scenarios, but rather the level of risk tolerance and acceptance. A risk map © is a graphical representation of the risk profile of the organization, showing the relationship between the likelihood and impact of different risks. It does not provide the details or context of the risk events or their scenarios, but rather the relative ranking and prioritization of risks.
A service organization is preparing to adopt an IT control framework to comply with the contractual requirements of a new client. Which of the following would be MOST helpful to the risk practitioner?
Negotiating terms of adoption
Understanding the timeframe to implement
Completing a gap analysis
Initiating the conversion
Completing a gap analysis identifies discrepancies between current controls and the requirements of the IT control framework, ensuring a focused approach to compliance. This supportsRisk Assessment for Compliance Requirements.
Which of the following is the PRIMARY benefit of consistently recording risk assessment results in the risk register?
Assessment of organizational risk appetite
Compliance with best practice
Accountability for loss events
Accuracy of risk profiles
A risk profile is a summary of the risks that an organization faces and their likelihood and impact. Consistently recording risk assessment results in the risk register can help improve the accuracy of risk profiles by providing a reliable and up-to-date source of information on the current risk situation, the risk response actions, and the residual risk levels. A risk register is a tool that captures and documents the risk identification, analysis, evaluation, and treatment processes2. A risk register can also facilitate risk communication, monitoring, and reporting2.
Assessment of organizational risk appetite, compliance with best practice, and accountability for loss events are not the primary benefits of consistently recording risk assessment results in the risk register. These are possible outcomes or objectives of risk management, but they do not directly depend on the risk register.
Which of the following BEST mitigates the risk of violating privacy laws when transferring personal information lo a supplier?
Encrypt the data while in transit lo the supplier
Contractually obligate the supplier to follow privacy laws.
Require independent audits of the supplier's control environment
Utilize blockchain during the data transfer
Contractually obligating the supplier to follow privacy laws is the best way to mitigate the risk of violating privacy laws when transferring personal information to a supplier, because it ensures that the supplier is legally bound to comply with the applicable laws and regulations that protect the privacy and security of the personal information. This also creates a clear accountability and liability for the supplier in case of a privacy breach, and defines the rights and obligations of both parties in relation to the personal information. The other options are not the best ways to mitigate the risk of violating privacy laws, although they may also be helpful in reducing the likelihood or impact of a privacy breach. Encrypting the data while in transit to the supplier, requiring independent audits of the supplier’s control environment, and utilizing blockchain during the data transfer are examples of technical or assurance controls that aim to protect the confidentiality, integrity, and availability of the personal information, but they do not address the legal or contractual aspects of the privacy laws. References = CRISC: Certified in Risk & Information Systems Control Sample Questions
Which of the following BEST enforces access control for an organization that uses multiple cloud technologies?
Senior management support of cloud adoption strategies
Creation of a cloud access risk management policy
Adoption of a cloud access security broker (CASB) solution
Expansion of security information and event management (SIEM) to cloud services
A cloud access security broker (CASB) solution is the best way to enforce access control for an organization that uses multiple cloud technologies, as it provides a centralized and consistent platform to manage and monitor the access to various cloud services and applications. A CASB solution can help to implement and enforce the enterprise’s access policies and standards, as well as to detect and prevent unauthorized or malicious access attempts. Senior management support of cloud adoption strategies, creation of a cloud access risk management policy, and expansion of security information and event management (SIEM) to cloud services are not the best ways to enforce access control for an organization that uses multiple cloud technologies, as they do not provide the technical capabilities or tools to manage and monitor the access to various cloud services and applications. References = CRISC by Isaca Actual Free Exam Q&As, question 210; CRISC: Certified in Risk & Information Systems Control Sample Questions, question 210.
Who is BEST suited to determine whether a new control properly mitigates data loss risk within a system?
Data owner
Control owner
Risk owner
System owner
The control owner is the person who is responsible for designing, implementing, monitoring, and maintaining a control. The control owner is best suited to determine whether a new control properly mitigates data loss risk within a system, as they have the most knowledge and authority over the control. The control owner should also evaluate the effectiveness and efficiency of the control and report any issues or gaps to the risk owner.
The other options are not the best suited to determine whether a new control properly mitigates data loss risk within a system. The data owner is the person who has the accountability and authority over the data and its classification. The data owner may not have the technical expertise or access to evaluate the new control. The risk owner is the person who has the accountability and authority to manage a specific risk. The risk owner may not have the detailed knowledge or involvement in the new control. The system owner is the person who has the accountability and authority over the system and its operation. The system owner may not have the direct responsibility or oversight of the new control. References = CRISC TOPIC 3 EXAM SHORT Flashcards, CRISC-1-50 topic3 Flashcards, CRISC Certified in Risk and Information Systems Control – Question609
Which of the following would BEST help to address the risk associated with malicious outsiders modifying application data?
Multi-factor authentication
Role-based access controls
Activation of control audits
Acceptable use policies
Role-based access controls (RBAC) are a type of preventive control that limit the access and actions of users based on their roles and responsibilities within the organization. RBAC can help to address the risk of malicious outsiders modifying application data by restricting their access to the data and the functions they can perform on it. RBAC can also enforce the principle of least privilege, which means that users only have the minimum level of access required to perform their tasks. RBAC can be implemented through policies, procedures, and technical mechanisms such as access control lists, encryption, and authentication. References = Risk and Information Systems Control Study Manual, Chapter 4, Section 4.2.1.1, p. 178-179
Which of the following is the PRIMARY reason to adopt key control indicators (KCIs) in the risk monitoring and reporting process?
To provide data for establishing the risk profile
To provide assurance of adherence to risk management policies
To provide measurements on the potential for risk to occur
To provide assessments of mitigation effectiveness
Key control indicators (KCIs) are metrics that measure the performance and effectiveness of the controls that are implemented to mitigate the risks. KCIs can help to monitor the status and health of the controls, as well as to identify any issues or gaps that need to be addressed. The primary reason to adopt KCIs in the risk monitoring and reporting process is to provide assessments of mitigation effectiveness, meaning that they can help to evaluate how well the controls are reducing the risk exposure and achieving the desired outcomes. KCIs can also help to support the risk management decision making and improvement actions, as well as to demonstrate the value and benefits of the controls. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.3.1.2, p. 115-116
A risk practitioner has become aware of production data being used in a test environment. Which of the following should be the practitioner's PRIMARY concern?
Sensitivity of the data
Readability of test data
Security of the test environment
Availability of data to authorized staff
Production data is the data that is used in the actual operation of a system or application, such as customer information, financial records, transactions, etc.
Test data is the data that is used in the testing or development of a system or application, such as dummy data, sample data, simulated data, etc.
A risk practitioner has become aware of production data being used in a test environment. This indicates that there is a risk of unauthorized access, use, disclosure, modification, or destruction of the production data, which may affect the confidentiality, integrity, and availability of the data.
The primary concern of the risk practitioner in this situation is the sensitivity of the data. This means that the risk practitioner should assess how valuable, critical, or confidential the data is, and what would be the impact or consequence if the data is compromised or lost.
The sensitivity of the data helps to determine the level of protection and control that is needed to safeguard the data, and the priority and urgency of the risk response actions.
The other options are not the primary concerns of the risk practitioner in this situation. They are either secondary or not essential for data protection.
The references for this answer are:
Risk IT Framework, page 32
Information Technology & Security, page 26
Risk Scenarios Starter Pack, page 24
Which of the following provides the MOST useful information when developing a risk profile for management approval?
Residual risk and risk appetite
Strength of detective and preventative controls
Effectiveness and efficiency of controls
Inherent risk and risk tolerance
A risk profile is a summary of the key risks that an organization faces, along with the corresponding risk responses, risk owners, and risk indicators1. A risk profile is a useful tool for communicating and reporting the risk status and performance to the management and other stakeholders2. When developing a risk profile for management approval, the most useful information to include is the residual risk and the risk appetite, because:
Residual risk is the level of risk that remains after the implementation of risk responses3. It indicates the degree of exposure or uncertainty that the organization still faces, and the potential impact or consequences of the risk events. Residual risk helps the management to evaluate the effectiveness and adequacy of the risk responses, and to decide whether to accept, reduce, transfer, or avoid the risk4.
Risk appetite is the amount and type of risk that the organization is willing to accept or pursue in order to achieve its objectives5. It reflects the organization’s risk culture, strategy, and priorities, and provides a basis for setting risk thresholds and targets. Risk appetite helps the management to align the risk profile with the organizational goals and values, and to ensure that the risk responses are consistent and proportional to the risk level6.
The other options are not the most useful information when developing a risk profile for management approval, because:
Strength of detective and preventative controls is a measure of how well the controls can identify or prevent the occurrence or impact of the risk events7. It is a part of the risk response information, but it does not provide a comprehensive or holistic view of the risk profile. It does not show the residual risk or the risk appetite, which are more relevant and important for the management approval.
Effectiveness and efficiency of controls is a measure of how well the controls achieve their intended objectives and how well they use the available resources8. It is a part of the risk performance information, but it does not provide a complete or balanced view of the risk profile. It does not show the residual risk or the risk appetite, which are more significant and meaningful for the management approval.
Inherent risk and risk tolerance are related but different concepts from residual risk and risk appetite. Inherent risk is the level of risk that exists before the implementation of risk responses3. Risk tolerance is the acceptable variation or deviation from the risk appetite or the risk objectives5. They are useful for the risk assessment and analysis, but they do not provide the current or desired state of the risk profile. They do not show the residual risk or the risk appetite, which are more critical and valuable for the management approval.
References =
Risk Profile - CIO Wiki
Risk Profile: Definition, Example, and How to Create One
Residual Risk - CIO Wiki
What is Residual Risk? - Definition from Techopedia
Risk Appetite - CIO Wiki
Risk Appetite: What It Is and Why It Matters - Gartner
Preventive and Detective Controls - CIO Wiki
Control Effectiveness and Efficiency - CIO Wiki
When reporting on the performance of an organization's control environment including which of the following would BEST inform stakeholders risk decision-making?
The audit plan for the upcoming period
Spend to date on mitigating control implementation
A report of deficiencies noted during controls testing
A status report of control deployment
A report of deficiencies noted during controls testing is the best option to inform stakeholders risk decision-making, as it provides an accurate and timely assessment of the effectiveness and efficiency of the organization’s control environment. A report of deficiencies noted during controls testing is a document that summarizes the results of the testing activities performed on the organization’s internal controls, such as design, implementation, operation, and monitoring. A report of deficiencies noted during controls testing should include the following elements:
The scope, objectives, and methodology of the controls testing
The criteria and standards used to evaluate the controls
The findings and observations of the testing process
The root causes and impacts of the identified deficiencies
The recommendations and action plans to address the deficiencies
The roles and responsibilities of the stakeholders involved in the remediation process
A report of deficiencies noted during controls testing helps to inform stakeholders risk decision-making by providing them with relevant and reliable information on the current state of the organization’s control environment. It also helps to identify and prioritize the areas for improvement and enhancement of the control environment. A report of deficiencies noted during controls testing also facilitates the communication, collaboration, and accountability among the stakeholders involved in the risk management and control processes.
The other options are not the best options to inform stakeholders risk decision-making. The audit plan for the upcoming period is a document that outlines the scope, objectives, and methodology of the planned audit activities, but it does not provide any information on the actual performance of the organization’s control environment. Spend to date on mitigating control implementation is a measure of the resources and costs incurred to implement the risk response actions, but it does not indicate the effectiveness or efficiency of the control environment. A status report of control deployment is a document that tracks and monitors the progress and performance of the control implementation process, but it does not evaluate the quality or adequacy of the control environment. References = Internal Control Deficiencies: Identification,Reporting and Communication, IT Risk Resources | ISACA, Internal Control Testing: Techniques, Types, and Examples
Real-time monitoring of security cameras implemented within a retail store is an example of which type of control?
Preventive
Deterrent
Compensating
Detective
Detailed Explanation:Real-time monitoring is adetective control, as it is designed to identify and report suspicious or unauthorized activities as they occur. Detective controls provide feedback to mitigate ongoing risks and serve as an integral part of incident response plans.
Business areas within an organization have engaged various cloud service providers directly without assistance from the IT department. What should the risk practitioner do?
Recommend the IT department remove access to the cloud services.
Engage with the business area managers to review controls applied.
Escalate to the risk committee.
Recommend a risk assessment be conducted.
The best action for the risk practitioner to take when business areas within an organization have engaged various cloud service providers directly without assistance from the IT department is to recommend a risk assessment be conducted. A risk assessment is a process of identifying, analyzing, and evaluating the risks associated with the use of cloud services, such as financial, privacy, compliance, security, performance, quality, and technical risks12. A risk assessment can help to determine the current and potential risk exposure and impact of the cloud services, as well as the effectiveness and efficiency of theexisting or proposed controls. A risk assessment can also help to prioritize the risks and to develop and implement appropriate risk response strategies and plans, such as risk avoidance, reduction, sharing, or acceptance. Recommending a risk assessment is the best action, because it can provide valuable information and guidance to the business areas and the IT department for managing the cloud services in a consistent, effective, and efficient manner, and for aligning the cloud services with the organizational objectives, strategy, and risk appetite. The other options are not the best action, although they may be related or subsequent steps in the risk management process. Recommending the IT department remove access to the cloud services is a drastic and impractical action, as it may disrupt the business operations and services, and it may not address the underlying causes or drivers of the cloud service adoption. Engaging with the business area managers to review controls applied is a useful and collaborative action, as it can help to understand and evaluate the current state and practices of the cloud service usage, and to identify and address any gaps or issues in the control environment. However, this action should be based on or supported by a risk assessment, rather than preceding or replacing it. Escalating to the risk committee is a reporting and communication action, as it can help to inform and involve the senior management and other stakeholders in the risk management process, and to obtain their support and approval for the risk response actions. However, this action should be done after or along with a risk assessment, rather than before or instead of it. References = Best Practices to Manage Risks in the Cloud - ISACA, Cloud Risk Management - PwC UK
Which of the following is MOST important to include in a Software as a Service (SaaS) vendor agreement?
An annual contract review
A service level agreement (SLA)
A requirement to adopt an established risk management framework
A requirement to provide an independent audit report
A service level agreement (SLA) is a contract between a SaaS vendor and a customer that defines the quality and availability of the SaaS service, as well as the responsibilities and obligations of both parties. An SLA is most important to include in a SaaS vendor agreement because it sets the expectations and standards for the SaaS service, provides a mechanism for measuring and monitoring the serviceperformance, and establishes the remedies and penalties for service failures or breaches. An SLA can also help to mitigate the risks and liabilities associated with SaaS delivery, such as data security, privacy, compliance, and disaster recovery. The other options are not the most important to include in a SaaS vendor agreement, although they may be beneficial or desirable depending on the context and nature of the SaaS service. An annual contract review is a process of evaluating and revising the SaaS vendor agreement to reflect the changing needs and circumstances of the customer and the vendor, but it is not a mandatory or essential element of the agreement. A requirement to adopt an established risk management framework is a way of ensuring that the SaaS vendor follows the best practices and standards for identifying, assessing, and mitigating the risks related to the SaaS service, but it is not a specific or measurable term of the agreement. A requirement to provide an independent audit report is a way of verifying and validating the SaaS vendor’s compliance with the SLA and other contractual obligations, but it is not a direct or primary component of the agreement. References = SaaS Agreements: Key Contractual Provisions, SaaS Agreement: Everything You Need to Know, Essential checklist for SaaS agreement negotiations, KeyClauses To Understand and Evaluate in SaaS Contracts, SaaS Reseller Agreement: Everything You Need to Know
Which of the following is MOST important when discussing risk within an organization?
Adopting a common risk taxonomy
Using key performance indicators (KPIs)
Creating a risk communication policy
Using key risk indicators (KRIs)
A common risk taxonomy is a framework that defines and categorizes the sources, types, and impacts of risks within an organization1. It helps to establish a consistent and shared understanding of risk across the organization, and to facilitate effective risk identification, assessment, reporting, and communication2. A common risk taxonomy also enables comparison and aggregation of risks at different levels and domains, and supports alignment of risk management with business objectives and strategies3. Using key performance indicators (KPIs) and key risk indicators (KRIs) are important for measuring and monitoring risk and performance, but they are not the most important factor when discussing risk within an organization. KPIs and KRIs should be derived from the common risk taxonomy and aligned with theorganization’s risk appetite and tolerance4. Creating a risk communication policy is also important for ensuring that risk information is communicated to the right stakeholders at the right time and in the right format, but it is not the most important factor either. A risk communication policy should be based on the common risk taxonomy and the risk roles and responsibilities within the organization5. References = Risk and Information Systems Control Study Manual, Chapter 1: IT Risk Identification, Section 1.2: Risk Taxonomy, pp. 25-29.
Which of the following is the PRIMARY objective for automating controls?
Improving control process efficiency
Facilitating continuous control monitoring
Complying with functional requirements
Reducing the need for audit reviews
According to the CRISC Review Manual1, control process efficiency is the degree to which a control process achieves its intended objectives with minimum resources, time, and cost. The primary objective for automating controls is to improve control process efficiency, as automation can help to reduce human errors, increase consistency and accuracy, enhance scalability and flexibility, and optimize performance and productivity. Automation can also help to achieve other objectives, such as facilitating continuous control monitoring, complying with functional requirements, and reducing the need for audit reviews, but these are not the primary objective for automating controls. References = CRISC Review Manual1, page 202.
Which of the following is the GREATEST concern associated with the transmission of healthcare data across the internet?
Unencrypted data
Lack of redundant circuits
Low bandwidth connections
Data integrity
The greatest concern associated with the transmission of healthcare data across the internet is unencrypted data, as this exposes the data to unauthorized access, interception, modification, or disclosure, which may compromise the confidentiality, integrity, and availability of the data. Healthcare data is sensitive and personal information that may include medical records, diagnoses, treatments, prescriptions, insurance claims, and biometric data. Healthcare data is subject to various legal and regulatory requirements, such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States, that mandate the protection and privacy of the data. Encryption is a method of transforming the data into an unreadable format that can only be accessed or restored by authorized parties who have the decryption key. Encryption helps to prevent or reduce the risk of data breaches, identity theft, fraud, or other malicious attacks. The other options are not the greatest concerns associated with the transmission of healthcare data across the internet, although they may pose some challenges or issues. Lack of redundant circuits is a concern for the reliability and continuity of the data transmission, but it does notaffect the security or privacy of the data. Low bandwidth connections is a concern for the speed and efficiency of the data transmission, but it does not affect the security or privacy of the data. Data integrity is a concern for the accuracy and completeness of the data, but it does not necessarily depend on the encryption of the data. References = Risk and Information Systems Control Study Manual, Chapter 4: Risk Response, page 156.
Which of the following should be the risk practitioner s FIRST course of action when an organization has decided to expand into new product areas?
Identify any new business objectives with stakeholders.
Present a business case for new controls to stakeholders.
Revise the organization's risk and control policy.
Review existing risk scenarios with stakeholders.
The first course of action for the risk practitioner when an organization has decided to expand into new product areas is to identify any new business objectives with stakeholders. Business objectives are the specific, measurable, achievable, relevant, and time-bound (SMART) goals that the organization aims to accomplish through its products and services. Stakeholders are the parties who have an interest or influence in the organization and its products and services, such as customers, employees, shareholders, suppliers, regulators, or competitors. Identifying any new business objectives with stakeholders is the first course of action, because it helps to understand and define the purpose, scope, and criteria of the new product areas, and to align them with the organization’s vision, mission, and strategy. Identifying any new business objectives with stakeholders also helps to establish the expectations, needs, and requirements of the stakeholders, and to ensure their engagement and support for the new product areas. Identifying any new business objectives with stakeholders is the basis for the subsequent risk management activities, such as identifying, analyzing, evaluating, and responding to the risks associated with the new product areas. The other options are not the first course of action, although they may be related or subsequent steps in the risk management process. Presenting a business case for new controls to stakeholders is a part of the risk response process, which involves selecting and executing the appropriate actions to reduce, avoid, share, or exploit the risks associated with the new product areas. Presenting a business case for new controls to stakeholders can help to justify and communicate the value and impact of the new controls, and to obtain the approval and resources for implementing them. However, this is not the first course of action, as it depends on the identification and prioritization of the business objectives and the risks. Revising the organization’s risk and control policy is a part of the risk governance process, which involves defining and updating the rules and guidelines for managing the risks and the controls associated with the new product areas. Revising the organization’s risk and control policy can help to ensure the consistency and effectiveness of the risk management process, and to comply with the relevant laws and regulations. However, this is not the first course of action, as it follows the identification and assessment of the business objectives and the risks. Reviewing existing risk scenarios with stakeholders is a part of the risk monitoring and review process, which involves evaluating and improving the performance and outcomes of the risk management process for the new product areas. Reviewing existing risk scenarios with stakeholders can help to identify and address any changes or issues in the risk levels or the risk responses, and to provide feedback and learning for the risk management process. However, this is not the first course of action, as it requires the identification and analysis of the business objectives and the risks. References = Risk Scenarios Toolkit - ISACA, How to Write Strong Risk Scenarios and Statements - ISACA, The Role of Executive Management in ERM - Corporate Compliance Insights
The PRIMARY objective of the board of directors periodically reviewing the risk profile is to help ensure:
the risk strategy is appropriate
KRIs and KPIs are aligned
performance of controls is adequate
the risk monitoring process has been established
The PRIMARY objective of the board of directors periodically reviewing the risk profile is to help ensure that the risk strategy is appropriate, because the risk strategy defines the enterprise’s risk appetite, tolerance, and objectives, and guides the risk management process and activities. The board of directors should review the risk profile to ensure that it reflects the current internal and external environment, and that it aligns with the enterprise’s strategy and goals. The other options are not the primary objective, because:
Option B: KRIs and KPIs are aligned is a desirable outcome of the risk strategy, but not the primary objective of the board of directors reviewing the risk profile. KRIs and KPIs are indicators that measure and monitor the risk exposure and performance of the enterprise, respectively, and they should be consistent with the risk strategy and objectives.
Option C: Performance of controls is adequate is a result of the risk response, but not the primary objective of the board of directors reviewing the risk profile. Performance of controls is the degree to which the controls are effective and efficient in mitigating the risks, and it should be evaluated and reported by the risk management function and the internal audit function.
Option D: The risk monitoring process has been established is a prerequisite for the risk profile, but not the primary objective of the board of directors reviewing the risk profile. The risk monitoring process is the process of tracking and reporting the risk status and performance, and it should be implemented and executed by the risk management function and the business process owners. References = Risk and Information Systems Control Study Manual, 7th Edition, ISACA, 2020, p. 119.
Performing a background check on a new employee candidate before hiring is an example of what type of control?
Detective
Compensating
Corrective
Preventive
A control is an action or measure that reduces the likelihood or impact of a risk to an acceptable level. Controls can be classified into different types based on their purpose or function, such as detective, compensating, corrective, or preventive. Performing a background check on a new employee candidate before hiring is an example of a preventive control. A preventive control is a control that aims to prevent the occurrence or manifestation of a risk, such as by avoiding, removing, or reducing the risk sources, causes, or drivers. A background check is a process that verifies the identity, qualifications, and history of a potential employee, and helps to ensure that the employee is suitable and trustworthy for the job. A background check can prevent the risk of hiring an unqualified, fraudulent, or malicious employee, who could compromise the performance, security, or compliance of the enterprise. The other options are not examples of preventive controls, as they involve different types of controls:
A detective control is a control that aims to detect the occurrence or manifestation of a risk, such as by monitoring, measuring, or reporting the risk events, indicators, or outcomes. An example of a detective control is a log review, which is a process that analyzes the records of the activities or transactions on the IT systems or applications, and helps to identify any anomalies, errors, or violations that could indicate a risk.
A compensating control is a control that aims to compensate for the weakness or deficiency of another control, such as by providing an alternative or additional level of protection or assurance. An example of a compensating control is a firewall, which is a device or software that filters the network traffic and blocks the unauthorized or malicious access to the IT systems or applications, and helps to compensate for the lack or failure of other security controls, such as encryption, authentication, or authorization.
A corrective control is a control that aims to correct the occurrence or manifestation of a risk, such as by restoring, repairing, or improving the affected assets, processes, or functions. An example of a corrective control is a backup, which is a copy or replica of the data or information on the IT systems or applications, and helps to correct the loss or damage of the data or information due to a risk, such as a hardware failure, a software error, or a cyberattack. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.3.3.1, pp. 62-63.
Which of the following is the BEST method for identifying vulnerabilities?
Batch job failure monitoring
Periodic network scanning
Annual penetration testing
Risk assessments
The best method for identifying vulnerabilities is periodic network scanning. Network scanning is a process of scanning and probing the network devices, systems, and applications to discover and analyze their security weaknesses, such as configuration errors, outdated software, or open ports. Network scanning can help to identify the vulnerabilities that could be exploited by attackers to gain unauthorized access, compromise data, or disrupt services. Periodic network scanning is the best method, because it can provide a regular and comprehensive view of the network security posture, and it can detect and address the new or emerging vulnerabilities in a timely manner. Periodic network scanning can also help to comply with the legal and regulatory requirements and standards for network security, such as the ISO/IEC 27001, the NIST SP 800-53, or the PCI DSS123. The other options are not the best method, although they may be useful or complementary to periodic network scanning. Batch job failure monitoring is a process of monitoring and reporting the failures or errors that occur during the execution of batch jobs, such as data processing, backup, or synchronization. Batch job failure monitoring can help to identify the operational or technical issues that affect the performance or availability of the network services, but it does not directly identify the security vulnerabilities or the potential threats. Annual penetration testing is a process of simulating a real-world attack on the network devices, systems, and applications to evaluate their security defenses and resilience. Penetration testing can help to identify and exploit the vulnerabilities that could be used by attackers to compromise the network security, and to provide recommendations for improvement. However, annual penetration testing is not the best method, because it is not frequent or consistent enough to keep up with the changing and evolving network security landscape, and it may not cover all thenetwork components or scenarios. Risk assessments are a process of identifying, analyzing, and evaluating the risks associated with the network devices, systems, and applications. Risk assessments can help to estimate the probability and impact of the vulnerabilities and the threats, and to prioritize and respond to the risks accordingly. However, risk assessments are not the same as or a substitute for vulnerability identification, as they rely on the vulnerability information as an input, rather than an output. References = Vulnerability Testing: Methods, Tools, and 10 Best Practices, ISO/IEC 27001 Information Security Management, NIST SP 800-53 Rev. 5
IT disaster recovery point objectives (RPOs) should be based on the:
maximum tolerable downtime.
maximum tolerable loss of data.
need of each business unit.
type of business.
IT disaster recovery point objectives (RPOs) should be based on the:
B. maximum tolerable loss of data.
RPOs are determined by how much data loss an organization can withstand in the event of a disaster. It’s a measure of the maximum age of files that an organization must recover from backup storage for normal operations to resume after a disaster. Therefore, RPOs are directly related to the maximum tolerable loss of data.
Which of the following is MOST helpful in determining the effectiveness of an organization's IT risk mitigation efforts?
Assigning identification dates for risk scenarios in the risk register
Updating impact assessments for risk scenario
Verifying whether risk action plans have been completed
Reviewing key risk indicators (KRIS)
Key risk indicators (KRIs) are metrics that provide information about the level of exposure to a specific risk or a group of risks.
Reviewing KRIs is the most helpful way to determine the effectiveness of an organization’s IT risk mitigation efforts. This means that the organization monitors and evaluates the actual results and outcomes of the risk responses, compares them with the risk appetite and tolerance of the organization, identifies any deviations or breaches that may require attention or action, and reports them to the appropriate parties for decision making or improvement actions.
The other options are not the most helpful ways to determine the effectiveness of an organization’s IT risk mitigation efforts. They are either secondary or not essential for risk management.
The references for this answer are:
Risk IT Framework, page 15
Information Technology & Security, page 9
Risk Scenarios Starter Pack, page 7
Which of the following is the MOST important reason to revisit a previously accepted risk?
To update risk ownership
To review the risk acceptance with new stakeholders
To ensure risk levels have not changed
To ensure controls are still operating effectively
The most important reason to revisit a previously accepted risk is to ensure that the risk levels have not changed. A previously accepted risk is a risk that the organization has decided to tolerate or retain without taking any further action, because the risk is either low or unavoidable, or the cost or effort of mitigation outweighs the potential benefit. However, risk acceptance is not a static or permanent decision, as the risk levels may change over time due to various factors, such as new threats, vulnerabilities, impacts, or opportunities. Therefore, it is essential to revisit a previously accepted risk periodically or when there is a significant change in the internal or external environment, to verify that the risk is still within the acceptable range and that the risk acceptance rationale is still valid. If the risk levels have increased or decreased, the organization may need to revise the risk acceptance decision and consider other risk response options, such as avoidance, reduction, sharing, or exploitation. The other options are not the most important reason to revisit a previously accepted risk, although they may be relevant or necessary depending on the context and nature of the risk. Updating risk ownership is a part of the risk governance process, which ensures that the roles and responsibilities for managing the risk are clearly defined and assigned, but it does not affect the risk levels or the risk acceptance decision. Reviewing the risk acceptance with new stakeholders is a part of the risk communication process, which ensures that the risk information and the risk acceptance rationale are shared and understood by the relevant parties, but it does not change the risk levels or the risk acceptance decision. Ensuring that the controls are still operating effectively is a part of the risk monitoring and review process, which ensures that the risk response actions are implemented and maintained properly, but it does not apply to the accepted risks, as they do not have any additionalcontrols. References = Understanding Accepted Risk - SC Dashboard | Tenable®, Risk Acceptance — ENISA, Accepting Risk - Overview, Advantages, Disadvantages, Alternatives
Which of the following provides the MOST helpful reference point when communicating the results of a risk assessment to stakeholders?
Risk tolerance
Risk appetite
Risk awareness
Risk policy
According to the CRISC Review Manual1, risk tolerance is the acceptable level of variation that management is willing to allow for any particular risk as it pursues its objectives. Risk tolerance provides a helpful reference point when communicating the results of a risk assessment to stakeholders, as it helps to compare the current level of risk exposure with the desired level of risk exposure, and to prioritize and allocate resources for risk response. Risk tolerance also helps to align the risk assessment results with the stakeholder expectations and preferences, and to facilitate risk-based decision making. References = CRISC Review Manual1, page 192.
Once a risk owner has decided to implement a control to mitigate risk, it is MOST important to develop:
a process for measuring and reporting control performance.
an alternate control design in case of failure of the identified control.
a process for bypassing control procedures in case of exceptions.
procedures to ensure the effectiveness of the control.
Once a risk owner has decided to implement a control to mitigate risk, it is most important to develop a process for measuring and reporting control performance. This process helps to monitor and evaluate the actual results and outcomes of the control, compare them with the expected or desired objectives and standards, identify any gaps or issues that may affect the control’s effectiveness or efficiency, and report them to the relevant stakeholders for decision making or improvement actions.
An alternate control design in case of failure of the identified control is a contingency plan that can be used to reduce the impact of a control failure or breakdown. It is not the most important thing to develop after implementing a control, but rather a backup option that can be activated when needed.
A process for bypassing control procedures in case of exceptions is a mechanism that allows authorized users to override or circumvent a control in certain situations, such as emergencies, errors, or special requests. It is not the most important thing to develop after implementing a control, but rather a risk response that can be applied when necessary.
Procedures to ensure the effectiveness of the control are the steps or actions that are required to implement, operate, and maintain the control in accordance with the risk owner’s expectations and requirements. They are not the most important thing to develop after implementing a control, but rather a part of the control design and implementation process.
The references for this answer are:
Risk IT Framework, page 13
Information Technology & Security, page 7
Risk Scenarios Starter Pack, page 5
Which of the following conditions presents the GREATEST risk to an application?
Application controls are manual.
Application development is outsourced.
Source code is escrowed.
Developers have access to production environment.
The production environment is the environment where the application is deployed and used by the end users. The production environment should be protected from unauthorized or unintended changes that could compromise the availability, integrity, or confidentiality of the application and its data. Developers have access to the production environment presents the greatest risk to an application, as it could allow them tobypass the change management process, introduce errors or vulnerabilities, or manipulate the application or its data for malicious purposes. The other options are not as risky as developers having access to the production environment, as they involve different aspects of the application lifecycle:
Application controls are manual means that the application relies on human intervention to perform some functions or validations, such as data entry, reconciliation, or authorization. This could increase the risk of human error, fraud, or inefficiency, but it does not directly affect the production environment.
Application development is outsourced means that the application is developed by a third party, such as a vendor or a contractor. This could increase the risk of quality issues, contractual disputes, or intellectual property rights, but it does not directly affect the production environment.
Source code is escrowed means that the source code of the application is deposited with a trusted third party, such as a lawyer or a bank. This could provide assurance and continuity in case the original developer is unable or unwilling to maintain or support the application, but it does not directly affect the production environment. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 4, Section 4.1.1.1, pp. 144-145.
The MOST important reason to aggregate results from multiple risk assessments on interdependent information systems is to:
establish overall impact to the organization
efficiently manage the scope of the assignment
identify critical information systems
facilitate communication to senior management
The interdependency of information systems means that the failure or disruption of one system can affect the performance or availability of other systems. Therefore, it is important to aggregate the results from multiple risk assessments on interdependent information systems to understand the overall impact to the organization. By aggregating the results, the risk manager can identify the potential cascading effects, the cumulative consequences, and the worst-case scenarios of interdependent risks. This can help theorganization to prioritize the risks, allocate the resources, and implement the risk response strategies accordingly. The other options are not as important as the overall impact to the organization, because they do not capture the full extent of the interdependency of information systems. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.4.3, page 99.
The PRIMARY basis for selecting a security control is:
to achieve the desired level of maturity.
the materiality of the risk.
the ability to mitigate risk.
the cost of the control.
The PRIMARY basis for selecting a security control is the ability to mitigate risk, because it is the measure of how well the control can prevent or reduce the occurrence or impact of the risk, and how effectively the control can achieve the desired level of security and protection for the system and the data. The ability to mitigate risk is the most important criterion for selecting a security control, as it directly relates to the purpose and value of the control. The other options are not the primary basis, because:
Option A: To achieve the desired level of maturity is a goal of selecting a security control, but not the primary basis. The desired level of maturity is the state or condition of the security control that reflects its quality, consistency, and reliability, and it should be aligned with the organization’s security objectives and standards. The desired level of maturity is a result of selecting a security control, not a reason for selecting it.
Option B: The materiality of the risk is a factor of selecting a security control, but not the primary basis. The materiality of the risk is the degree or extent of the risk that affects the organization’s performance, reputation, and value, and it should be considered when selecting a security control, but it is not the only or the most important factor. The materiality of the risk is an input to selecting a security control, not an output of selecting it.
Option D: The cost of the control is a constraint of selecting a security control, but not the primary basis. The cost of the control is the amount of resources and expenditure that are required to implement and maintain the control, and it should be balanced with the benefit and effectiveness ofthe control, but it is not the only or the most important constraint. The cost of the control is a limitation of selecting a security control, not a motivation for selecting it. References = Risk and Information Systems Control Study Manual, 7th Edition, ISACA, 2020, p. 211.
A control owner has completed a year-long project To strengthen existing controls. It is MOST important for the risk practitioner to:
update the risk register to reflect the correct level of residual risk.
ensure risk monitoring for the project is initiated.
conduct and document a business impact analysis (BIA).
verify cost-benefit of the new controls being implemented.
The risk practitioner should verify the cost-benefit of the new controls being implemented to ensure that they are aligned with the enterprise’s risk appetite and strategy, and that they provide value to the business. The other options are not as important as verifying the cost-benefit of the new controls, because:
Option A: Updating the risk register is a good practice, but it does not provide assurance that the new controls are effective and efficient.
Option B: Ensuring risk monitoring for the project is initiated is also a good practice, but it is not as urgent as verifying the cost-benefit of the new controls, which should be done before the project is closed.
Option C: Conducting and documenting a BIA is not relevant to the scenario, as the project is already completed and the new controls are implemented. References = Risk and Information Systems Control Study Manual, 7th Edition, ISACA, 2020, p. 184.
Which of the following is performed after a risk assessment is completed?
Defining risk taxonomy
Identifying vulnerabilities
Conducting an impact analysis
Defining risk response options
Defining risk response options is performed after a risk assessment is completed. A risk assessment is the process of identifying, analyzing, and evaluating the risks that affect the enterprise’s objectives and operations. After a risk assessment is completed, the enterprise needs to define the risk response options, which are the actions that can be taken to address the risks. The risk response options include accepting, avoiding, transferring, mitigating, or exploiting the risks. Defining risk response options helps to select the most appropriate and effective strategy to manage the risks. Defining risk taxonomy, identifying vulnerabilities, and conducting an impact analysis are performed before or during a risk assessment, not after. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 2, Section 2.1.1.4, page 541
1: ISACA Certified in Risk and Information Systems Control (CRISC®) Exam Guide, Answer to Question 644.
The PRIMARY purpose of vulnerability assessments is to:
provide clear evidence that the system is sufficiently secure.
determine the impact of potential threats.
test intrusion detection systems (IDS) and response procedures.
detect weaknesses that could lead to system compromise.
The primary purpose of vulnerability assessments is to detect weaknesses that could lead to system compromise. A vulnerability assessment is a systematic review of security weaknesses in an information system. It evaluates if the system is susceptible to any known vulnerabilities, assigns severity levels to those vulnerabilities, and recommends remediation or mitigation, if and whenever needed1. By identifying and prioritizing the vulnerabilities, a vulnerability assessment helps to prevent or reduce the risk of cyberattacks that could exploit the vulnerabilities and compromise the system. The other options are not the primary purpose, but they may be secondary or tertiary outcomes or benefits of a vulnerability assessment. Providing clear evidence that the system is sufficiently secure is a result of a successful vulnerability assessment and remediation process, but it is not the main objective. Determining the impact of potential threats is a part of the risk assessment process, which complements the vulnerability assessment process, but it is not the same as detecting the vulnerabilities. Testing intrusion detection systems (IDS) and response procedures is a part of the penetration testing process, which simulates a real-world attack on the system to evaluate its security posture, but it is not the same as scanning the system for vulnerabilities. References = What is Vulnerability Assessment | VA Tools and Best Practices - Imperva
Which of the following BEST enables the risk profile to serve as an effective resource to support business objectives?
Engaging external risk professionals to periodically review the risk
Prioritizing global standards over local requirements in the risk profile
Updating the risk profile with risk assessment results
Assigning quantitative values to qualitative metrics in the risk register
A risk profile is a summary of the key risks that affect an organization, a business unit, a process, or a project. A risk profile can help stakeholders understand the current and potential exposure to various sources of uncertainty, and prioritize the risk response accordingly. A risk profile should be aligned with the business objectives, which are the desired outcomes or results that the organization or the business unit wants to achieve. Updating the risk profile with risk assessment results best enables the risk profile to serve as an effective resource to support business objectives, because it ensures that the risk profile reflects the most accurate and up-to-date information about the risks and their impacts. Risk assessment is the process of analyzing and evaluating the likelihood and consequences of the identified risks, and comparing them with the risk criteria and appetite. Risk assessment results can provide valuable insights into the risk level, trend, and exposure, and help identify the most critical and relevant risks that need attention and action. Updating the risk profile with risk assessment results can help align the risk profile with the business objectives, by showing how the risks may affect the achievement of the objectives, and how the risk response can support or enhance the objectives. Updating the risk profile with risk assessment results can also help communicate and justify the risk profile to the business stakeholders, and obtain their feedback and approval. References = Risk Management Essentials: How to Develop a Risk Profile (TRN2-J07), Risk Assessment and Analysis Methods: Qualitative and Quantitative - ISACA, Using Risk Assessment to Support Decision Making - ISACA.
Which of the following BEST helps to balance the costs and benefits of managing IT risk?
Prioritizing risk responses
Evaluating risk based on frequency and probability
Considering risk factors that can be quantified
Managing the risk by using controls
Prioritizing risk responses helps to balance the costs and benefits of managing IT risk by ensuring that the most significant risks are addressed first and that the resources allocated to risk management are used efficiently and effectively. Evaluating risk based on frequency and probability is a part of risk analysis, not risk response. Considering risk factors that can be quantified is also a part of risk analysis, and it does not necessarily capture all the relevant aspects of risk. Managing the risk by using controls is a possible risk response, but it does not guarantee that the costs and benefits of risk management are balanced, as some controls may be too expensive or ineffective for the level of risk they mitigate. References = Risk and Information Systems Control Study Manual, Chapter 4: Risk Response, page 145.
Which of these documents is MOST important to request from a cloud service
provider during a vendor risk assessment?
Nondisclosure agreement (NDA)
Independent audit report
Business impact analysis (BIA)
Service level agreement (SLA)
A vendor risk assessment is a process of evaluating and managing the risks associated with outsourcing IT services or functions to a third-party provider, such as a cloud service provider.
One of the most important documents to request from a cloud service provider during a vendor risk assessment is an independent audit report. This is a report that provides an objective and reliable assurance on the quality, security, and performance of the cloud service provider’s operations, processes, and controls, based on the standards and criteria established by an independent auditor or a recognized authority, such as ISACA, ISO, NIST, etc.
An independent audit report helps to verify the compliance and effectiveness of the cloud service provider’s risk management practices, identify any gaps or issues that may affect the service delivery or security, and recommend improvements or corrective actions.
The other options are not the most important documents to request from a cloud service provider during a vendor risk assessment. They are either secondary or not essential for vendor risk management.
The references for this answer are:
Risk IT Framework, page 22
Information Technology & Security, page 16
Risk Scenarios Starter Pack, page 14
An organization has just implemented changes to close an identified vulnerability that impacted a critical business process. What should be the NEXT course of action?
Redesign the heat map.
Review the risk tolerance.
Perform a business impact analysis (BIA)
Update the risk register.
According to the CRISC Review Manual1, the risk register is a tool that records the results of risk identification, analysis, evaluation, and treatment. It should be updated whenever there is a change in the risk profile, such as when a vulnerability is closed or a new threat is identified. Updating the risk register allows the organization to monitor the current status of risks and the effectiveness of risk responses. Therefore, the next course of action after implementing changes to close an identifiedvulnerability is to update the risk register with the new information. References = CRISC Review Manual1, page 191.
A risk practitioner shares the results of a vulnerability assessment for a critical business application with the business manager. Which of the following is the NEXT step?
Develop a risk action plan to address the findings.
Evaluate the impact of the vulnerabilities to the business application.
Escalate the findings to senior management and internal audit.
Conduct a penetration test to validate the vulnerabilities from the findings.
According to the CRISC Review Manual1, a risk action plan is a document that defines the specific actions, resources, responsibilities, and timelines for implementing the risk responses. A risk action plan should be developed after the results of a vulnerability assessment are shared with the relevant stakeholders, such as the business manager, to address the identified vulnerabilities and mitigate the associated risks. Developing a risk action plan is the next step in the risk management process, as it helps to ensure that the risk responses are executed effectively and efficiently, and that the residual risks are within the acceptable levels. References = CRISC Review Manual1, page 201.
Who should be responsible for strategic decisions on risk management?
Chief information officer (CIO)
Executive management team
Audit committee
Business process owner
Strategic decisions on risk management are the decisions that involve setting the direction, objectives, and priorities for risk management within an organization, as well as aligning them with the organization’s overall strategy, vision, and mission1. Strategic decisions on risk management also involve defining the organization’s risk appetite and tolerance, which are the amount and level of risk that the organization is willing and able to accept to achieve its goals2. The responsibility for strategic decisions on risk management should belong to the executive management team, which is the group of senior leaders who have the authority and accountability for the organization’s performance and governance3. The executive management team has the best understanding of the organization’s strategic context, environment, and stakeholders, and can make informed and balanced decisions that consider the benefits and costs of risk-taking4. The executive management team also has the ability and responsibility to communicate and cascade the strategic decisions on risk management to the rest of the organization, and to monitor and evaluate their implementation and outcomes5. The chief information officer (CIO), the audit committee, and the business process owner are not the best choices for being responsible for strategic decisions on risk management, as they do not have the same level of authority and accountability as the executive management team. The CIO is the senior leader who oversees the organization’s information andtechnology strategy, resources, and systems6. The CIO may be involved in providing input and feedback to the executive management team on the strategic decisions on risk management, especially those related to IT risk, but they do not have the final say or the overall responsibility for them. The audit committee is a subcommittee of the board of directors that oversees the organization’s financial reporting, internal controls, and external audits7. The audit committee may be involved in reviewing and approving the strategic decisions on risk management, as well as ensuring their compliance with the relevant laws and standards, but they do not have the authority or the expertise to make or implement them. The business process owner is the person who has the authority and accountability for a business process that supports or enables the organization’s objectives and functions. The business process owner may be involved in executing and reporting on the strategic decisions on risk management, as well as identifying and mitigating the risks related to their business process, but they do not have the perspective or the influence to make or communicate them. References = 1: Strategic Risk Management: Complete Overview (With Examples)2: [Risk Appetite and Tolerance - ISACA] 3: [Senior Management - Definition, Roles andResponsibilities] 4: Stanford Strategic Decision and Risk Management | Stanford Online5: A 7-Step Process for Strategic Risk Management — RiskOptics - Reciprocity6: [Chief Information Officer (CIO) - Gartner ITGlossary] 7: [Audit Committee - Overview, Functions, and Responsibilities] : [Business Process Owner - Gartner IT Glossary] : [Business Process Owner - Roles and Responsibilities] : [Risk and Information Systems Control Study Manual, Chapter 1: IT Risk Identification, Section 1.1: IT Risk Concepts, pp. 17-19.]
A risk owner has accepted a high-impact risk because the control was adversely affecting process efficiency. Before updating the risk register, it is MOST important for the risk practitioner to:
ensure suitable insurance coverage is purchased.
negotiate with the risk owner on control efficiency.
reassess the risk to confirm the impact.
obtain approval from senior management.
A risk owner is the individual who is accountable for the management of a specific risk. A risk owner can decide to accept a high-impact risk if the control that mitigates the risk is adversely affecting the process efficiency. However, before updating the risk register, which is a document that records and tracks the identified risks and their responses, it is most important for the risk practitioner to obtain approval from senior management. Senior management is the group of executives who have the authority and responsibility for the strategic direction and performance of the organization. Obtaining approval from senior management can help ensure that the risk acceptance decision is aligned with the organization’s risk appetite and policies, and that the potential consequences of the high-impact risk are understood and accepted by the top-level decision makers. Obtaining approval from senior management can also help communicate and justify the risk acceptance decision to other stakeholders, such as regulators, auditors, customers, etc., and avoid any conflicts or misunderstandings that may arise from the risk acceptance decision. References = Why Assigning a Risk Owner is Important and How to Do It Right, Risk Ownership: A brief guide, Creating a Risk Register: All You Need to Know.
Which of the following is the BEST indicator of the effectiveness of a control action plan's implementation?
Increased number of controls
Reduced risk level
Increased risk appetite
Stakeholder commitment
The effectiveness of a control action plan’s implementation can be measured by the extent to which it achieves the desired risk reduction. A control action plan is a set of actions that are designed to address the root causes of a risk and mitigate its impact or likelihood. The best indicator of the effectiveness of a control action plan’s implementation is the reduced risk level, which means that the risk is either eliminated or brought within the acceptable range. The other options are not the best indicators, because they do not directly reflect the risk reduction. Increased number of controls may not necessarily reduce the risk level, especially if the controls are not aligned with the risk causes, objectives, and priorities. Increased risk appetite may indicate a higher tolerance for risk, but it does not mean that the risk level has been reduced. Stakeholder commitment may facilitate the implementation of the control action plan, but it does not guarantee the effectiveness of the plan. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 3: Risk Response, Section 3.2: Control Action Plan, p. 170-171.
Which of the following is the BEST key performance indicator (KPI) to measure the effectiveness of an anti-virus program?
Frequency of anti-virus software updates
Number of alerts generated by the anti-virus software
Number of false positives detected over a period of time
Percentage of IT assets with current malware definitions
An anti-virus program is a software that detects and removes malicious software, such as viruses, worms, or ransomware, from the IT assets, such as computers, servers, or networks. The effectiveness of an anti-virus program can be measured by the key performance indicators (KPIs) that reflect the achievement of the program objectives and the alignment with the enterprise’s risk appetite and tolerance. The best KPI to measure the effectiveness of an anti-virus program is the percentage of IT assets with current malware definitions. Malware definitions are the files or databases that contain the signatures or patterns of the known malicious software, and they are used by the anti-virus program to scan and identify the malware. The percentage of IT assets with current malware definitions indicates how well the anti-virus program is able to protect the IT assets from the latest or emerging threats, and reduce the exposure and impact of the risks associated with the malware. The other options are not as good as the percentage of IT assets with current malware definitions, as they may not reflect the quality or timeliness of the protection, or the alignment with the enterprise’s risk appetite and tolerance. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 4, Section 4.3.2.1, pp. 171-172.
Which of the following is MOST helpful to management when determining the resources needed to mitigate a risk?
An internal audit
A heat map
A business impact analysis (BIA)
A vulnerability report
A business impact analysis (BIA) is the most helpful tool to management when determining the resources needed to mitigate a risk. A BIA is a process of identifying and evaluating the potential effects of disruptions or incidents on the critical functions and processes of an organization. A BIA helps to estimate the financial, operational, and reputational impacts of risks, as well as the recovery time objectives and recovery point objectives for each function and process. A BIA also helps to prioritize the functions and processes based on their importance and urgency, and to allocate the resources needed to protect, restore,and resume them. A BIA can provide valuable information to management for developing and implementing risk mitigation strategies and plans. The other options are not the most helpful tools to management when determining the resources needed to mitigate a risk, although they may be useful or complementary to the BIA. An internal audit is a process of evaluating and improving the effectiveness of the governance, risk management, and control systems of an organization, but it does not directly estimate the impacts of risks or the resources needed to mitigate them. A heat map is a graphical tool that displays the probability and impact of individual risks in a matrix format, but it does not provide the details of the functions and processes affected by the risks or the resources needed to protect them. A vulnerability report is a document that identifies and assesses the security weaknesses in an information system, but it does not measure the impacts of risks or the resources needed to mitigate them. References = Business Impact Analysis (BIA) | Ready.gov, Business Impact Analysis - ISACA, Business Impact Analysis - Risk Management from MindTools.com
Which of the following is a KEY outcome of risk ownership?
Risk responsibilities are addressed.
Risk-related information is communicated.
Risk-oriented tasks are defined.
Business process risk is analyzed.
A key outcome of risk ownership is that risk responsibilities are addressed, as this means that the risk owner has the authority and accountability to manage the risk, and that the roles and expectations of the other stakeholders are clearly defined and agreed upon. Risk ownership is the process of assigning a person or entity with the responsibility to manage a particular risk. Risk ownership helps to ensure that the risk is properly identified, assessed, and treated, and that the risk status and performance are monitored and reported. The other options are not key outcomes of risk ownership, although they may be related or beneficial aspects of it. Risk-related information is communicated is an outcome of risk reporting, which is a part of risk monitoring and control. Risk-oriented tasks are defined is an outcome of risk response planning, which is a part of risk treatment. Business process risk is analyzed is an outcome of risk assessment, which is a part of risk identification and analysis. References = Risk and Information Systems Control Study Manual, Chapter 2: IT Risk Identification, page 47.
Within the three lines of defense model, the accountability for the system of internal control resides with:
the chief information officer (CIO).
the board of directors
enterprise risk management
the risk practitioner
The three lines of defense model is a framework that describes the roles and responsibilities of different functions in an organization for managing risks and controls.
The first line of defense is the operational management, which is responsible for implementing and maintaining effective controls, identifying and assessing risks, and reporting on risk and control performance.
The second line of defense is the risk management and compliance functions, which are responsible for establishing and overseeing the risk management framework, providing guidance and support to the operational management, and monitoring and reporting on risk and compliance issues.
The third line of defense is the internal audit function, which is responsible for providing independent and objective assurance on the adequacy and effectiveness of the risk management and control system, and recommending improvements.
Within the three lines of defense model, the accountability for the system of internal control resides with the chief information officer (CIO). The CIO is the senior executive who oversees the IT function of the organization, and is responsible for ensuring that the IT risks and controls are aligned with the business objectives and strategies, and are integrated with the enterprise risk management and governance processes.
The references for this answer are:
Risk IT Framework, page 20
Information Technology & Security, page 14
Risk Scenarios Starter Pack, page 12
A control owner responsible for the access management process has developed a machine learning model to automatically identify excessive access privileges. What is the risk practitioner's BEST course of action?
Review the design of the machine learning model against control objectives.
Adopt the machine learning model as a replacement for current manual access reviews.
Ensure the model assists in meeting regulatory requirements for access controls.
Discourage the use of emerging technologies in key processes.
The risk practitioner’s best course of action is to review the design of the machine learning model against the control objectives, because this will help to evaluate the suitability, effectiveness, and reliability of the model as a control measure. A machine learning model is a type of artificial intelligence that can learn from data and make predictions or decisions based on the data. A machine learning model can be used to automate or enhance the access management process, such as by identifying excessive access privileges, detecting unauthorized access, or recommending access rights. However, a machine learning model also introduces new risks and challenges, such as data quality, model accuracy, model bias, model explainability, model security, and model governance. Therefore, the risk practitioner should review the design of the machine learning model against the control objectives, which are the specific goals or outcomes that the control is intended to achieve. The control objectives can be derived from the IT risk management strategy, the IT governance framework, the IT policies and standards, and the regulatory requirements. The review of the machine learning model should cover the following aspects: - The data sources and inputs: The risk practitioner should verify that the data used to train and test the machine learning model is relevant, complete, accurate, consistent, and representative of the access management process and the access rights. The risk practitioner should also check that the data is collected, stored, processed, and transmitted in a secure and compliant manner, and that the data privacy and confidentiality are protected. - The model algorithms and outputs: The risk practitioner should validate that the model algorithms are appropriate, robust, and transparent for the access management process and the control objectives. The risk practitioner should also evaluate that the model outputs are accurate, reliable, and interpretable, and that they provide meaningful and actionable insights or recommendations for the access management process and the control objectives. - The model performance and monitoring: The riskpractitioner should measure and monitor the model performance and effectiveness against the control objectives and the predefined metrics and indicators. The risk practitioner should also ensure that the model is updated and maintained regularly to reflect the changes in the access management process and the access rights, and that the model is audited and reviewed periodically to ensure its compliance and quality. By reviewing the design of the machine learning model against the control objectives, the risk practitioner can ensure that the model is fit for purpose and adds value to the access management process and the control objectives. The risk practitioner can also identify and mitigate any potential risks or issues that may arise from the use of the machine learning model as a control measure. References = Risk and Information Systems Control Study Manual, Chapter 3: Risk Response and Mitigation, Section 3.3: Control Design and Implementation, pp. 124-1271, Manage roles in your workspace - Azure Machine Learning2, Dataset Inference: Ownership Resolution in Machine Learning3
Which of the following is a KEY responsibility of the second line of defense?
Implementing control activities
Monitoring control effectiveness
Conducting control self-assessments
Owning risk scenarios
The second line of defense is a group of functions that provide oversight, guidance, and monitoring of the risk management activities of the first line of defense. The second line of defense includes risk management, compliance, and internal control departments. Their key responsibility is to monitor the effectiveness of the control activities implemented by the first line of defense, and to report any issues or gaps to senior management and the board. The second line of defense also supports the first line of defense by providing frameworks, policies, tools, and techniques to identify, measure, and manage risks. The other options are not the key responsibility of the second line of defense, as explained below:
A. Implementing control activities is the responsibility of the first line of defense, which consists of the business units and process owners that own and manage the risks associated with their daily operations.
C. Conducting control self-assessments is a technique used by the first line of defense to evaluate the design and operation of their own controls, and to identify and report any deficiencies or improvement opportunities.
D. Owning risk scenarios is the responsibility of the first line of defense, which is accountable for the risks inherent in their business activities, and for developing and executing risk response strategies. References = Modernizing The Three Lines of Defense Model | Deloitte US, The second line of defence: fit for purpose, not an uncomfortable fit | Knowledge | Linklaters, COSO’s Take on the Three Lines of Defense | ERM - Enterprise Risk Management, Three Lines of Defense | Risk Management - Schneider Downs CPAs, What is the Three Lines of Defense Approach to Risk Management?
A recent internal risk review reveals the majority of core IT application recovery time objectives (RTOs) have exceeded the maximum time defined by the business application owners. Which of the following is MOST likely to change as a result?
Risk forecasting
Risk tolerance
Risk likelihood
Risk appetite
Recovery time objectives (RTOs) are the maximum acceptable time frames for restoring the critical functions and processes after a disruption1. RTOs are derived from the business impact analysis (BIA) andreflect the organization’s risk appetite, which is the amount of risk that an organization is willing to accept to achieve its objectives2. Risk tolerance is the level of risk a company is willing to tolerate, and it is affected by a number of factors, including how much uncertainty or financial loss can be tolerated and where those losses will impact operations3. Risk tolerance is used to measure if the risk exposure is within the risk appetite and to implement controls to reduce the residual risk to an acceptable level2. If the majority of core IT application RTOs have exceeded the maximum time defined by the business application owners, it means that the organization is not meeting its risk appetite and is exposed to more risk than it can accept. Therefore, the most likely change as a result is to adjust the risk tolerance to reflect the current reality and to take actions to improve the recovery capabilities and reduce the risk exposure4. Risk forecasting is the process of estimating the potential outcomes and impacts of future events that may affect the organization’s objectives5. Risk forecasting may change as a result of the RTOs exceeding the maximum time, but it is not the most likely change, as it does not directly address the gap between the risk appetite and the risk exposure. Risk likelihood is the probability of a risk event occurring5. Risk likelihood may change as a result of the RTOs exceeding the maximum time, but it is not the most likely change, as it does not directly measure the impact of the risk event on the organization’s objectives. Risk appetite is the amount of risk that an organization is willing to accept to achieve its objectives2. Risk appetite may change as a result of the RTOs exceeding the maximum time, but it is not the most likely change, as it is a strategic decision that reflects the organization’s vision and mission, and not a tactical response to a specific risk event. References = Risk and Information Systems Control Study Manual, Chapter 5: Risk Response and Mitigation, Section 5.3: Business Continuity Planning, pp. 227-238.
Deviation from a mitigation action plan's completion date should be determined by which of the following?
Change management as determined by a change control board
Benchmarking analysis with similar completed projects
Project governance criteria as determined by the project office
The risk owner as determined by risk management processes
Deviation from a mitigation action plan’s completion date should be determined by the risk owner as determined by risk management processes, because the risk owner is the person or entity who has the accountability and authority to manage the risk and its associated mitigation actions. The risk owner should monitor and report the progress and status of the mitigation action plan, and determine if there is any deviation from the expected completion date, based on the risk management processes and criteria. The other options are not the ones who should determine the deviation, because:
Option A: Change management as determined by a change control board is a process that ensures that any changes to the project scope, schedule, cost, or quality are controlled and approved, but it does not determine the deviation from the mitigation action plan’s completion date, which is a risk management activity.
Option B: Benchmarking analysis with similar completed projects is a technique that compares the performance and practices of the current project with those of similar or successful projects, but it does not determine the deviation from the mitigation action plan’s completion date, which is a risk management activity.
Option C: Project governance criteria as determined by the project office is a set of rules and standards that define the roles, responsibilities, and authority of the project stakeholders, but it does notdetermine the deviation from the mitigation action plan’s completion date, which is a risk management activity. References = Risk and Information Systems Control Study Manual, 7th Edition, ISACA, 2020, p. 122.
When communicating changes in the IT risk profile, which of the following should be included to BEST enable stakeholder decision making?
List of recent incidents affecting industry peers
Results of external attacks and related compensating controls
Gaps between current and desired states of the control environment
Review of leading IT risk management practices within the industry
The best thing to include when communicating changes in the IT risk profile is the gaps between the current and desired states of the control environment, as this shows the stakeholders the extent and impact of the changes, and the actions and resources needed to address them. The control environment is the set of policies, processes, and systems that provide reasonable assurance that the IT risks are identified, assessed, and treated effectively and efficiently. The current state of the control environment reflects the existing level and performance of the controls, and the residual risk that remains after the controls are applied. The desired state of the control environment reflects the target level and performance of the controls, and the risk appetite and tolerance of the organization. The gaps between the current and desired states of the control environment indicate the areas of improvement or enhancement for the IT risk management process, and the priorities and strategies for risk response. The other options are not the best things to include when communicating changes in the IT risk profile, although they may be useful or relevant information. A list of recent incidents affecting industry peers can provide some context and comparison for the IT risk profile, but it does not measure or explain the changes in the IT risk level or the control environment. Results of external attacks and related compensating controls can demonstrate the security and resilience of the IT systems and networks, but they do not cover the entire scope or spectrum of the IT risk profile or the control environment. A review of leading IT risk management practices within the industry can provide some insights and benchmarks for the IT risk management process, but it does not reflect the specific situation or needs of the organization or the stakeholders. References = Risk and Information Systems Control Study Manual, Chapter 5: Risk and Control Monitoring and Reporting, page 181.
Which of the following should a risk practitioner do FIRST when an organization decides to use a cloud service?
Review the vendor selection process and vetting criteria.
Assess whether use of service falls within risk tolerance thresholds.
Establish service level agreements (SLAs) with the vendor.
Check the contract for appropriate security risk and control provisions.
According to the CRISC EXAM TOPIC 2 LONG Flashcards, the first thing that a risk practitioner should do when an organization decides to use a cloud service is to review the vendor selection process and vetting criteria. This is because the vendor selection process and vetting criteria are essential steps to ensure that the cloud service provider meets the organization’s requirements and expectations, and that the risks associated with the cloud service are identified and managed. By reviewing the vendor selection process and vetting criteria, the risk practitioner can evaluate the quality, reliability, security, and compliance of the cloud service provider, and determine if the cloud service is suitable and beneficial for the organization. The risk practitioner can also identify any gaps or weaknesses in the vendor selection process and vetting criteria, and recommend improvements or alternatives accordingly. References = CRISC EXAM TOPIC 2 LONG Flashcards
From a risk management perspective, which of the following is the PRIMARY benefit of using automated system configuration validation tools?
Residual risk is reduced.
Staff costs are reduced.
Operational costs are reduced.
Inherent risk is reduced.
From a risk management perspective, the primary benefit of using automated system configuration validation tools is that they reduce the inherent risk, which is the risk that exists before any controls are applied. Automated system configuration validation tools can help to ensure that the system settings are consistent, compliant, and secure, and that they match the predefined standards and policies. This can reduce the likelihood and impact of errors, misconfigurations, vulnerabilities, or deviations that may compromise the system’s functionality, performance, or integrity. The other options are not the primary benefits of using automated system configuration validation tools, although they may be secondary benefits or outcomes of doing so. Residual risk is the risk that remains after the controls are applied, and it may not be directly affected by the automated system configuration validation tools. Staff costs and operational costs are related to the efficiency and economy of the system configuration process, but they are not the main risk management objectives. References = Risk and Information Systems Control Study Manual, Chapter 4: Risk Response, page 150.
Which of the following should be included in a risk assessment report to BEST facilitate senior management's understanding of the results?
Benchmarking parameters likely to affect the results
Tools and techniques used by risk owners to perform the assessments
A risk heat map with a summary of risk identified and assessed
The possible impact of internal and external risk factors on the assessment results
A risk heat map is a graphical tool that displays the level of risk for each risk area based on the impact and likelihood of occurrence. It also provides a summary of the risk assessment results, such as the number and severity of risks, the risk appetite and tolerance, and the risk response strategies. A risk heat map can help senior management to understand the risk profile of the organization, prioritize the risks that need attention, and allocate resources accordingly. A risk heat map is more effective than the other options because it can communicate complex information in a simple and visual way, and it can highlight the key risk areas and trends. References = Risk and Information Systems Control Study Manual, Chapter 3, Section 3.4.2, page 97.
Which of the following is a detective control?
Limit check
Periodic access review
Access control software
Rerun procedures
A detective control is a type of internal control that seeks to uncover problems in a company’s processes once they have occurred. Examples of detective controls include physical inventory checks, reviews of account reports and reconciliations, as well as assessments of current controls1. A periodic access review is a detective control that involves verifying the access rights and privileges of users to ensure that they are appropriate and authorized. A periodic access review can help to detect any unauthorized or inappropriate access, such as excessive or redundant permissions, segregation of duties violations, or dormant ororphaned accounts23. The other options are not detective controls, but rather preventive controls, which are designed to prevent errors or fraud from occurring in the first place. A limit check is a preventive control that validates the input data against a predefined range or limit, and rejects any data that falls outside the acceptable range4. Access control software is a preventive control that restricts the access to information systems or resources based on the identity, role, or credentials of the user5. Rerun procedures are preventive controls that ensure the accuracy and completeness of data processing by repeating the same process and comparing the results6. References = Detective Control: Definition, Examples, Vs. Preventive Control; Detective Control - What Is It, Examples, Vs Preventive Control; Limit Check - an overview |ScienceDirect Topics; Access Control Software - an overview | ScienceDirect Topics; Rerun Procedures - an overview | ScienceDirect Topics
Which of the following BEST reduces the probability of laptop theft?
Cable lock
Acceptable use policy
Data encryption
Asset tag with GPS
According to the CRISC Review Manual1, a cable lock is a physical security device that attaches a laptop to a fixed object, such as a desk or a wall, to prevent unauthorized removal or theft. A cable lock is the best option to reduce the probability of laptop theft, as it acts as a deterrent and a barrier for potential thieves. A cable lock also helps to protect the confidentiality, integrity, and availability of the data stored on the laptop, as well as the laptop itself. References = CRISC Review Manual1, page 253.
An organization with a large number of applications wants to establish a security risk assessment program. Which of the following would provide the MOST useful information when determining the frequency of risk assessments?
Feedback from end users
Results of a benchmark analysis
Recommendations from internal audit
Prioritization from business owners
A benchmark analysis is a process of comparing the organization’s performance, practices, and processes with those of other organizations in the same industry or sector. A benchmark analysis can provide the most useful information when determining the frequency of risk assessments, because it can help the organization to identify the best practices, standards, and expectations for security risk management in its industry. A benchmark analysis can also help the organization to assess its current level of maturity, capability, and compliance in relation to security risk management, and to determine the gaps and areas for improvement. By conducting a benchmark analysis, the organization can establish a realistic and appropriate frequency of risk assessments that aligns with its industry norms and its own risk profile. The other options are not as useful as a benchmark analysis, because they do not provide a comprehensive and relevant view of the security risk management landscape, but rather focus on specific or partial aspects of the organization’s situation. References = Risk and Information Systems Control Study Manual, Chapter 1, Section 1.3.2, page 18.
After undertaking a risk assessment of a production system, the MOST appropriate action is for the risk manager to:
recommend a program that minimizes the concerns of that production system.
inform the development team of the concerns, and together formulate risk reduction measures.
inform the process owner of the concerns and propose measures to reduce them
inform the IT manager of the concerns and propose measures to reduce them.
A risk assessment of a production system is a process of identifying, analyzing, evaluating, and treating the risks that may affect the performance, quality, or safety of the production system, which is a system that transforms inputs into outputs using various resources, processes, and technologies12.
The most appropriate action for the risk manager to take after undertaking a risk assessment of a production system is to inform the process owner of the concerns and propose measures to reduce them, which is a process of communicating and consulting with the person who is responsible for the design, operation, and improvement of the production system, and suggesting possible risk responses that can prevent, mitigate, transfer, or accept the risks34.
This action is the most appropriate because it ensures the involvement and collaboration of the process owner, who has the authority and accountability to implement and monitor the risk responses, and who can provide feedback and input on the feasibility and effectiveness of the proposed measures34.
This action is also the most appropriate because it supports the risk management process and objectives, which are to identify and address the risks that may affect the achievement of the organization’s goals and the delivery of value to the stakeholders34.
The other options are not the most appropriate actions, but rather possible alternatives or supplements that may have some limitations or drawbacks. For example:
Recommending a program that minimizes the concerns of the production system is an action that involves designing and planning a set of coordinated and interrelated activities and tasks that aim to reduce the likelihood or impact of the risks34. However, this action is notthe most appropriate because it does not involve the process owner, who is the key stakeholder and decision maker for the production system, and who may have different views or preferences on the risk responses34.
Informing the development team of the concerns, and together formulating risk reduction measures is an action that involves communicating and consulting with the group of people who are responsible for creating, testing, and deploying the products or services that are produced by the production system, and jointly developing possible risk responses34. However, this action is not the most appropriate because it does not involvethe process owner, who is the primary owner and user of the production system, and who may have different needs or expectations on the risk responses34.
Informing the IT manager of the concerns and proposing measures to reduce them is an action that involves communicating and consulting with the person who is responsible for managing and overseeing the IT resources, processes, and systems that support the production system, and suggesting possible risk responses34. However, this action is not the most appropriate because it does not involve the process owner, who is the main stakeholder and beneficiary of the production system, and who may have different requirements or constraints on the risk responses34. References =
1: Risk Assessment for the Production Process1
2: Risk Assessment for Industrial Equipment2
3: Risk IT Framework, ISACA, 2009
4: IT Risk Management Framework, University of Toronto, 2017
Which of the following activities should only be performed by the third line of defense?
Operating controls for risk mitigation
Testing the effectiveness and efficiency of internal controls
Providing assurance on risk management processes
Recommending risk treatment options
Providing assurance on risk management processes is the activity that should only be performed by the third line of defense, because it is the role and responsibility of the independent and objective assurance function, such as internal audit or external audit, to evaluate and report on the effectiveness and efficiency of the risk management processes and controls. The third line of defense is the last layer of the three lines of defense model, which is a framework that defines the roles and responsibilities of different functions and levels within the organization for risk management and control. The first line of defense is the operational management and staff, who are responsible for identifying, assessing, and managing the risks and controls within their areas of responsibility. The second line of defense is the oversight and support functions, such as risk management, compliance, or legal, who are responsible for establishing and monitoring the risk policies, standards, and frameworks, and providing guidance and advice to the first line of defense. The third line of defense is the assurance function, who are responsible for providing independent and objective assurance on the adequacy and effectiveness of the risk management processes and controls, and reporting to the senior management and the board of directors. Operating controls for risk mitigation, testing the effectiveness and efficiency of internal controls, and recommending risk treatment options are all activities that can be performed by the first or second line of defense, but not by the third line of defense, as they are not part of the assurance function. References = Risk and Information Systems Control Study Manual, Chapter 2, Section 2.4.1, page 59
Which of the following is MOST important for a risk practitioner to understand about an organization in order to create an effective risk
awareness program?
Policies and procedures
Structure and culture
Key risk indicators (KRIs) and thresholds
Known threats and vulnerabilities

TESTED 19 Apr 2025

Copyright © 2014-2025 DumpsBuddy. All Rights Reserved

