Which technology is an open-source infrastructure automation tool that automates repetitive tasks for users who work in networks such as cloud provisioning and intraservice orchestration?
Company XYZ is running OSPF in their network. They have merged with another company that is running EIGRP as the routing protocol. Company XYZ now needs the two domains to talk to each other with redundancy, while maintaining a loop free environment. The solution must scale when new networks are added into the network in the near future. Which technology can be used to meet these requirements?
A European government passport agency considers upgrading its IT systems to increase performance and workload flexibility in response to constantly changing requirements. The budget manager wants to reduce capital expenses and IT staff and must adopt the lowest-cost technology. Which technology choice is suitable?
How many fully established neighbour relationships exist on an Ethernet with five routers running OSPF as network type broadcast?
Which actions are performed at the distribution layer of the three-layer hierarchical network design model? (Choose two)
An engineer is designing the QoS strategy for Company XYZ. Based on initial analysis, a lot of scavenger type of traffic is traversing the network's 20Mb Internet link toward the service provider. The new design must use a QoS technique that limits scavenger traffic to 2 Mbps, which helps avoid oversubscription of the link during times of congestion. Which QoS technique can be used to facilitate this requirement?
Organizations that embrace Zero Trust initiatives ranging from business policies to technology infrastructure can reap business and security benefits. Which two domains should be covered under Zero Trust initiatives? (Choose two)
A senior network designer suggests that you should improve network convergence times by reducing BGP timers between your CE router and the PE router of the service provider. Which two factors should you consider to adjust the timer values? (Choose two.)
A large enterprise customer has a single router that uses two active/active 10-Mbps internet links in one of its
offices. Each link currently handles approximately 7 Mbps of traffic, which is close to the full link capacity.
When a link fails, the failure leads to significantly degraded performance of all applications. Static routing is
used. The current ISP cannot deliver additional bandwidth capacity on the existing links. The customer needs
a network design that is resistant to failure, but does not increase CAPEX. Which solution should be proposed
to the customer?
VPLS is implemented in a Layer 2 network with 2000 VLANs. What is the primary concern to ensure successful deployment of VPLS?
Refer to the exhibit.
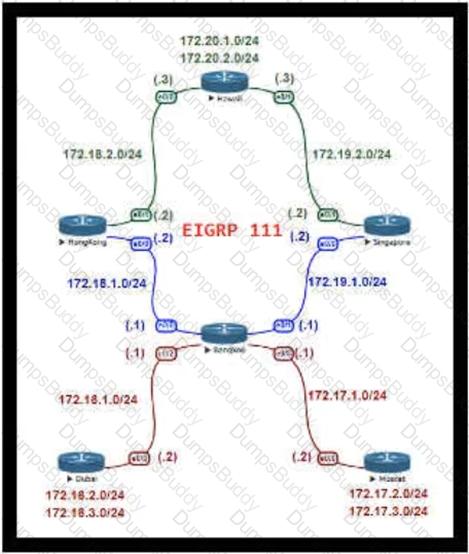
For Company XYZ Bangkok is using ECMP to reach the 172 20 2 0/24 network The company wants a design that would allow them to forward traffic from 172 16 2 0/24 toward 172 20 2 0/24 via the Singapore router as the preferred route The rest of the traffic should continue to use ECMP Which technology fulfills this design requirement?
Which two design solutions ensure sub 50 msec of the convergence time after a link failure in the network?
(Choose two)
Which two mechanisms avoid suboptimal routing in a network with dynamic mutual redistribution between multiple OSPFv2 and EIGRP boundaries? (Choose two.)
An enterprise requires MPLS connected branches to access cloud-based Microsoft 365 services over an SD-WAN solution. Internet access Is available only at dual regional hub sites that are connected to the MPLS network. Which connectivity method provides an optimum access method to the cloud-based services If one ISP suffers loss or latency?
Refer to the exhibit.
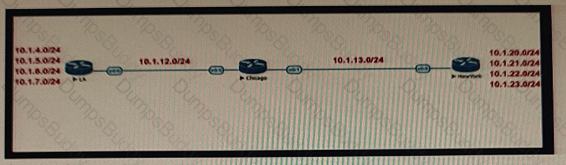
Company XYZ BGP topology is as shown in the diagram. The interface on the LA router connected toward the 10 1.5.0/24 network is faulty and is going up and down, which affects the entire routing domain. Which routing technique can the network administrator use so that the rest of the network is not affected by the flapping issue?
Which three components are part of the foundational information security principles of the CIA triad? (Choose three.)
As part of a new network design documentation, you are required to explain the reason for choosing cisco FabricPath for Layer 2 loop avoidance.
Which two elements help Cisco FabricPath mitigate Layer 2 loops if they happen in the Layer 2 MP network?
(Choose two)
You want to split an Ethernet domain in two.
Which parameter must be unique in this design to keep the two domains separated?
In a redundant hub and spoke "wheel" design, all spokes are connected to the hub, and spokes are connected to other spokes as well. During failure on one spoke link, the traffic from that site can be sent to a neighboring site for it to be forwarded to the hub site. But during peak hours, a link is overloaded and traffic is re-routed to a neighbor, which subsequently becomes overloaded. This overload results in network traffic oscillation as the load varies at each spoke site. This design provides more redundancy but not more resiliency because the routing protocol must process many alternate paths to determine the lowest cost path. Which two design
changes help to improve resilience in this case? (Choose two.)
Company XYZ wants to redesign the Layer 2 part of their network and wants to use all available uplinks for increased performance. They also want to have end host reachability supporting conversational learning. However, due to design constraints, they cannot implement port-channel on the uplinks. Which other technique can be used to make sure the uplinks are in active/active state?
What are two examples of components that are part of an SDN architecture? (Choose two.)
What are two primary design constraints when a robust infrastructure solution is created? (Choose two.)
Refer to the table.
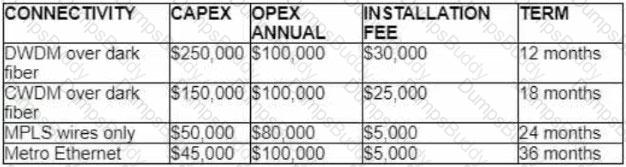
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The solution must provide a single 10G connection between locations and be able to run its own varying QoS profiles without service provider interaction based on the migration stages. All connectivity methods are at 10 Gbps. Which transport technology costs the least if the connectivity is required for just one year?
Company XYZ has a hub-and-spoke topology over an SP-managed infrastructure. To measure traffic performance metrics, they implemented IP SLA senders on all spoke CE routers and an IP SLA responder on the hub CE router. What must they monitor to have visibility on the potential performance impact due to the constantly increasing number of spoke sites?
A business invests in SDN and develops its own SDN controller that, due to budget constraints, runs on a single controller. The controller actively places an exclusive lock on the configuration of the devices to ensure it is the only source of changes to the environment. What is the result if the controller fails?
For a company that offers online billing systems for their customers, which strategy ensures the RPO is kept as low as possible?
A large enterprise cloud design team is evaluating different cloud consumption models. What is an example of typical PaaS limitations or concerns that should be considered during service design?
Refer to the exhibit.
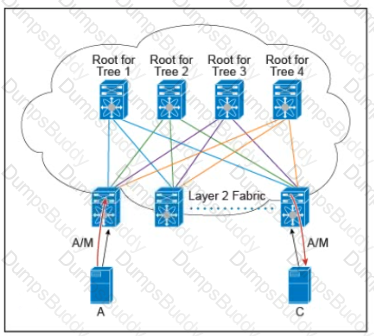
There are multiple trees in the Cisco FabricPath All switches in the Layer 2 fabric share the same view of each tree. Which two concepts describe how the multicast traffic is load-balanced across this topology? (Choose two )
Which two protocols are used bv SDN controllers to communicate with switches and routers? (Choose two )
A network security team uses a purpose-built tool to actively monitor the campus network, applications, and user activity. The team also analyzes enterprise telemetry data from IPFIX data records that are received from devices in the campus network. Which action can be taken based on the augmented data?
Refer to the diagram.

Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
What statement describes the application layer as defined in the software-defined networking architecture?
As more links are added to the network, information and attributes related to the link is added to the control plane meaning every link that gets added will slow down the convergence of the control plane by some measurable amount of time. As a result when additional redundancy is built or added the MTTR will increase too Which risk increases along with the increased MTTR?
While designing a switched topology, in which two options is UplinkFast recommended? (Choose two )
With virtualization being applied in many parts of the network every physical link is likely to carry one or more virtual links, but what is a drawback in cases like this?
What is the most important operational driver in building a resilient and secure modular network design?
Refer to the exhibit.
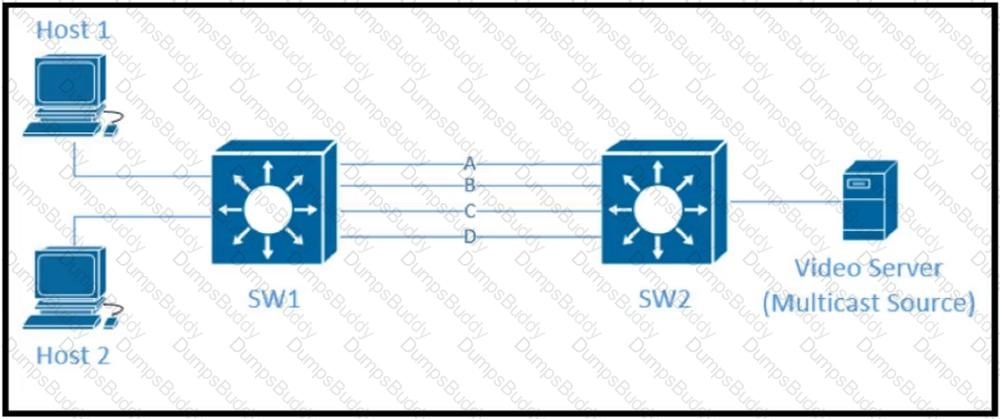
Traffic was equally balanced between Layer 3 links on core switches SW1 and SW2 before an introduction of the new video server in the network. This video server uses multicast to send video streams to hosts and now one of the links between core switches is over utilized Which design solution solves this issue?
An architect receives a functional requirement for a NAC system from a customer security policy stating that if a corporate Wi-Fi device does not meet current AV definitions, then it cannot access the corporate network until the definitions are updated. Which component should be built into the NAC design?
Company XYZ wants to implement an IPS device to detect and block well-known attacks against their network They want a design solution where all packets that are forwarded to the network are checked against a signature database before being allowed through This check must be done with the minimum effect on performance. Which design is recommended?
A business requirement stating that failure of WAN access for dual circuits into an MPLS provider for a Data Centre cannot happen due to related service credits that would need to be paid has led to diversely routed circuits to different points of presence on the providers network? What should a network designer also consider as part of the requirement?
A customer asks you to perform a high level review of their upcoming WAN refresh for remote sites The review is specially focused on their retail store operations consisting of 500+ locations connected via mutlipoint IPsec VPN solution. Which routing protocol would be valid but would also be the most restrictive for the expansion of this deployment model?
Which two aspects are considered when designing a dual hub dual DMVPN cloud topology? (Choose two )
Which two possible drawbacks should you consider when introducing Network Functions Virtualization in a network design? (Choose two)
In the case of outsourced IT services, the RTO is defined within the SLA. Which two support terms are often included in the SLA by IT and other service providers? (Choose two.)
A small organization of 20 employees is looking to deliver a network design service for modernizing customer networks to support advanced solutions.
Project scope and weekly progress should be visualized by the management.
Always consider feedback and make changes accordingly during the project.
Should consider flexibility to change scope at the point of time.
Which project methodology meets the requirements and have the least impact on the outcome?
Drag and drop the end-to-end network virtualization elements from the left onto the correct network areas on the right.
IPFIX data collection via standalone IPFIX probes is an alternative to flow collection from routers and switches. Which use case is suitable for using IPFIX probes?\
Which three items do you recommend for control plane hardening of an infrastructure device? (Choose three.)
You are a network designer and you must ensure that the network you design is secure. How do you plan to prevent infected devices on your network from sourcing random DDoS attacks using forged source address?
The controller has a global view of the network, and it can easily ensure that the network is in a consistent and optimal configuration. Which two statements describe a centralized SDN control path? (Choose two.)
A service provider hires you to design its new managed CE offering to meet these requirements
• The CEs cannot run a routing protocol with the PE
• Provide the ability for equal or unequal ingress load balancing in dual-homed CE scenarios.
• Provide support for IPv6 customer routes
• Scale up to 250.000 CE devices per customer.
• Provide low operational management to scale customer growth.
• Utilize low-end (inexpensive) routing platforms for CE functionality.
Which tunneling technology do you recommend?
While access lists are generally associated with routers and firewalls, they can also be applied on layer 2 interfaces and to VLANs to provide granular security. Which are two benefits of using layer 2 access lists for segmentation? (Choose two.)
Various teams in different organizations within an enterprise are preparing low-level design documents to capture network parameters using a Waterfall project model:
• hardware sizing and power consumption
• Layer 2 and layer 3 services parameters
• configuration of all control plane protocols
Input from relevant stakeholders was captured at the start of the project, and the project scope has been defined based on the parameters above. What impact will it have on documentation and project deliverables if the stakeholders ask to have changes carried out in the network before the information has been captured?
Which parameter is the most important factor to consider when deciding service placement in a cloud solution?
You are designing a large-scale DMVPN network with more than 500 spokes using EIGRP as the IGP protocol Which design option eliminates potential tunnel down events on the spoke routers due to the holding time expiration?
You are designing the QoS policy for a company that is running many TCP-based applications. The company is experiencing tail drops for these applications. The company wants to use a congestion avoidance technique for these applications. Which QoS strategy can be used to fulfill the requirement?
You have been asked to design a high-density wireless network for a university campus. Which two principles would you apply in order to maximize the wireless network capacity? (Choose two.)
An engineer must design a network for a company that uses OSPF LFA to reduce loops. Which type of loop would be reduced by using this design?
During evaluation of migrating current on premises infrastructure to add cloud-based infrastructure, a network planning team must meet three core requirements as they make recommendations on which cloud strategy to adopt going forward
• Technology is changing rapidly, therefore the enterprise must be open to adopting new ways of doing things, and be ready to invest CapEx-funds in the next three years
• Network bandwidth capacity requirements are dynamic and are expected to change over the next year
• If new technologies are to be introduced, operational expenses must be kept at a minimum. Which cloud strategy meets these requirements?
Company XYZ is planning to deploy primary and secondary (disaster recovery) data center sites. Each of these sites will have redundant SAN fabrics and data protection is expected between the data center sites. The sites are 100 miles (160 km) apart and target RPO/RTO are 3 hrs and 24 hrs, respectively. Which two considerations must Company XYZ bear in mind when deploying replication in their scenario? (Choose two.)
It is often seen that companies pick a cloud vendor solely based on technical preferences without putting enough weight on the business strategies that are driving the cloud initiatives Which strategic requirement may come into play where it is more likely that the decision makers will look to leverage laaS over SaaS or PaaS?
Retef to the exhibit.
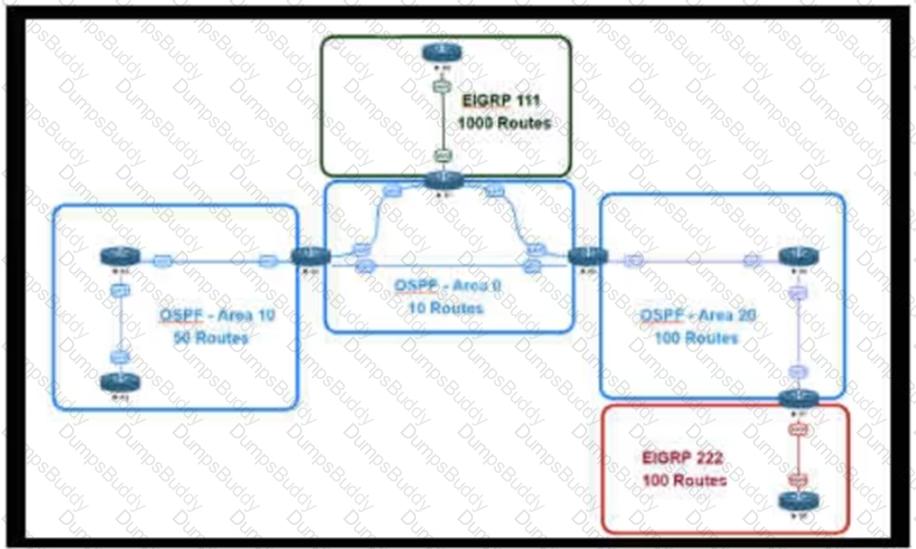
An engineer is designing a multiarea OSPF network for a client who also has a large EIGRP domain EIGRP routes are getting redistributed into OSPF ,OSPF area 20 has routers with limited memory and CPU resources The engineer wants to block routes from EIGRP 111 from propagating into area 20 and allow EIGRP 222 routes to How in Which OSPF area type fulfills this design requirement?
An engineer is designing a DMVPN network where OSPF has been chosen as the routing protocol A spoke-to-spoke 'J
Company XYZ asks for design recommendations for Layer 2 redundancy. The company wants to prioritize fast convergence and resiliency elements. In the design. Which two technologies are recommended? (Choose two.)
A European national bank considers migrating its on-premises systems to a private cloud offering in a non-European location to significantly reduce IT costs. What is a primary factor prior to migration?
Two enterprise networks must be connected together. Both networks are using the same private IP addresses.
The client requests from both sides should be translated using hide NAT (dynamic NAT) with the overload
feature to save IF addresses from the NAT pools. Which design addresses this requirement using only one
Cisco I OS NAT router for both directions?
Which layer of the SDN architecture orchestrates how the applications are given the resources available in the network?
An enterprise organization currently provides WAN connectivity to their branch sites using MPLS technology, and the enterprise network team is considering rolling out SD-WAN services for all sites.
With regards to the deployment planning, drag and drop the actions from the left onto the corresponding steps on the right.
Company XYZ network runs IPv4 and IPv6 and they want to Introduce a multidomain, multicast-based network. The new design should use a flavor of PIM that forwards traffic using SPT. Which technology meets this requirement?
Company XYZ needs advice in redesigning their legacy Layer 2 infrastructure. Which technology should be included in the design to minimize or avoid convergence delays due to STP or FHRP and provide a loop-free topology?
Which three items do you recommend for control plane hardening of an infrastructure device? (Choose three.)
Organic growth or decline comes from a company's normal business activities, rather than through acquisitions or divestment. Changes in usage patterns can also cause organic change in network requirements Which tool is useful when designing and operationalizing a network that is in the process of change?
An IT service provider is upgrading network infrastructure to comply with PCI security standards. The network team finds that 802.1X and VPN authentication based on locally-significant certificates are not available on some legacy phones.
Which workaround solution meets the requirement?
Your company utilizes many different types of network transports and you want to increase the efficiency of the network Which solution can be used to improve network efficiency over PPPoE IPsec, and GRE networks'?
Which extensions to GRE tunneling provide session tracking and in-order packet delivery in exchange for additional state stored in tunnel endpoints?
A network attacker exploits application flaws to compromise critical systems in the organization with these objectives:
• Obtain sensitive data and export the data out of the network.
• Compromise developer and administrator credentials to potentially
What is the next step after application discovery is completed in Zero Trust networkings
A network uses an SDN architecture with switches and a centralized controller What should be on the switches but not on the controller?
Refer to the exhibit.
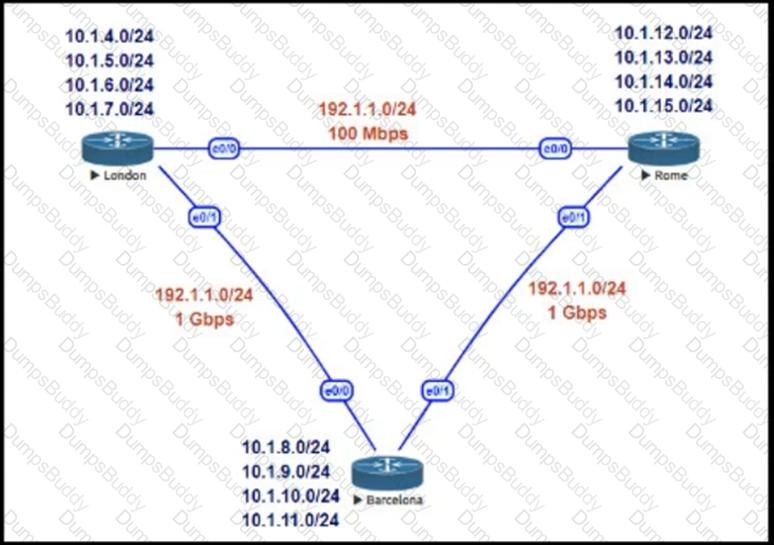
This network is running EIGRP as the routing protocol and the internal networks are being advertised in EIGRP. Based on the link speeds, all traffic between London and Rome is getting propagated via Barcelona and the direct link between London and Rome is not being utilized under normal working circumstances. The EIGRP design should allow for efficiency in the routing table by minimizing the routes being exchanged. The link between London and Rome should be utilized for specific routes. Which two steps accomplish this task? (Choose two.)
Which two areas of business presents a technical solution to support the company during emergency situations by understanding the data flows and using business processes to expiam how it answers to business needs and enables the business to improve'? (Choose two.)
Refer to the exhibit.
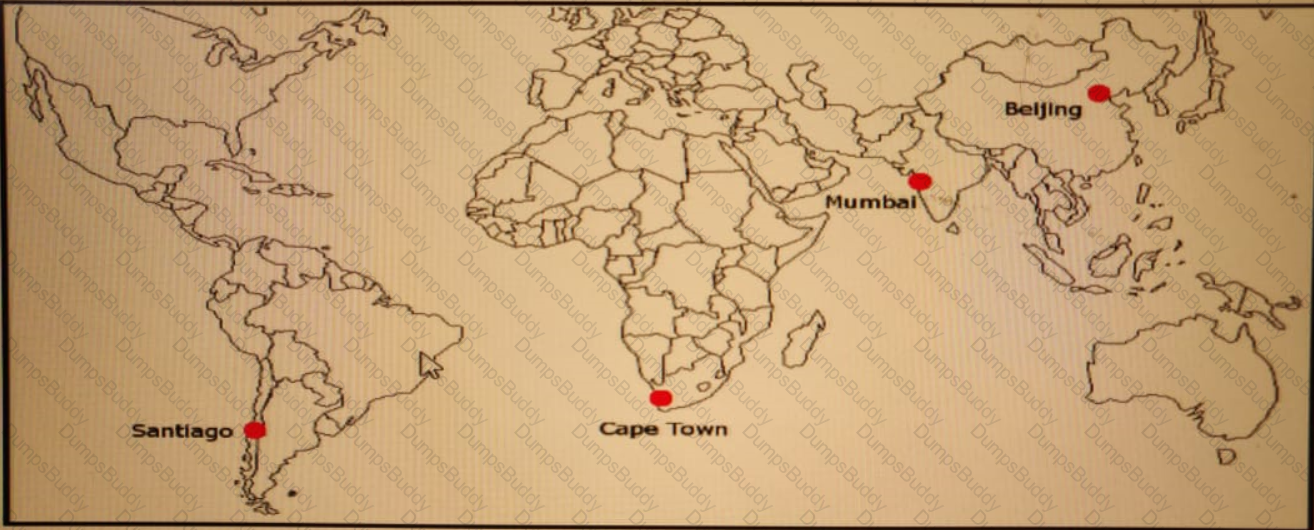
ACME Mining has four data centers in Santiago. Cape Town. Mumbai, and Beijing, full-mesh connected via a 400 Mb/s EVP-LAN They want to deploy a new mission-critical application with these
requirements:
cluster heartbeat 2 Mb/s continuous (250 KB/s)
cluster heartbeat one-way maximum latency 100 ms
These are the current ping tests results between the four data centers:
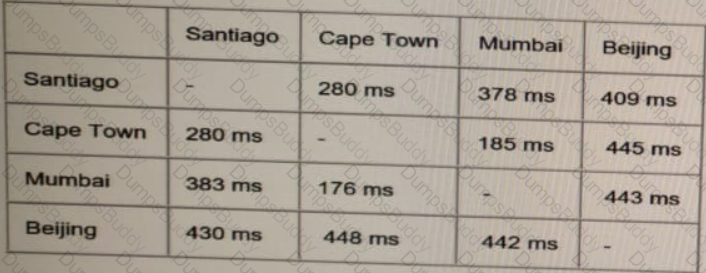
Which hosting data center pair can host the new application?
Enterprise XYZ wants to implement fast convergence on their network and optimize timers for OSPF However they also want to prevent excess flooding of LSAs if there is a constantly flapping link on the network Which timers can help prevent excess flooding of LSAs for OSPF?
Company XYZ is migrating their existing network to IPv6 and they must plan for Layer 2 and Layer 3 devices Some of the access layer switches do not support IPv6, however, core and distribution switches fully support unicast and multicast routing. The company wants to minimize cost of the migration. Which migration strategy should be used in the design?
Refer to the exhibit.
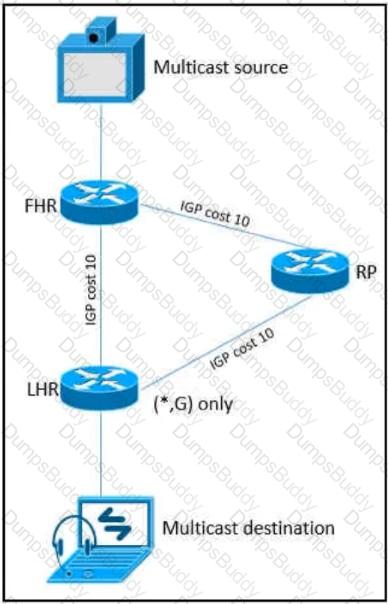
As part of a redesign project, you must predict multicast behavior What happens to the multicast traffic received on the shared tree (*,G), if it is received on the LHR interface indicated*?
Company XYZ uses an office model where the employees can use any open desk and plug their laptops in. They want to authenticate the end users using their domain username and password before allowing them access to the network. The design must also accommodate the ability of controlling traffic within the same group or subnet if a macro (or micro) segmentation-based model is adopted in the future. Which protocol can be recommended for this design to authenticate end users?
A product manufacturing organization is integrating cloud services into their IT solution The IT team is working on the preparation phase of the implementation approach, which includes the Define Strategy step. This step defines the scope of IT, the application, and the service What is one topic that should be considered in the Define Strategy step?
Refer to the exhibit.
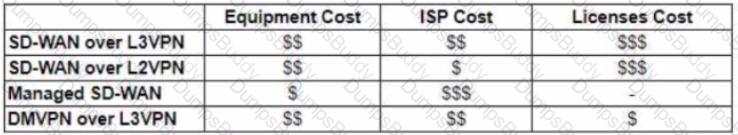
The WAN network of the General Bank of Greece has experienced several outages It takes too long to activate a new branch site The networking department of the bank plans to upgrade the legacy end-of-life WAN network with a new flexible manageable, and scalable in-house solution The number of branches will increase exponentially in the next fiscal year The CTO states that the bank’s mam goal is OPEX reduction The network engineering team prepares a table to evaluate the available options Which WAN technology can be used for the solution?
What are two top cloud-native security challenges faced by today's cloud-oriented organizations? (Choose two.)
What is a connection service inside a data center that provides direct connectivity to a cloud provider?
A network design includes a long signaling delay in notifying the Layer 3 control plane that an interface has failed Which two of these actions would reduce that delay? (Choose two.)
An enterprise solution team is performing an analysis of multilayer architecture and multicontroller SDN solutions for multisite deployments. The analysis focuses on the ability to run tasks on any controller via a standardized interface. Which requirement addresses this ability on a multicontroller platform?
A network engineering team is in the process of designing a lab network for a customer demonstration. The design engineer wants to show that the resiliency of the MPLS traffic Engineering Fast Reroute solution has the same failover/failback times as a traditional SONET/SDH network (around 50MSEC). In order to address both link failure and node failure within the lab typology network, which type of the MPLS TE tunnels must be considered for this demonstration?
A software-defined network can be defined as a network with an API that allows applications to understand and react to the state of the network in near real time. A vendor is building an SDN solution that exposes an API to the RIB and potentially the forwarding engine directly. The solution provides off-box processes with the capability to interact with the routing table in the same way as a distributed routing process. Which SDN framework model does the solution use?
Company XYZ wants to use the FCAPS ISO standard for network management design. The focus of the design should be to monitor and keep track of any performance issues by continuously collecting and analyzing statistical information to monitor, correct, and optimize any reduced responsiveness across the network. Which layer accomplishes this design requirement?
The network team in XYZ Corp wants to modernize their infrastructure and is evaluating an implementation and migration plan to allow integration MPLS-based, Layer 2 Ethernet services managed by a service provider to connect branches and remote offices. To decrease OpEx and improve
response times when network components fail, XYZ Corp decided to acquire and deploy new routers. The network currently is operated over E1 leased lines (2 Mbps) with a managed CE service provided by the telco.
Drag and drop the implementation steps from the left onto the corresponding targets on the right in the correct order.

A legacy enterprise is using a Service Provider MPLS network to connect its head office and branches. Recently, they added a new branch to their network. Due to physical security concerns, they want to extend their existing IP CCTV network of the head office to the new branch, without any routing changes in the network. They are also under some time constraints. What is the best approach to extend the existing IP CCTV network to the new branch, without incurring any IP address changes?
Cost is often one of the motivators for a business to migrate from a traditional network to a software- defined network. Which design decision is directly influenced by CAPEX drivers?
What are two key design principles when using a hierarchical core-distribution-access network model? (Choose two )
Refer to the exhibit.
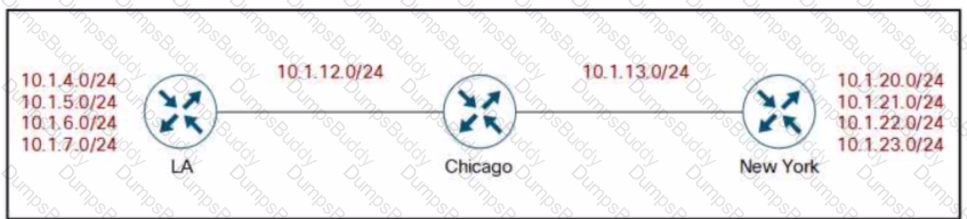
Company XYZ BGP topology is as shown in the diagram. The interface on the LA router connected toward the 10.1.5.0/24 network is faulty and is going up and down, which affects the entire routing domain. Which routing technique can be used in the routing policy design so that the rest of the network is not affected by the flapping issue?
The major business applications of an enterprise are largely monolithic and hard-coded As part of a major modernization and overhaul of the applications the goal is to move to a modular and containerized application architecture mode At the same time decoupling from the hardware is desired to move to an on-demand provisioning However the CyberOps team mandated that the final architecture must provide the same security levels as an air-gapped data center. Which cloud architecture meets these requirements?
The Agile Manifesto is a document that defines the key values and principles behind the Agile philosophy and helps development teams work more efficiently and sustainably Each of the four key values is split into two sections a left-hand side and a right-hand side In other words, though there is value in the items on the right we value the items on the left more What is one of the key values of the Agile Manifesto?
An IT services company offers cloud services to a banking customer. The banking customer has raised a ticket about unauthorized access and data loss. They use an authentication token on a mobile phone for authenticating access to the cloud platform from their local applications. The security response team has determined that the attacker used a phishing scheme in an effort to replace the token allowing them to direct the banking data to which policy change can help prevent identical situations in the future ?