How can an engineer prevent basic replay attacks from people who try to brute force a system via REST API?
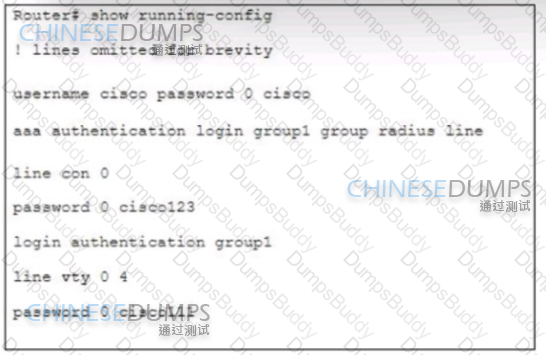
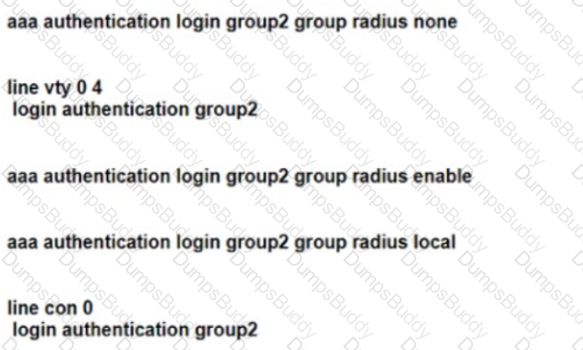
Refer to the exhibit. Authentication for users must first use RADIUS, and fall back to the local database on the router if the RADIUS server is unavailable Which two configuration sets are needed to achieve this result? (Choose two.)
Which location tracking method is used when locating client devices using Cisco hyperlocation?
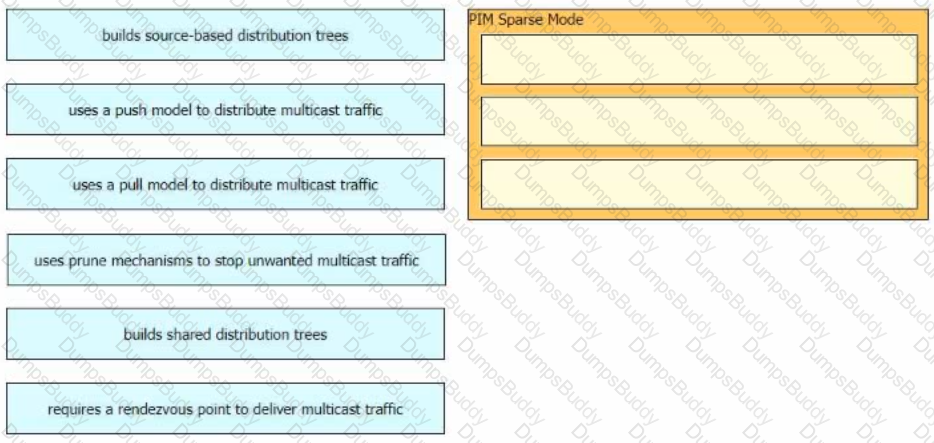
Drag and drop the characteristics of PIM Sparse Mode from the left to the right. Not all options are used.
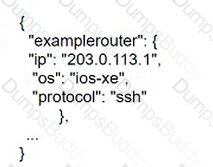
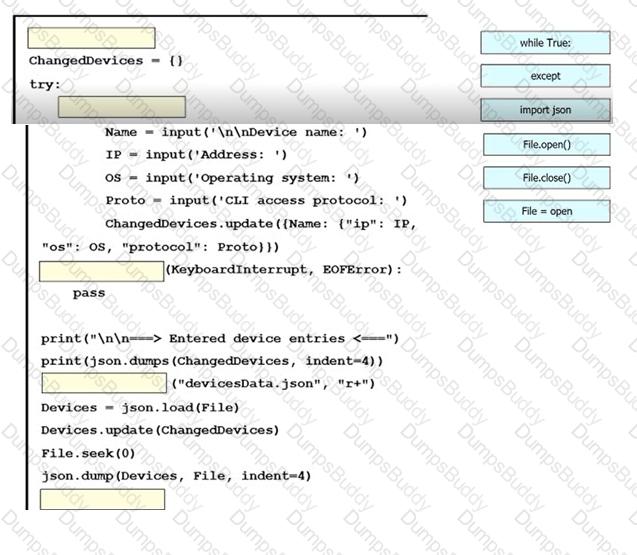
An engineer must create a script to append and modify device entries in a JSON-formatted file. The script must work as follows:
Until interrupted from the keyboard, the script reads in the hostname of a device, its management IP address, operating system type, and CLI remote access protocol.
After being interrupted, the script displays the entered entries and adds them to the JSON-formatted file, replacing existing entries whose hostname matches.
The contents of the JSON-formatted file are as follows
Drag and drop the statements onto the blanks within the code to complete the script. Not all options are used.
Which IEEE standard provides the capability to permit or deny network connectivity based on the user or device identity?
To support new clients in the environment, an engineer must enable Fast Transition on the corporate WLAN. Which command must be applied on a Cisco Catalyst 9800 Series WLC?
A script contains the statement white loop != 999 ’ Which value terminates the loop?
Which technology collects location information through data packets received by the APs instead of using mobile device probes?
An engineer must create a new SSID on a Cisco 9800 wireless LAN controller. The client has asked to use a pre-shared key for authentication. Which profile must the engineer edit to achieve this requirement?

Refer to the exibit. How should the programmer access the list of VLANs that are recevied via the API call?
A customer requires their wireless data traffic to egress at the switch port of the access point. Which access point mode supports this?
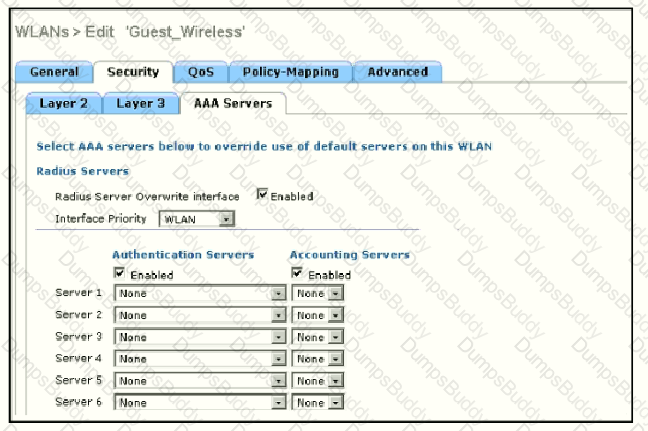
Assuming the WLC's interfaces are not in the same subnet as the RADIUS server, which interface would the WLC use as the source for all RADIUS-related traffic?

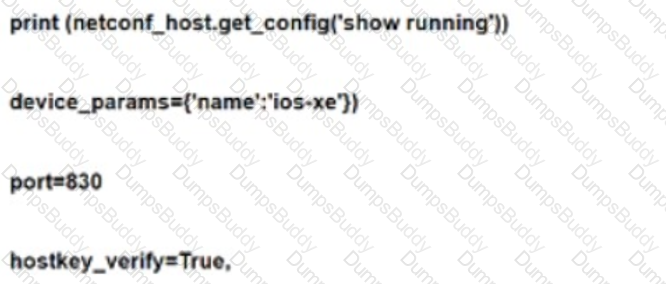
Refer to lhe exhibit. An engineer deploys a script to retrieve the running configuration from a NETCONF-capable Cisco IOS XE device that Is configured with default settings. The script fails. Which configuration must be applied to retrieve the configuration using NETCONF?
With IGMPv2, which multicast group address does the IGMP querier use to send query messages to all hosts on the LAN?