A small company has 5 servers and 50 clients. What are two reasons an engineer should spilt this network into separate client and server subnets? (Choose two)
Refer to the exhibit.
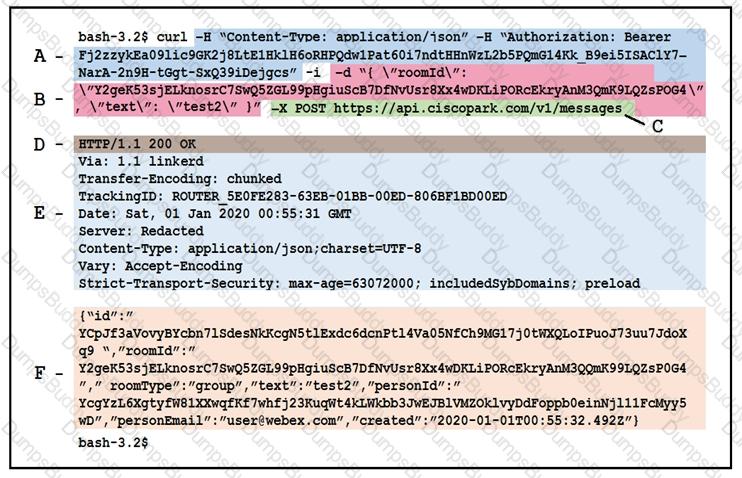
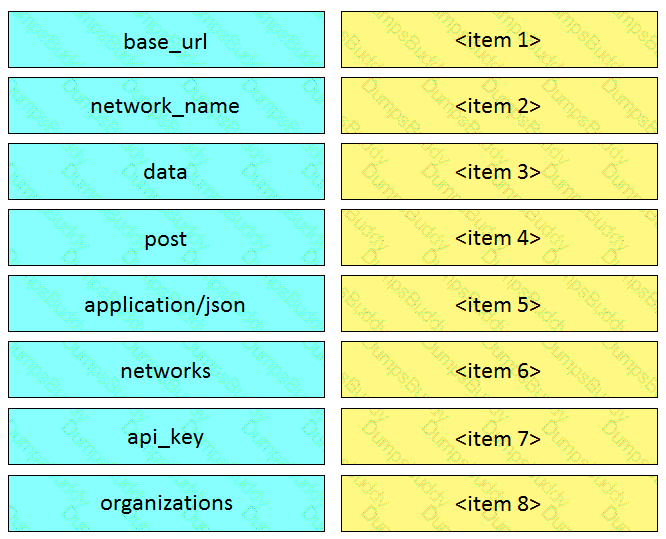
Drag and drop the descriptors from the left onto the correct parts of the API request and response on the right.
What are the two principles of an infrastructure as code environment? (Choose two)
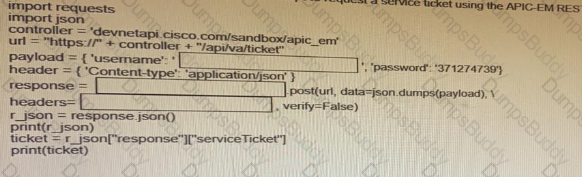
Fill in the blanks to complete the python script to request a service ticket using the APIC-EM rest API for the user “devnetuser”.
: 19 DRAG DROP
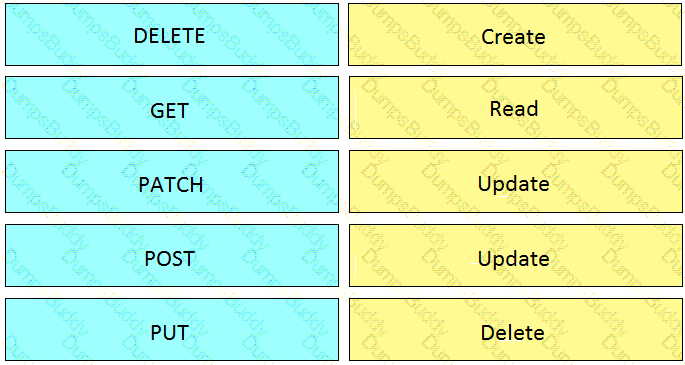
Drag and drop the HTTP methods from the left onto their generally accepted corresponding create, read, update, and delete operations on the right.
Fill in the blanks to complete the statement.
Given a username of “devnet” And a password “Cisco123”, applications must create a base64 encoding of the string” ____________ ” when sanding HTTP requests to an API that uses _______________ authentication.
Which statement about authentication a RESTCONF API session with a router that runs Cisco IOS XE software is true?
Which platform has an API that be used to obtain a list of vulnerable software on user devices?
Refer to the exhibit.
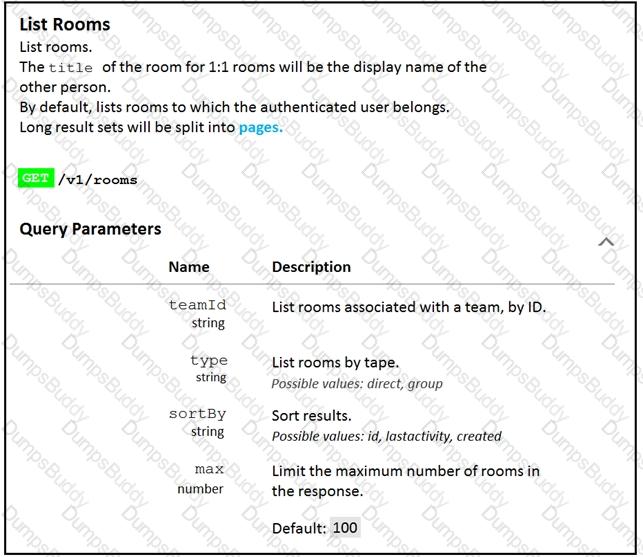
Fill in the blank to complete the query parameter and value so that the result set is returned in reverse chronological order (most recent first) based on when message were entered.

Which status code is used by a REST API to indicate that the submitted payload is incorrect?
Which model-driven programmability protocol does Cisco IOS XE Software support?
Refer to the exhibit.
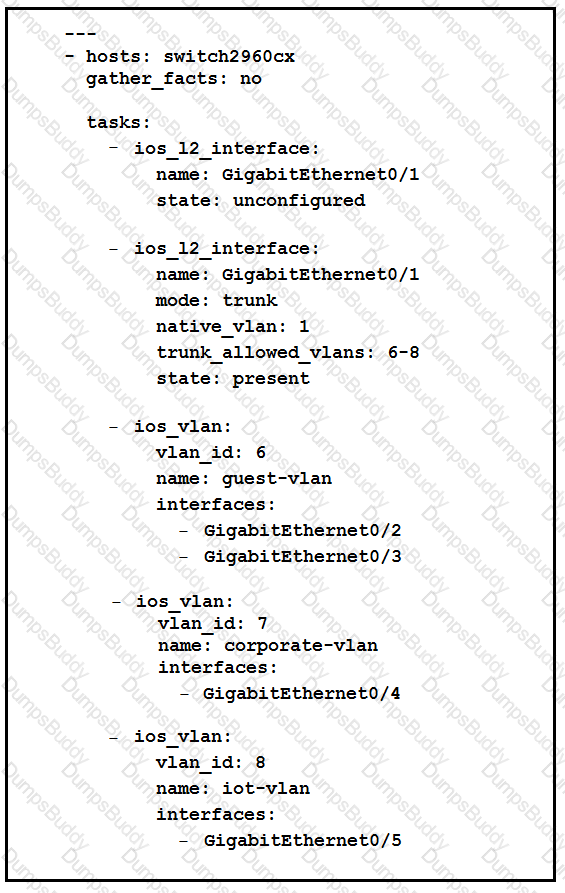
Which two statement describe the configuration of the Ansible script is run? (Choose two.)
Which type of threat occur when an attacker can send hostile data to an interpreter within an application?
A developer is reviewing a code that was written by a colleague. It runs fine, but there are many lines of code to do a seemingly simple task repeatedly. Which action organizes the code?
Which two statements describe the advantages of using a version control system? (Choose two.)
Refer to the exhibit.
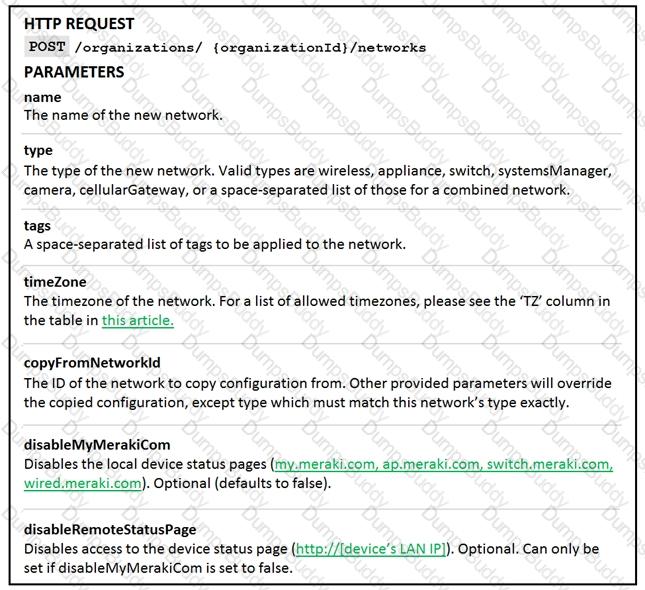
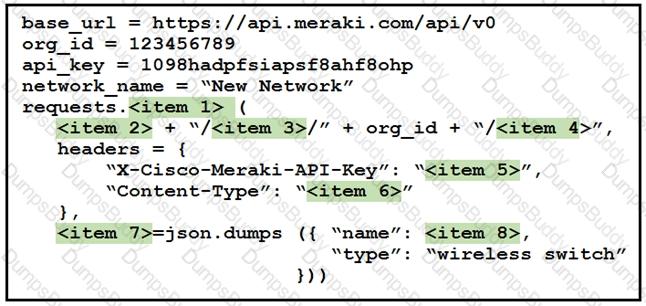
Drag and drop the code from the left onto the item numbers on the right to complete to Meraki python script shown in the exhibit.
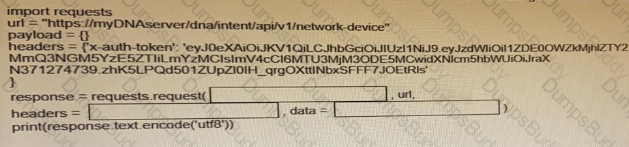
Fill in the blanks to complete the python script to retrieve a list of network devices using the Cisco DNA center API.
What are two advantages of YANG-based approaches for infrastructure automation? (Choose two.)
Drag and drop the functionalities from the left onto correct networking devices on the right.
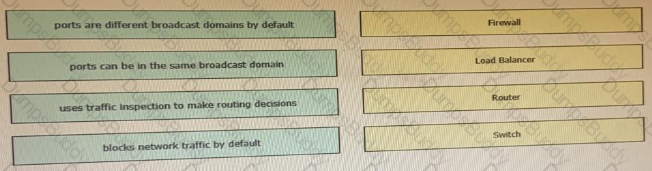
Which device is used to transport traffic from one broadcast domain to another broadcast domain?
How does requesting a synchronous API operation differ from requesting an asynchronous API operation?
When a Cisco IOS XE networking device is configured using RESTCONF, what is the default data-encoding method?
Refer to the exhibit.
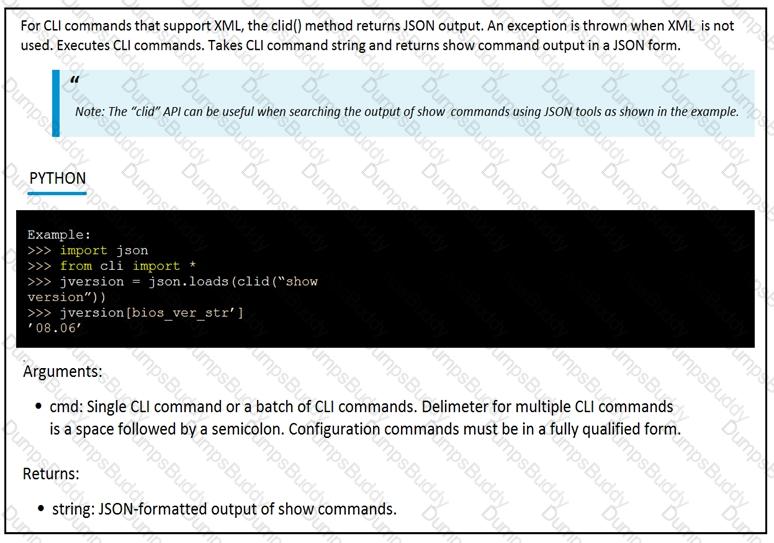
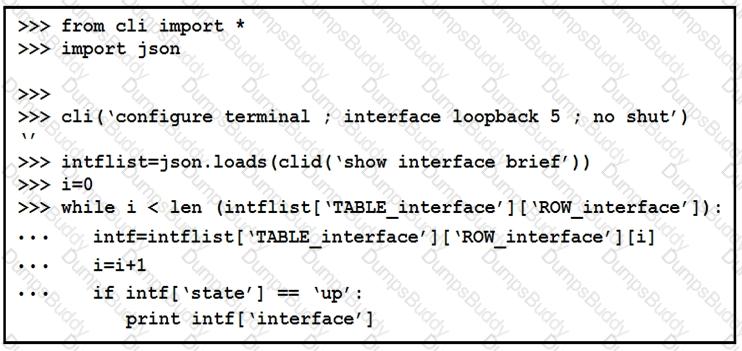
The python interpreter and the Cisco python SDK are available by default in the Cisco NX-OS software. The SDK documentation shows how the cild() API can be used when working with working with JSON and XML. What are two effect of running the script? (Choose two.)
Refer to the exhibit.
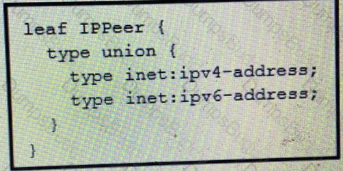
What is the value of the node defined by this YANG structure?
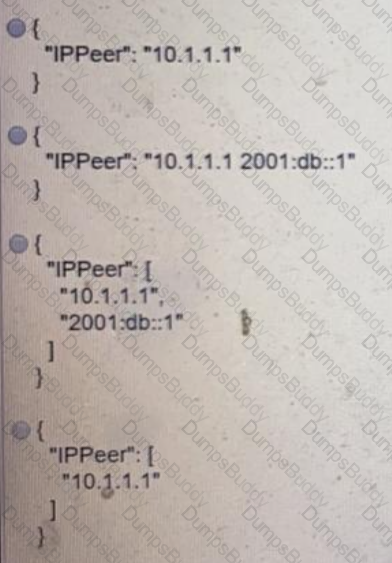
Drag and drop the network automation interfaces from the left onto the transport protocols that they support on the right. Not all options are used.
How is a branch called "my-bug-fix" started to develop a fix needed in a product?
Refer to the exhibit.
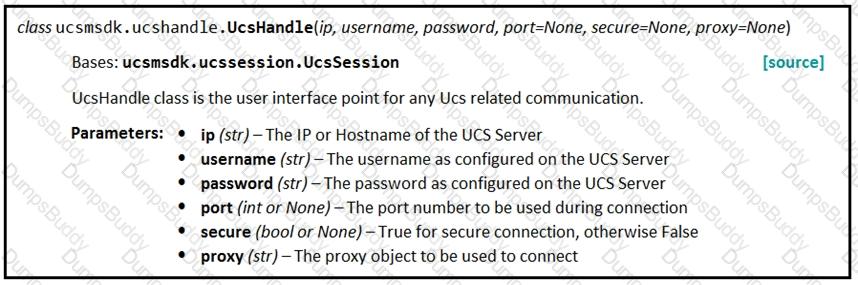
Given the API documentation for the UCS SDK python class, UcsHandle, which code snippet creates a handle instance?
Which platform has an API that has the capability to obtain a list of vulnerable software on user devices?
Refer to the exhibit.
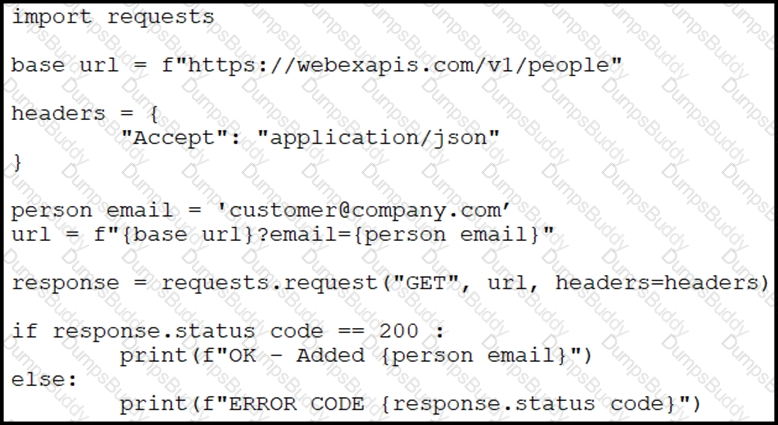
A collaboration engineer has developed a script to automate the gathering of information by providing the email address of the individual. When the engineer tests the script, a 401 error is received. Which command fixes the script?
Which Python function is used to parse a string that contains JSON data into a Python dictionary?
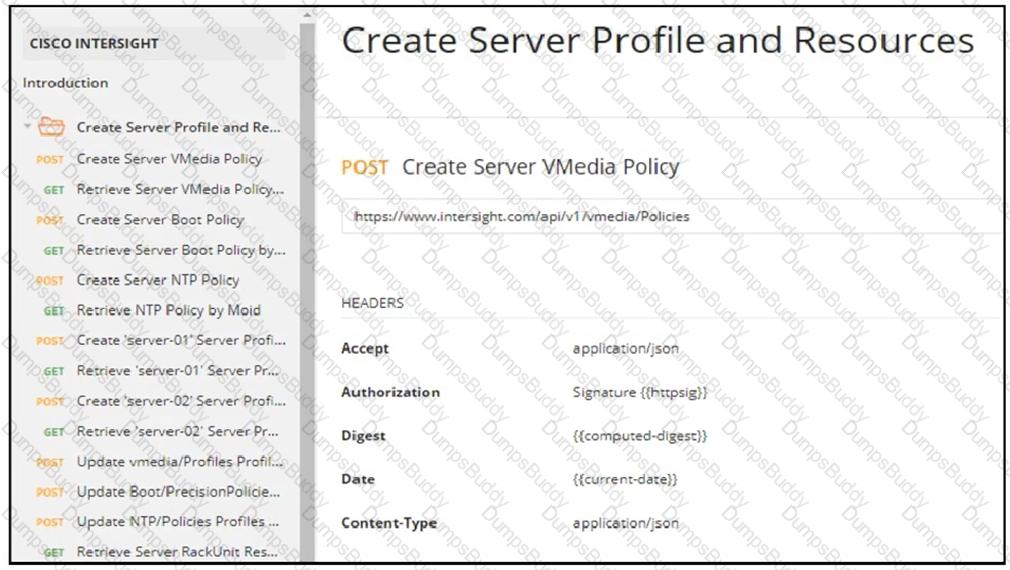
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script by using the Cisco SDK. Not all options are used.


Refer to the exhibit. A developer creates a Python script by using the Cisco Meraki API. The solution must:
• Obtain a list of HTTP servers for a network named "netl".
• Print the response body if the HTTP status code is 200.
• Handle the timeout requests as exceptions, and print Timeout Error next to the exception to stdout.
Which block of code completes the script?
A)
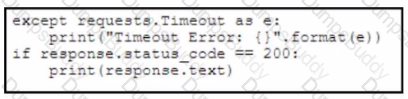
B)
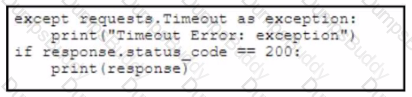
Drag and drop the characteristics from the left onto the software development methodologies on the right.
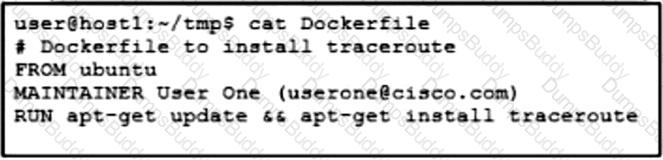
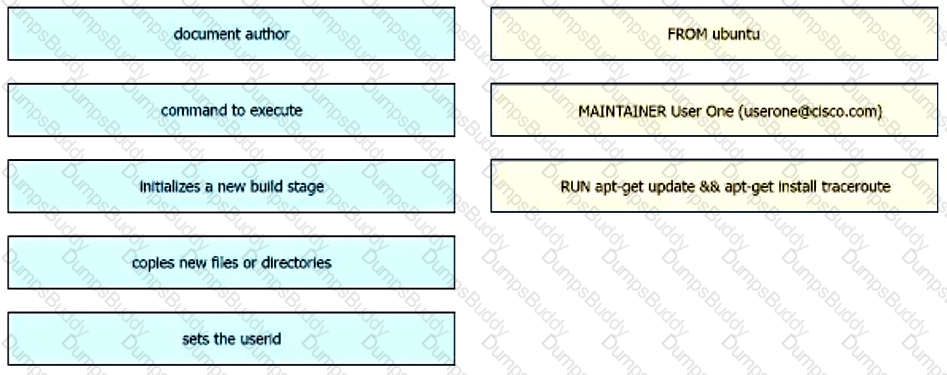
Refer to the exhibit. Drag and drop the Dockerfile contents from the left onto the functions on the right that create a container image to run traceroute to track network path to specific targets. Not all options are used.
A team of developers is responsible for a network orchestration application in the company. The responsibilities also include:
developing and improving the application in a continuous manner
deployment of the application and management of CI/CD frameworks
monitoring the usage and problems and managing the performance improvements
Which principle best describes this DevOps practice?
A developer is attempting to retrieve all the messages from a Cisco Webex space. The server responds by sending the first 1,000 messages. The developer must make additional requests to retrieve the rest of the messages. Which API constraint is described in this scenario?
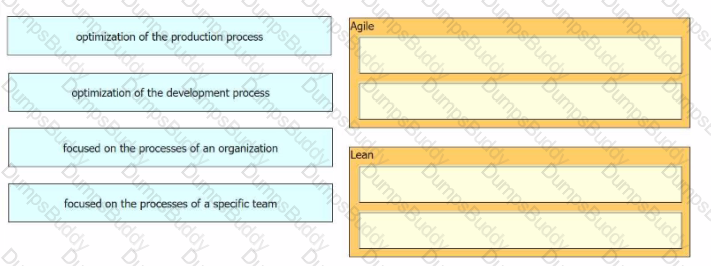
Drag and drop characteristics from the left onto the infrastructure management methodologies on the right.
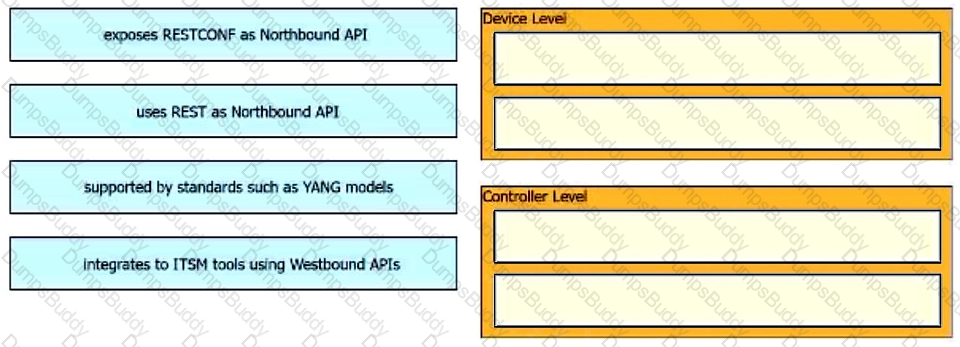
What is a capability of model-driven programmability for infrastructure automation?
Refer to the exhibit.
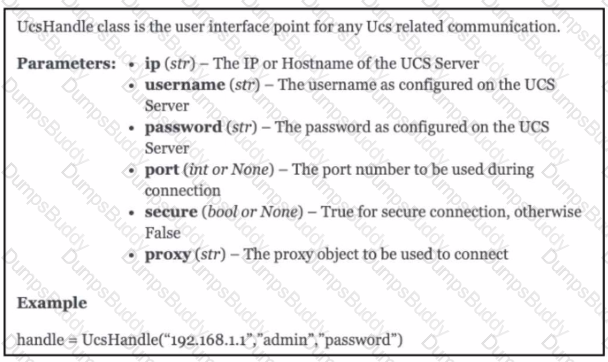
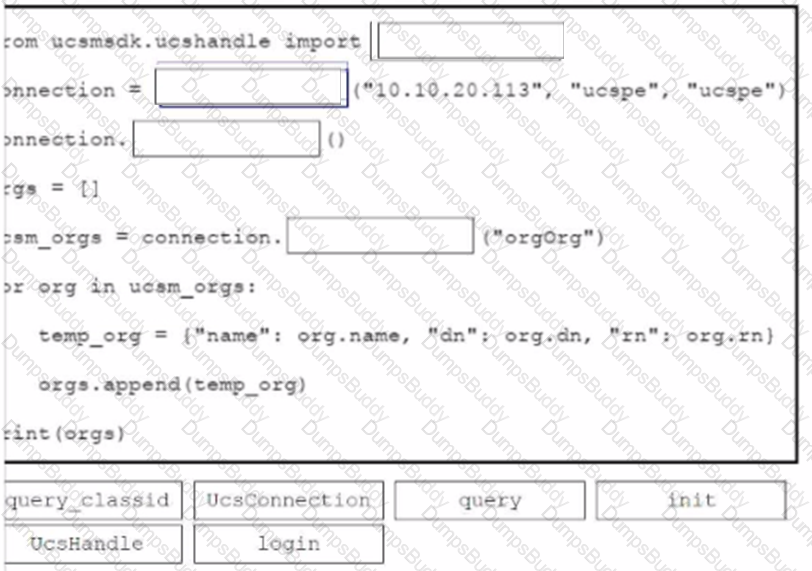
An engineer needs to retrieve all the organizations in a Cisco UCS Manager deployment. Drag and drop the code snippets from the bottom onto the blanks in.. Python script to print the information to standard output. Some options may be used more than once. Not all options are used.
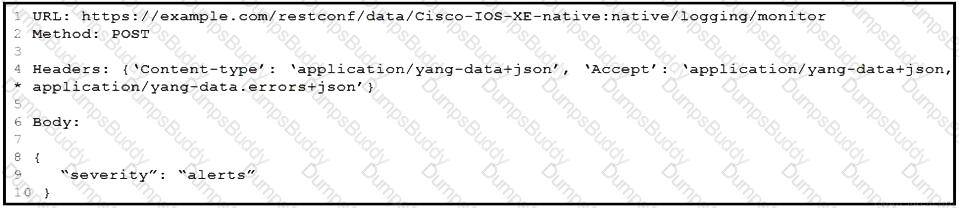
Refer to the exhibit. Which HTTP code is returned after the RESTCONF query is executed?
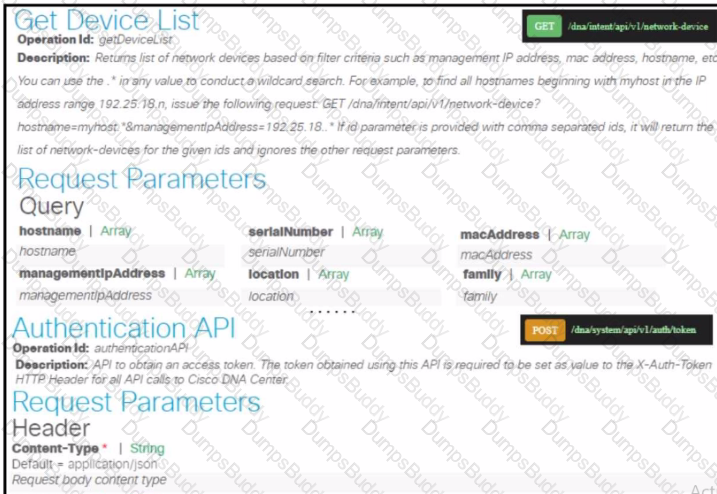
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the Python script to retrieve a list of hosts using the Cisco DNA Center API. Not all options …used.
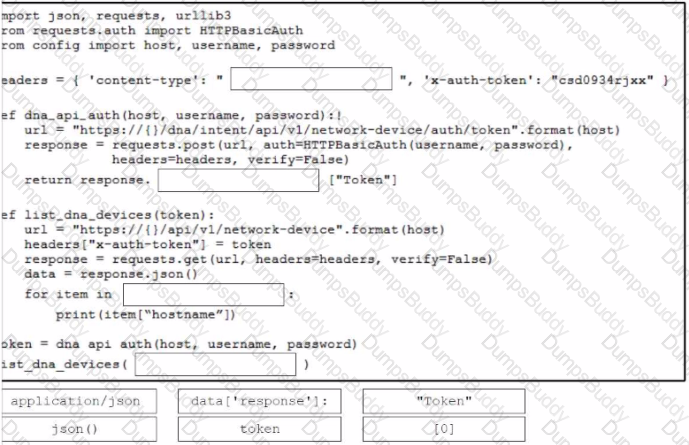
Drag and drop the code from the bottom onto the box where the code is missing to obtain a list of network devices by using the Cisco Meraki API. Not all options are used.
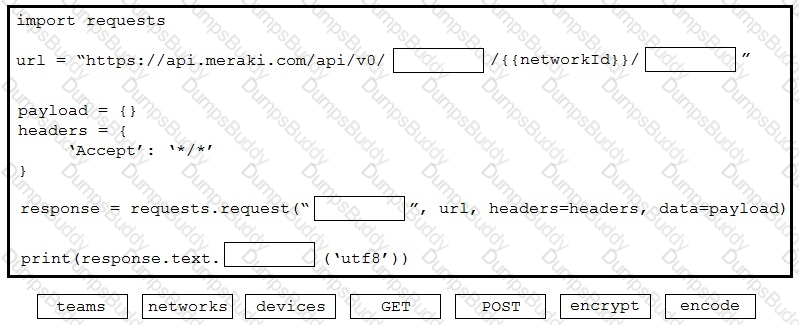
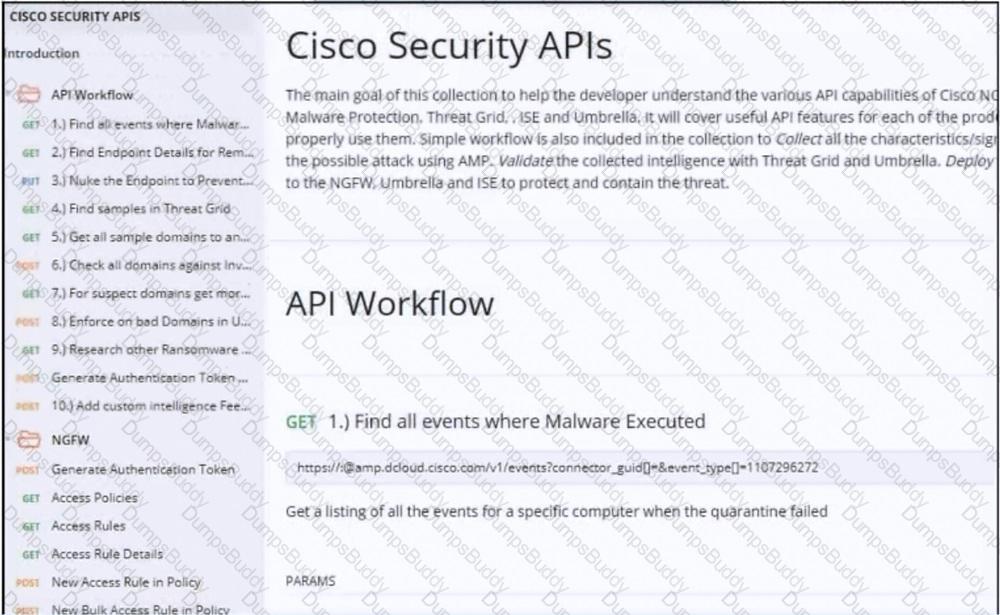
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.
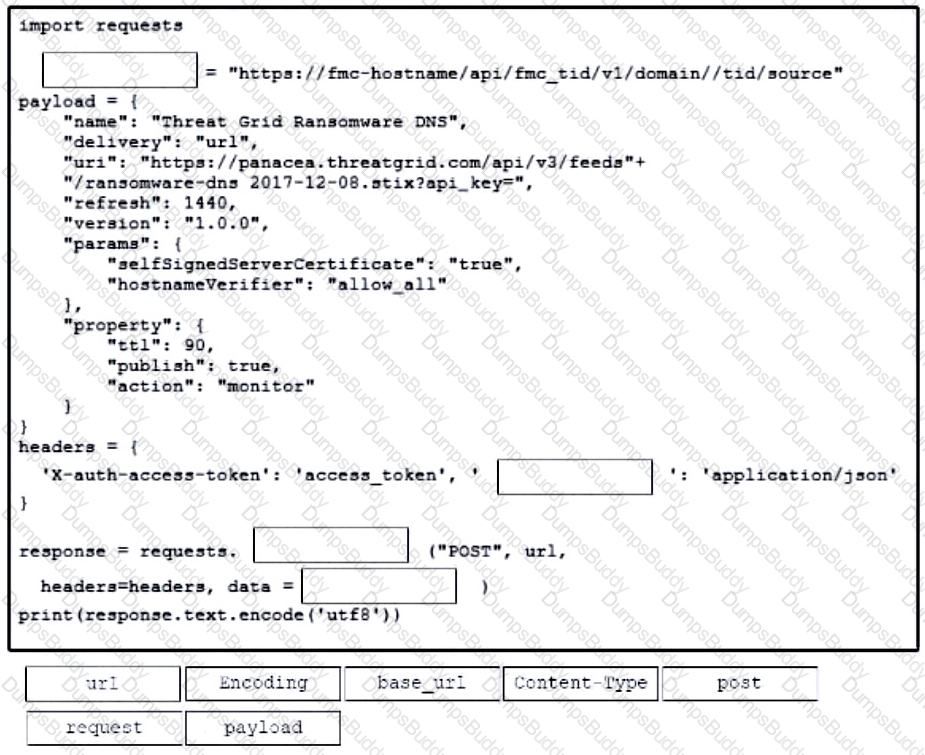
Which HTTP response code is returned from a successful REST API call to create a new resource?
A company wants to automate the orders processed on its website using API. The network device that supports the solution must:
support XML encoding
support distributed transactions
support YANG data models
be support software redundancy
Which requirement prevents the use of RESTCONF for the solution?
A developer has experienced security issues with a previously developed application. The API offered by that application is open and without any constraints. During a recent attack, the application was overloaded with API requests. To address this issue, an API constraint is implemented to protect the application from future attacks or any sudden throttling. Which API constraint must the application developer implement in this situation?
Refer to the exhibit.
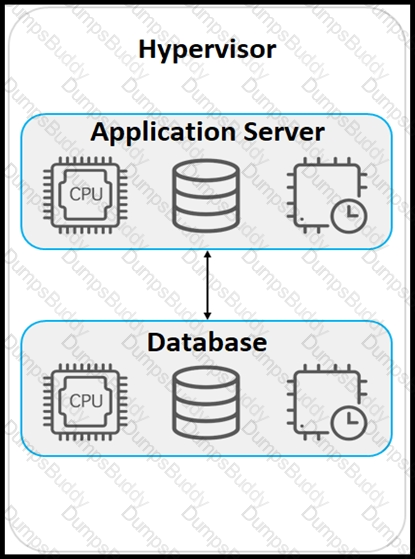
An application must be deployed on a server that has other applications installed. The server resources are to be allocated based on the deployment requirements. The OS for each application must be independent. Which type of deployment is used?
Which solution reduces costs from MPLS, improves application performance, and simplifies operations?
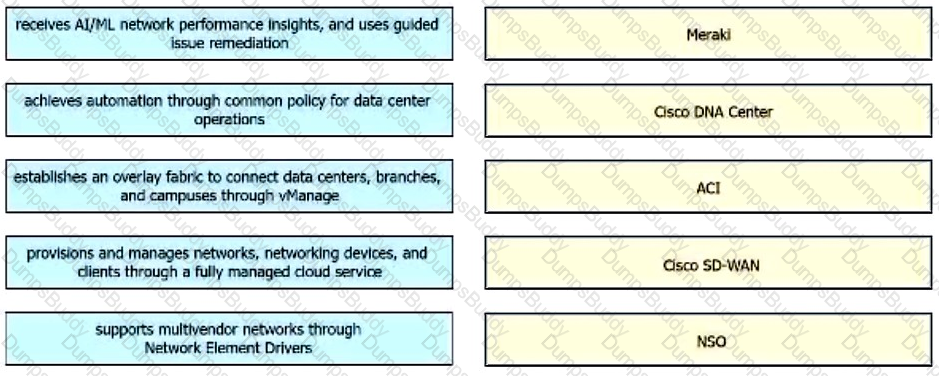
Drag and drop the capabilities from the left onto the Cisco Network Management Platforms that support the capabilities on the right.
Users cannot access a webserver and after the traffic is captured, the capture tool snows an ICMP packet that reports "time exceeded in-transit". What is the cause of this webserver access issue?
An engineer is creating an API to automatically obtain specific zones from Cisco Meraki MV cameras. The data that is provided when the API runs must represent the current analytic zones that are configured on the cameras. The API must start automatically at 6 p.m. every day and save the data on a server for further processing. Which part of the HTTP request must be configured to meet these requirements?
Drag and drop the code from the bottom onto the box where the code is missing to present GigabilEthernet2 details in the XML format. Not all options are used.
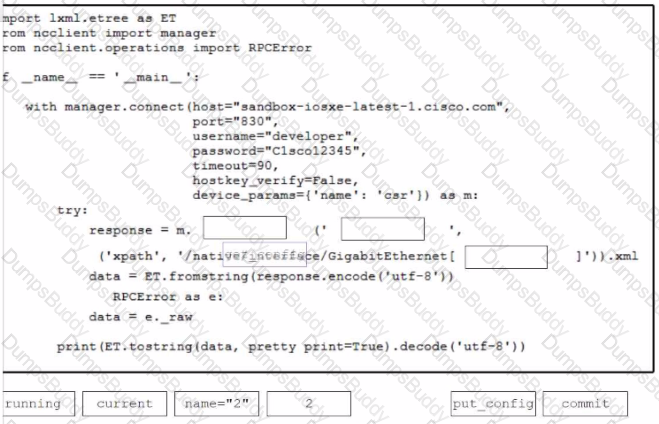
Drag and drop the common API styles from the left onto the requirement on the right.
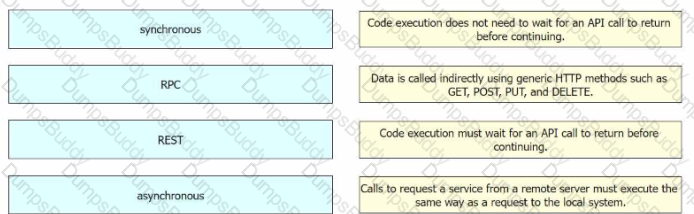
What is an advantage of device-level management as compared to controller-level management to automate the configuration of network devices?
Drag and drop the characteristics from the left onto the corresponding categories on the right to compare RESTful and RPC APIs.
Which two commands download and execute an Apache web server container in Docker with a port binding 8080 in the container to 80 on the host? (Choose two.)
What is the purpose of running tests before writing code in test-driven development?
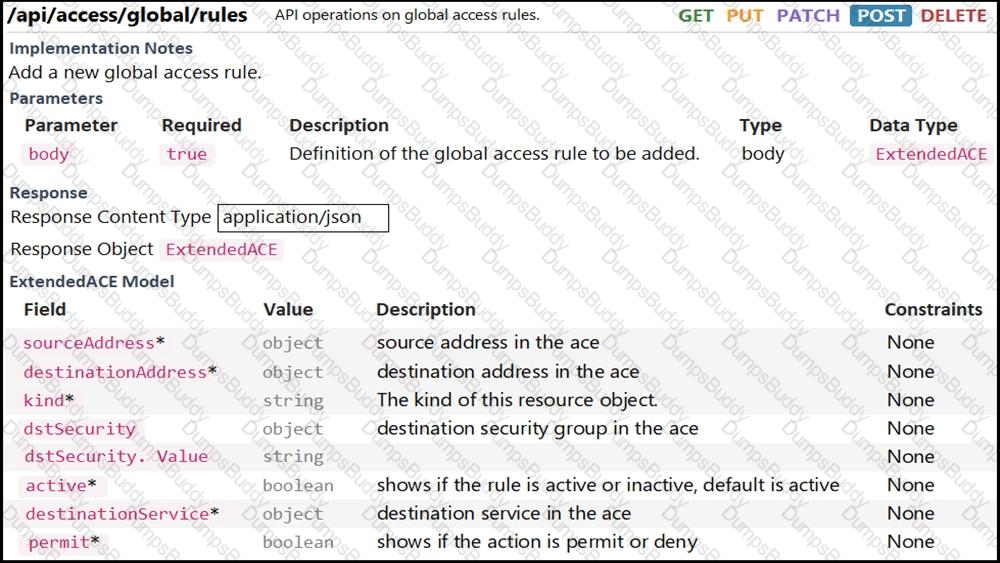
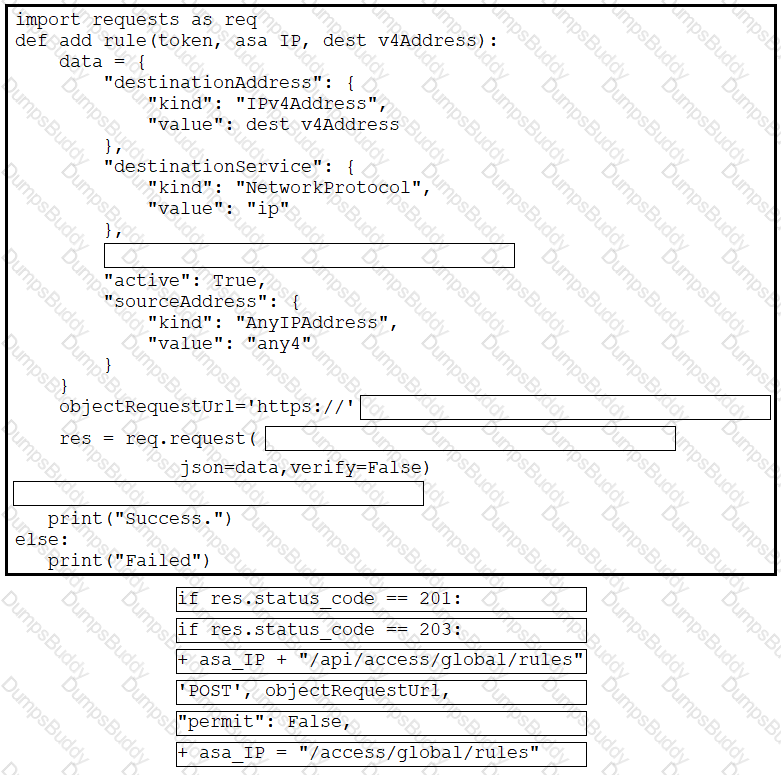
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to complete the function that adds a new global access rule that denies traffic using the Cisco ASA REST API. Not all options are used.
What is a component of the first stage of an application development CI/CD pipeline?
Refer to the exhibit.

An engineer is comparing two tiles by using the unified cliff format What is determined by the content in the file2.py file?
Refer to the exhibit.
What are two characteristics of the NETCONF response? (Choose two.)
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. The Python script retrieves a list of tasks from a to-do list for effective project management purposes. Not all options are used.

What is a requirement when authenticating a RESTCONF API session with a router that runs Cisco IOS XE Software?
Drag and drop the Dockerfile instructions from the left onto the descriptions on the right. Not at options are used.
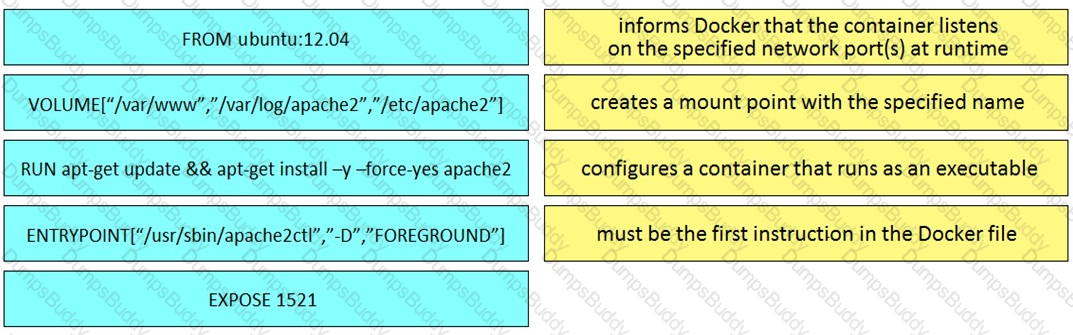
Refer to the exhibit.

A network engineer must change the configuration on devices daily. The Python script must collect CLI arguments from the user, organize data according to the Cisco-IOS-XE-native YANG model, and utilize Cisco REST APIs to make the configuration. Which workflow is being automated by the Python script?
A developer needs a list of clients connected to a specific device in a Meraki network. After making a REST API call, the developer receives an unfamiliar response code. Which Cisco DevNet resource should be used to identify the meaning of the response code?
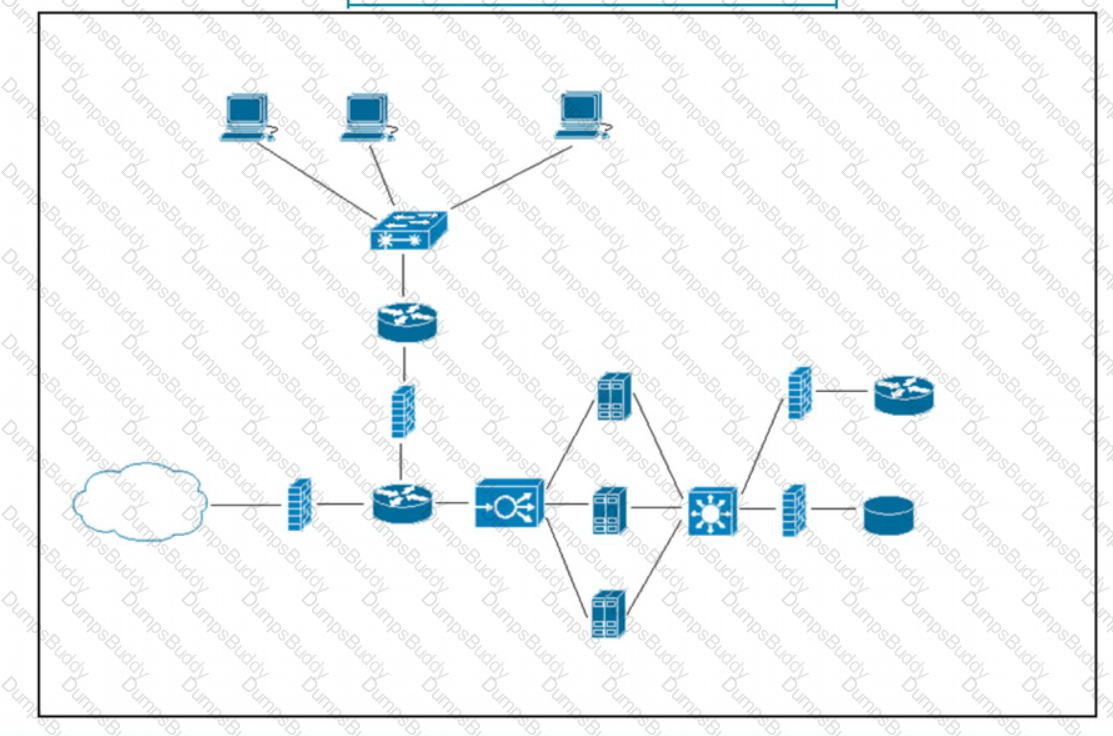
Refer to the exhibit. What does the load balancer enable in the network topology?
Refer to the exhibit.
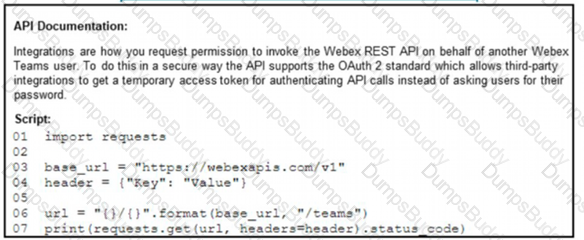
A developer creates a Python script that queries Cisco Webex. When the script is executed, a 401 code is returned. After troubleshooting, the developer discovers that the service is missing privileges. Which change to the header in line 4 of the script results in the code 200?
A)

B)

C)

D)

A local Docker alpine image has been created with an image ID of a391665405fe and tagged as “latest”. Which command creates a running container based on the tagged image, with the container port 8080 bound to port 80 on the host?
Refer to the exhibit.

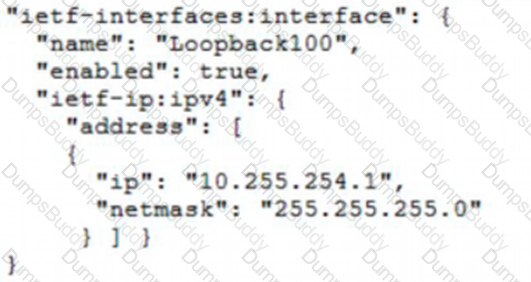
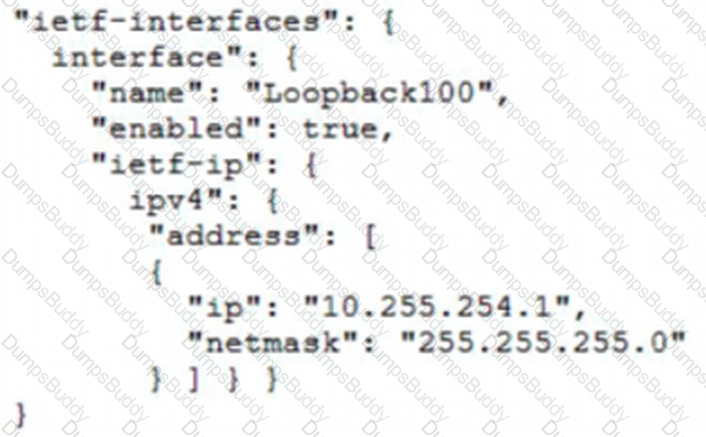
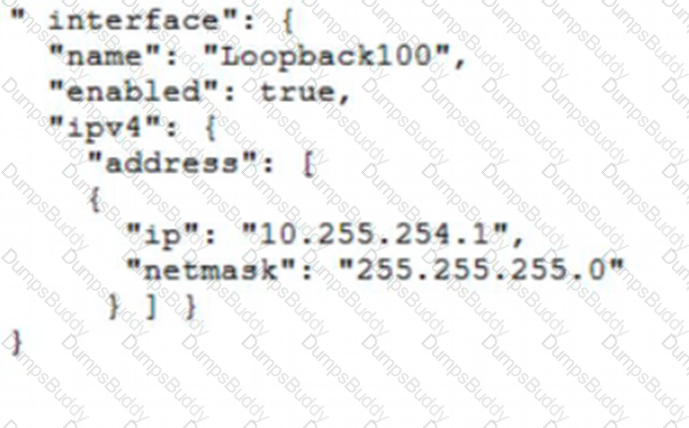
Which JSON snippet configures a new interface according to YANG model?
A)
B)
C)
D)
Access to the management interface of devices must be restricted by using SSH and HTTPS. Which two ports must be included in the ACLs for the protocols to work? (Choose two.)
Which tool allows changes to the configuration management toolset to be tested?
Which advantage does the agile process offer compared to waterfall software development?
Which application should be used to externally access all applications deployed in the same host machine with a single public IP address and port, when each application listens on different local ports?
Refer to the exhibit.
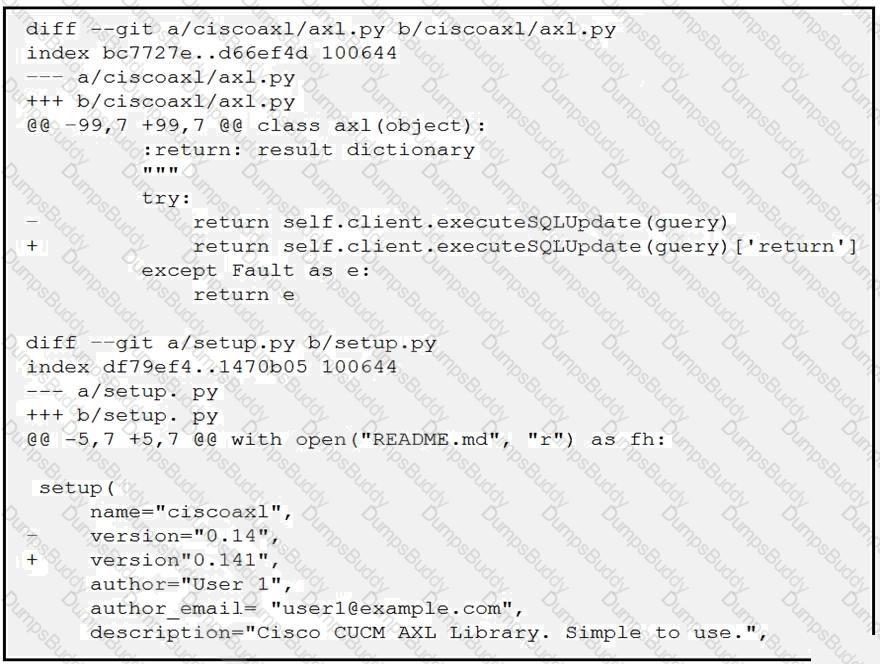
Which two files are being edited in the unified diff? (Choose two.)
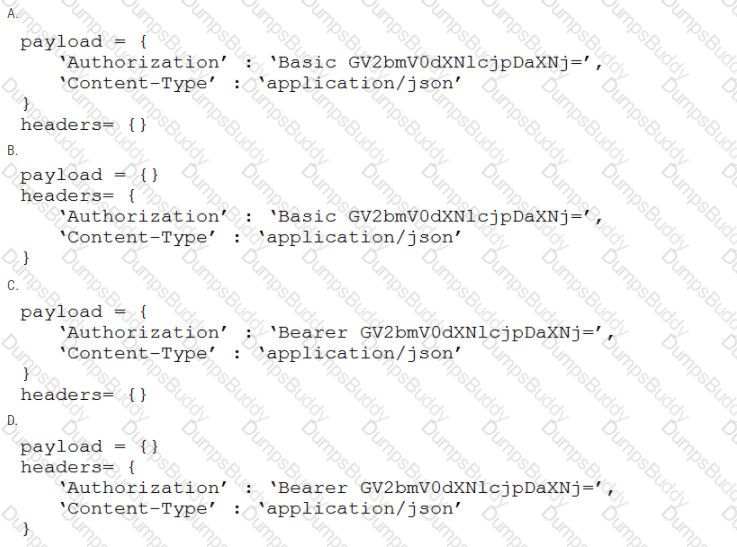
A developer is creating a script to interact with a REST API service which requires basic authentication. The credentials are "devnet:391665405" and the Base64 encoding of the credentials is "GV2bmV0dXNlcjpDaXNj=". Which payload and header combination must be used for authentication?
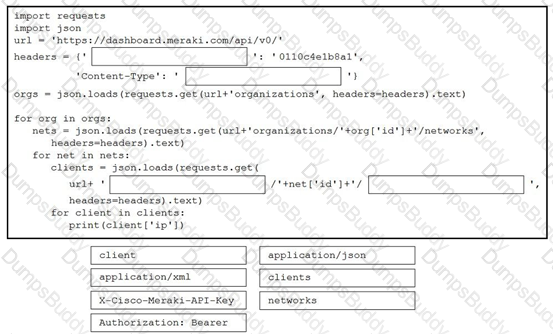
Drag and drop the code from the bottom onto the box where the code is missing in the Python script to complete a function to return all the clients on a network by using the Cisco Meraki Dashboard API. Not all options are used.
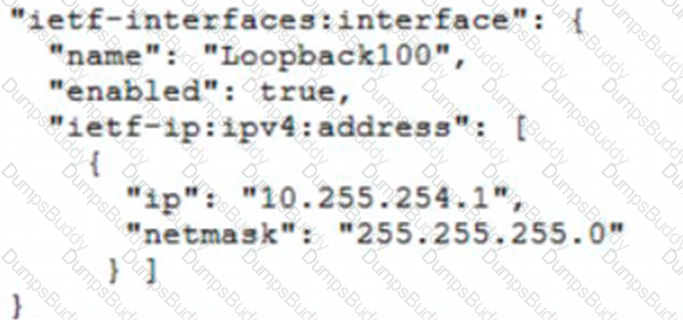
Refer to the exhibit.
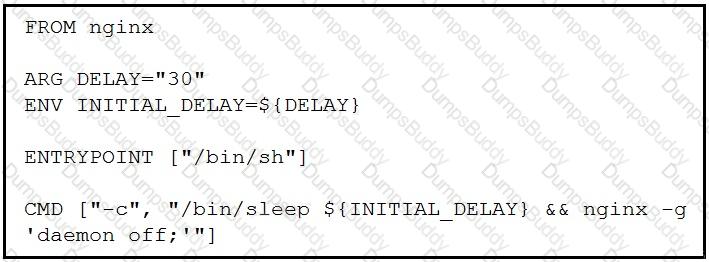
Which command, including arguments, is executed when the container starts?
Refer to the exhibit.
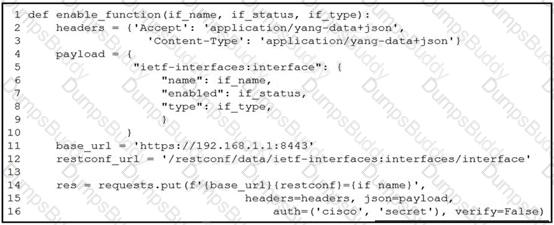
A network engineer wants to automate the port enable/disable process on specific Cisco switches. The engineer creates a script to send a request through RESTCONF and uses ietf as the YANG model and JSON as payload. Which command enables an interface named Loopback1?
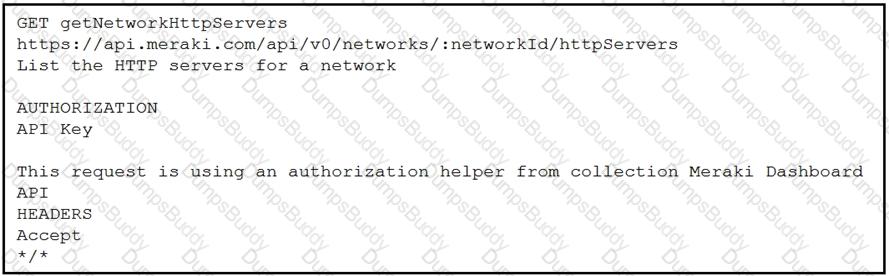
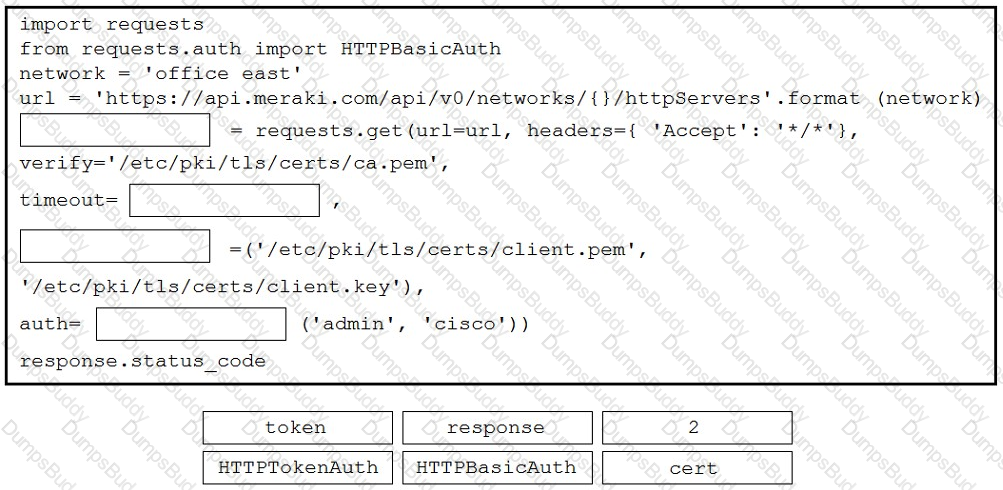
Refer to the exhibit. A developer is creating a Python script to obtain a list of HTTP servers on a network named office_east by using the Cisco Meraki API. The request has these requirements:
• Must time out if the response is not received within 2 seconds.
• Must utilize client certificates and SSL certificate verification.
• Must utilize basic authentication that uses a username of admin and a password of cisco.
• Must save the response to an object named response.
Drag and drop the code snippets from the bottom onto the blanks in the code to meet the requirements. Not all options are used.
Drag and drop the code snippets from the bottom into the Python script to write API output to a csv file. Not all options are used.
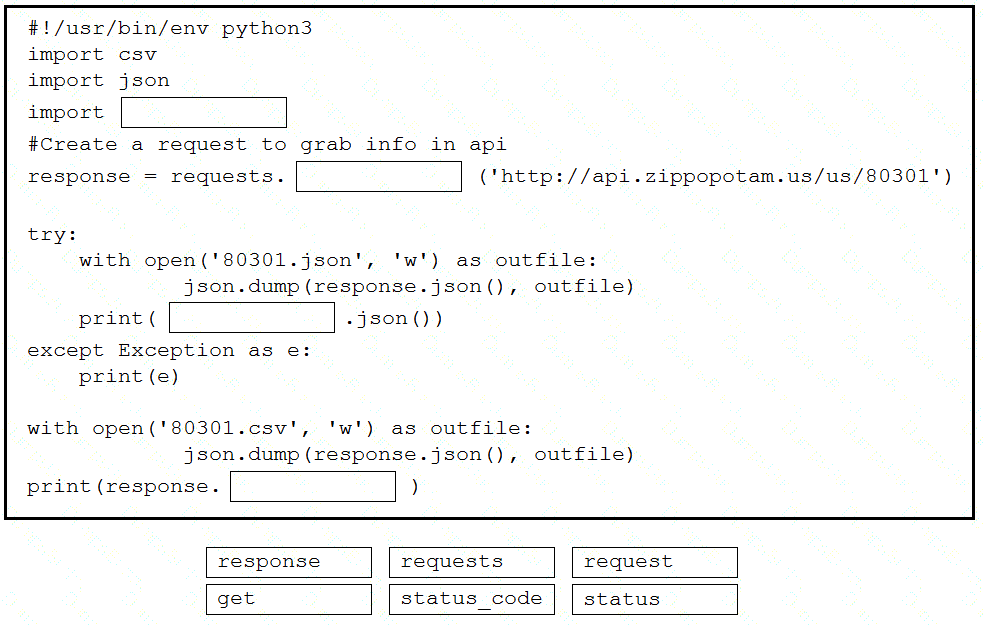
Refer to the exhibit.
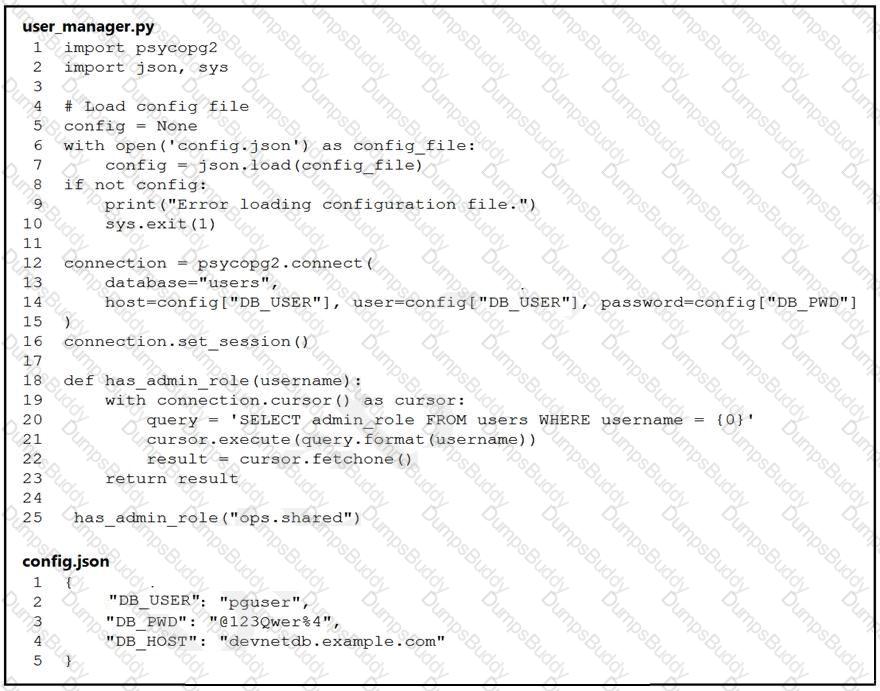
An engineer must check the admin rights of users on a database regularly and prepares
the Python script to automate the process. The script connects to the database and runs a query. What is a security issue about the secrets in the code that relates to secret protection?
Where is an IP packet routed if the packet does not match any routes in the routing table?
In which two ways is an application characterized when interacting with a webhook? (Choose two.)
In test-driven development, what are two of the green bar patterns? (Choose two.)
A developer creates a script that configured multiple Cisco IOS XE devices in a corporate infrastructure. The internal test environment is unavailable, and no maintenance window is available to test on a low-priority production environment. Which resource is used to test the code before it is applied to the production environment?
Refer to the exhibit.
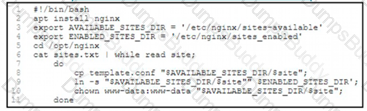
An engineer must configure a load balancer server. The engineer prepares a script to automate workflow by using Bash. The script install the nginx package, moves to the /optAtginx directory, and reads the sites M We (or further processing Based on the script workflow, which process is being automated within the loop by using the information mi sites txt?
Into which type of Python data structure should common data formats be parsed?
Refer to the exhibit.

A developer creates a script to obtain a list of devices by using the Cisco DNA Center API. The remote server authorizes the request only if an authentication token is supplied in the headers. A function named get_auth_token() must retrieve a valid token by using HTTP Basic Authentication. Which code must be added to complete the get_auth_token() function?
Refer to the exhibit.
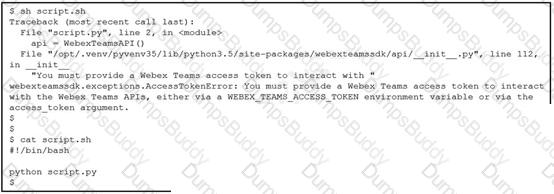
Which line must be included in the Bash script for the Python code to succeed?
Refer to the exhibit.
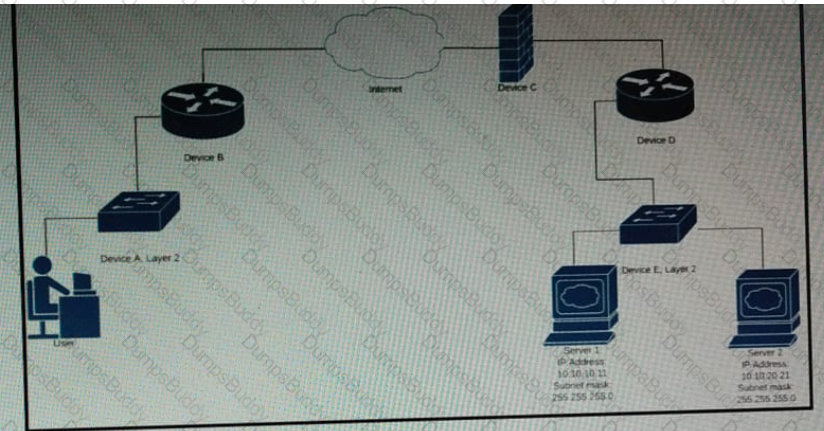
Which device limits traffic between server 1 and server 2?
Refer to the exhibit.
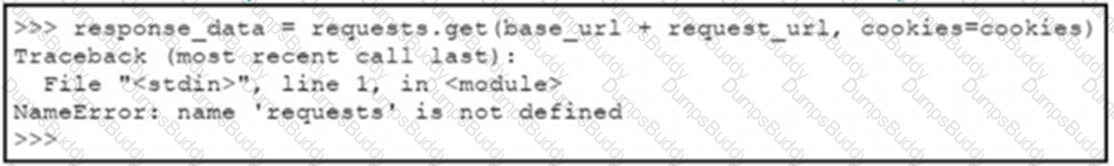
A Python code has been written to query a device. The executed code results in the error shown. Which action resolves the problem?