Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
Refer to the exhibit.
An attacker scanned the server using Nmap.
What did the attacker obtain from this scan?
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
Which type of data must an engineer capture to analyze payload and header information?
The SOC team has confirmed a potential indicator of compromise on an endpoint. The team has narrowed the executable file's type to a new trojan family. According to the NIST Computer Security Incident Handling Guide, what is the next step in handling this event?
Which technology should be used to implement a solution that makes routing decisions based on HTTP header, uniform resource identifier, and SSL session ID attributes?
When an event is investigated, which type of data provides the investigate capability to determine if data exfiltration has occurred?
The SOC team has confirmed a potential indicator of compromise on an endpoint. The team has narrowed the executable file's type to a new trojan family. According to the NIST Computer Security Incident Handling Guide, what is the next step in handling this event?
Which security model assumes an attacker within and outside of the network and enforces strict verification before connecting to any system or resource within the organization?
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
An engineer configured regular expression “.”\.(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1 .[01]" on Cisco ASA firewall. What does this regular expression do?
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
Endpoint logs indicate that a machine has obtained an unusual gateway address and unusual DNS servers via DHCP Which type of attack is occurring?
Refer to the exhibit.
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
Refer to the exhibit.
An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server Which display filters should the analyst use to filter the FTP traffic?
An engineer is investigating a case of the unauthorized usage of the “Tcpdump” tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
At a company party a guest asks questions about the company’s user account format and password complexity. How is this type of conversation classified?
Which data type is necessary to get information about source/destination ports?
Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
Refer to the exhibit.
A suspicious IP address is tagged by Threat Intelligence as a brute-force attempt source After the attacker produces many of failed login entries, it successfully compromises the account. Which stakeholder is responsible for the incident response detection step?
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt. Within 48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?
Which event artifact is used to identify HTTP GET requests for a specific file?
Which type of evidence supports a theory or an assumption that results from initial evidence?
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external penmeter data flows contain records, writings, and artwork Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age. The engineer must identify protected data. Which two types of data must be identified'? (Choose two.)
Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
What is personally identifiable information that must be safeguarded from unauthorized access?
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
What is a difference between inline traffic interrogation and traffic mirroring?
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
Refer to the exhibit.
An engineer received an event log file to review. Which technology generated the log?
What is a collection of compromised machines that attackers use to carry out a DDoS attack?
According to the September 2020 threat intelligence feeds a new malware called Egregor was introduced and used in many attacks. Distnbution of Egregor is pnmanly through a Cobalt Strike that has been installed on victim's workstations using RDP exploits Malware exfiltrates the victim's data to a command and control server. The data is used to force victims pay or lose it by publicly releasing it. Which type of attack is described?
Refer to the exhibit.
Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
A user received an email attachment named "Hr405-report2609-empl094.exe" but did not run it. Which category of the cyber kill chain should be assigned to this type of event?
A user reports difficulties accessing certain external web pages. When an engineer examines traffic to and from the external domain in full packet captures, they notice that many SYNs have the same sequence number, source, and destination IP address, but they have different payloads. What is causing this situation?
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
An engineer received an alert affecting the degraded performance of a critical server. Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
Why should an engineer use a full packet capture to investigate a security breach?
What is the communication channel established from a compromised machine back to the attacker?
A cyberattacker notices a security flaw in a software that a company is using They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software To which category of the Cyber Kill Cham model does this event belong?
A security analyst notices a sudden surge of incoming traffic and detects unknown packets from unknown senders After further investigation, the analyst learns that customers claim that they cannot access company servers According to NIST SP800-61, in which phase of the incident response process is the analyst?
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
A security specialist notices 100 HTTP GET and POST requests for multiple pages on the web servers. The agent in the requests contains PHP code that, if executed, creates and writes to a new PHP file on the webserver. Which event category is described?
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
Refer to the exhibit.
Which stakeholders must be involved when a company workstation is compromised?
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
Which information must an organization use to understand the threats currently targeting the organization?
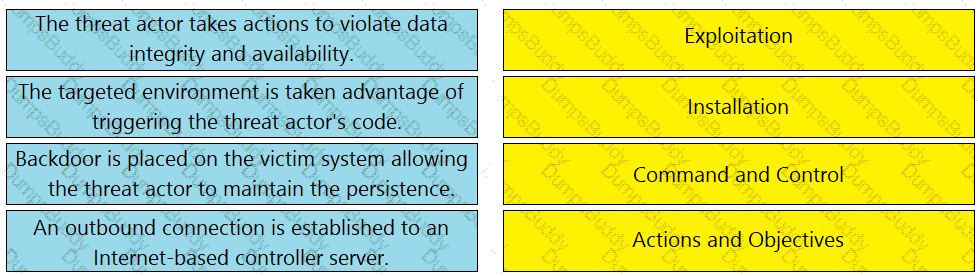
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
What is the difference between discretionary access control (DAC) and role-based access control (RBAC)?
An organization is cooperating with several third-party companies. Data exchange is on an unsecured channel using port 80 Internal employees use the FTP service to upload and download sensitive data An engineer must ensure confidentiality while preserving the integrity of the communication. Which technology must the engineer implement in this scenario'?
Refer to exhibit.
An analyst performs the analysis of the pcap file to detect the suspicious activity. What challenges did the analyst face in terms of data visibility?