When attempting to start a VPN tunnel, in the logs the error “no proposal chosen” is seen numerous times. No other VPN-related entries are present.
Which phase of the VPN negotiations has failed?
Fill in the blank. Once a certificate is revoked from the Security Gateway by the Security Management Server, the certificate information is ________ .
What is the best method to upgrade a Security Management Server to R80.x when it is not connected to the Internet?
Fill in the blank: __________ information is included in “Full Log” tracking option, but is not included in “Log” tracking option?
To ensure that VMAC mode is enabled, which CLI command should you run on all cluster members?
There are two R77.30 Security Gateways in the Firewall Cluster. They are named FW_A and FW_B. The cluster is configured to work as HA (High availability) with default cluster configuration. FW_A is configured to have higher priority than FW_B. FW_A was active and processing the traffic in the morning. FW_B was standby. Around 1100 am, its interfaces went down and this caused a failover. FW_B became active. After an hour, FW_A’s interface issues were resolved and it became operational.
When it re-joins the cluster, will it become active automatically?
An administrator is creating an IPsec site-to-site VPN between his corporate office and branch office. Both offices are protected by Check Point Security Gateway managed by the same Security Management Server. While configuring the VPN community to specify the pre-shared secret the administrator found that the check box to enable pre-shared secret and cannot be enabled.
Why does it not allow him to specify the pre-shared secret?
In which VPN community is a satellite VPN gateway not allowed to create a VPN tunnel with another satellite VPN gateway?
Which statements below are CORRECT regarding Threat Prevention profiles in SmartDashboard?
SSL Network Extender (SNX) is a thin SSL VPN on-demand client that is installed on the remote user’s machine via the web browser. What are the two modes of SNX?
IF the first packet of an UDP session is rejected by a rule definition from within a security policy (not including the clean up rule), what message is sent back through the kernel?
Vanessa is firewall administrator in her company. Her company is using Check Point firewall on a central and several remote locations which are managed centrally by R77.30 Security Management Server. On central location is installed R77.30 Gateway on Open server. Remote locations are using Check Point UTM-1570 series appliances with R75.30 and some of them are using a UTM-1-Edge-X or Edge-W with latest available firmware. She is in process of migrating to R80.
What can cause Vanessa unnecessary problems, if she didn’t check all requirements for migration to R80?
When gathering information about a gateway using CPINFO, what information is included or excluded when using the “-x” parameter?
Fill in the blank: A new license should be generated and installed in all of the following situations EXCEPT when ________ .
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.
What is the valid range for Virtual Router Identifier (VRID) value in a Virtual Routing Redundancy Protocol (VRRP) configuration?
What makes Anti-Bot unique compared to other Threat Prevention mechanisms, such as URL Filtering, Anti-Virus, IPS, and Threat Emulation?
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
On R80.10 when configuring Third-Party devices to read the logs using the LEA (Log Export API) the default Log Server uses port:
Fill in the blank: The R80 feature _____ permits blocking specific IP addresses for a specified time period.
Your manager asked you to check the status of SecureXL, and its enabled templates and features. What command will you use to provide such information to manager?
In SmartEvent, what are the different types of automatic reactions that the administrator can configure?
Can multiple administrators connect to a Security Management Server at the same time?
With MTA (Mail Transfer Agent) enabled the gateways manages SMTP traffic and holds external email with potentially malicious attachments. What is required in order to enable MTA (Mail Transfer Agent) functionality in the Security Gateway?
D18912E1457D5D1DDCBD40AB3BF70D5D
The system administrator of a company is trying to find out why acceleration is not working for the traffic. The traffic is allowed according to the rule based and checked for viruses. But it is not accelerated. What is the most likely reason that the traffic is not accelerated?
How would you deploy TE250X Check Point appliance just for email traffic and in-line mode without a Check Point Security Gateway?
Check Point Support in many cases asks you for a configuration summary of your Check Point system. This is also called:
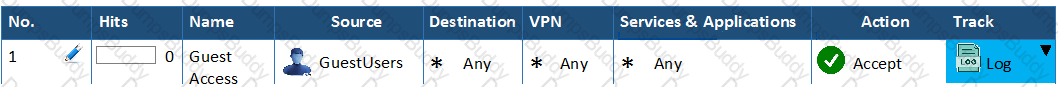
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this?
What CLI command compiles and installs a Security Policy on the target’s Security Gateways?
Ken wants to obtain a configuration lock from other administrator on R80 Security Management Server. He can do this via WebUI or via CLI.
Which command should he use in CLI? (Choose the correct answer.)
For Management High Availability, which of the following is NOT a valid synchronization status?
Which Check Point software blade provides Application Security and identity control?
Selecting an event displays its configurable properties in the Detail pane and a description of the event in the Description pane. Which is NOT an option to adjust or configure?
You have successfully backed up Check Point configurations without the OS information. What command would you use to restore this backup?
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ________ .
After making modifications to the $CVPNDIR/conf/cvpnd.C file, how would you restart the daemon?
Check Point Management (cpm) is the main management process in that it provides the architecture for a consolidates management console. CPM allows the GUI client and management server to communicate via web services using ___________.
What API command below creates a new host with the name “New Host” and IP address of “192.168.0.10”?
Sieve is a Cyber Security Engineer working for Global Bank with a large scale deployment of Check Point Enterprise Appliances Steve's manager. Diana asks him to provide firewall connection table details from one of the firewalls for which he is responsible. Which of these commands may impact performance briefly and should not be used during heavy traffic times of day?