You are the Check Point administrator for Alpha Corp with an R80 Check Point estate. You have received a call by one of the management users stating that they are unable to browse the Internet with their new tablet connected to the company Wireless. The Wireless system goes through the Check Point Gateway. How do you review the logs to see what the problem may be?
A network administrator has informed you that they have identified a malicious host on the network, and instructed you to block it. Corporate policy dictates that firewall policy changes cannot be made at this time. What tool can you use to block this traffic?
Which option in tracking allows you to see the amount of data passed in the connection?
CPU-level of your Security gateway is peaking to 100% causing problems with traffic. You suspect that the problem might be the Threat Prevention settings.
The following Threat Prevention Profile has been created.
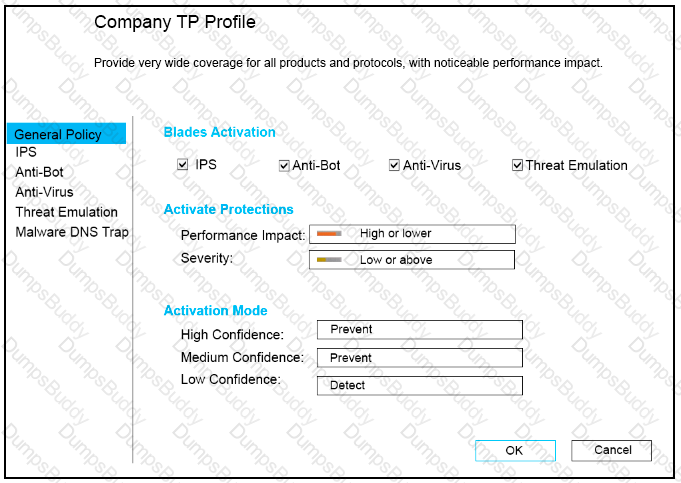
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
Which is a suitable command to check whether Drop Templates are activated or not?
AdminA and AdminB are both logged in on SmartConsole What does it mean if AdmmB sees a lock icon on a rule? Choose the BEST answer.
When a Security Gateways sends its logs to an IP address other than its own, which deployment option is installed?
Which of the following is considered a "Subscription Blade", requiring renewal every 1-3 years?
Which one of the following is the preferred licensing model? Select the BEST answer
Fill in the blank: To create policy for traffic to or from a particular location, use the _____________.
When installing a dedicated R80 SmartEvent server, what is the recommended size of the root partition?
In Logging and Monitoring, the tracking options are Log, Detailed Log and Extended Log. Which of the following options can you add to each Log, Detailed Log and Extended Log?
Most Check Point deployments use Gaia but which product deployment utilizes special Check Point code (with unification in R81.10)?
Fill in the blanks: Default port numbers for an LDAP server is ______ for standard connections and _______ SSL connections.
Which of the following is NOT a valid application navigation tab in the R80 SmartConsole?
Fill in the blank: In Security Gateways R75 and above, SIC uses ______________ for encryption.
What is the most complete definition of the difference between the Install Policy button on the SmartConsole’s tab, and the Install Policy within a specific policy?
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ___________.
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were dropped. You don’t have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
The default shell of the Gaia CLI is cli.sh. How do you change from the cli.sh shell to the advanced shell to run Linux commands?
Which type of Check Point license ties the package license to the IP address of the Security Management Server?
Fill in the blank: When a policy package is installed, ________ are also distributed to the target installation Security Gateways.
How many users can have read/write access in Gaia Operating System at one time?
What are two basic rules Check Point recommending for building an effective security policy?
Which one of the following is a way that the objects can be manipulated using the new API integration in R80 Management?
When connected to the Check Point R80 Management Server using the SmartConsole the first administrator to connect has a lock on:
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
You are the Check Point administrator for Alpha Corp. You received a call that one of the users is unable to browse the Internet on their new tablet which is connected to the company wireless, which goes through a Check Point Gateway. How would you review the logs to see what is blocking this traffic?
Which option, when applied to a rule, allows traffic to VPN gateways in specific VPN communities?
When logging in for the first time to a Security management Server through SmartConsole, a fingerprint is saved to the:
You have enabled "Extended Log" as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
With URL Filtering, what portion of the traffic is sent to the Check Point Online Web Service for analysis?
A security zone is a group of one or more network interfaces from different centrally managed gateways. What is considered part of the zone?
How is communication between different Check Point components secured in R80? As with all questions, select the best answer.
If an administrator wants to restrict access to a network resource only allowing certain users to access it, and only when they are on a specific network what is the best way to accomplish this?
In which scenario is it a valid option to transfer a license from one hardware device to another?
When configuring LDAP User Directory integration, Changes applied to a User Directory template are:
When configuring Anti-Spoofing, which tracking options can an Administrator select?
Which Threat Prevention Software Blade provides protection from malicious software that can infect your network computers? (Choose the best answer.)
Fill in the blank: A(n)_____rule is created by an administrator and configured to allow or block traffic based on specified criteria.
The Gateway Status view in SmartConsole shows the overall status of Security Gateways and Software Blades. What does the Status Attention mean?
What Check Point tool is used to automatically update Check Point products for the Gaia OS?
Which backup utility captures the most information and tends to create the largest archives?
Identity Awareness allows easy configuration for network access and auditing based on what three items?
Identity Awareness allows the Security Administrator to configure network access based on which of the following?
You want to set up a VPN tunnel to a external gateway. You had to make sure that the IKE P2 SA will only be established between two subnets and not all subnets defined in the default VPN domain of your gateway.
What are the Threat Prevention software components available on the Check Point Security Gateway?
Rugged appliances are small appliances with ruggedized hardware and like Quantum Spark appliance they use which operating system?
To ensure that VMAC mode is enabled, which CLI command you should run on all cluster members? Choose the best answer.
Fill in the blank: In order to install a license, it must first be added to the ____________.
You have successfully backed up your Check Point configurations without the OS information. What command would you use to restore this backup?
There are four policy types available for each policy package. What are those policy types?
What needs to be configured if the NAT property ‘Translate destination on client side’ is not enabled in Global properties?
Fill in the blank: An identity server uses a ___________ for user authentication.
An administrator can use section titles to more easily navigate between large rule bases. Which of these statements is FALSE?
After a new Log Server is added to the environment and the SIC trust has been established with the SMS what will the gateways do?
The ______ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
In which deployment is the security management server and Security Gateway installed on the same appliance?
Fill in the blank When LDAP is integrated with Check Point Security Management it is then referred to as_____
The Online Activation method is available for Check Point manufactured appliances. How does the administrator use the Online Activation method?
Which of the following is NOT a policy type available for each policy package?
In order to see real-time and historical graph views of Security Gateway statistics in SmartView Monitor, what feature needs to be enabled on the Security Gateway?